How to Set Up Prisma Cloud Threat Detection in 6 Steps
Alex, a cloud security analyst (part of the SecOps team) at a financial institution is tasked with ensuring that the organization's cloud environments are secure across multiple cloud service providers. While she utilizes Prisma Cloud to continuously enforce security governance and monitor compliance, she understands that effectively detecting threats is equally important for a strong security posture. Let’s look at how Alex set up Prisma Cloud’s threat detection capabilities to quickly detect threats, prioritize investigation and remediate issues across a large multi-cloud landscape:
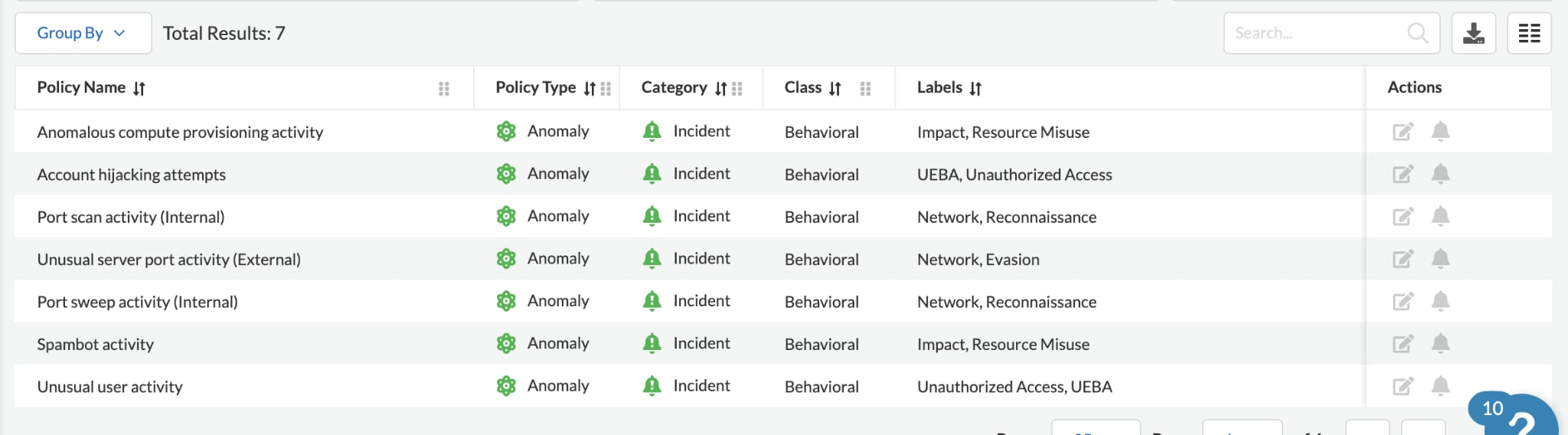
Step 1: Activating the right anomaly policies
The institution Alex works for follows the widely adopted MITRE ATT&CK™ Matrix for Cloud (IaaS) as the guiding principle for their threat detection strategy. Fortunately, Prisma Cloud’s threat detection capabilities are mapped to the MITRE ATT&CK Matrix, making it seamless for Alex to enable the specific policies:
| MITRE ATT&CK for Cloud tactics | Prisma Cloud Anomaly Policies | Details |
| Discovery | Port scan activity
Port sweep activity |
Through port scan/sweep activities, adversaries can uncover vulnerabilities associated with running services. |
| Credential Access | Excessive Login Failures
Account Hijacking Attempts |
Remote work increases the risks of compromised credentials and insider threats. These policies will help Alex detect the anomalies. |
| Persistence | Unusual user activity | Once an adversary gains access, whether it is due to insider threats or account compromise, they may engage in activities different from regular users such as accessing different types of cloud services or accessing from an unusual location. |
| Defense Evasion | Ransomware activity
Downloader activity Remote Access Trojan activity |
Adversaries may try to avoid detection after gaining credentials and/or leverage and abuse trusted processes to hide and masquerade their malware. |
| Impact | Anomalous compute provisioning | With the surge in crypto currencies, cryptojacking continues to be a lucrative business for adversaries. |
| Exfiltration | Backdoor activity
Worm activity |
Adversaries may exfiltrate data by transferring large amounts of data using protocols that are commonly used within a cloud environment, such as HTTP, HTTPS, FTP, etc. |
Step 2: Configuring threat detection settings
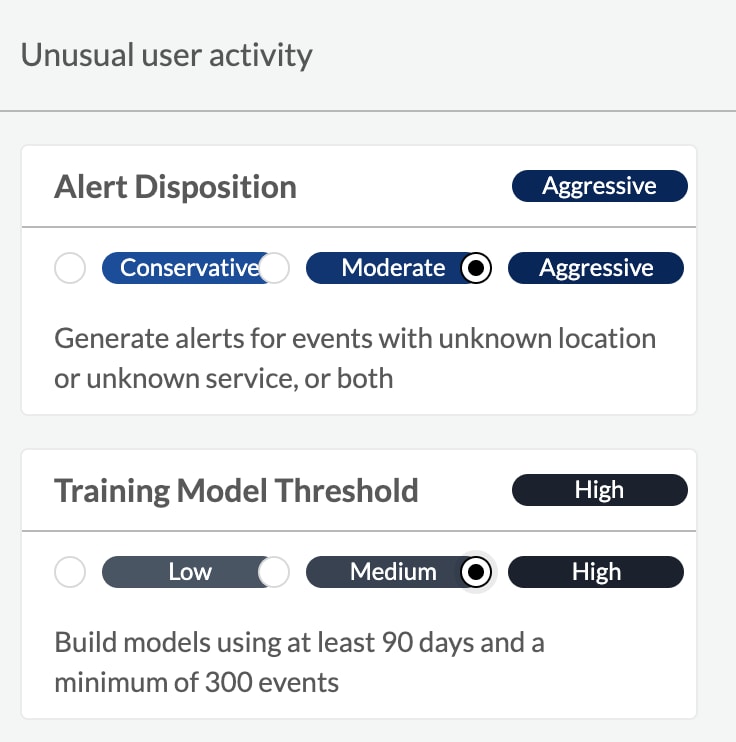
Like most security teams, Alex has limited capacity to manage alerts. She needs the ability to strike the right balance between false positives and false negatives so the most critical threats are detected while not overwhelming her team with too many alerts. Prisma Cloud gives her that fine level of control where she can optimize two different aspects of threat detection:
- Alert disposition - Modify what severity level of the alerts would notify based on the preference of Alex and her team.
- Training threshold - This allows Alex to choose how long and how many events Prisma Cloud’s Threat Detection Machine Learning (ML) models will learn before generating alerts. The more it takes, the more the ML model will learn about the environment and generate fewer false positives.
Let’s take the Unusual User Activity policy for example. Alex chooses “Aggressive - Generate alerts for events with unknown location or unknown service, or both” for Alert Disposition because the organization has strict security guardrails for their users and they need to catch any user activity that looks remotely suspicious. On the other hand, she chooses “High - Build models using at least 90 days and a minimum of 300 events” for Training Model Threshold because they would like the Machine Learning model to learn more about the users’ normal behavior before it starts generating alerts to minimize the number of false positives.
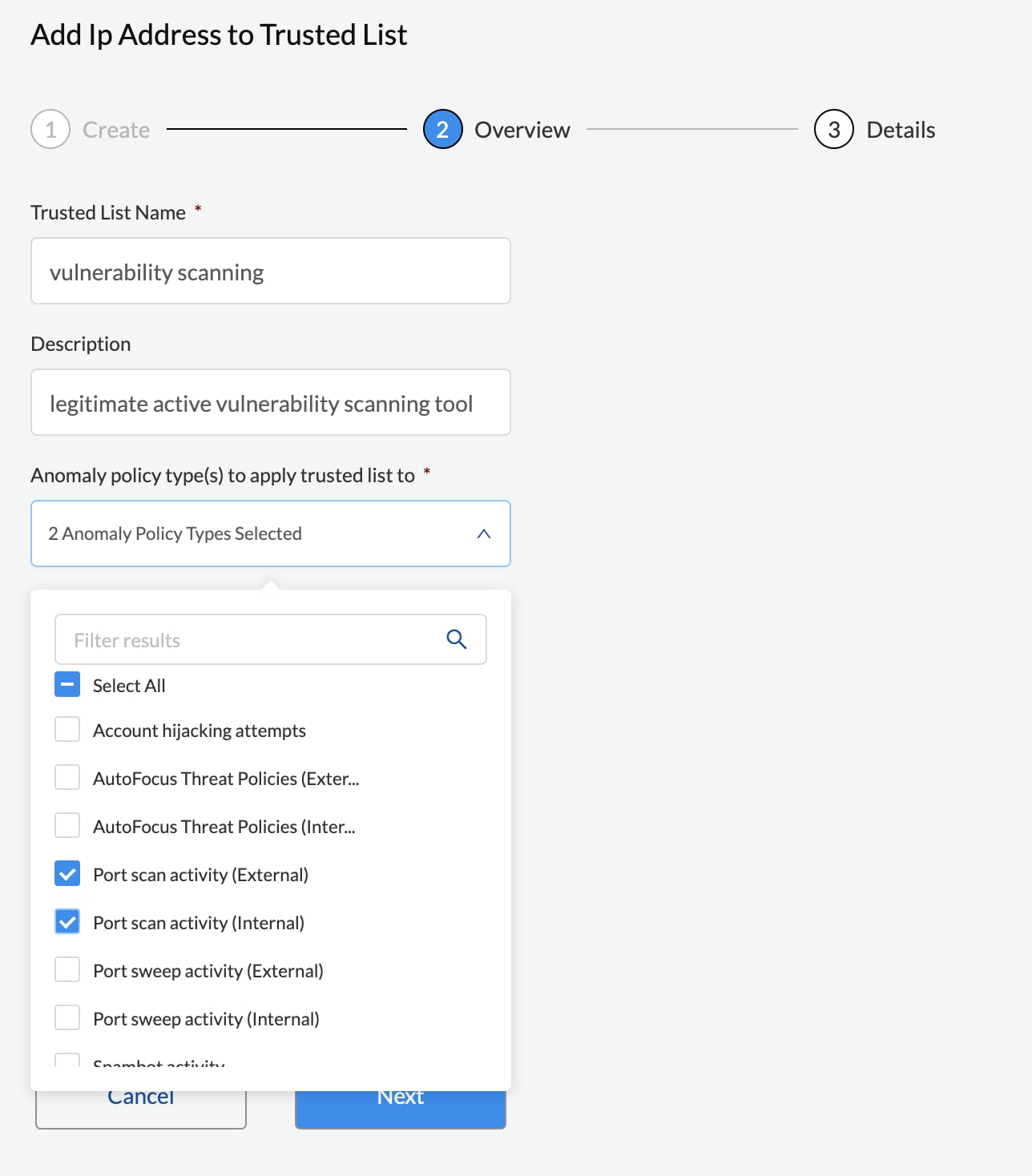
Step 3: Creating Trusted List to avoid alerting on legitimate behaviors
Some legitimate behaviors may trigger anomaly alerts, such as vulnerability scanning or PenTest tools. Alex adds the IP addresses that they use for the vulnerability scanning tool for internal security audit to a new Trusted List to prevent such activities from generating security alerts.
Step 4: Routing alerts to the right teams and channels
The SecOps team has different members assigned to take care of threat alerts for different business units. Alex creates one Alert Rule to send herself alerts related to the Account Group managing the mobile banking application team, and she creates another Alert Rule to send her team alerts related to the Account Group managing the equity trading application.
Some engineering teams prefer monitoring all alerts in their existing third-party platform, such as Splunk. Alex accommodates their needs and configures external integrations on Prisma Cloud for those third-party tools.
Step 5: Further customize configuration settings
After a while, Alex and her team would like to prioritize and focus on higher severity alerts for Unusual user activity, so Alex lowers the Alert Disposition threshold to “Conservative - Generate alerts for events with unusual location or both unusual service and unusual location” so it will only generate alerts on the more serious issues.
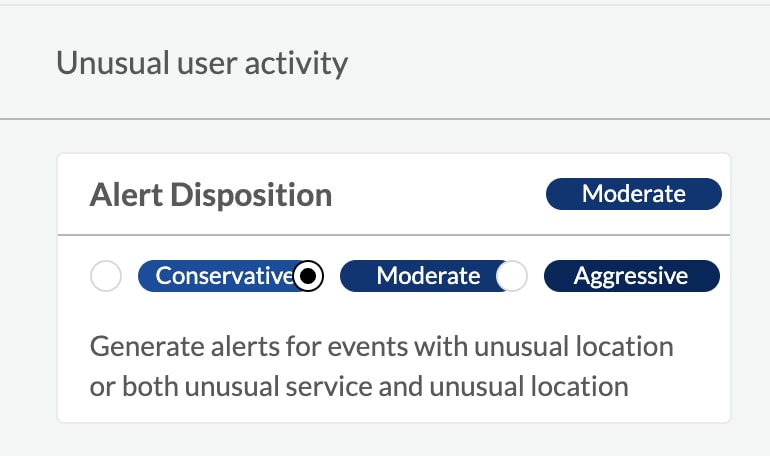
Step 6: Alert Investigation
After operationalizing the ML algorithms for the anomaly-based policies, Alex and her team are notified of an alert of “Unusual user activity” showing that certain users performed unusual activities in an unusual location (Mumbai, India) after working hours.
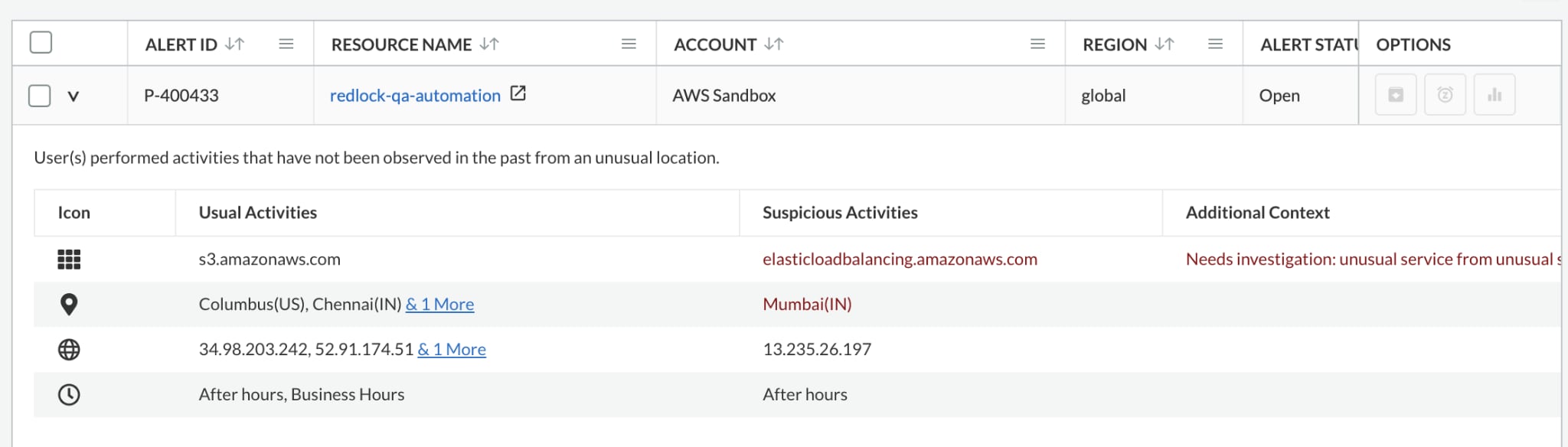
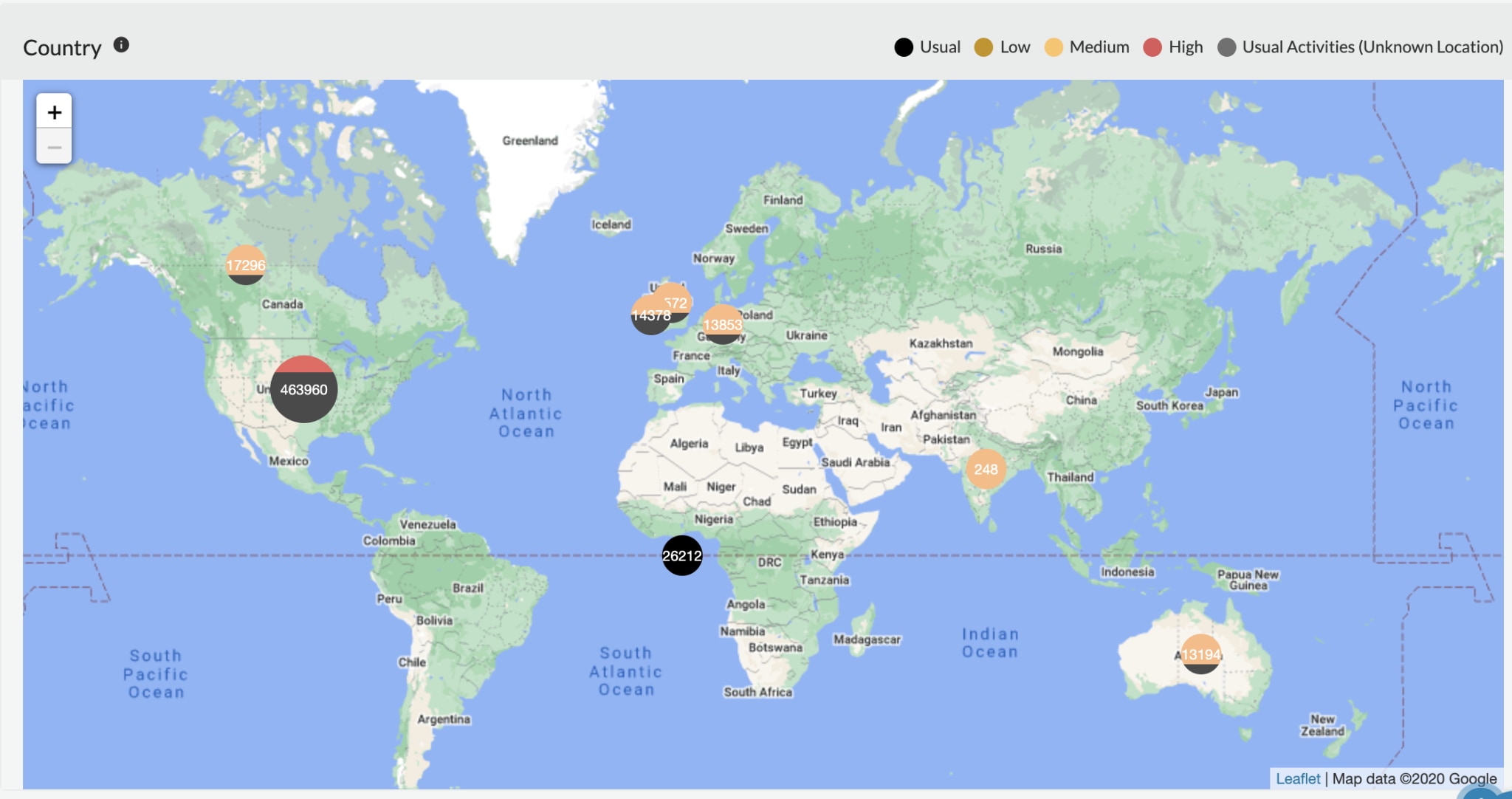
Alex is aware that the organization does not have a branch office or team working in Mumbai, and she quickly starts investigating it using the incident investigation capabilities within Prisma Cloud. She first checks the Map View to determine if the unusual activities are originating from multiple geo locations.
She then leverages the Trending View to review the normal activities as well as the abnormal activities, and immediately identifies the activities in India are anomalous.
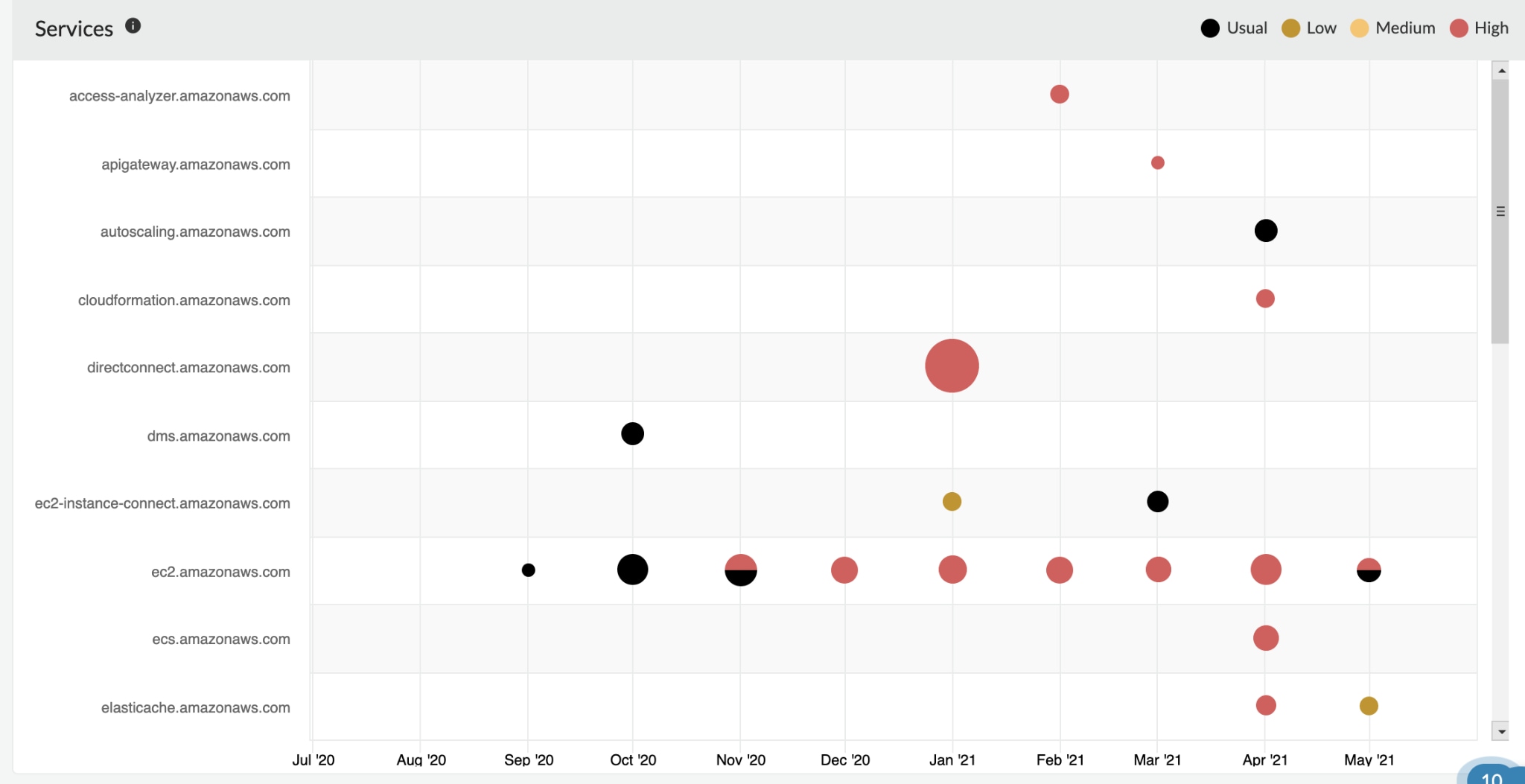
Her team discovers that the attacker obtained access into their cloud environment and was trying to connect to their server. However, Prisma Cloud’s Threat Detection capabilities promptly alerted her to the unusual activities along with providing highly contextual information. Alex and the team disable the impacted user accounts to prevent the attacker from executing other malicious activities, like data exfiltration or cryptojacking.
Using Prisma Cloud, Alex and her team are enabled to continuously monitor and investigate every threat detection alert such as the one described, as well as fine tune the Alert Disposition, Training Threshold and Trusted Lists so they can further optimize detection efficacy while minimizing false positives and false negatives. To learn more about Prisma Cloud’s threat detection capabilities, visit us here.
Related Blogs
Subscribe to Cloud Native Security Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.