Creating a Secure 5G Service-Based Architecture: Part 3 - Runtime Defense
In my previous blogs on vulnerabilities in 5G Service Based Architecture (SBA) security and on API security, we looked at the key capabilities for effective 5G security and examined what this means for vulnerability management and API security. In this blog, we’ll look at runtime defense, a form of autonomous learning to detect and prevent activity outside the learned model of a running container.
As a reminder, in the first 5G SBA blog, we identified the key capabilities for effective 5G security, which include:
- Vulnerability management for comprehensive coverage and monitoring, identifying, and preventing risks to all the hosts, images, and functions in your environment.
- Layer 7 visibility and security for web applications and APIs on any cloud native architecture.
- Powerful runtime defenses that apply automated protection against unwanted activity and threats.
- Compliance enforcement with pre-built compliance checks for centrally viewing and enforcing your own or industry compliance standards.
- Shift left security with CI/CD, repository, registry, and Open Policy Agent integrations to secure workloads across the Software Development Life Cycle (SDLC).
Runtime defense is a critical feature to ensure the security of running hosts, containers and even serverless functions. Palo Alto Network’s definition sums it up nicely:
“Runtime defense is the set of features that provide both predictive and threat-based active protection for running containers. For example, predictive protection includes capabilities like determining when a container runs a process not included in the origin image or creates an unexpected network socket. Threat-based protection includes capabilities like detecting when malware is added to a container or when a container connects to a botnet.”
Palo Alto Network’s runtime defense feature uses machine learning to create models for each and every running container in your cluster. In a 5G network where hundreds or more containers are running, relying on human engineers to create these models is not the right approach. These models need to be created quickly and accurately via machine learning. Prisma Cloud leverages AI and machine learning to create these automatically, greatly offloading the operational burdens of securely running a 5G network.
If we go into the Prisma Cloud UI, we can actually see the runtime model that was automatically created for a given container. For the fun of it, we will pick on the Session Mobility Function (SMF) and examine its runtime model.
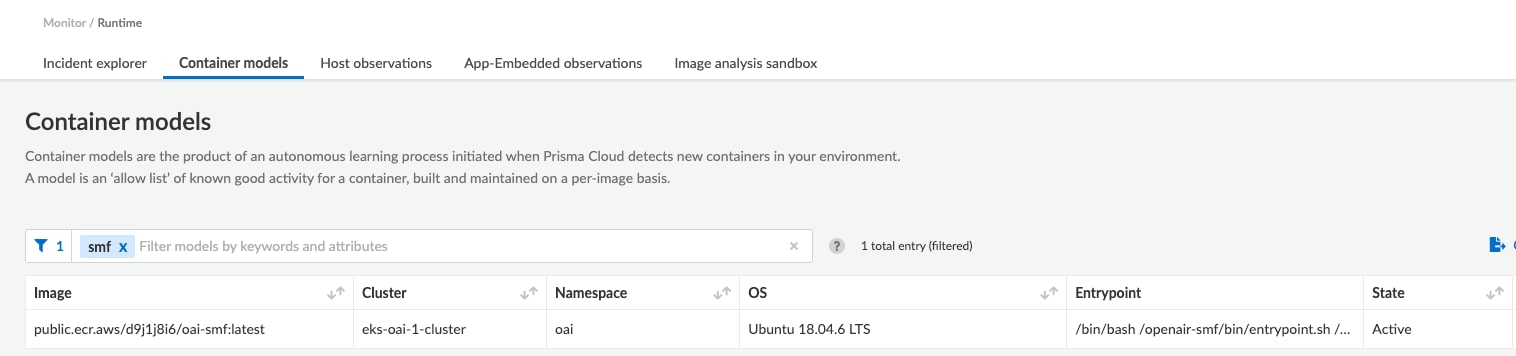
Once we start looking at the container model, we can see that there are categories like Process, Networking and Filesystem which show what was discovered statically as well as dynamically during the learning period.
Below are some of the things Prisma Cloud has in its model for the SMF in my environment.
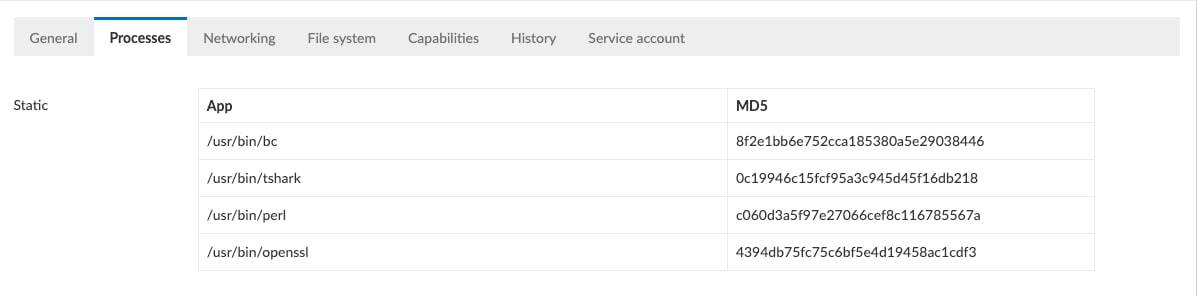
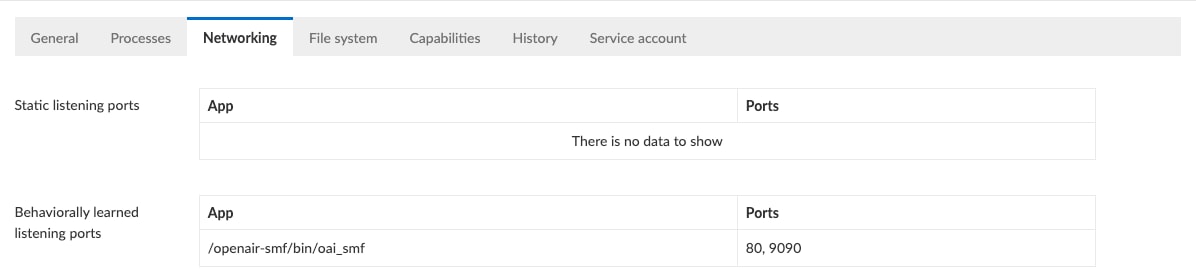
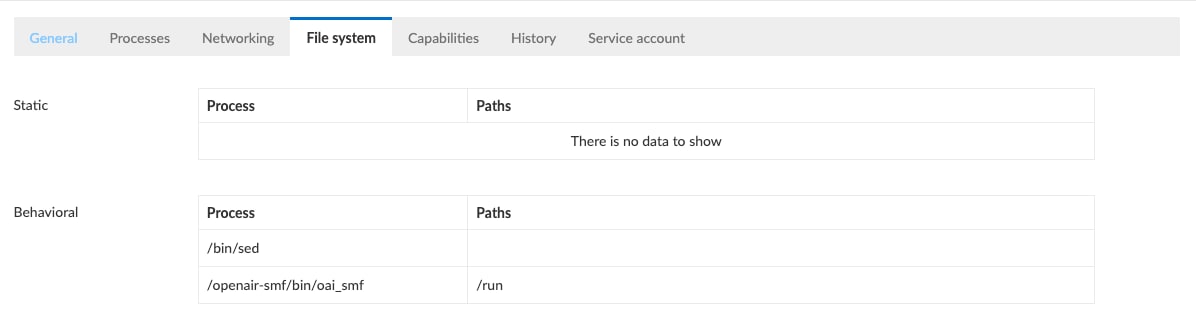
We see a list of the processes that have been observed running within the container, the ports being used (80 is for HTTP and 9090 is for HTTP/2), as well as learned file system behavior. It is important to emphasize that an admin did not have to enter this in, it was learned by the system. Going forward, Prisma Cloud will watch for any behavioral anomalies outside of this model.
These models are extremely important, as often attackers will take a “low and slow” approach which is hard to detect via network security alone. With runtime defense, we can catch anomalies that act as warning signs that something is not right.
To see runtime security in action, we will simulate an attacker who has gained access to one of our containers and is doing some reconnaissance. We will watch Prisma Cloud flag this activity as outside the normal model (we could have it blocked, but in this example we will just alert). To do this, we will exec into the running container and issue some commands. Once in we will have root access to the pod and can do whatever we want. Perhaps the first thing we want to do is see which processes are running. From the CLI of the container we can make sure the ps command is supported (using “which”), and then run “ps -ef”, which shows us the running processes.
# which ps
/bin/ps
# ps -ef
UID PID PPID C STIME TTY TIME CMD
root 1 0 0 Apr05 ? 00:02:10 /openair-smf/bin/oai_smf -c /openair-smf/etc/smf.conf -o
root 7118 0 0 16:06 pts/0 00:00:00 sh
root 12395 7118 0 16:19 pts/0 00:00:00 ps -ef
Modeling the “openair-smf” process in this example, triggering various runtime alerts.
We can see that the oai_smf process is running, and as an attacker we might start to look more closely at this and the directory it is running in. However, this act of running the “which” and “ps” command has triggered several runtime alerts. The “which” and “ps” processes are both not a part of the runtime model and were therefore flagged. Below we can see the detailed information Prisma Cloud provides for us, including the cluster, image, container, and specifics of the command.
Aggregated Events
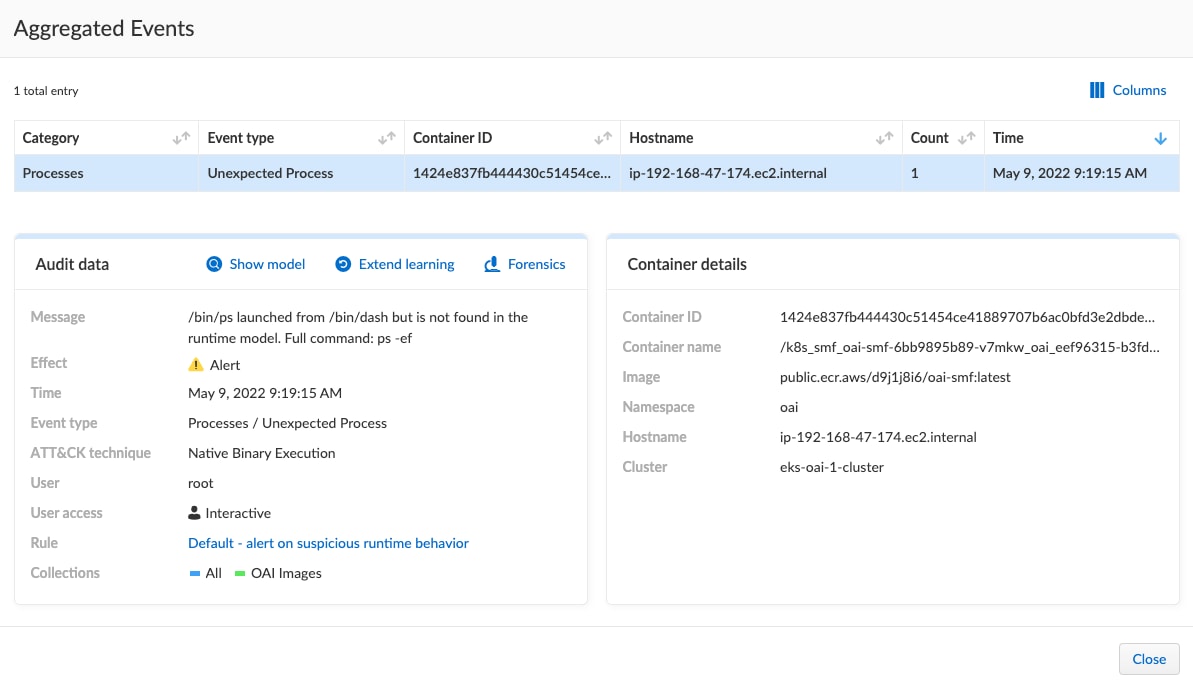
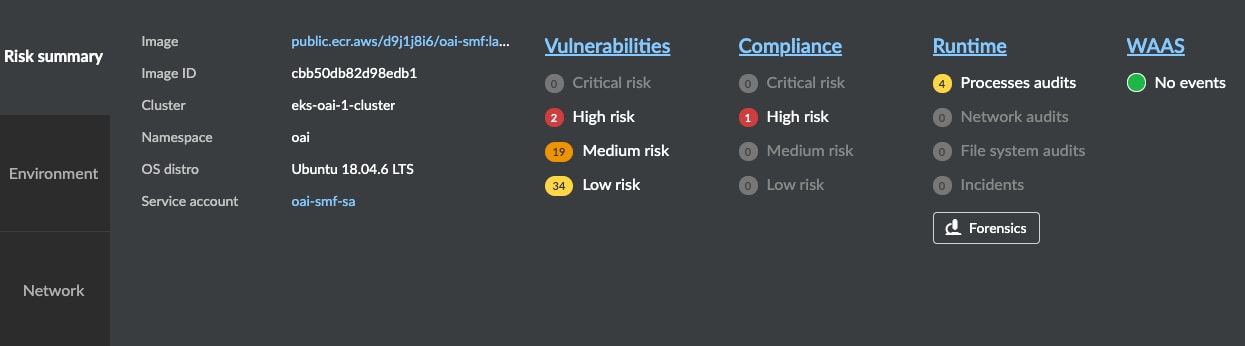
If we look again in Radar at my container, we can see the Runtime Process related events.
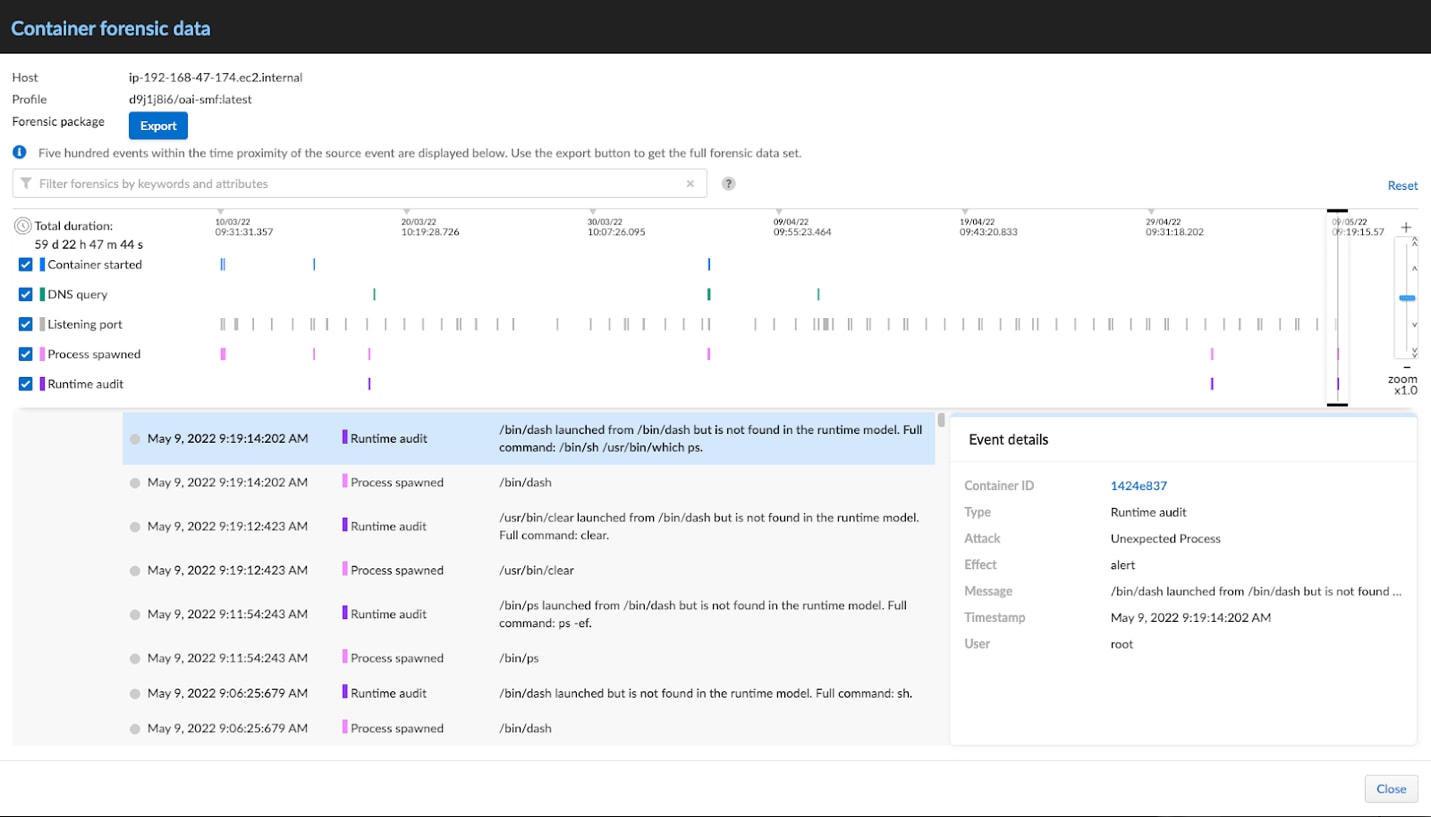
Digging deeper into the Forensics screen lets us see exactly what happened. Not only can we see the commands and processes that were spawned, but we see it on a timeline, so we know when each event happened relative to the others. Below you can see my activity while in the SMF (note, I also ran the “clear” command, which Prisma Cloud caught as well!).
It's worth noting that these alerts are available to you in numerous other channels as well, beyond just the user interface (UI). It's also possible (and recommended) to enable integration of key events (e.g., Container Runtime, WAAS, etc.) with backend tools used by your organization for monitoring. For instance, Prisma Cloud could send an email when it saw an event like the ones above, or send you a Slack notification, or even open a Jira ticket. Numerous options are supported to cater to each organization's preference.
Running a 5G core network is not an easy task. Keeping tabs on the expected and valid behavior of all the running workloads is even harder. For effective security operators and enterprises will need to rely on ML and products like Prisma Cloud to offload these tasks and make the job of securing their environment an easier one.
Summary
As cloud native application development becomes the de-facto method for building and delivering 5G services and applications, organizations must adopt a modern cloud-native application security solution that provides end-to-end security and defense-in-depth.
Prisma Cloud is at the bleeding edge of cloud native security and provides customers with the most comprehensive security capabilities necessary for protecting their entire 5G cloud native application stack.
To test out all the great functionality and more with Prisma Cloud’s WAAS module, request a hands on demo here.
Related Blogs
Subscribe to Cloud Native Security Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.