Anomaly Detection Policies for Unusual Workload Credential Usage
Cloud computing is an essential component of modern business operations, providing numerous benefits — scalability, flexibility and cost-efficiency among them. But cloud computing comes with risks, particularly in terms of security and privacy. Sensitive data and critical applications can become compromised through breach and unauthorized access.
Detecting malicious behavior in cloud environments, however, is challenged by the tendency for malicious activities to be logged merely on the control plane level — without recording traces in traditional log sources. Unwanted data movements between cloud services or accounts appear only in cloud-native logs like AWS CloudTrail or AWS Config and not in network or operating system logs.
Risks of Exfiltrating Temporary Credentials from Compute Instances
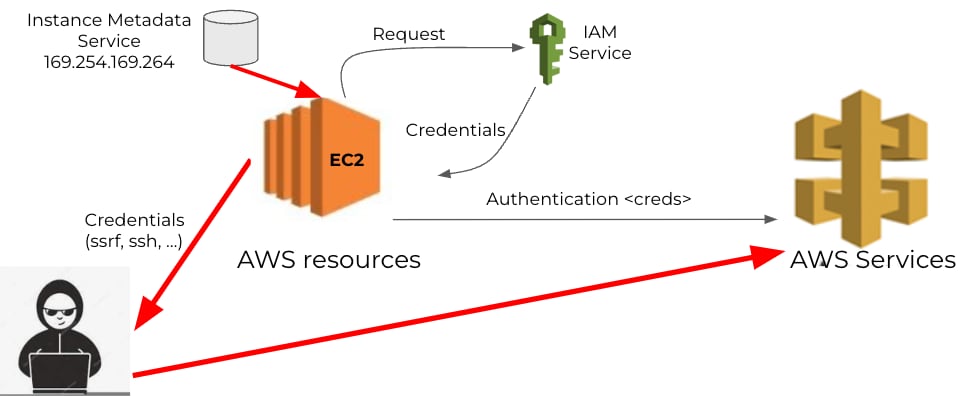
Cloud computing resources, such as EC2 instances, require appropriate authentication and authorization to perform tasks. In AWS, for example, you’d typically assign a role to the compute resource during deployment. The role comes with a set of temporary credentials, which the instance will renew every period. The temporary credentials are stored in the instance metadata service (IMDS), which can be accessed through a REST API call from the EC2 instance.
If an attacker manages to trigger a REST API call to the IMDS service from the target EC2 instance, they can exfiltrate the credentials and use them from a different instance or even a machine external to the AWS cloud. This would give the attacker full privileges of the EC2 instance from where the credentials were extracted.
Detecting Suspicious Workload Credential Use with Prisma Cloud
To effectively secure sensitive data and infrastructure from attacks stemming from unauthorized credential use, Prisma Cloud has added to its cloud infrastructure entitlement management (CIEM) capabilities with the release of two anomaly policies designed to detect anomalous use of workload credentials.
The two policies are designed to identify when a credential assigned to a workload resource is used outside of the resource context. This behavior could indicate an attack or, in the least, unusual use of resource credentials. These policies are classified under the MITRE ATT&CK framework, a globally recognized knowledge base of adversary tactics and techniques.
Overview of the New Policies
We designed the unusual usage of workload credentials anomaly policies to detect when a credential assigned to a workload is used by a different workload or device. To achieve this goal, the policies required the collection of all IP addresses assigned to an EC2 instance. Then, if a WRITE audit event is triggered using the EC2 instance credentials, but from an IP address unassociated with the instance, an alert will be generated. To facilitate the interpretation of the anomalous behavior, we created two policies:
- Unusual Usage of Workload Credential from Outside the Cloud: This policy detects when the anomalous IP address is outside the IP address space of the cloud provider.
- Unusual Usage of Workload Credential from Inside the Cloud: This policy detects the case when the anomalous IP address is inside the IP address space of the cloud provider.
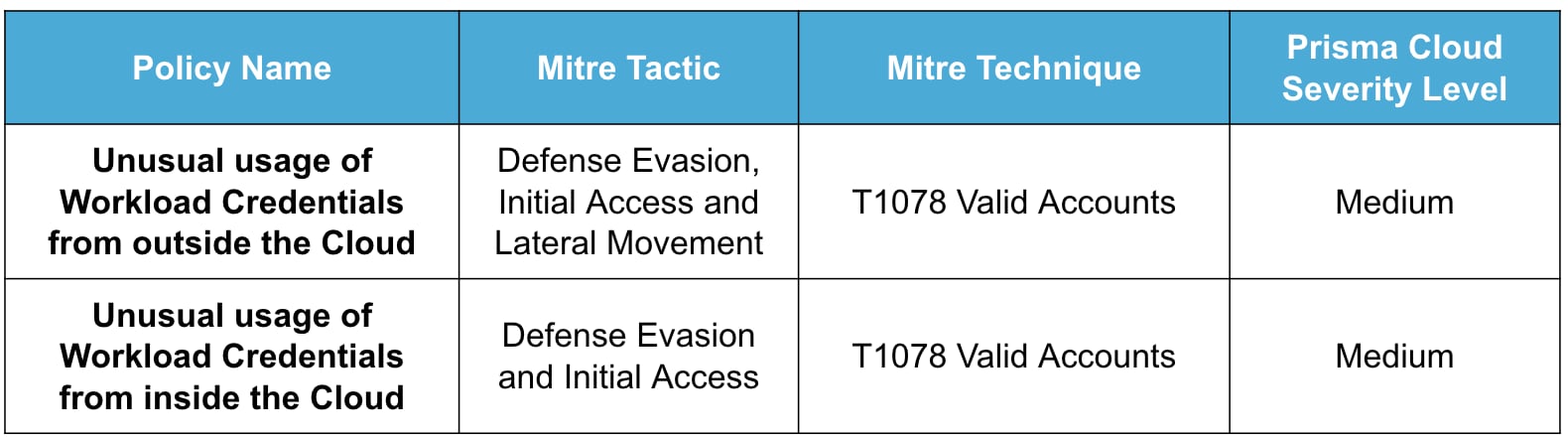
The policies are classified under the Mitre Att&ck framework as:
Anomaly Detection Technique
The two policies for unusual usage of workload credentials work similarly. Both use a two-phases approach to identify incidents that will generate alerts for a customer.
Learning
We first look for AssumeRole events, which indicate an instance requesting a new set of credentials. This event makes the logic add the instance and corresponding role to a model of normal behavior. After we see the first activity from an instance, we will record the IP address. In addition, we will augment this data with other IP addresses for the instance, which will come from the metadata that we’ve collected (e.g., there could be multiple IP addresses per interface, multiple interfaces for the instance, or changes in the IP assignment). At the end of this process, we’ll have a collection of IP addresses per instance.
Note that if there is no activity from an instance, all the state for it will be deleted. This is because it’s common for instances to last a short period, especially in environments where autoscaling is enabled. The purging process will keep our state table small.
Detection
The policies compare the source IP address from where a WRITE audit event is generated to the IP addresses of the instances in the state table. If there’s a discrepancy, an alert will be raised. If the offending IP address is outside the IP address space of the cloud provider, an unusual usage of workload credential from outside the cloud alert will be triggered. If the offending IP address is within the cloud provider’s IP address space, an unusual usage of workload credential from inside the cloud alert will be triggered
Policies in Action
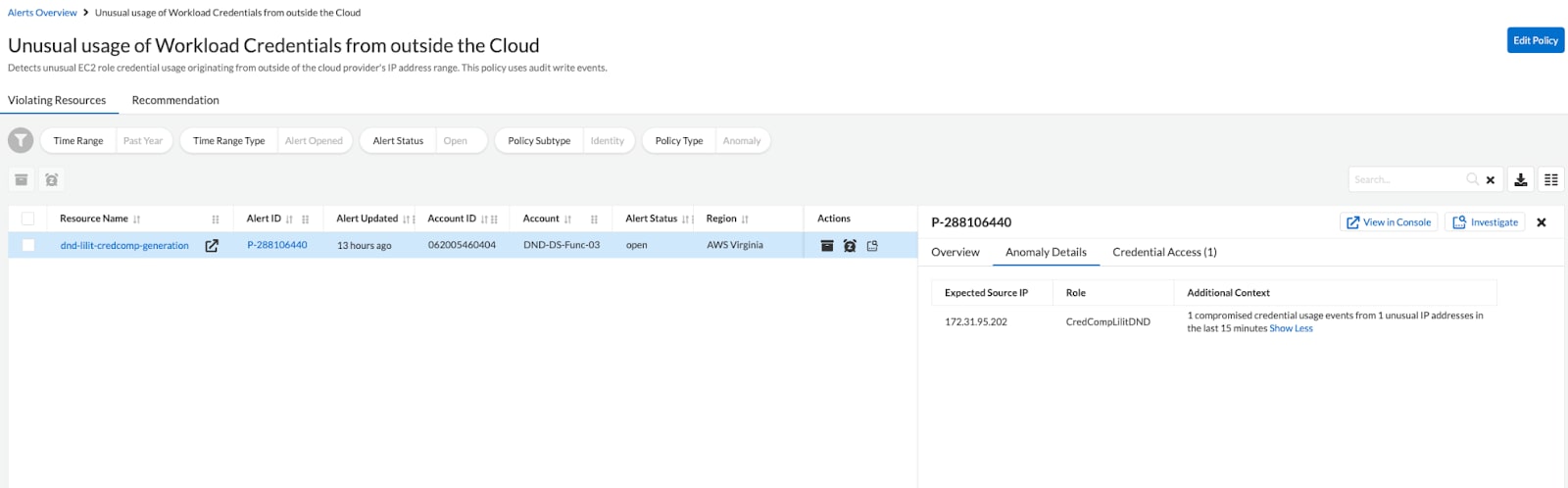
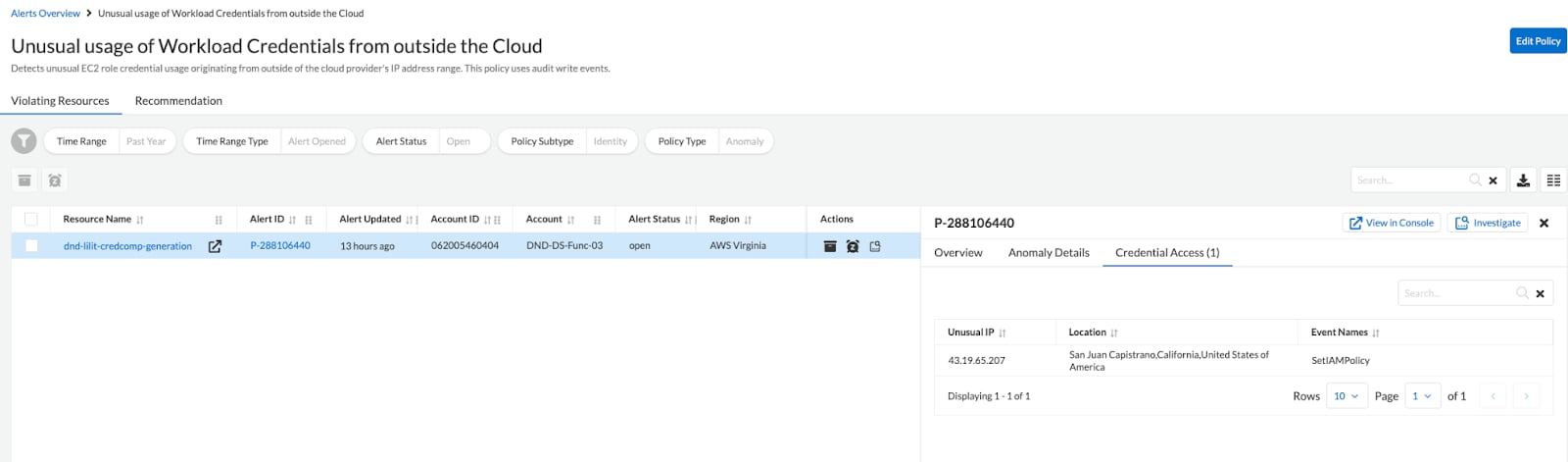
Figures 2 and 3 show an example of an unusual usage of workload credentials from outside of the AWS cloud detected by Prisma Cloud. As depicted in figure 2, the resource named dnd-lilit-credcomp-generation is expected to use IP address 172.31.95.202 to communicate with AWS services. But in figure 3, we can observe that a new IP address is using the credentials of the resource. The anomalous IP 43.19.65.207, which is outside of the AWS IP address space, triggers the anomalous behavior.
The unusual usage of workload credentials anomaly policies are an essential tool for detecting compromised credentials used in cloud computing environments. With the use of these policies, organizations can better protect their resources against possible attacks and unauthorized access.
Learn More
Learn more about the CIEM and Threat Detection capabilities of Prisma Cloud and take it for a free 30-day test drive to experience the advantages firsthand.
Related Blogs
Subscribe to Cloud Native Security Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.