How Cortex Xpanse Can Identify CISA-Identified Known Exploited Vulnerabilities
This post is also available in: 日本語 (Japanese)
What Cortex Xpanse does today
In late 2021, the U.S. Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (DHS/CISA) issued Binding Operational Directive 22-01 (BOD 22-01), which introduced a list of Known Exploited Vulnerabilities (KEVs) that threat actors have exploited. Cortex Xpanse can help users to find potentially-impacted services for further investigation, patching, or decommissioning via the new Software Potentially Impacted by CISA Known Exploited Vulnerabilities (BOD 22-01) Issue category.
As of this writing, CISA’s Known Exploited Vulnerabilities catalog accompanying BOD 22-01 contained 788 individual Common Vulnerabilities and Exposures (CVEs), impacting at least 322 unique products and services, approximately 57% of which face the public internet. These numbers continue to increase steadily as CISA adds new CVEs to the catalog.
Xpanse Issue Policies Aligning to CISA’s Known Exploited Vulnerabilities (KEV) Catalog
(Updated: 8/1/2022)
This section includes all Xpanse Issue policies that enumerate potentially vulnerable products and services in the KEV catalog. We will continually update this list as our research and development teams add detection capabilities to our product.
Expander shows systems that are exposed to the public internet, without the need to install agents or sensors of any kind. Some of the systems below do not advertise version information, or are otherwise restricted from doing so depending on the configuration of our customers’ networks. Expander attempts to retrieve or derive version information and other metadata, but this is not possible in all cases.
We are able to determine some devices/applications with a higher degree of confidence and thereby infer vulnerability to specific CVEs in the KEV catalog. The insecure versions of the following services fall into that category, and have been automatically enabled as Issue Policies in Cortex Xpanse:
- Apache Druid
- Apache Web Server
- Atlassian Confluence Server
- Atlassian Crowd Server
- Cisco Small Business RV Series Router
- Citrix Application Delivery Controller
- Drupal Web Server
- Exim Mail Transfer Agent
- Hikvision Device
- Microsoft Exchange Server
- Mikrotik Router
- MobileIron Sentry
- PHP
- SolarWinds Orion Platform
- SolarWinds Serv-U
- Sumavision Enhanced Multimedia Router
- Telerik Web UI
- Zoho ManageEngine ServiceDesk Plus
Other devices/applications do not provide this level of visibility, though Xpanse is still able to identify the presence of the active internet-facing service. These applications have Issue policies that can be enabled by your team in the Policies tab; we encourage our customers to toggle them to “On” as needed.
- Accellion FTA
- Adobe ColdFusion
- Adobe Commerce
- Adobe Flash
- Apache Active MQ
- Apache Log4j*
- ApacheShiro
- Apache Solr
- Atlassian Jira Server
- Cisco Adaptive Security Appliance
- Cisco Duo SSO
- Cisco Firepower Device
- Cisco HyperFlex
- Cisco IOS
- Cisco IOS XE
- Cisco IOS XR
- Cisco Unified IP Phones
- Citrix SD-WAN
- Citrix ShareFile Server
- Citrix Workspace
- Citrix XenMobile Server
- DrayTek Vigor Router
- Elastic Kibana User Interface
- Elasticsearch Server
- EmbedThis GoAhead WebServer
- F5 Advanced Web Application Firewall
- F5 BIG-IP Access Policy Manager
- F5 BIG-IP Platform
- F5 BIG-IP TMUI
- ForgeRock Access Management Server
- Fortinet FortiOS
- Fortinet Fortigate SSL Vpn
- Hikvision Device
- IBM Planning Analytics
- IBM Websphere Application Server
- Kaseya VSA
- Liferay Portal
- Log4Shell Vulnerable Apache Solr
- Log4Shell Vulnerable IBM WebSphere Application Server
- Log4Shell Vulnerable SonicWall Email Security
- Log4Shell Vulnerable VMware Workspace ONE Access Server
- Microsoft OWA Server
- MikroTik Router
- MongoDB Mongo-Express
- Nagios Fusion
- NetGear ProSafe
- Netis Router
- October CMS
- Oracle WebLogic Server
- PAN-OS Device
- Pulse Secure Pulse Connect Secure VPN
- rConfig Network Configuration Management
- RDP Server
- Redis Server
- Roundcube Webmail
- SaltStack Server
- SAP NetWeaver Application Server
- SharePoint Server
- SMB Server
- SonicWall Email Security
- SonicWall Secure Mobile Access VPN
- SonicWall Secure Remote Access
- Sophos SG Series Firewall
- Sophos XG Series Firewall
- Symantec Messaging Gateway
- Synacor Zimbra Collaboration Suite
- Tenda Routers
- ThinkPHP Application
- Tomcat Web Server
- vBulletin Web Server
- VMware ESXi
- VMware Spring Framework
- VMware vCenter Admin Page
- VMware Workspace ONE Access Server
- VMware Workspace One Administrative Configurator
- Zabbix IT Monitoring Software
- Zoho ManageEngine ADSelfService Plus
- Zoho ManageEngine Desktop Central
- Zyxel Firewall
- vBulletinWebServer
Customers can leverage this basic enumeration for quick identification of active internet-facing services and export of an audit list for patching. For Cortex XSOAR customers, Xpanse integration leverages the outside-in perspective to automatically check for exposed software, and in some cases record the detected versions and queue other actions.
Surfacing KEV Exposures in Expander → Issues Module
Xpanse groups Issue types into categories or themes to make them easier to browse and filter. We’ve created a new Issue Category called Software Potentially Impacted by CISA Known Exploited Vulnerabilities (BOD 22-01) containing all existing policies covering software potentially affected by CVEs in the KEV catalog. This section offers a walk through of the user experience for enumerating assets that may be impacted by a KEV.
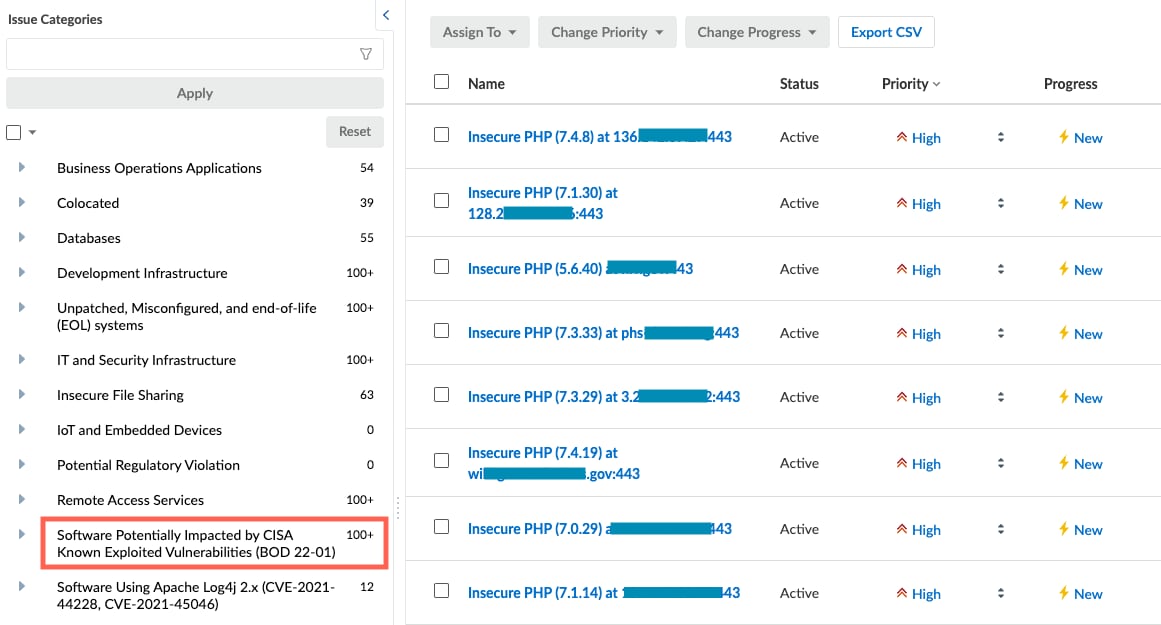
To find a particular Issue of interest, scroll through the list [1] or start typing the name of the Issue in the search field [2], select from the list that populates below, then click Apply [3].
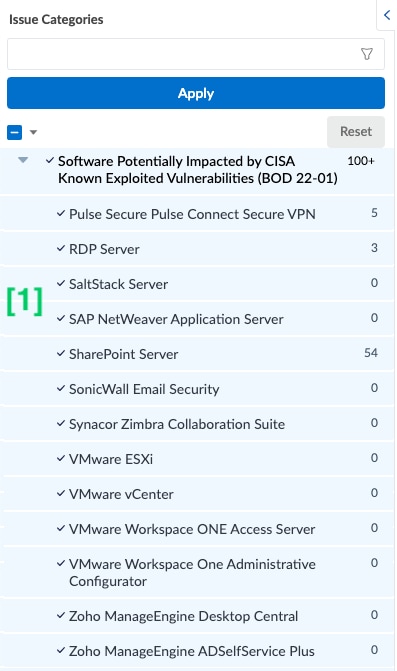
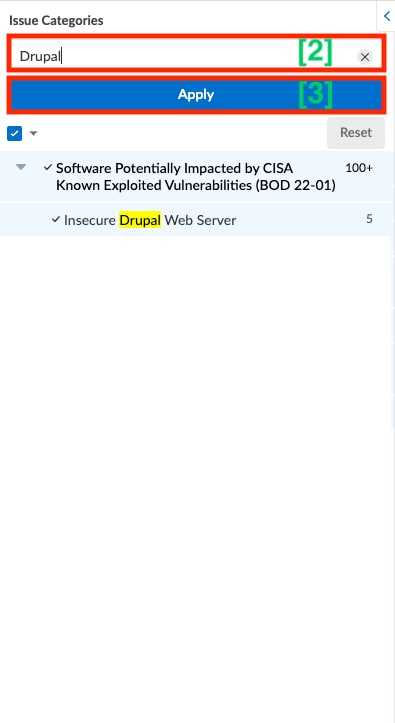
As you select individual Issues, Xpanse’s cumulative findings will populate within the list view in the main part of the screen:
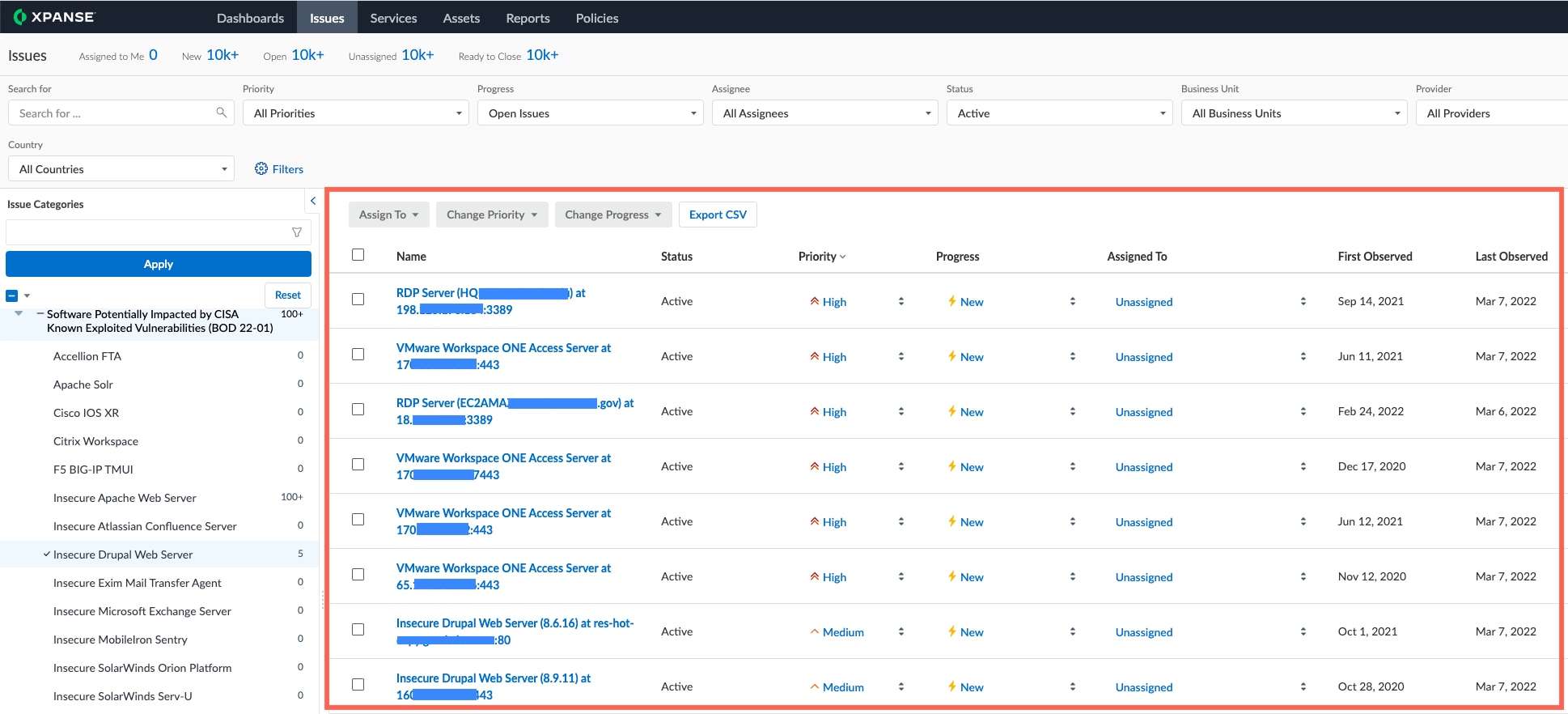
To export this list as a comma separated values (.csv) file, click the Export CSV button:
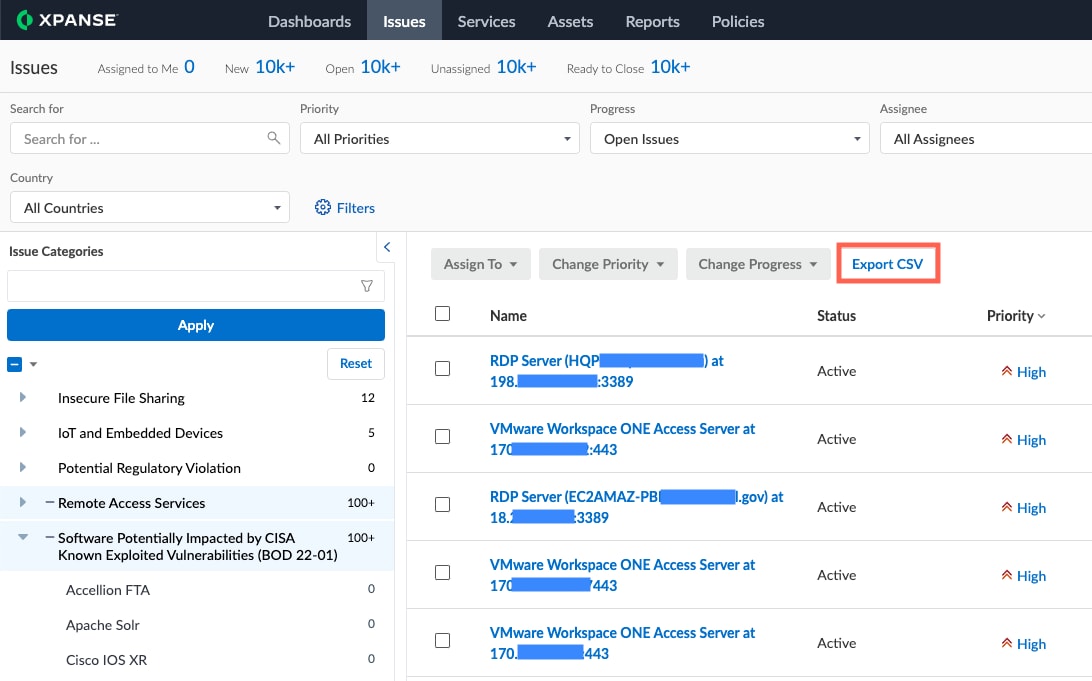
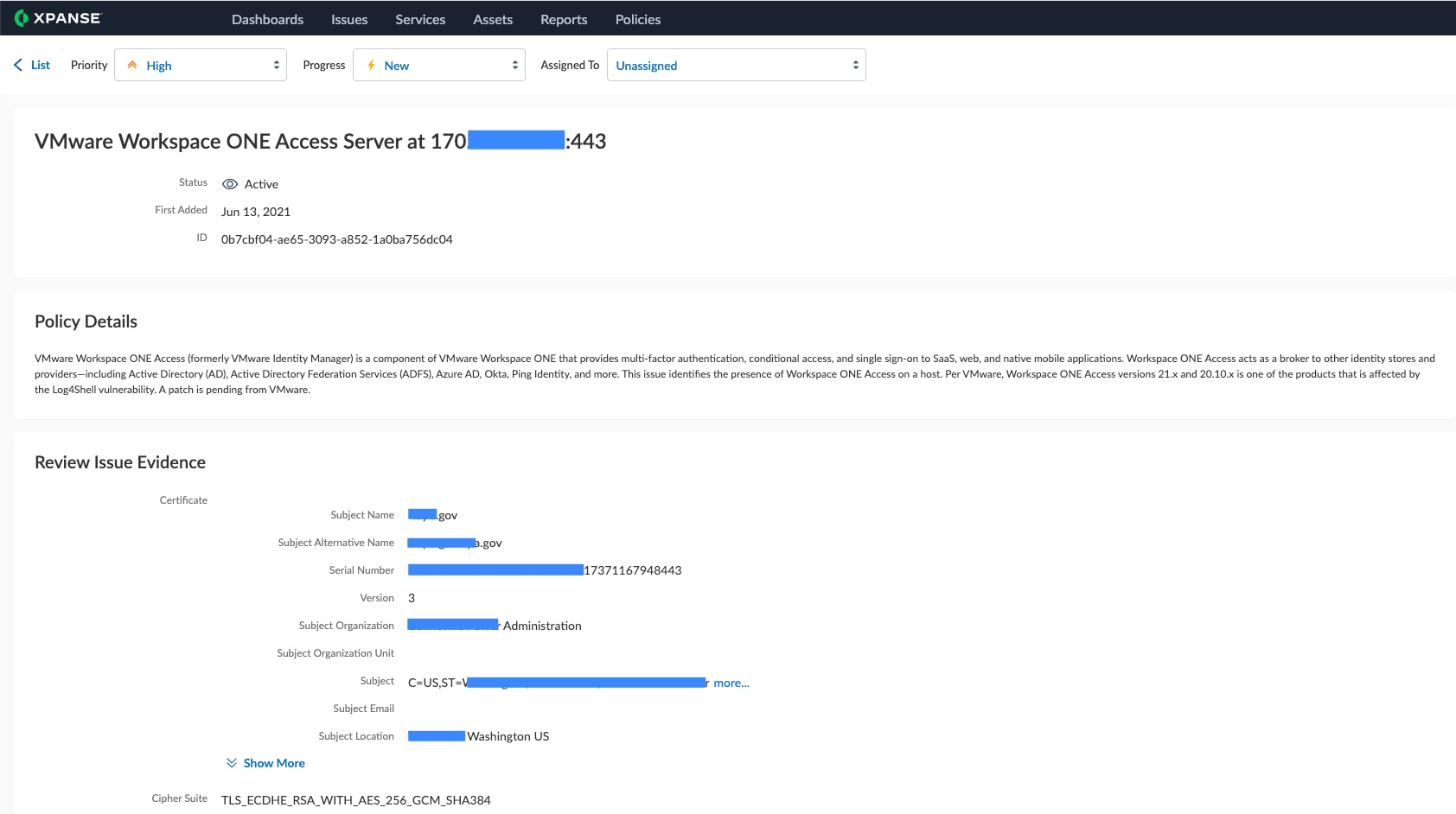
To get more information on an individual Issue on the list, click into it in the list view:

This will open the Issues details view, with information on the specific exposure and why Xpanse flagged it, where it was found on your network, and any IP ranges, certificates, or domains associated with the observation:
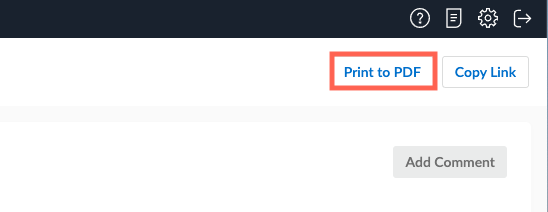
To created a detailed, shareable report on the selected Issue, use the Print to PDF button:
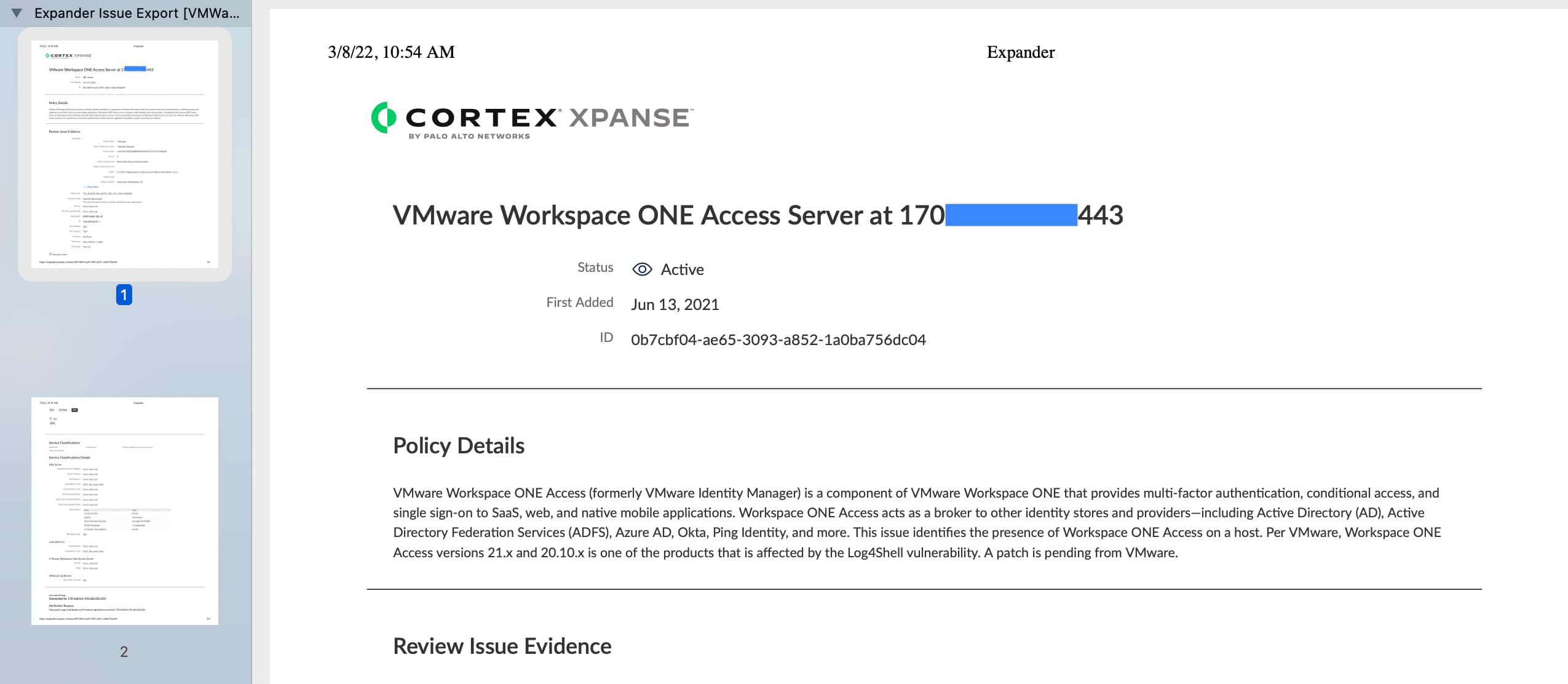
This generates a .pdf summary of Issue details, including all the information for that Issue in Expander:
Related Blogs
Subscribe to Security Operations Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.