To achieve operational security, federal agencies have had to expand their capabilities over the years. These expansions have moved from network enforcement points, such as firewalls and IPS, to the examination and control of applications and the data moving through those applications with DLP systems.
In the early days, the internet SSL was something of an anomaly with only a few sites utilizing transport encryption. But the explosion of cloud-based services (IaaS, PaaS, SaaS), such as Office 365 and Gmail as well as e-commerce and online banking, has driven the utilization of SSL from what was once maybe a 10 percent slice of the internet to well over 50 percent and, in some cases, upwards of 70 percent. In order for these security chains to continue to secure their organizations, they have had to adopt SSL decryption within their chains. This has led to costly, highly complex, and difficult to manage environments.
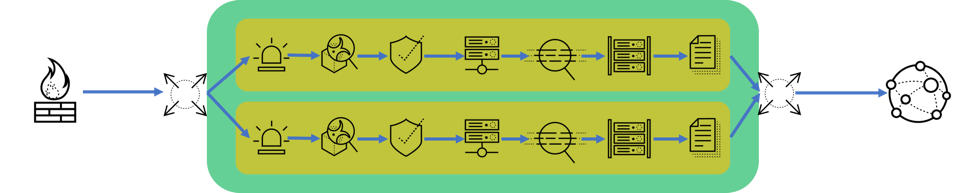
Fig 1. Traditional Security Chains between Load Balancers
The utilization of SSL services on the internet continued to increase, and these security chains could no longer handle the amount of traffic they were required to inspect. In order to scale to meet the inspection and enforcement needs, two options for SSL decryption were introduced within the security chains:
- Each device in the chain decrypts and inspects the traffic as it moves through the chain. This introduces an extreme amount of latency as each security device in the chain must now decrypt, inspect, and encrypt the traffic before sending it along to the next device.
- Specialized SSL decryption and load balancing appliances were installed to shoulder the burden of decryption and balance traffic across multiple chains. As these devices and more chains were added to accommodate needs, the costs related to installation, operation, and maintenance continued to rise.
SSL-encrypted traffic continues to grow exponentially, and agencies need the ability to handle the decryption of traffic for these security chains in a simplified and easy-to-manage manner. Palo Alto Networks Decryption Broker, which we announced as part of the PAN-OS 8.1 launch, is able to handle this traffic at scale, with minimal performance impact, allowing for the full benefits of the Palo Alto Networks Next-Generation Security Platform to examine for known and unknown threats before handing sessions off to the third-party devices within the security chain. Here’s how it works:
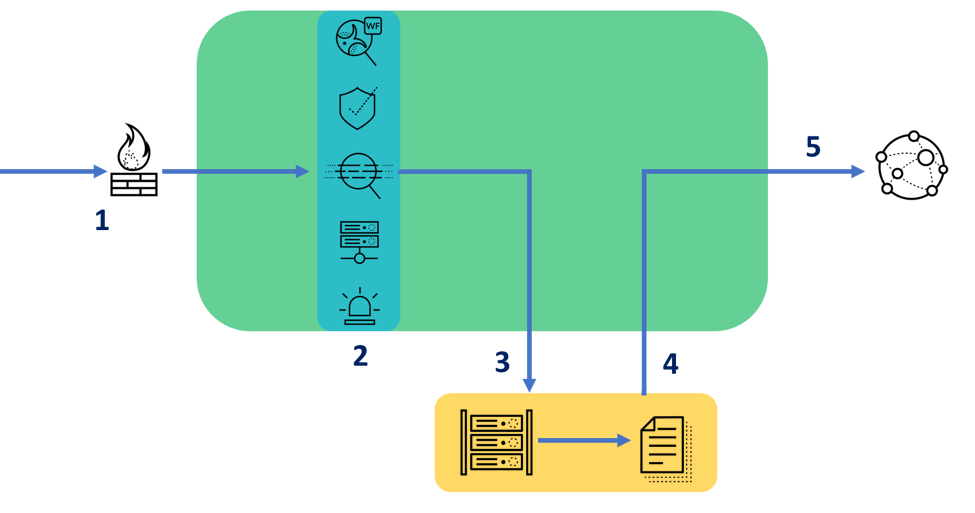
Fig 2: Palo Alto Networks Decryption Broker
- Ingress traffic is examined against the initial security policy. If it passes, it is sent to be decrypted.
- Decrypted traffic is examined for onboard content and threats, based on the attribution of user and application identification in addition to the verdicts rendered out of the content and threat engines.
- Once traffic passes onboard checks, the decryption broker then forwards traffic into the security chain to inspect the now decrypted traffic and render verdicts, scrub data, etc.
- The traffic is returned to the firewall through the second decryption broker interface.
- Egress traffic is encrypted and forwarded to the destination.
With the closed loop forwarding of these security chains, control of the decrypted data is isolated from the standard network based on the agency’s segmentation policy. These chains can be constructed in either a Layer 3 (IP-forwarded) or Layer 2 (MAC-forwarded) deployment ensuring the isolation hop to hop before the traffic is returned to the firewall for encryption and forwarding.
Our SSL Decryption Broker can greatly simplify the network and security architecture by integrating the core functions of URL Filtering, Threat Inspection, and WildFire into the Decryption Broker. This allows the elimination of security appliance sprawl and consolidation of technologies into the Palo Alto Networks platform. The simplification of this environment has many additional benefits, such as the simplification of troubleshooting issues that will arise in the security chain. Lastly, the management of the environment is greatly simplified, allowing for a standardization of security and decryption policy and further allowing it to be deployed at scale.
For more information about the configuration of SSL Decryption Broker, please review the forthcoming PAN-OS 8.1 Admin Guide and learn what’s new in PAN-OS 8.1.