Employee remote work continues to challenge the security measures of organizations. Is the user who keeps trying to access your cloud applications from Boston really Amelia in HR, who logged in this morning from your Portland, Oregon HQ? Identifying suspicious user activity based on anomalies is one way to combat potential threats.
The Cortex XSOAR Impossible Traveler content pack can help to automatically determine the legitimacy of remote access attempts and take appropriate steps to contain malicious user activity. Learn more about how you can automate response to alerts warning of suspicious login activity from uncommon locations or risky IP addresses.
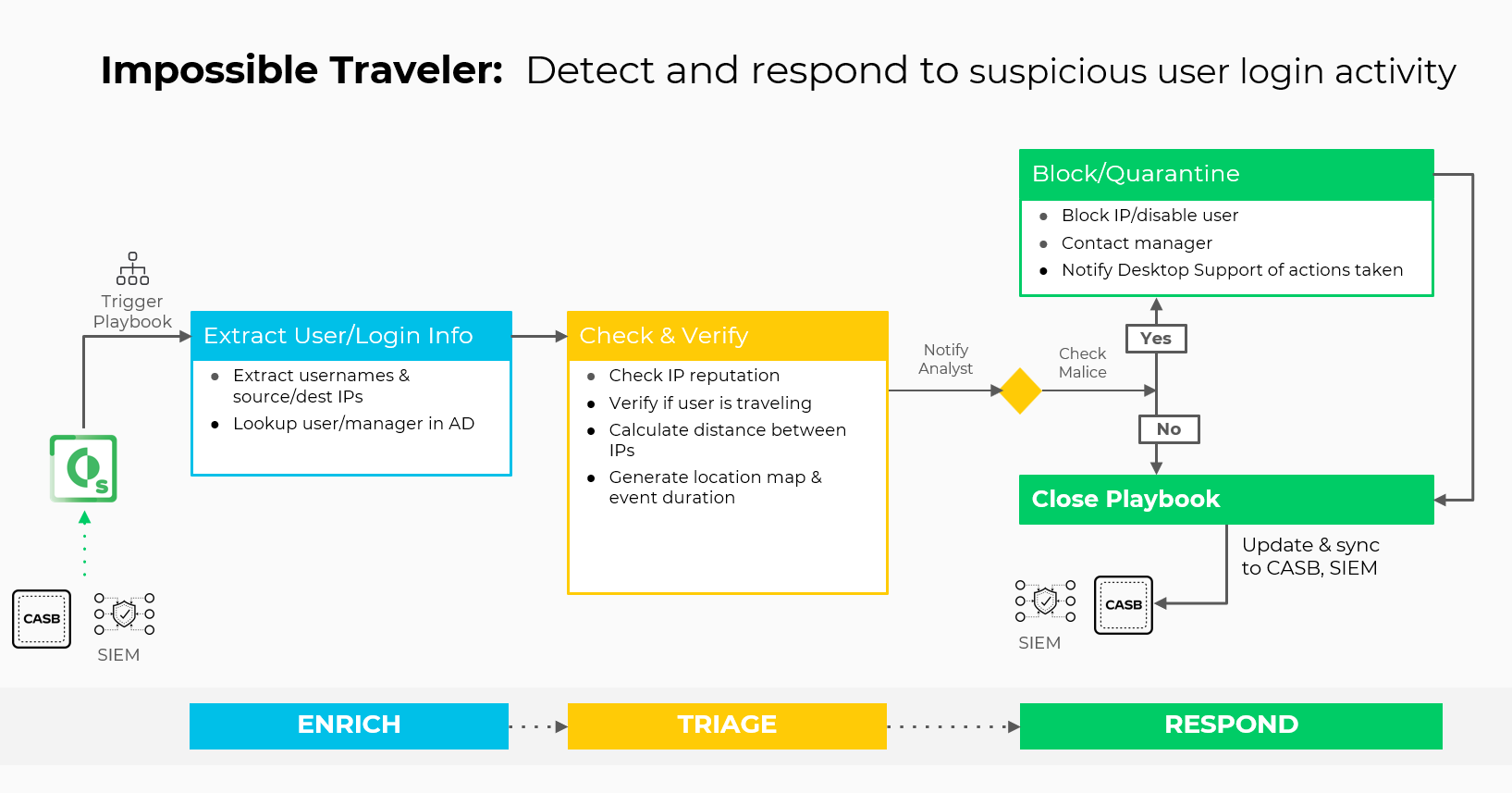
What does this pack do?
- Gathers IP-based information from the addresses used to initiate the connections
- Retrieves information about the user account that initiated the connections
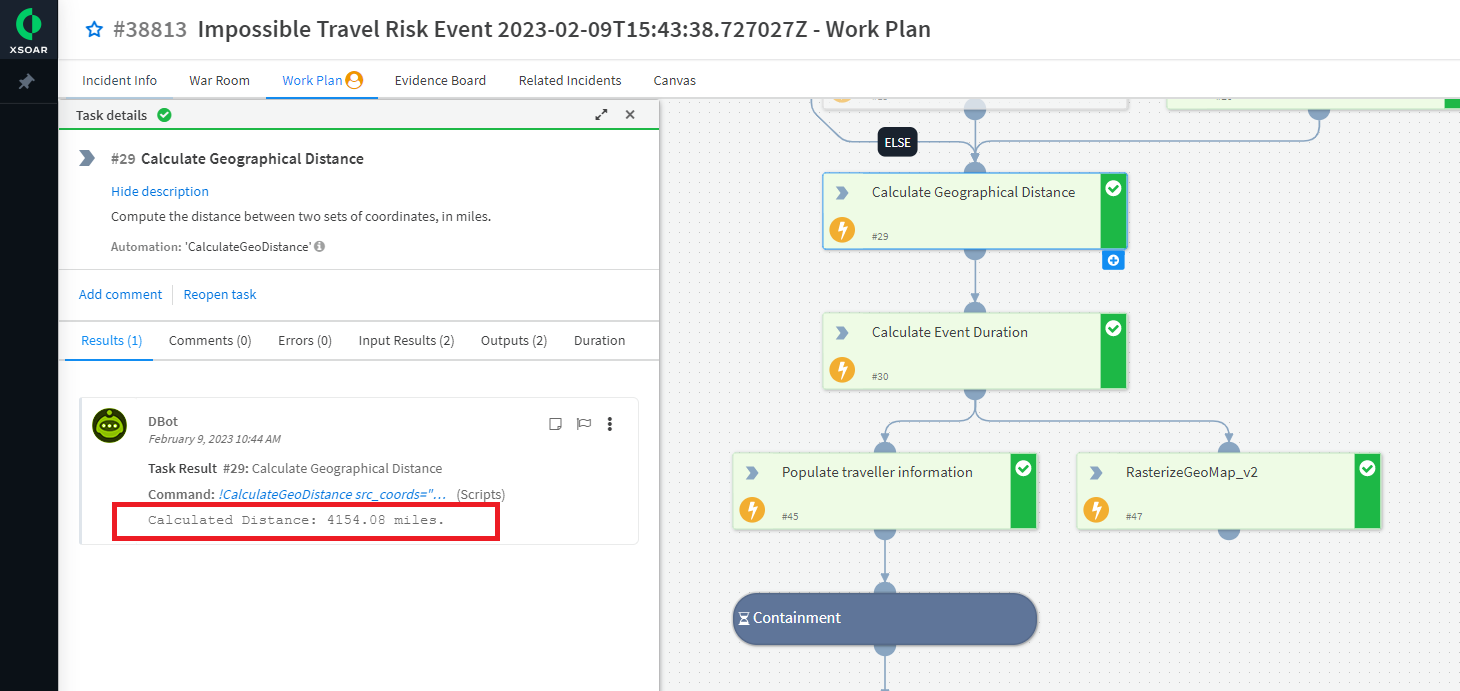
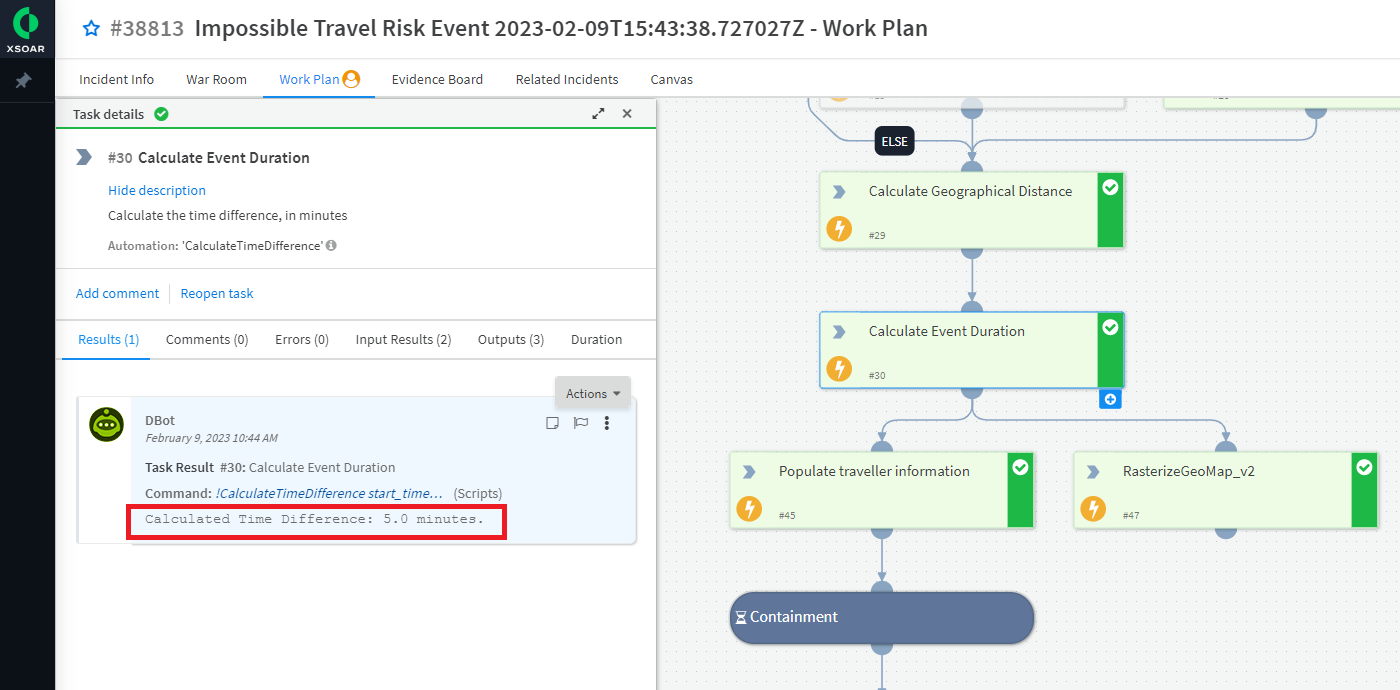
- Calculates the time and distance between user login attempts
- Generates a geographical map of the deduced travel path of the user
- Determines, based on IPs, allow list entries, manager decision, and supposed speed of travel, whether the traveler is an impossible traveler
- Allows the analyst to block IPs from the user and disable the user in case of compromise
Let’s catch the Impossible Traveler
The Impossible Traveler content pack includes out-of-the-box incident fields, layouts, and an incident playbook for impossible traveler investigations, all easily customizable to suit the needs of your organization. The playbook ingests detection alerts that have identified user activity originating from geographically distant locations.
Let’s see it in action: Triggered by an alert coming from a SIEM, the playbook pulls in user details from Active Directory as well as manager account information. Simultaneously, it enriches IP information by checking the reputations of associated IP addresses using existing threat intelligence tool integrations. By calculating the distance between IPs, a location map calculates geographical distance and generates event duration.
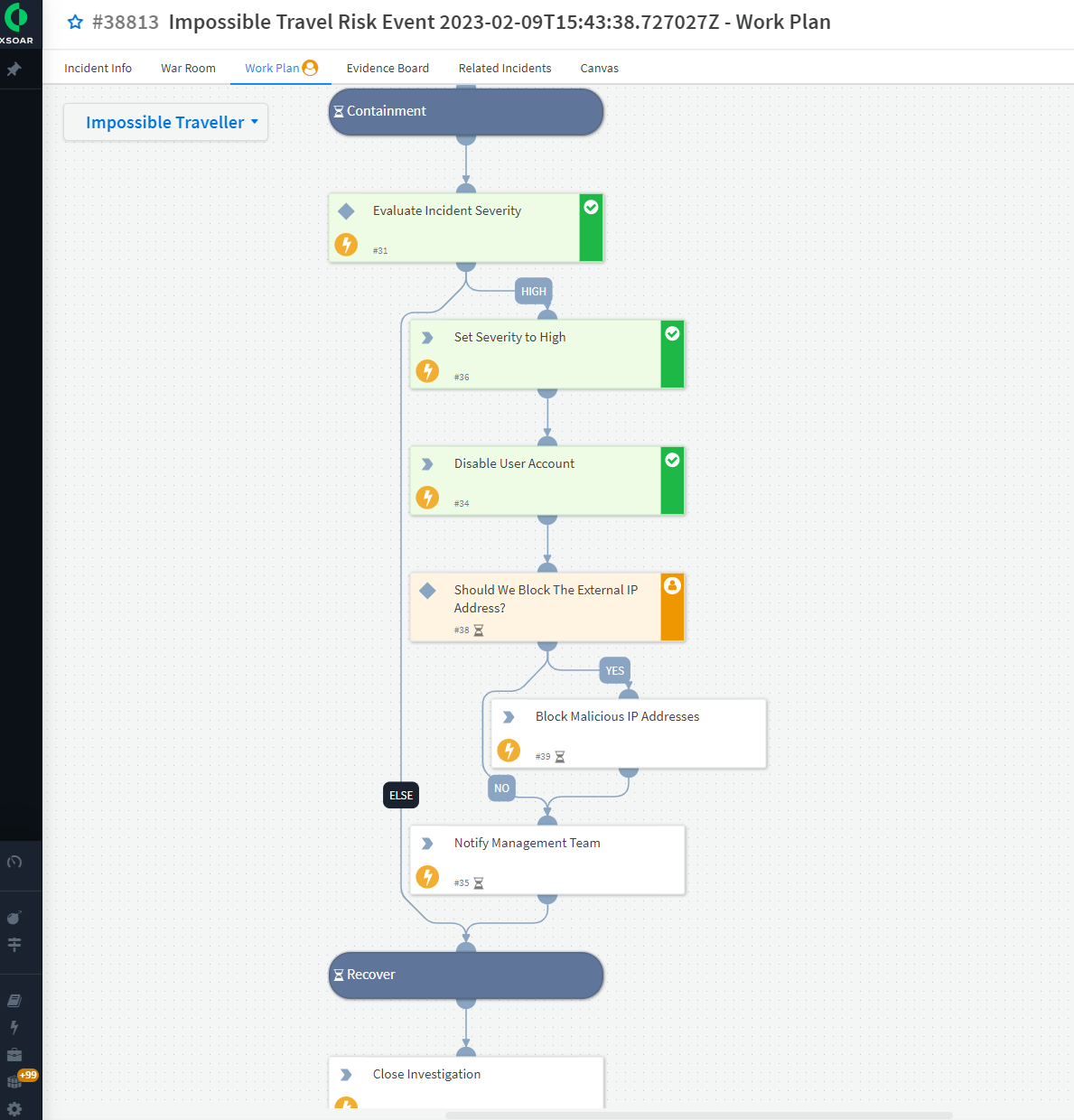
If the log-in is deemed malicious (like in the scenario shown below), the playbook can execute a series of containment steps such as disabling the user account, blocking the external IP address, and notifying the management team.
Don’t have Cortex XSOAR? Download our free Community Edition today to test out this playbook and hundreds more automations for common use cases you deal with daily in your security operations or SOC.