Disconnected security tool set bred complexity
Trading Point had added separate cybersecurity tools over time to support its global growth. However, this piecemeal approach had made it harder to ‘join the dots’ between alerts, increasing risk and reducing efficiency.
- Separate endpoint monitoring, security operations centre (SOC), and security information and event management (SIEM) tools were fragmenting visibility, absorbing resources and making it harder to detect malicious intent. Insights from security products needed to be correlated to separate the signal from noise.
- Multiple security products were replicating alerts and information, ultimately undermining motivation and limiting creative output. Alert fatigue and duplication of work needed to be prevented.
- Virtual private network (VPN) was becoming inadequate. Split tunnelling risked security through uninspected user internet traffic, while full tunnelling introduced too much latency, severely impacting user experience.
- A solution to better support the growing hybrid workforce needed to be found.
- Users could disable their VPN client, increasing risk. Resources were also required to administer user VPN accounts. Risks from user activity and expenditure of resources on ‘run of the mill’ tasks both needed to be decreased.
- Each of the above cybersecurity tools was connected to a separate firewall network security solution with a separate management console, resulting in complications and security glitches. Administration needed to be simplified and security protection more consistent.
“Detection and response are herculean tasks in a complex environment. By automating repetitive and monotonous tasks, we allow our security analysts more time to explore creative solutions to problems – such as creating better automation playbooks or threat hunting – which improves our daily operations and helps our analysts to grow and develop.”
Andreas Andrellis
Team Leader in Information Security Operations, Trading Point
Security Journey
Platformization sharpens security focus
Trading Point was already a satisfied Palo Alto Networks network security customer. So, when the time came to modernise network connectivity and the SOC, Trading Point again turned to Palo Alto Networks.
Cortex XSIAM’s AI and analytics engine, with its thousands of prebuilt analytics modules, helps process security data and stop threats in real time. This improves Trading Point’s ability to quickly detect and stop threats. “We conducted rigorous breach and attack simulations. XSIAM detected more than double the amount of threats than our incumbent EDR solution,” says Andreas Andrellis, Team Leader in Information Security Operations at Trading Point.
The team was also amazed at the innovation in Prisma Access. “It felt as familiar as the next-generation firewalls, which made it easy for us to fully onboard; there was no steep learning curve,” Andreas adds.
Supports world-class global brokerage services
 Cybersecurity consolidation manages risk across Trading Point’s diverse and complex environment, including its data centres and hybrid locations, encompassing multiple clouds and remote employees. By driving resilience, Palo Alto Networks is helping to keep threats at bay and ensure uninterrupted trading operations.
Cybersecurity consolidation manages risk across Trading Point’s diverse and complex environment, including its data centres and hybrid locations, encompassing multiple clouds and remote employees. By driving resilience, Palo Alto Networks is helping to keep threats at bay and ensure uninterrupted trading operations.
Moreover, integrated Autonomous Digital Experience Management (ADEM) monitors the user experience and provides comprehensive visibility from Prisma Access into any issues affecting end users. Andreas comments, “It can sometimes be hard to quickly identify and diagnose end-user problems. ADEM monitors the Wi-Fi signal, crucial applications our employees rely on every day, and ISP issues affecting the users.”
Closes out incidents with confidence
 Cortex XSIAM centralises data and SOC capabilities – such as XDR, SOAR, and SIEM – into one platform. To date, 30 data sources have been integrated into XSIAM, including endpoints, firewalls, Azure, Defender, and Office 365. According to Andreas, new sources can be connected “extremely fast.”
Cortex XSIAM centralises data and SOC capabilities – such as XDR, SOAR, and SIEM – into one platform. To date, 30 data sources have been integrated into XSIAM, including endpoints, firewalls, Azure, Defender, and Office 365. According to Andreas, new sources can be connected “extremely fast.”
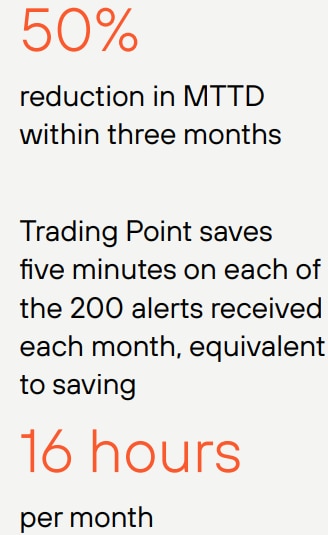
Security tasks are also automated to reduce manual work and accelerate incident response and remediation: 50% of incidents are closed automatically. So far, the Trading Point team has created 10 playbooks to automate security responses that were previously handled manually. Within three months, the team has reduced mean time to detect (MTTD) by 50% and mean time to respond (MTTR) by 60%.
“Our XSIAM playbooks automate security tasks before analysts review incidents. XSIAM also learns from manual actions and recommends future automations for improved incident response. Overall, it’s a great tool,” says Andreas.
Enables simple, secure hybrid working
Some 1,000 users rely on Prisma Access, together with its robust service connections to provide interconnection with the data centres and cloud infrastructure. Within the framework of communication with the data centres, Trading Point uses redundant service connections in different regions and Border Gateway Protocol dynamic routing.
The flexibility and adaptability of the network security platform enables the Trading Point team to also deploy Palo Alto Networks Next-Generation Firewalls (NGFWs) and Prisma Access interchangeably, reducing the latency with the data centres and adding capacity as and when needed to accommodate future growth.
Streamlines management
The unified network security platform is easier to manage than separate point solutions. For example, Trading Point has used Panorama to onboard the NGFWs deployed at the remote offices, allowing the team to manage multiple firewalls from one central platform. Instead of having users configured on the local database of the firewall, Trading Point uses single sign-on (SSO) with multifactor authentication (MFA) for Prisma Access.











