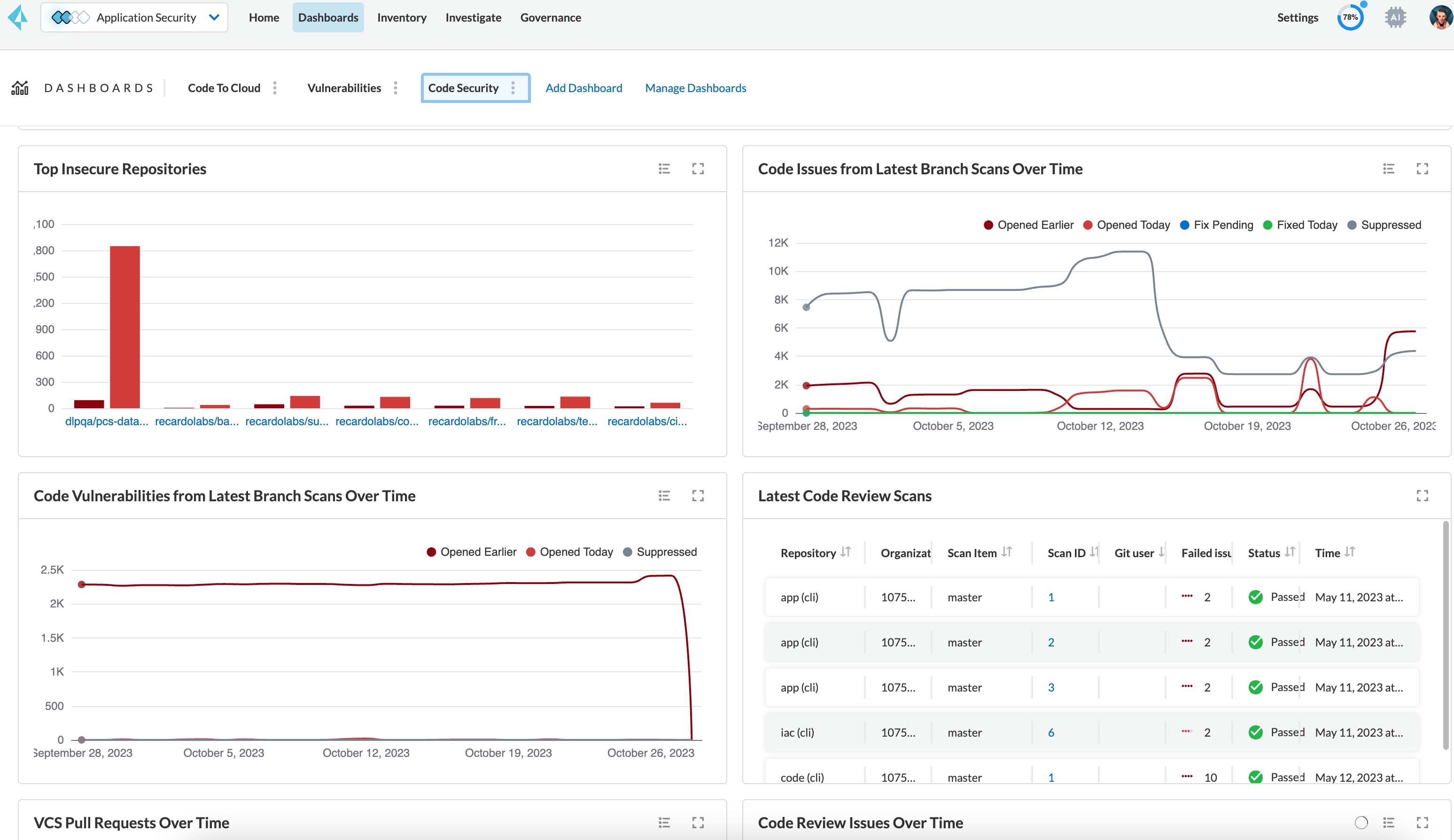
Centralized visibility across the engineering ecosystem
The cloud-native engineering ecosystem is increasingly complex, making it challenging for AppSec teams to get the comprehensive visibility needed to secure it. Having a unified inventory of the languages, frameworks, tools and executables within your ecosystems is the first step toward a secure software supply chain.
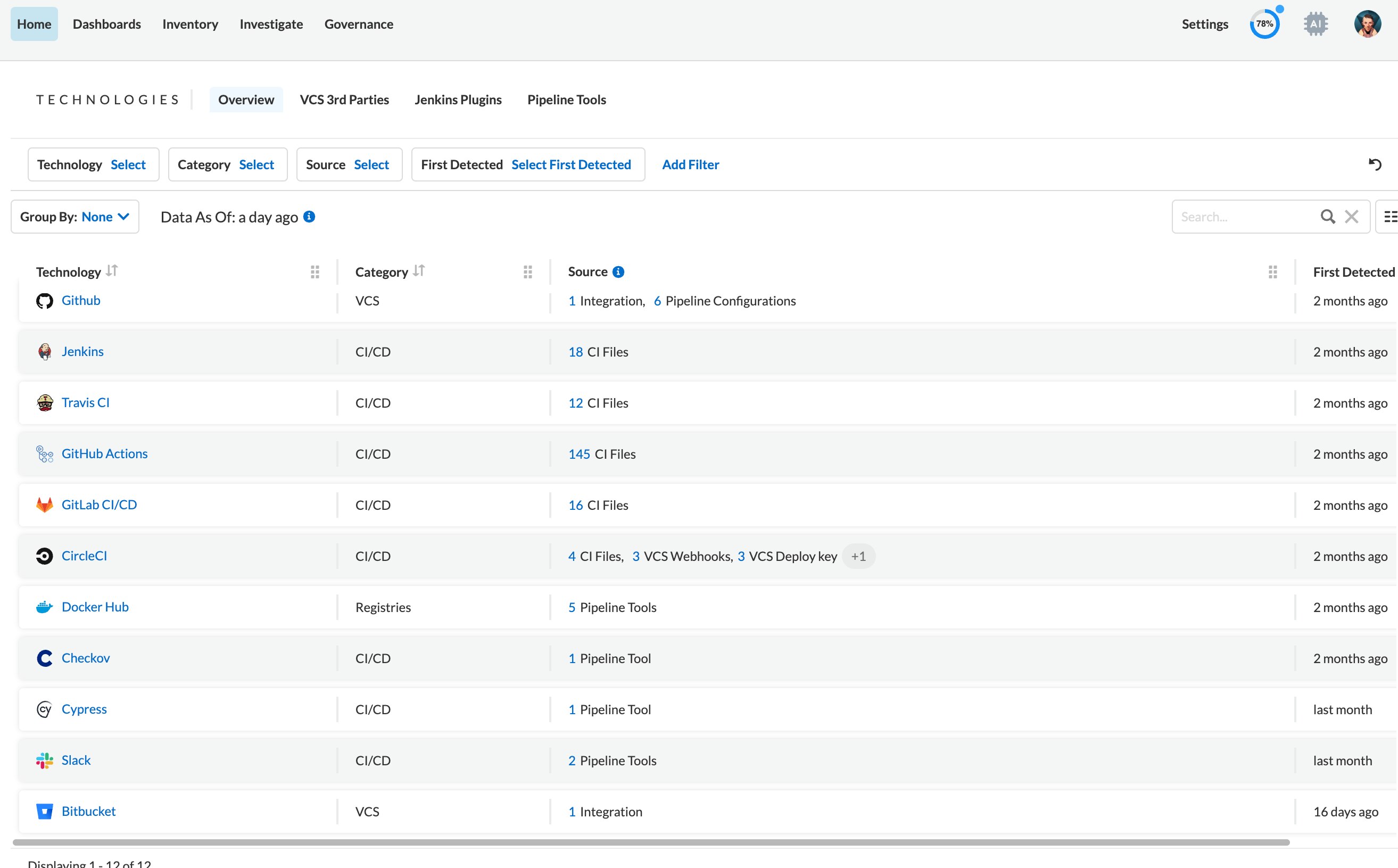
Prisma Cloud brings together a single view of all technologies in use and their associated security risks.
Scan across languages and repositories with unmatched accuracy.
Identify security risks across code types for all the most popular languages.
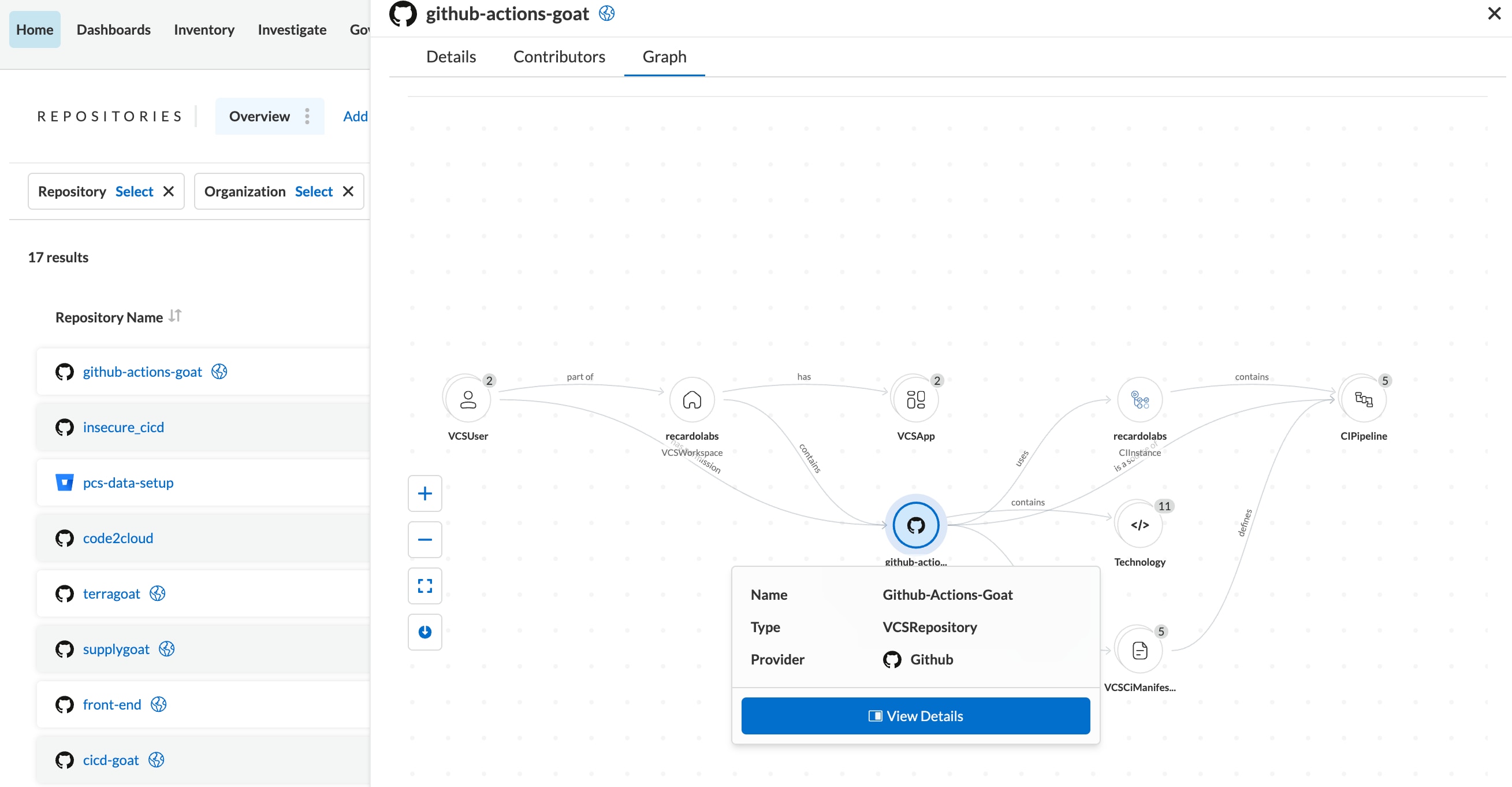
Connect infrastructure and application risks.
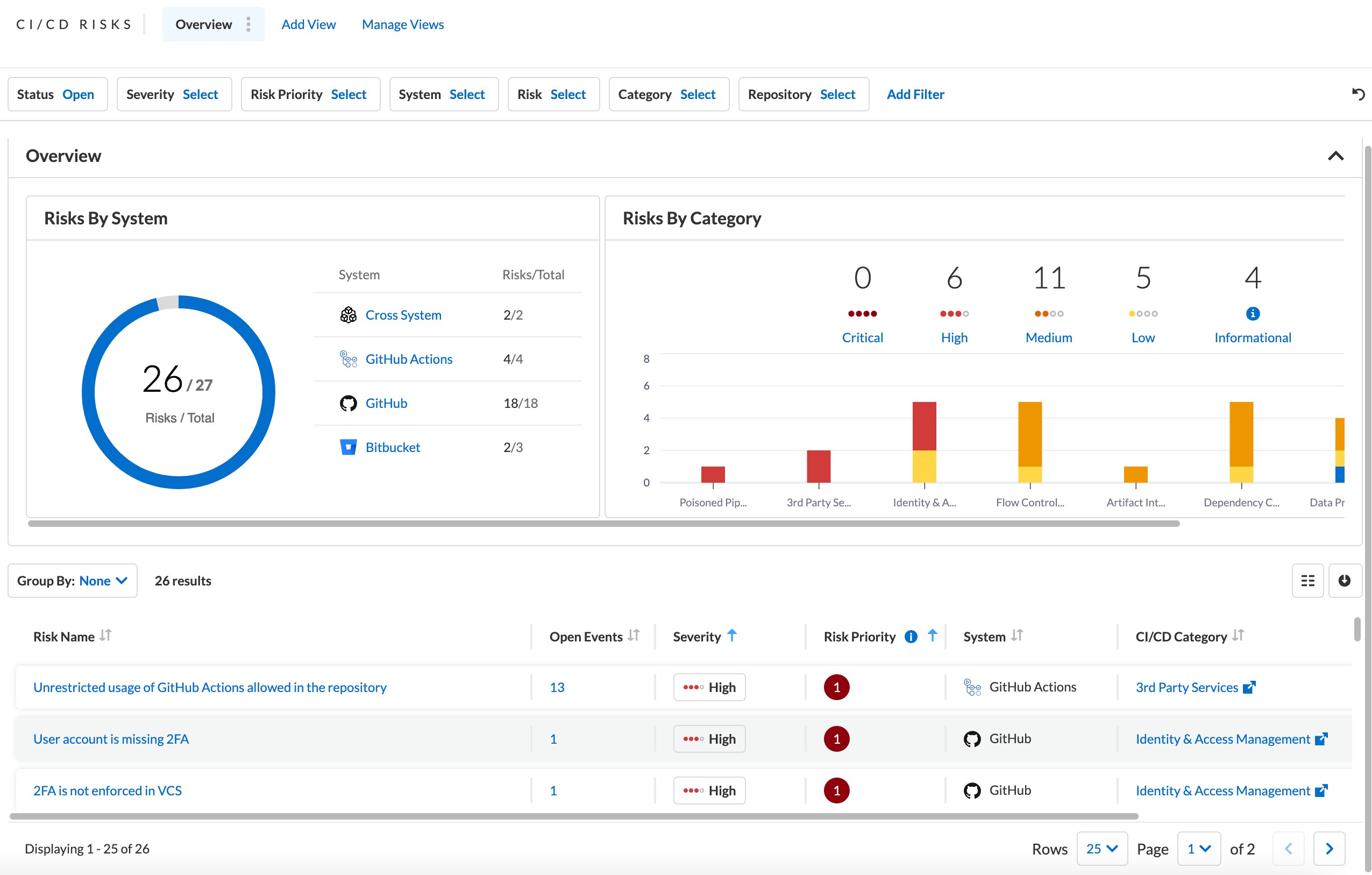
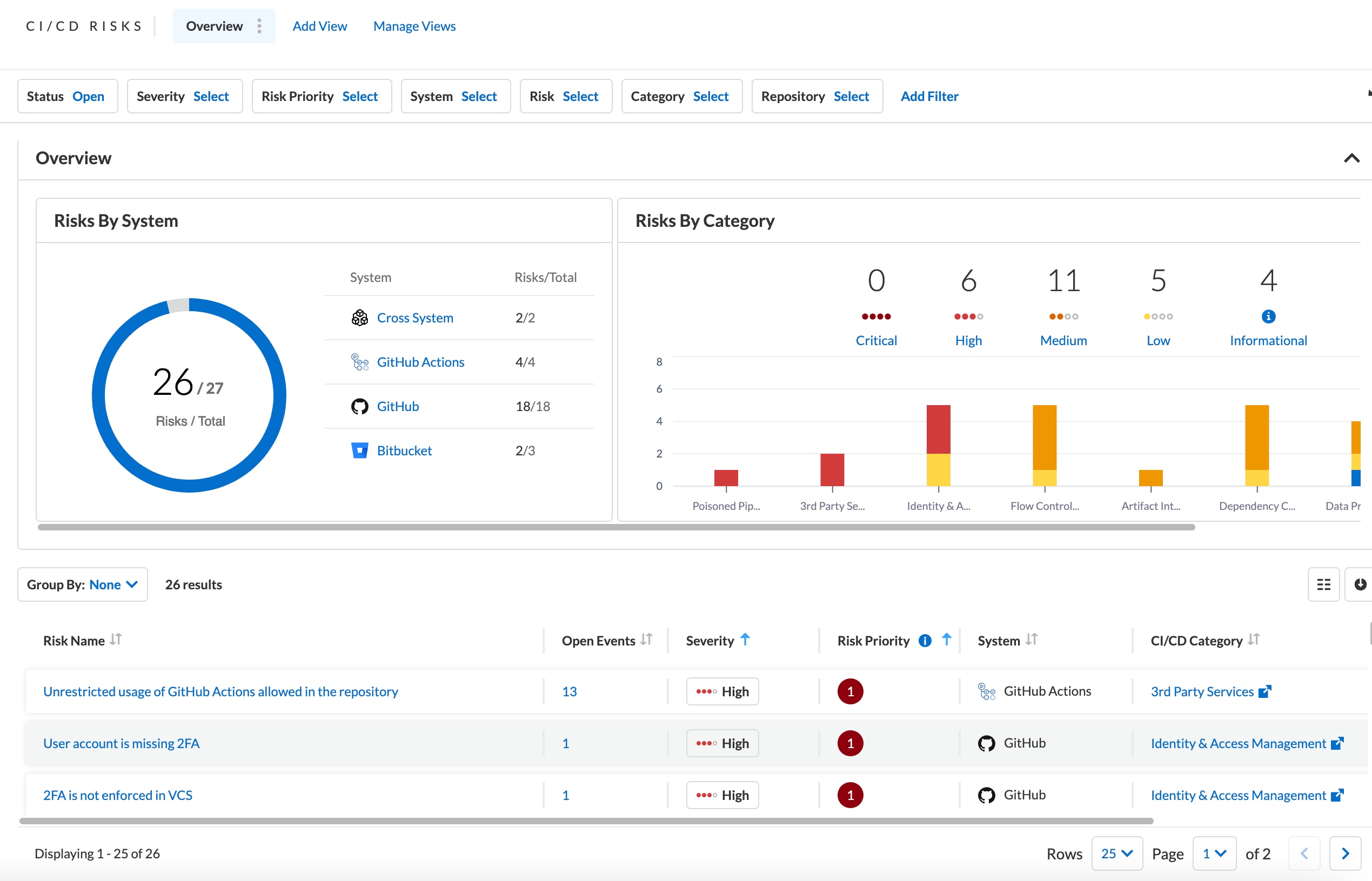
Focus on the critical risks that are exposed within your codebase, eliminate false positives and prioritize remediations faster.
Visualize your software supply chain.
Get a consolidated inventory of your CI/CD pipelines and code risks across your engineering ecosystem.
Catalog your software supply chain.
Generate a software bill of materials (SBOM) to track all sources of application risk and understand your attack surface.