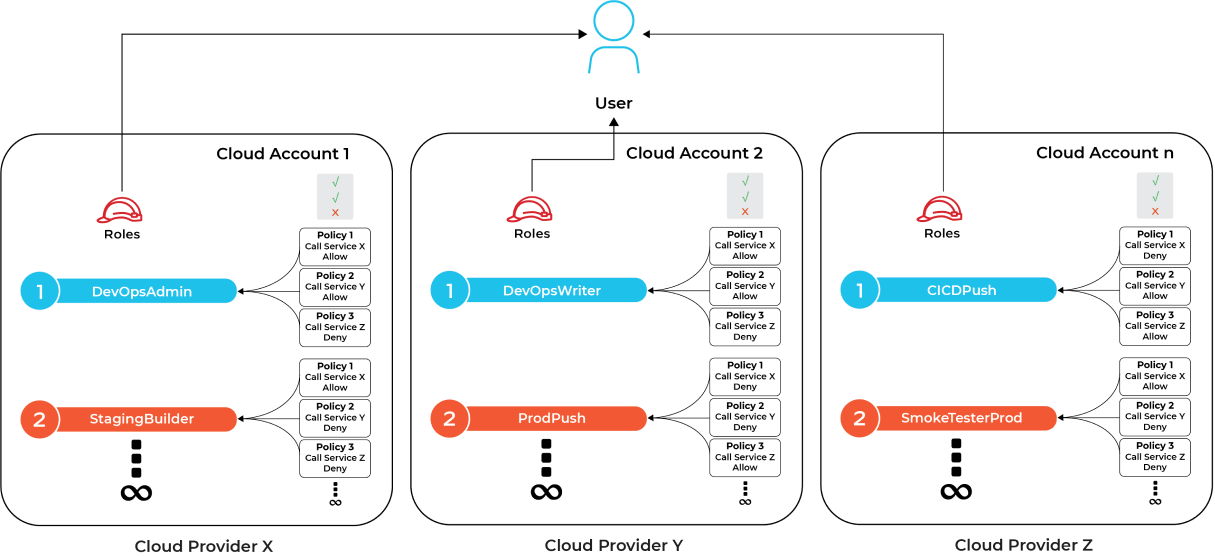
Consider Figure 1 below, where the user account has access across three different cloud providers—each with its own unique roles and permissions. The governance challenge here comes from the sheer volume of user and machine roles combined with permissions and services that are created in each cloud account.
While many organizations attempt to enforce a least privilege model, this often breaks down quickly with multi-cloud complexity. All these variables make visibility into effective permissions challenging.