1. 5G security use case priorities during commercial launch
Service providers intend to address immediate security challenges inherent with 5G New Radio (NR) and 5G Next-Gen Core (NGC) by prioritizing these security use cases.
-
1Core network signaling security services
![a1]()
-
2Cloud RAN fronthaul and backhaul security
![a2]()
-
3Core network configuration services, including slice management
![a3]()
2. Top 5 service provider security-as-a-service (SECaaS) priorities
A number of key offerings are central to enhancing the CSP 5G SECaaS portfolio.
- 1Application visibility and control for IoT services
![b1]()
- 2Subscriber (IMSI) threat correlation
![b2]()
- 3Secure applications on the mobile edge
![b3]()
- 4Automated cloud-based proactive security for known and unknown attacks
![b4]()
- 5Device (IMEI) threat correlation
![b5]()
3. Signaling security crucial to 5G
Current signaling control planes are stable for the most part, but service providers are less confident that this security performance can be duplicated on the 5G control plane.
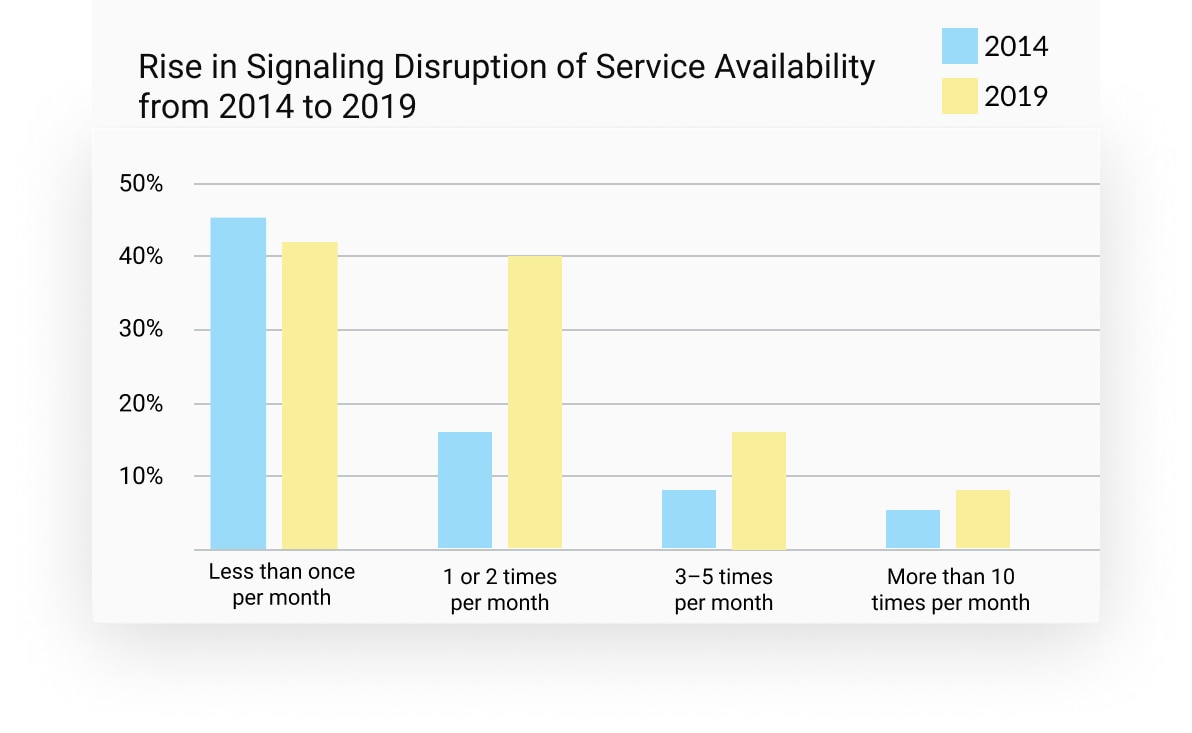
of CSPs agree signaling storms will be more common in 5G NR RAN and 5G NGC
of CSPs agree signaling security between inter-operator networks (roaming) will be crucial in 5G
4. Full content inspection a must-have
Full content inspection enhances visibility into RAN and Core and is fast becoming an extremely important “must-have” network security capability to CSPs.
-
![42p]() agree full content inspection is vital in 5G NR RAN
agree full content inspection is vital in 5G NR RAN -
![41p]() agree full content inspection is vital in 5G/NGC
agree full content inspection is vital in 5G/NGC -
![32p]() agree full content inspection is vital in roaming
agree full content inspection is vital in roaming -
![25p]() agree full content inspection is vital in Gi/SGi interface
agree full content inspection is vital in Gi/SGi interface -
![24p]() agree full content inspection is vital in MEC cloud
agree full content inspection is vital in MEC cloud
5. Threat correlation: a critical requirement
Full content inspection enhances visibility into RAN and Core and is fast becoming an extremely important “must-have” network security capability to CSPs.
- IMSIof CSPs rated subscriber (IMSI) correlation to threats and vulnerabilities a critical security service
![c1]()
- IMEIof CSPs rated device (IMEI) correlation to threats and vulnerabilities a critical security service
![c2]()
Although security challenges await at the inaugural phase of the 5G rollout, CSPs have clear insight into strategic security use case priorities that will guarantee success.
Source
"Heavy Reading's 2019 5G Security Survey," Heavy Reading, February 2019.