Tools, best practices and assistance to stay a step ahead
Take advantage of our expertise as you adopt a prevention-based architecture. Our transformational approach keeps you ahead of fast-evolving threats and simplifies operations to give you something you never expected from cybersecurity: peace of mind.
Transform quickly, efficiently, and with confidence
Transformation services help you define and implement a proven best practice security strategy that delivers measurable outcomes.
Using automation and a Zero Trust approach, the services help you streamline and simplify operations while strengthening your security posture. Harness our experience and extensive partner network to align your people, processes and procedures with business needs, elevating confidence and control to a whole new level.
Datasheet
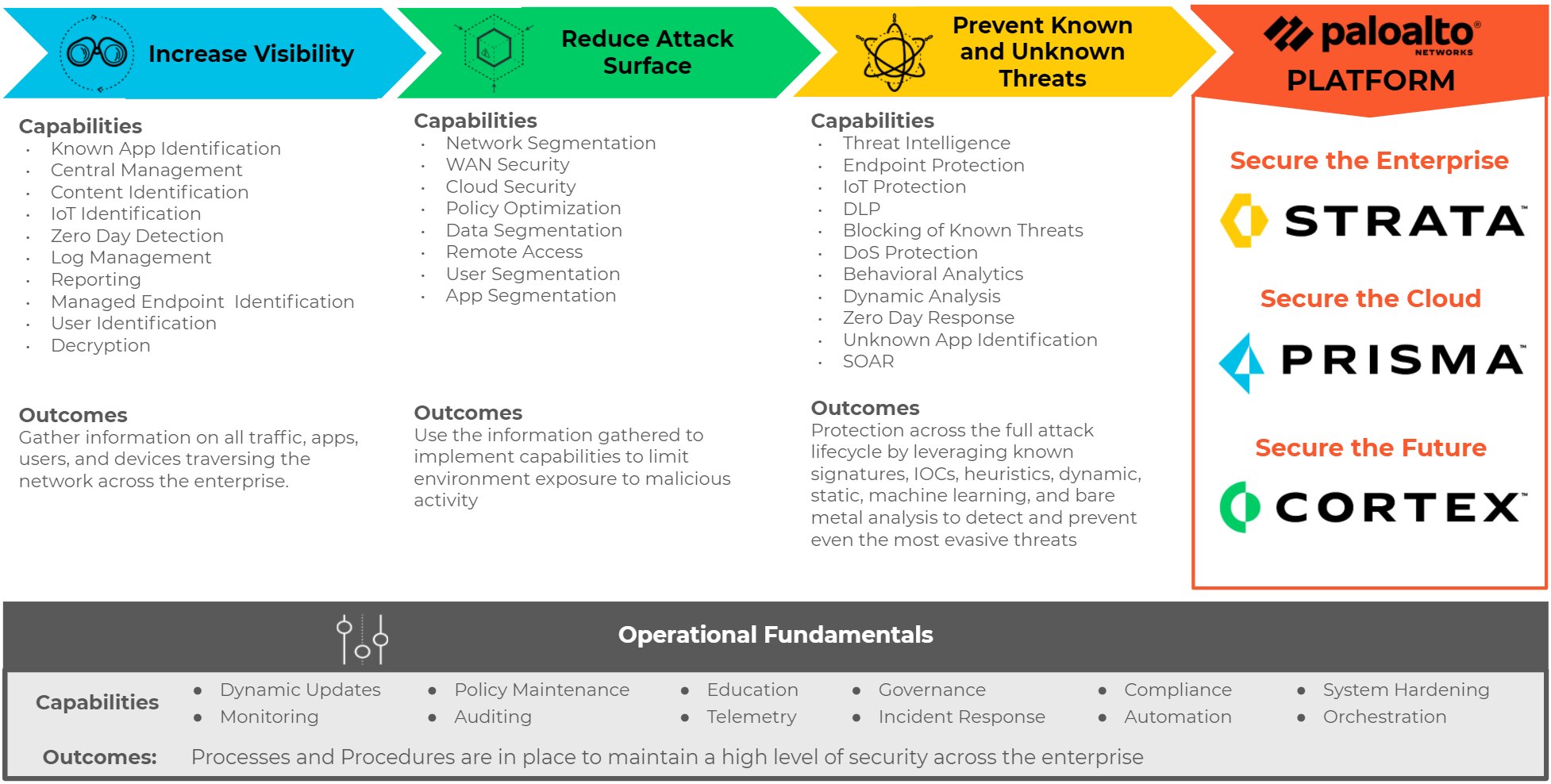
Four Domains of capabilities for a comprehensive security posture
There are four key milestones on the transformation journey: visibility, control, enforcement and integration. Read more about the levels in the white paper.