Building the Zero Trust Enterprise: The Role of the SOC
One of the essential truths of Zero Trust is to “never trust, always verify.” However, how do we know the policies and subsequent trust decisions we are making are the right ones? How do we continuously monitor and validate those decisions? Most threat prevention tools must decide, in real time, whether to permit or block user access, endpoint files and an innumerable set of other events and actions. The Security Operations Center (SOC) operates at a different level – using analytics, AI, automation and human analysis – and this allows the SOC to reevaluate past trusted decisions. When building a Zero Trust enterprise, the main role of the SOC is to provide an additional layer of verification to further reduce risk.
At the same time, many organizations are working to modernize their approach to the SOC due to an overwhelming amount of alerts, crippling manual processes and a lack of skilled personnel. While the SOC is an essential element of Zero Trust, organizations should consider how to incorporate innovations like automation, analytics and machine learning to increase SOC efficiency.
Why Do We Need Zero Trust?
At its core, Zero Trust seeks to eliminate implicit trust throughout the enterprise by continuously validating all digital transactions. Zero Trust amends past assumptions that everything inside an organization’s network could be implicitly trusted. This implicit trust would allow users in the network – including external adversaries and malicious insiders – to conduct internal network discovery, move laterally and access or steal sensitive data due to a lack of security controls. These types of techniques are used extensively in many modern attacks, such as ransomware that starts with a vulnerability exploit and then “lands and expands” within an organization.
Digital transformation projects and initiatives, such as the ongoing migration to the cloud and hybrid work, have underscored the need to replace outdated security models that focus solely on protecting the network perimeter. Zero Trust presents a unique opportunity to rebuild security in a way that supports major initiatives, like remote work and migration to the cloud, while minimizing the attack surface, eliminating security gaps and meeting audit demands.
Keys for Building a Zero Trust Enterprise
When embarking on a Zero Trust journey, an organization first needs to define a unified security policy. This typically starts with identifying critical assets and deploying a Zero Trust architecture with strict, least-access policies across users, applications and infrastructure.
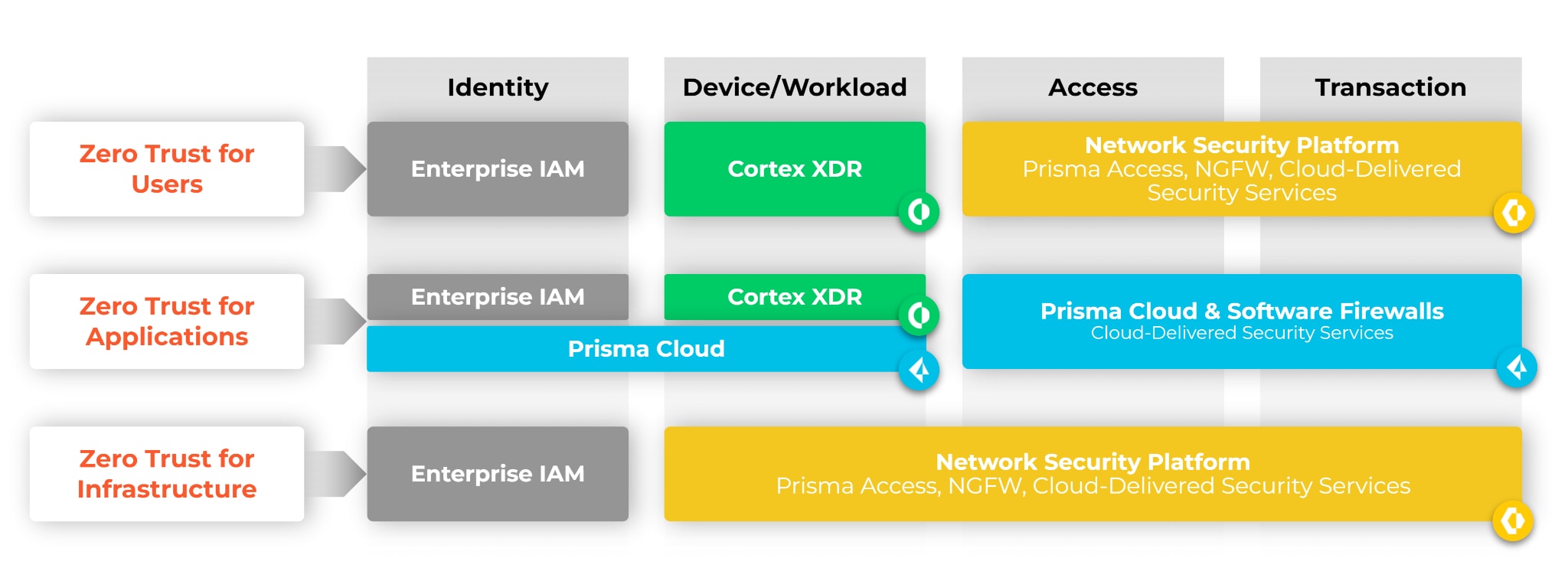
However, Zero Trust is an ongoing process that requires continued evolution and refinement as each organization’s business requirements and subsequent technology shifts occur. Continuous monitoring should be a core requirement in any Zero Trust journey. Additionally, monitoring needs to go beyond any single security tool to broaden visibility. This makes the role of the SOC critical in the continued audit and maintenance of any Zero Trust security posture.
The Role of the SOC in Achieving Zero Trust
Once organizations have visibility into critical assets and have created rock solid Zero Trust policies, continuous monitoring and ongoing improvements are key to maturing any Zero Trust strategy.
The role of the SOC is essential. It provides an ongoing audit function for Zero Trust policies and actions, helping security teams verify their past trust decisions. As a case in point, an organization might implement multi-factor authentication to correctly identify users and grant access to applications. The SecOps team can analyze a user’s activity with machine learning, behavioral analytics and human insights to detect insider abuse and mitigate damage by disabling the user’s account. Even with a mature Zero Trust implementation that secures users, applications and workloads, organizations still need a SOC for threat detection, response, automation and risk management.
The SOC should be able to perform the following three functions to reduce risk, remove implicit trust and detect and stop attacks across the cyberattack lifecycle.
- Detect and Respond to Threats Anywhere in the Organization: Whether identifying an external threat actor, a malicious insider, malware or risky user behavior, SecOps teams need a powerful and effective detection and response solution, backed with proven and tested results. With the growing amount of security data being generated, SecOps analysts need a solution that can automatically integrate key data, profile user behavior and accurately detect adversary tactics, techniques and procedures (TTP). To eliminate blind spots and streamline analysis, a detection and response tool should operate across all data, rather than offering a siloed approach to triage and investigations.
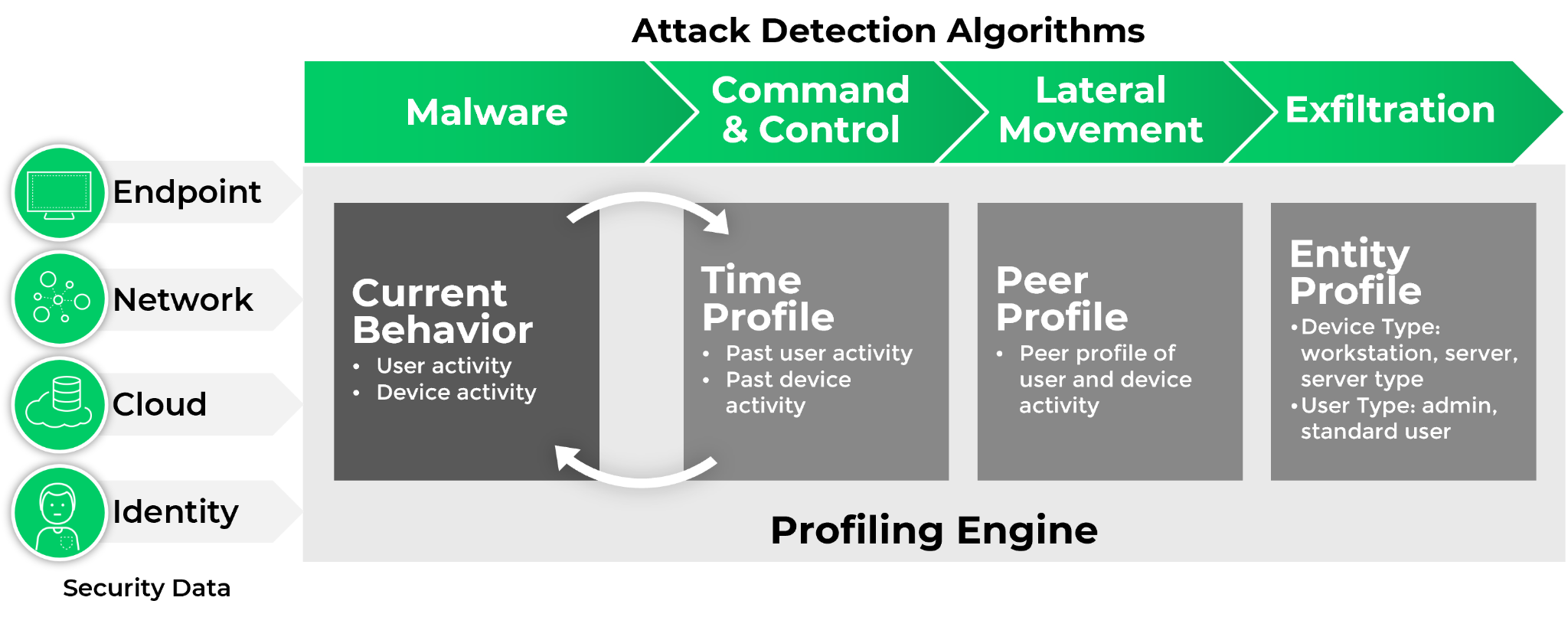
- Orchestrate and Automate SecOps Tasks: Many security teams manage dozens of security tools, perform countless operations, and handle thousands or even tens of thousands of alerts a day. They need a security orchestration, automation and response (SOAR) platform to help them triage and respond to incidents, leveraging threat intelligence to prioritize and analyze threats. A comprehensive SOAR platform that addresses all aspects of incident management needs to provide comprehensive out-of-the-box integrations of commonly used tools in the SOC, best practice playbooks to aid in automating workflows, as well as integrated case management and real-time collaboration to enable cross-team incident investigation.
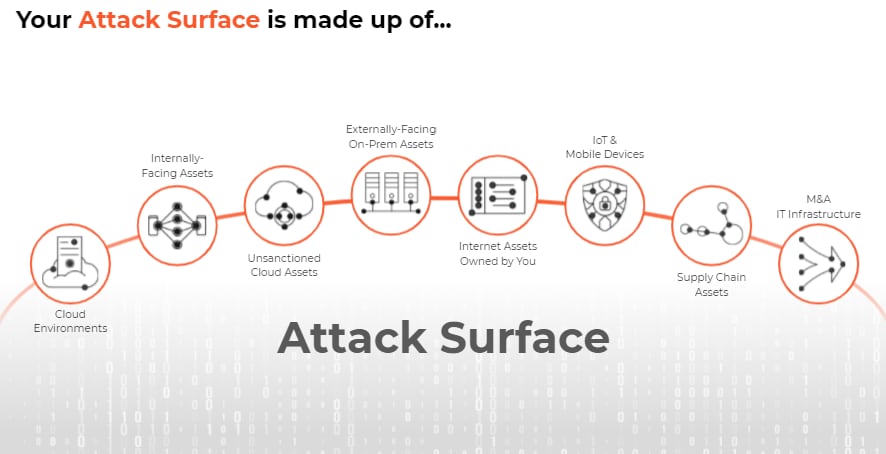
- Assess and Secure the External Attack Surface: SecOps teams must identify the assets they are trying to protect and prevent from being attacked. A critical step to informing any risk management function is to have a clear understanding of one’s attack surface – you can’t protect what you can’t see. This includes detecting external gaps in visibility, discovering unknown assets and shadow IT, and identifying and prioritizing vulnerabilities, configuration flaws and exposure of sensitive information.
Palo Alto Networks Can Help with Cortex
Let’s face it. We understand most SecOps teams don’t want to be system integrators. Nor do they want to “run ragged” performing manual, repetitive tasks. An array of siloed tools requires massive time and costs to maintain. Numerous and disparate solutions can limit security outcomes by introducing complexity and fractured visibility for the analytics required by modern SOCs.
Palo Alto Networks Cortex solutions can help SecOps teams prevent successful attacks, reduce TCO and integrate across hundreds of third-party tools. The Cortex suite of products can equip security analysts with the tools they need to keep their data safe, so they can focus more on what matters and less on mundane tasks.
Organizations can begin or accelerate their Zero Trust journey by deploying the Cortex suite of products, Cortex XDR, Cortex XSOAR and Cortex Xpanse, which seamlessly work together as a force multiplier across your security operations.
Cortex XDR: The industry’s first extended detection and response platform that stops modern attacks by integrating data from any source. Cortex XDR harnesses the power of AI, analytics and rich data to detect stealthy threats. Intelligent alert grouping, root cause analysis and cross-data insights simplify investigations, so SOC teams can streamline incident response and recovery. Cortex XDR delivers peace of mind with best-in-class endpoint protection that achieved the highest combined protection and detection scores in the MITRE ATT&CK® round 3 evaluation.
Cortex XSOAR: A single platform for end-to-end incident and security operational process lifecycle management. Security teams of all sizes can leverage the extensive 725+ prebuilt integration content packs, robust security-focused case management with real-time collaboration to orchestrate, automate and speed incident response or security process across their environment. In addition, with integrated threat intel management, security teams get powerful built-in threat data, the ability to automatically map threat information to incidents, and operationalize threat intelligence with the ability to take action on the threat data.
Cortex Xpanse: A complete and accurate inventory of an organization’s global, internet-facing cloud assets and misconfigurations to continuously discover, evaluate and mitigate an external attack surface, flag risky communications, evaluate supplier risk or assess the security of M&A targets.
While each standalone product brings its own unique features and benefits when combined with one another, or with Palo Alto Networks Next-Generation Firewall, Prisma Cloud, Prisma Access and more, the positive results increase exponentially. They help lower the risk and impact from breaches with a comprehensive product suite for security operations, empowering enterprises with best-in-class detection, investigation, automation and response capabilities, bar none.
Interested in scheduling a demo? Get started today. You can also learn how Palo Alto Networks can help you become a Zero Trust enterprise.
Related Blogs
Subscribe to the Newsletter!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.