While attack surface management (ASM) is making its way into many enterprise SOC’s today, it has been a challenge for industrial organizations to track their full attack surface because of the large amount of Operational Technologies (OT) and Industrial Control Systems (ICS) within their environment.
OT and ICS are often hard to find and traditionally have been built without security in mind, making them more vulnerable. OT and ICS equipment include building management systems, fire control systems, physical access control mechanisms, HVAC systems, medical devices, manufacturing equipment, and more.
Legacy OT and ICS systems often persist on nonstandard ports that aren’t typically scanned with a vulnerability management scanner. Or, they are open on port 80/443, exposing their web interface, while appearing as just another web server, which can be exploited by bad actors, including nation-states.The state-sponsored Triton malware attack in 2017 allowed a bad actor to take over safety instrument systems (SIS) at a Saudi petrochemical plant.
General security best practices have improved, and ICS/OT devices are not exposed as commonly as they were pre-2018. However, there is still critical OT infrastructure routinely exposed to the public internet. In the 2022 Attack Surface Threat Report, Cortex Xpanse researchers found that nearly 14% of all exposed infrastructure on the public internet was related to building control systems.
Security teams must exert better control
Continuous visibility is one way security teams can better monitor their critical operational infrastructure. Cortex Xpanse is an Active ASM solution that helps your organization actively discover, learn about, and respond to unknown risks in all publicly connected systems and exposed services.
Through continuous indexing and high-fidelity attribution, Xpanse helps organizations identify what assets belong to them and often helps them find up to 40% more internet-facing assets than they had been tracking previously. This shadow IT often includes OT and ICS devices.
Additionally, Xpanse has dozens of policies that allows organizations to monitor and alert on OT and ICS device exposures. Xpanse generates real-time alerts when it finds any asset exposed to the internet and/or identified as a risk.
For example, Xpanse can discover dozens of Schneider Electric devices, which control things like power supplies, motors, pumps, valves, and so much more. In addition, we also cover devices from Siemens, Honeywell, and other common operational systems. Having these exposed on the internet can lead to disruptions that halt production and potentially even destroy products and procedures.
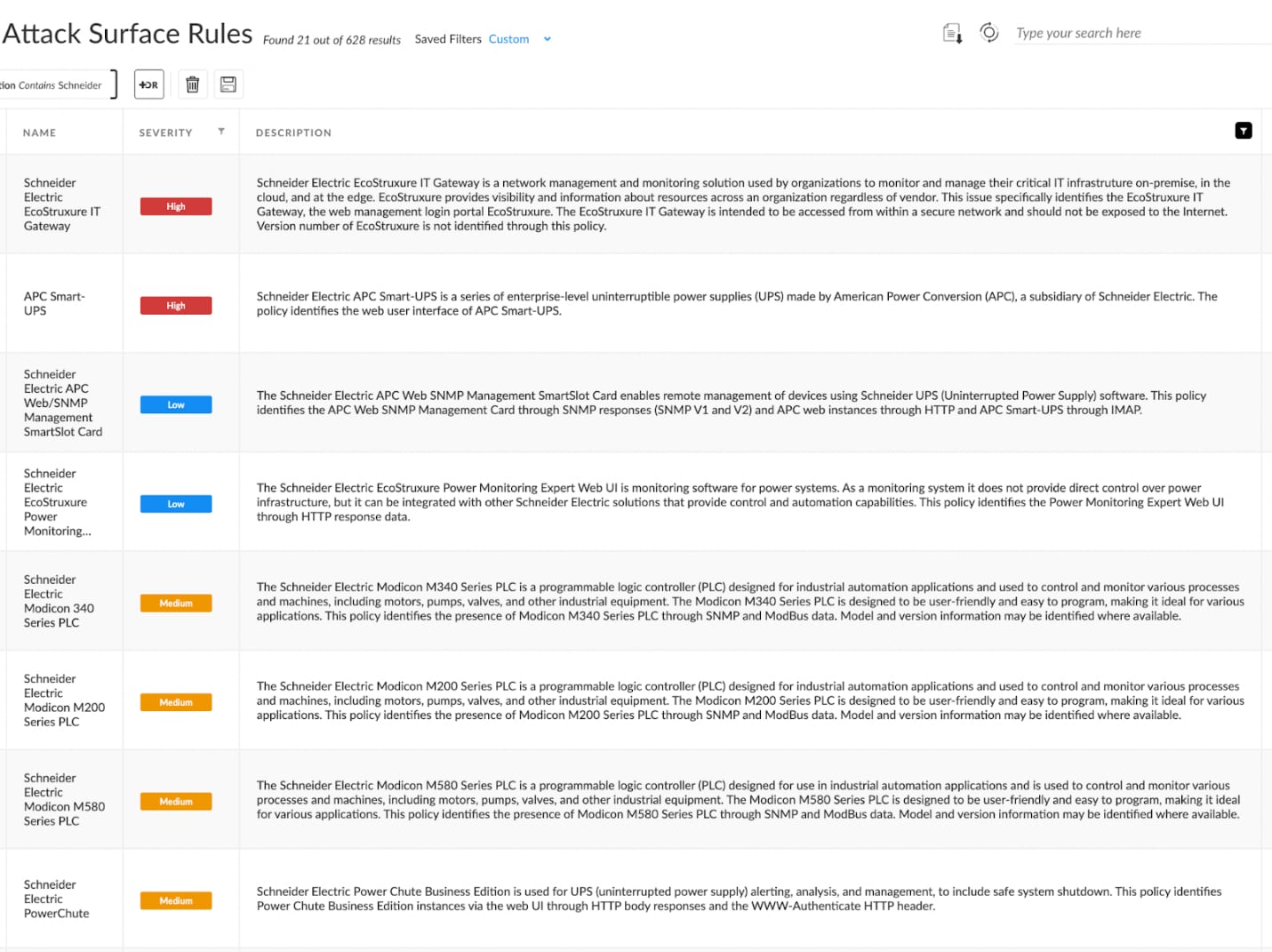
Industrial organizations can now not only monitor their traditional IT attack surface but also secure large portions of their older and legacy OT and ICS technologies that typically lack advanced security controls. Xpanse allows for a proactive approach to reducing cyber risk, allowing customers to identify assets, pinpoint their locations and version, as well as automatically prioritize which are the most at risk. Xpanse also suggests steps to remediate the vulnerability.
Cortex Xpanse offers the most comprehensive attack surface management solution on the market, focused on giving our customers the best visibility into their attack surface to prevent a cyberattack. Our customers range from governments to Fortune 500 private enterprises
To learn more about your OT and ICS exposures, schedule your demo here