The Smartest IoT Security Solution for Smart Devices
The incredible growth of the Internet of Things (IoT) has presented unique business opportunities and enabled operational models across a wide range of industries and use cases. Although estimates vary, Gartner's research predicts that there will be over 18 billion connected IoT devices in enterprises by 2030. To put these numbers in perspective, by 2030, there will be four times the number of IoT devices connecting to the network than users in an enterprise.
While IoT devices help organizations increase productivity and efficiency (in some cases they increase revenue as well), unfortunately, they also expand the attack surface and are an easy target for attackers, making them the weakest link in your enterprise. A recent analysis¹ detected more than 1.5 billion attacks on IoT devices in the first half of 2021, which doubled from 2020. This co-emergence of devices and attacks raises the question, what is so difficult about securing IoT devices?
Continuing our six-part webinar series, episode 4 will cover how our new IoT Security solution can reduce the unseen and unmitigated risk of IoT devices across your enterprise. If you missed our previous episodes, you can check them out here:
- Episode 1: Industry Firsts in NGFW Design and Security for Internet Edge, Campus, and Data Centers
- Episode 2: Evolution of IPS to Advanced Threat Prevention
- Episode 3: Innovations in Web Security to Stop Evasive Threats
The Challenges of Securing IoT Devices
In addition to the growing number and variety of devices, and the increasing sophistication of cyber attacks, there are four main areas where the enterprise is challenged to secure devices.
- IoT devices carry huge inherent risk. Devices are often shipped with vulnerabilities, are difficult to patch, and lack encryption in communication. Some become vulnerable when their service life lasts many years past their cyber-life and their operating systems are no longer supported.
![Learn how our IoT Security solution delivers ML-powered visibility, prevention, and zero-trust policy enforcement in a single platform.]()
- No clear ownership for securing IoT within the organization. Typically, devices don’t fall under the responsibility. The typical IT security team does not recognize devices as part of their responsibility and the department and site engineers who provision IoT devices do not have the security expertise to protect them. In addition, IoT devices are also left out of the SOC workflow. As a result, incident response teams are not equipped to deal with IoT device breaches, leading to more work and delays in response.
- IoT blindspots in existing IT and security solutions. The lack of IoT visibility and context makes network segmentation, firewall policies, endpoint protection platforms and vulnerability management solutions ineffective against the largest contributor of risk. Each security team also waste valuable time trying to identify unknown IP addresses in triage and investigation, when IoT visibility can easily identify these devices for them.
- Many IoT security solutions offer neither security nor scalability. Most IoT security solutions take a static approach to identify IoT devices. This means a new device with significant security issues might already be on your network, but your security tools have no way of identifying it. These tools also lack any preventative controls or policy recommendations that increase the number of actionable alerts for security teams.
These challenges result in an expanded attack surface for cyberthreats. Despite having security solutions and teams in place, the risk that IoT devices pose to the organization go unseen and unmitigated. Organizations need a comprehensive solution to see, monitor, and secure all devices.
Introducing IoT Security 2.0
Your organization is likely facing one or more of the challenges described here. Palo Alto Networks IoT Security can help you address these challenges by eliminating one of the biggest blind spots in network security. IoT Security delivers ML-powered visibility, prevention, and zero-trust policy enforcement in a single platform.
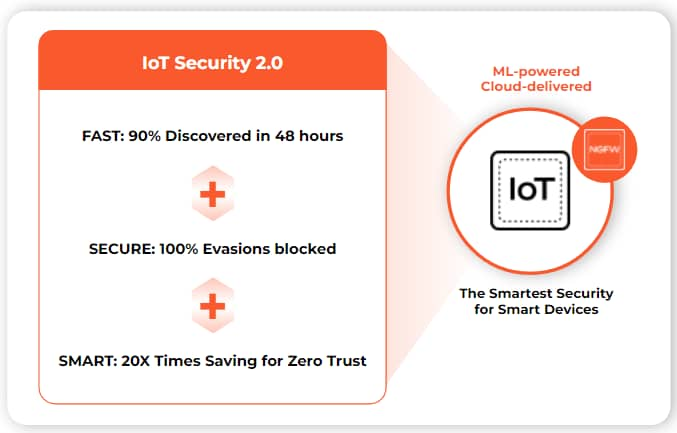
To learn more about IoT Security 2.0, be sure to register for episode 4 in our webinar miniseries, Smart and Easy IoT Security for Zero Trust.
If you missed our previous episodes, check out what’s new with our NGFWs and security infrastructure in episode one, learn about the latest in Intrusion Prevention in episode two, and learn how our Advanced URL Filtering and DNS Security solutions can protect customers in real time in episode three.
¹https://www.kaspersky.com/about/press-releases/2022_43-of-businesses-dont-protect-their-full-iot-suite
Related Blogs
Subscribe to Network Security Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.
