Executive Summary: Vulnerability Identified
On September 16th, CVE-2022-3172, a medium severity vulnerability (with CVSS score of 5.1) in the Kubernetes API server, was published. The vulnerability is an open redirect vulnerability that allows an aggregated API server to redirect client requests, which could lead to credentials theft and information leakage.
The vulnerability could be exploited by a compromised aggregated API server that will return a redirect response to the client, causing the client to execute unintended actions.
Palo Alto Networks’ Prisma Cloud customers are protected from this threat through the Runtime Protection feature, which monitors and alerts on suspicious activity in the Kubernetes cluster, including aggregated API servers.
Kubernetes Aggregated API Server
To understand the vulnerability, we will first elaborate on what a Kubernetes Aggregated API server is and its functionality.
Kubernetes Aggregated API Server allows “Kubernetes API server to be extended with additional APIs. The additional APIs can either be ready-made solutions such as a metrics server, or APIs that you develop yourself”.
The aggregation layer, which is where an aggregated API server resides, runs with the kube-apiserver. For such a resource to work, it should be registered in advance by adding an APIService object, which defines the URL path, inside the API Server. Next, the API Server will act as a proxy, delegating all traffic to the registered API Service.
The Security Vulnerability
While the Kubernetes API server forwards requests to the aggregated API server, it does not validate the response from the aggregated API server. This could lead to a scenario where a compromised aggregated API server would return a redirect response pointing to a malicious endpoint. This response will be forwarded to the client, which in turn will access the malicious endpoint.
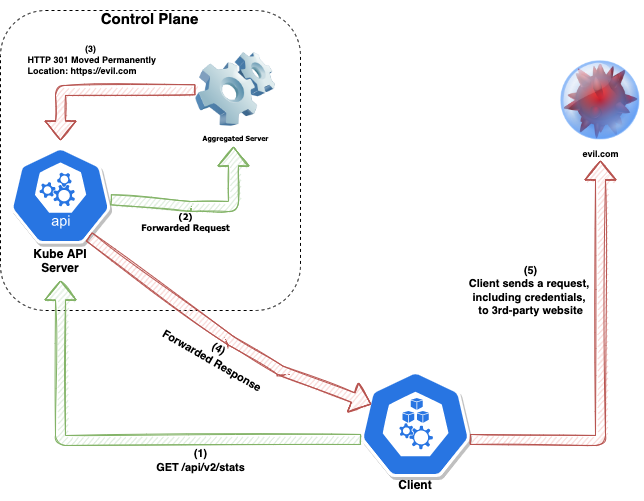
Exploitation Impact
An aggregated API server could redirect client traffic to any URL. This could lead to the client performing unexpected and unintended actions as well as forwarding a client's API server credentials to third parties.
Mitigations
Kubernetes mitigates the vulnerability in versions
- kube-apiserver v1.25.1
- kube-apiserver v1.24.5
- kube-apiserver v1.23.11
- kube-apiserver v1.22.14
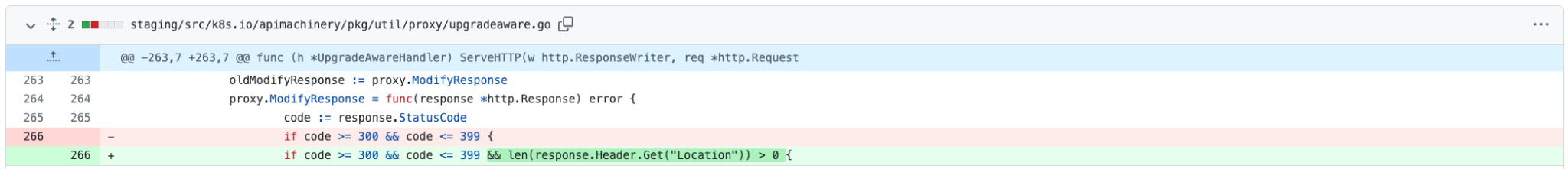
The prompt fix (#112330) blocked all HTTP responses entirely, ranging from 300 to 399 status codes, from aggregated API servers, by default. After the fix was released, a new incident was raised because the presumption that all responses in the ranges stated above are redirects is incorrect. For instance, HTTP status code “304 (Not Modified)” does not redirect the user to any resource, yet such responses were blocked by this patch and so a new fix (#112524) was released, specifically blocking HTTP 3xx responses that contain the HTTP Location header, as well.
As it can be appreciated in the following code snippet, the mitigation to block all HTTP 3xx status codes when the HTTP Location header is also present was done on the last delivered fix:
Note: If your aggregated API server(s) are considered trustworthy and redirect functionality is required, the kube-apiserver --aggregator-reject-forwarding-redirect flag could be set to false, to restore the previous configuration and perform redirects.
Conclusion
Palo Alto Networks Prisma Cloud customers are protected from this threat through the Runtime Protection Feature that alerts on suspicious activity in the cluster, including in aggregate API servers.
As part of a Palo Alto Networks commitment to constantly improve and optimize public cloud security, we actively invest resources in monitoring and mitigating such technologies while reporting issues to corresponding vendors to keep customers and users safe from potential threats.