Developers use secrets to enable their applications to securely communicate with other services. Hardcoding credentials (like usernames and passwords) simplifies development and saves time. Unfortunately, version control systems (VCS) like GitHub are not secure, which creates potential exposures that can be exploited. This often happens when developers accidently leave their secrets in the source code, and once they’re committed into a repo, the secret is saved in history and accessible to anyone who has access to the repo. If the repo is made public, threat actors can easily find and use the secrets in their attack path.
It's not enough to detect common secrets at runtime. Effective secrets security requires detection across hundreds of possibilities (text keys, access tokens, API keys, certificates, passwords, database connection strings, etc.) embedded into existing developer workflows.
Prisma Cloud customers can now activate secrets security. This new module further extends the industry's only Code-to-Cloud CNAPP, and brings together multiple novel techniques that provide unrivaled visibility and control of secrets for cloud developers:
- Precise detection of complex strings
- Custom secrets policies
- Native developer feedback
- Risk factor context for faster remediation
Precise Detection of Complex Strings
Not all secrets are consistent or follow commonly identifiable patterns (access tokens, API keys, encryption keys, OAuth tokens, certificates, etc.). While Prisma Cloud has a library of over 100 signatures to detect and alert on the wide array of secrets with known, predictable expressions, random strings like usernames and passwords must also be identified.
Signature-based methods can’t detect random strings. For this reason, Prisma Cloud augments its comprehensive signature library with a fine-tuned entropy model that alerts on exposed passwords and other random identifiers. Furthemore, unlike traditional entropy techniques which generate false positives, Prisma Cloud leverages the context around the string to precisely identify more complex secret types and significantly reduce false positives.
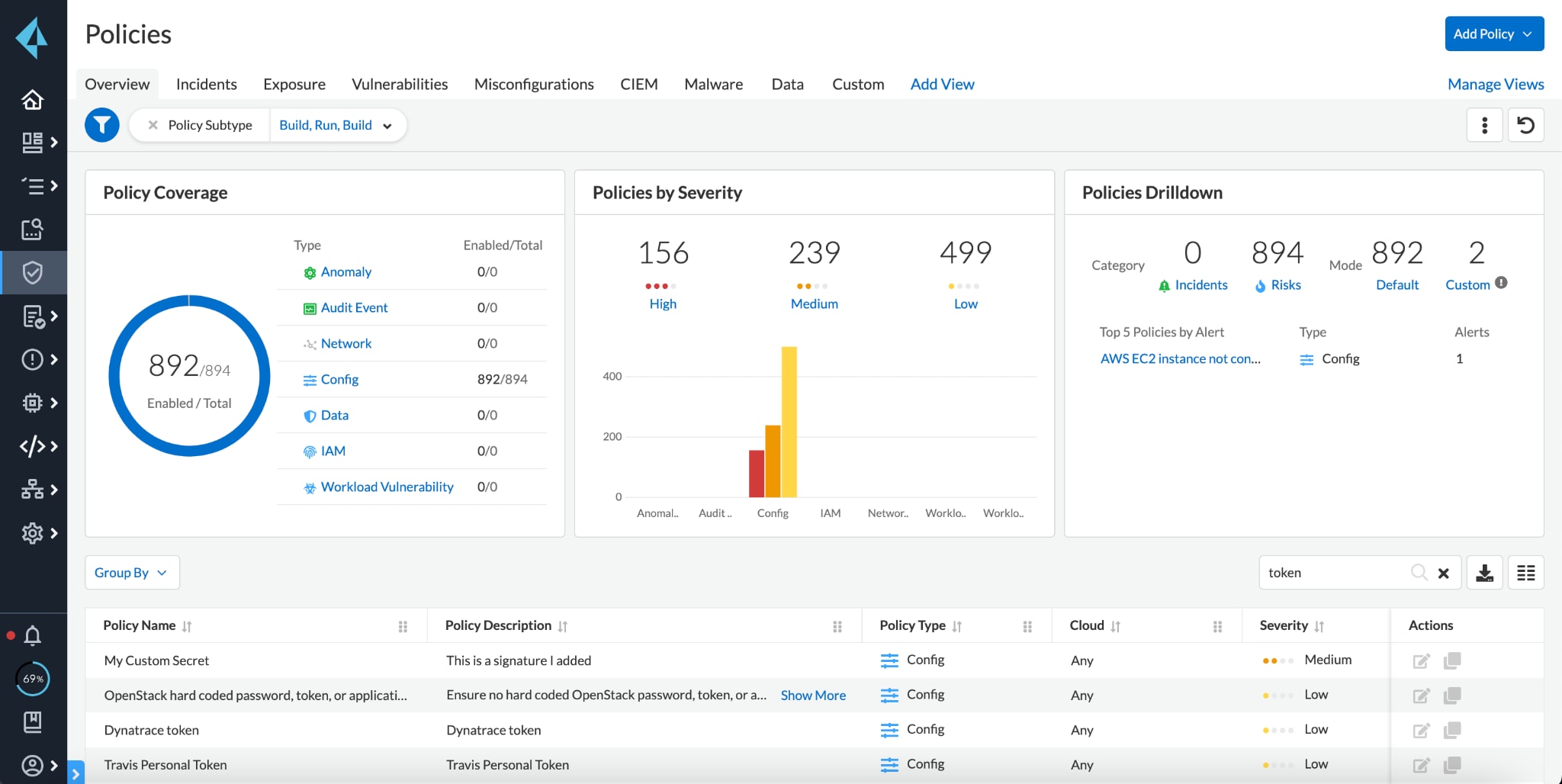
Custom Secrets Policies
Enterprises may utilize a custom syntax or at least specific characteristics to consistently define secrets across the organization. For this reason, the Prisma Cloud Secrets Security module allows users to easily define custom strings to alert on exposed or at risk secrets. This customization feature minimizes potential false positive alerts and streamlines detection.
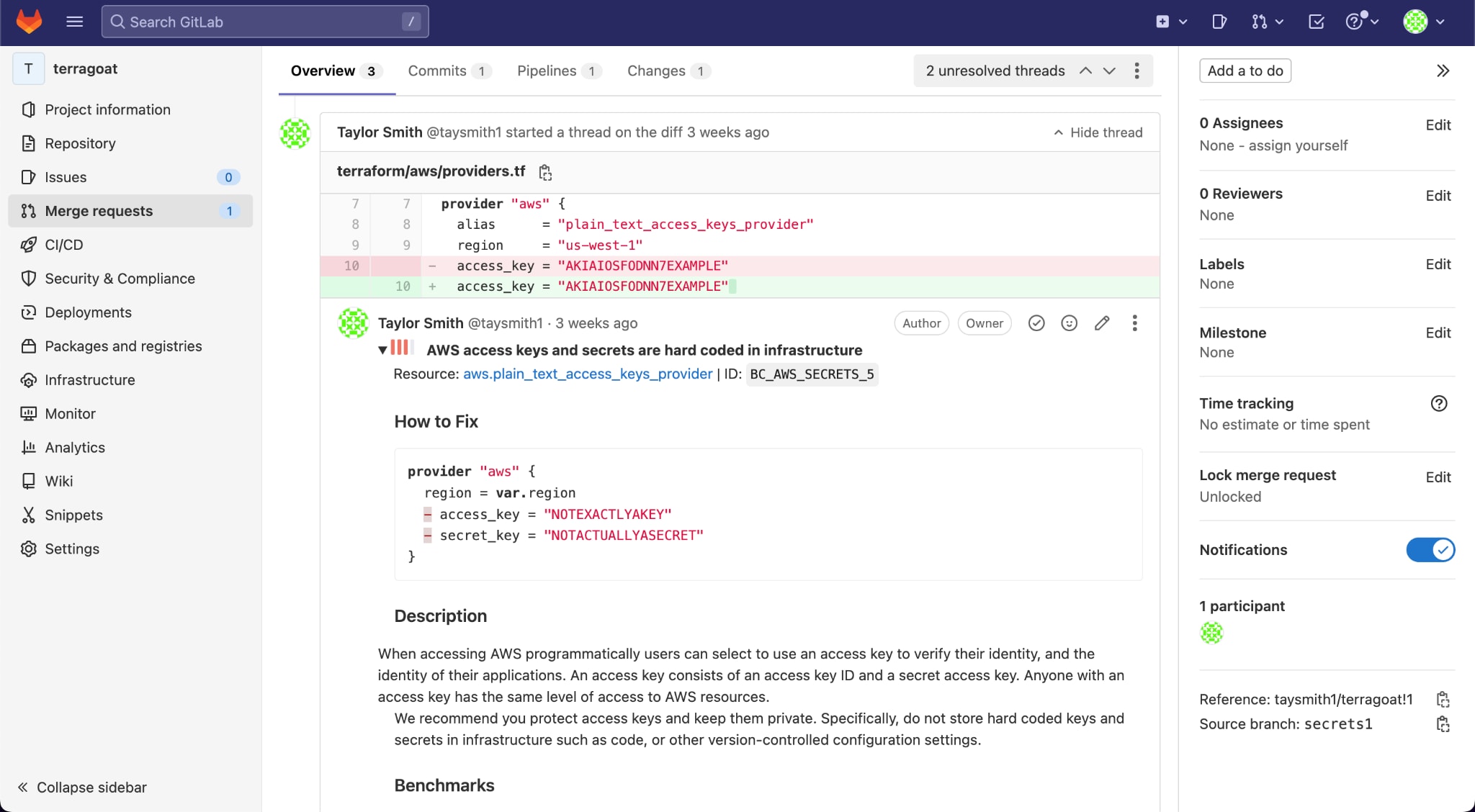
Native Developer Feedback
Developers have numerous ways to understand the risks associated with secrets that are exposed or vulnerable:
- IDE, CI/CD, VCS: Robust coverage across numerous development workflows deliver risk insights wherever developers build and compile their code.
- Projects: Native integrations in dev workflows seamlessly surface detected secrets within a file that is non-compliant.
- Supply chain: The Supply Chain Graph displays the source code file nodes. A detailed investigation into the dependency tree helps developers identify the root cause of secret exposure.
- Pull request comments: Users can spot potentially leaked secrets as part of their pull request scans, which can be easily removed.
- Pre-Commit hooks and CI integrations: Leverage the pre-commit hook to block secrets from being pushed to a repository before a pull request is opened.
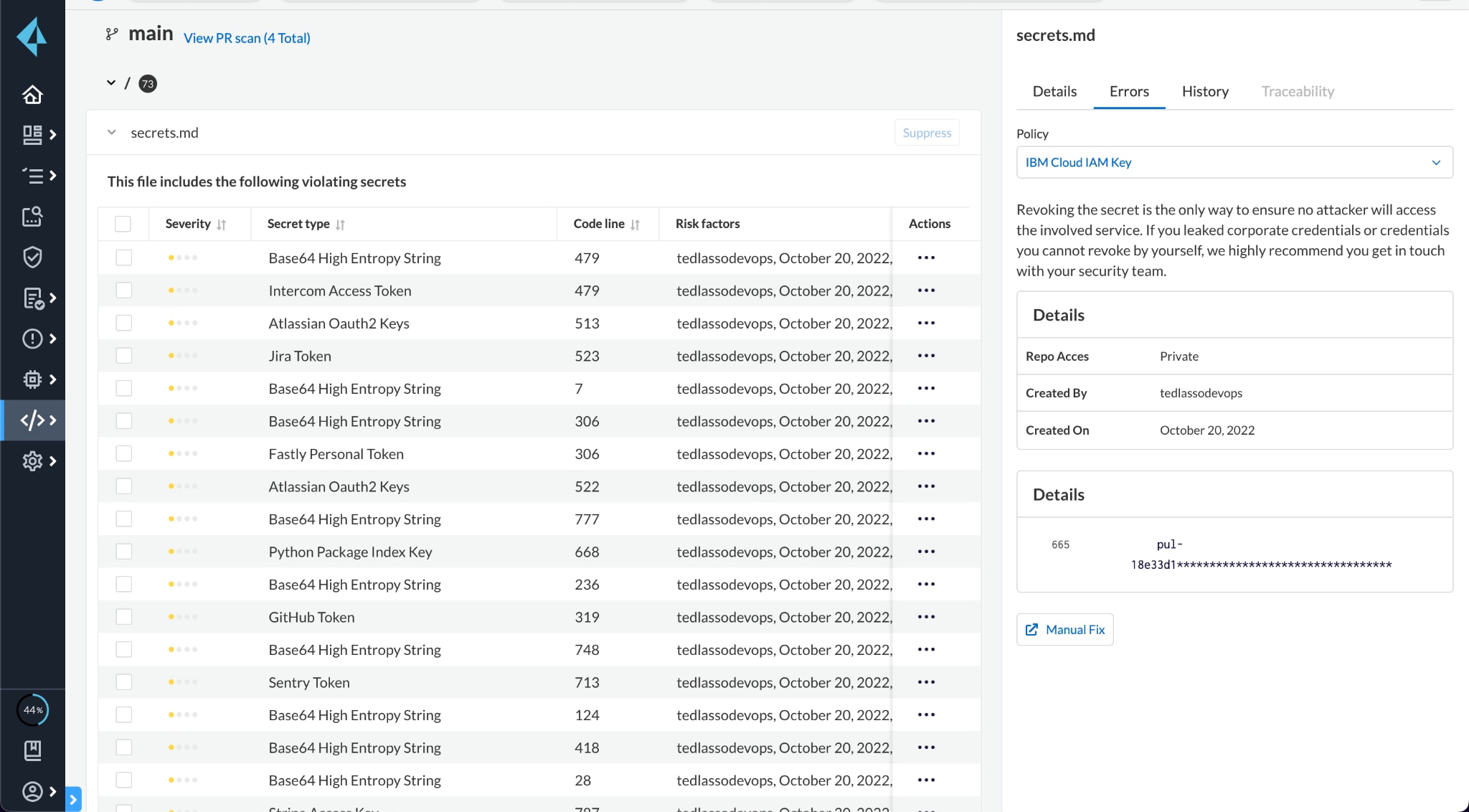
Risk Factor Context for Prioritization and Faster Remediation
Alerts with context are the most actionable. For this reason, the secrets security module uses three parameters when analyzing how vulnerable an at-risk secret is:
- The last Git user who modified the file that triggered the potential secret exposure and is responsible for fixing the issue, plus who will be impacted if you rotate the secret key.
- Timeline of error date(s) to better understand how long the risk has been exposed and prioritize accordingly.
- Whether the repository storing the file is private or public (can be accessed directly from the internet). Publicly exposed secrets are extremely consequential because they can be easily leveraged and exploited in minutes, whereas exposed secrets in a private repository are much less severe.
Users can easily investigate alert details using the in-product search to gain deeper information into specific error properties.
Part of the CNAPP
The new Prisma Cloud Secrets Security module can be natively integrated across the code, build, deploy, and runtime phases of the application lifecycle. With single-click activation that expands coverage across the supply chain and a powerful multidimensional approach that combines both a signature-based policy library and a fine-tuned entropy model, exposed and vulnerable secrets are swiftly identified in IaC templates, golden images, and Git repositories, as well as in running environments. With coverage for all file types, only Prisma Cloud offers the depth and breadth required to effectively secure secrets.
To learn more about Prisma Cloud’s innovative approach to secrets security, join us for our upcoming Product Deep Dive webinar on January 17th.