Identity is the new perimeter. In almost every modern breach, the attacker's primary goal is to compromise credentials and move laterally across the network. To do this, they start at the same place: The Active Directory (AD).
We are excited to announce a powerful new capability available now for Cortex ITDR (Identity Threat Detection and Response): Malicious LDAP Query Protection.
This module delivers ITDR directly via the Cortex XDR agent. This enhances Domain Controller (DC) security by shifting from log analysis to real-time, autonomous prevention.
The Problem: The "Phone Book" is Open to Everyone
Think of your Active Directory as the organization's "phone book." It contains every user, every permission, and every address. By design, it is built to answer questions, receiving millions of legitimate queries every hour from users logging in, sending emails, or accessing resources.
This availability makes the DC the "brain" of the company. Since every user inherently has access to the Active Directory, once an attacker compromises a single user account, they effectively gain access to query the organization's entire neural center.
Before launching a full-scale attack, threat actors enter a reconnaissance phase. They query this "phone book" to identify privileged users, groups, and potential attack paths. Because the DC is designed to answer these questions, attackers can often map out your entire network, finding the "keys to the kingdom", without tripping standard alarms.
The specific challenge is scale. As discussed in recent Unit 42 research, a single DC serving 100,000 users processes millions of queries per hour. Sifting through this volume to find a single malicious reconnaissance attempt is like finding a needle in a haystack of needles.
The Solution: From Manual Detection to Autonomous Prevention
While previous approaches relied on manual hunting or post-event log analysis, our Research team has taken those methodologies and automated them into an autonomous defense layer.
Our researchers didn't just write rules; they actively simulated attacks against test environments using popular tools to model the exact behavioral patterns of adversaries. This allows the Cortex XDR agent on the DC to analyze traffic directly at the source.
How It Works: Context is King
To accurately distinguish between a legitimate query and an attacker's reconnaissance, the module analyzes the context of the traffic in real-time.
A single query might look innocent on its own. However, the module connects the dots, analyzing the single query in relation to the last 100 queries from the same address, to reveal malicious intent.
We analyze several key behavioral dimensions:
- Source of Query: Is this query coming from a trusted admin workstation or an anomalous endpoint?
- Number of Queries (Volume): We monitor for massive spikes in read operations. A legitimate user might look up one or two contacts; a tool like BloodHound will query thousands of objects in seconds.
- Contextual Patterns: We evaluate the "who" and "why." If a user account suddenly deviates from their standard behavior, performing lookups that don't match their role, the system flags it.
- Query Attributes: We identify specific search filters (like searching for adminCount=1 or unconstrained delegation) that are rarely used in business logic but are highly valuable to attackers.
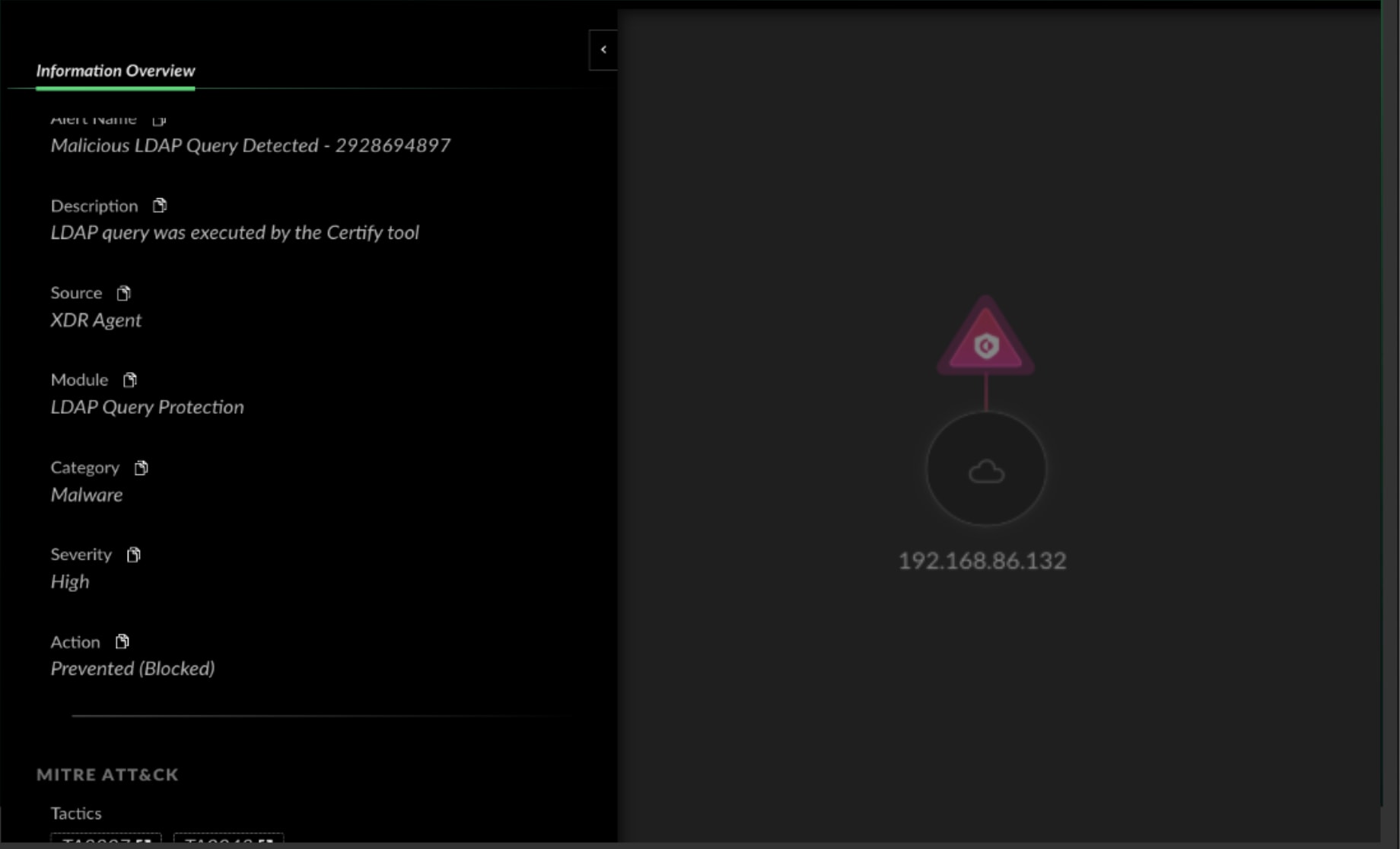
Blocking the Tools of the Trade
This module can now identify and block the unique signatures of specific tools, providing alerts that say not just "Suspicious Activity," but specifically "Attack detected via BloodHound."
XDR blocks pieces of malicious functionality of variants of these tools:
- BloodHound / SharpHound: Used to visualize attack paths.
- AdFind: Linked to APT groups like Stately Taurus.
- ADRecon: Used by BlackCat (ALPHV) affiliates.
- Certify: Used to exploit Active Directory Certificate Services (AD CS).
The Benefits:
Implementing this protection provides a "double profit" for security teams:
- Real-Time Prevention (The Shield): It stops the attack at the reconnaissance phase. By blocking the query, you effectively blind the attacker, forcing them to work without a map.
- Enriched Analytics (The Intelligence): Every blocked query feeds back into the Cortex ITDR analytics engine. This enriches the broader security dataset, allowing the system to generate specific "Issues" in the console. This informs SOC analysts precisely which tool was used and who was targeted, converting raw data into actionable intelligence.
Summary
Protecting the DC is non-negotiable. With Malicious LDAP Query Protection, Cortex ITDR ensures that your AD infrastructure remains a secure resource for your employees, not an open map for your adversaries.