
Patterns of Deception
Being an Account of Several Most Remarkable Cases of Electronic Mail Fraud, as Related by Dr. Watson of the Digital Crime Division of the deductions made by the singular Detective Aems (advanced email security).
Author's Note: The company names mentioned herein are cited solely as examples of criminal impersonation. No association with the legitimate enterprises is implied, and all trademarks remain the property of their rightful owners.
A Preface from Dr. Watson
In all my years documenting the extraordinary methods of Detective Aems, I have observed a consistent pattern: where the conventional investigators of Scotland Yard's Cybersecurity Division stumble about with their crude instruments and pedestrian logic, my colleague employs a revolutionary system of deduction that sees beyond the obvious to the very heart of criminal intent.
The cases I present here demonstrate not merely the inadequacy of traditional email security investigative methods, but the transformative power of scientific reasoning applied to the dark art of electronic deception. Where others see isolated fragments, Detective Aems perceives the intricate web that binds all evidence together.
The Adventure of the False Banking House
"Watson," said Detective Aems, settling into his chair with characteristic precision, "observe how our colleagues from the Yard have once again been thoroughly outmaneuvered."
I examined the evidence before us: an electronic missive purporting to originate from the venerable Wells Fargo institution, detected within the correspondence systems of a prominent financial house. The message appeared unremarkable, a simple notification from Google Drive regarding a shared document.
"Inspector Lestrade and his Secure Email Gateway division found nothing amiss," I noted. "They declared it legitimate correspondence from a trusted cloud service."
"Precisely their error," Aems replied, his keen eyes scanning the document with that peculiar intensity I had come to recognize. He withdrew a photographic plate from his files and placed it before us. "Observe, Watson, examine this captured image of the initial deception."
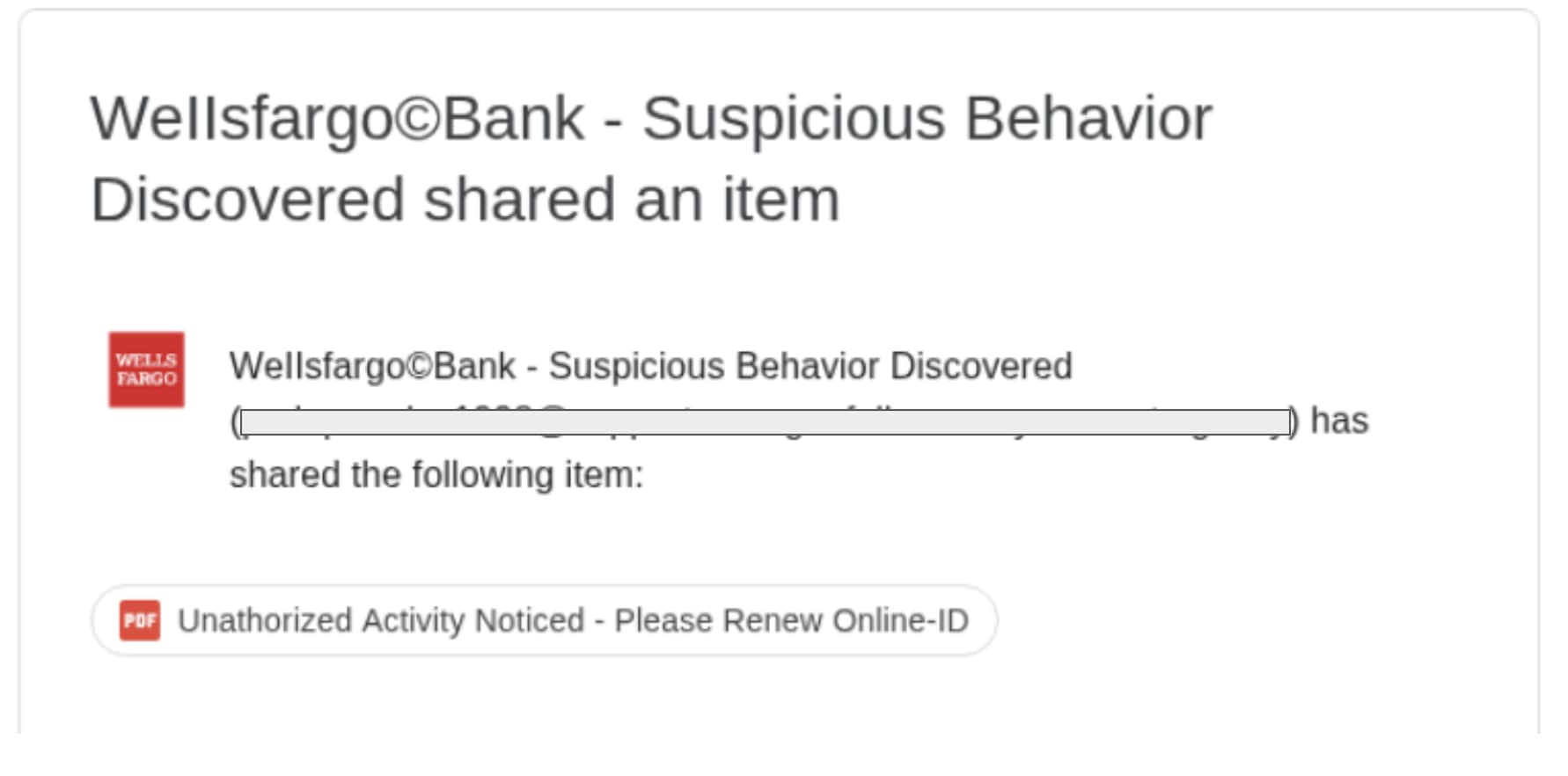
"They see a tree and declare the forest safe. Notice the sender's authentication records, they betray a most curious anomaly." He gestured to his analytical engine, which I had learned to regard with something approaching reverence. Unlike the crude scanning devices employed by the Yard, this remarkable instrument possessed what Aems termed 'contextual reasoning', the ability to perceive patterns invisible to lesser methods.
"The document title contains a deliberate misspelling," Aems continued, pointing to the evidence, "'Unаthоrized Асtivity Nоtiсеd', Cyrillic characters masquerading as Latin ones. The link leads not to a simple document, but to a redirect chain culminating in a credential harvesting apparatus."
He produced a second photographic specimen. "Behold the final stage of their elaborate trap."

"Protected by a CAPTCHA challenge, a most ingenious method to simultaneously reassure the victim of legitimacy while blinding automated detection systems."
"But surely," I protested, "the automated scanners would detect such deception?"
"Ah, Watson, there you echo the very fallacy that renders the Yard's methods obsolete. Their scanners, like Lestrade himself, see only what lies immediately before them. The CAPTCHA blocks their automated analysis entirely, rendering them as blind as bats in daylight."
Detective Aems rose and approached his correlation engine, a device that, I confess, seemed to border on the supernatural in its capabilities. "My methods, however, synthesize the sender's anomalous authentication, the emotional manipulation inherent in the subject line, and the suspicious redirect pattern. The truth becomes unmistakable: this is no mere phishing attempt, but the opening gambit of a sophisticated financial fraud campaign."
The Case of the Streaming Service Imposters
The following month brought two remarkably similar cases that further illustrated the gulf between conventional and scientific detection methods, alongside what I have termed "The Administrator's Gambit" and "The Document Deception."
"Four separate criminal enterprises," Aems announced, "each employing sophisticated personalization techniques. Two pose as streaming services, one as internal administration, and another as a document sharing service."
"Two separate criminal enterprises," Aems announced, "both employing brand impersonation with consummate skill. The first poses as the Netflix streaming service, the second as Spotify."
Inspector Lestrade had arrived at our chambers in a state of considerable agitation. "We've examined both communications thoroughly," he declared. "Well-formatted emails, legitimate corporate branding, no malware detected. Our scanners found nothing suspicious whatsoever."
"And therein lies your fundamental misconception," Aems replied with barely concealed disdain. He produced two photographic specimens from his case files. "You search for what you expect to find, while the modern criminal operates in the spaces between your assumptions."
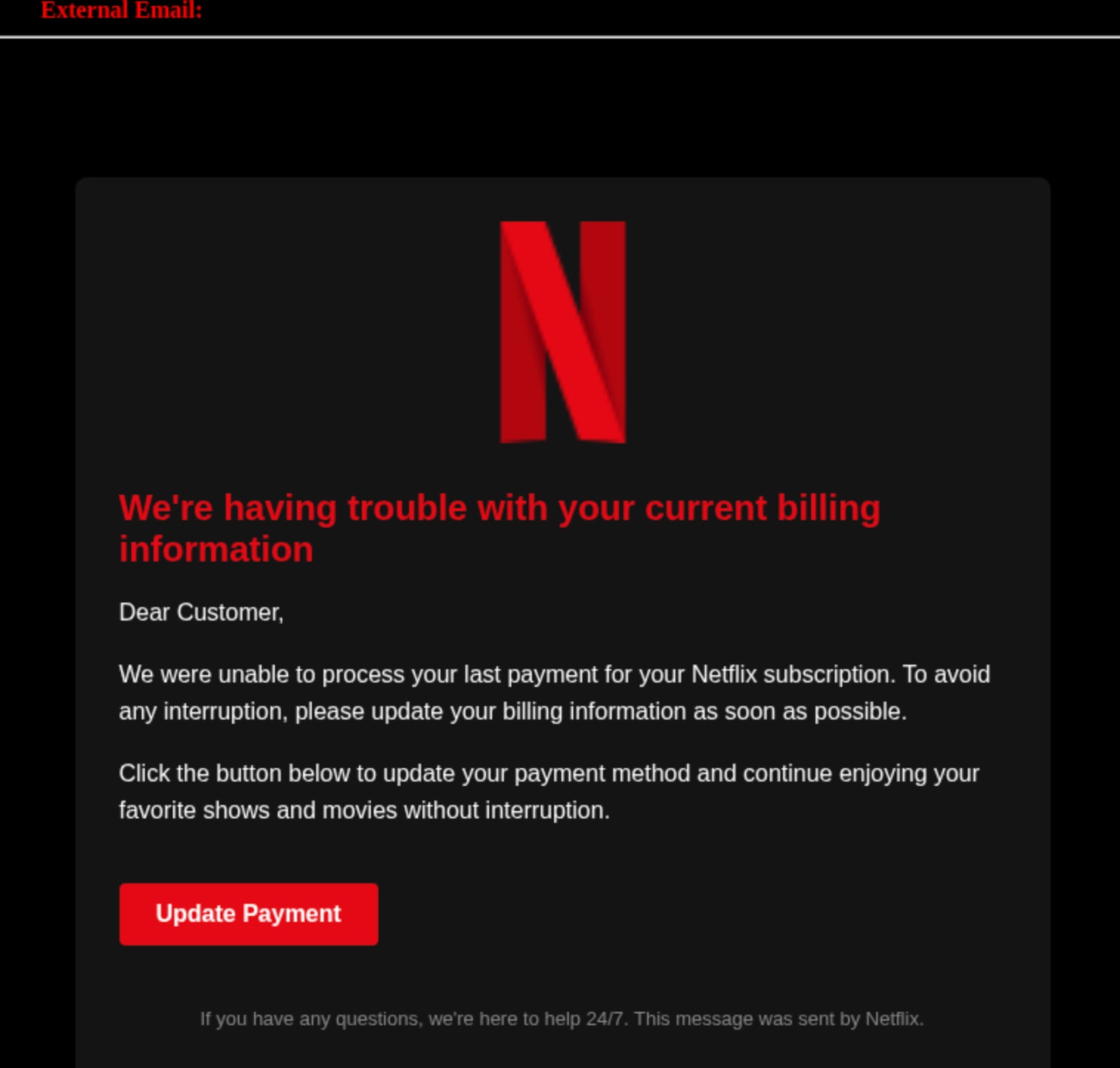
"Observe the Netflix deception," he said, indicating the first photograph. "Perfect replication of corporate styling, yet examine the sender authentication carefully."

He placed the second specimen beside the first. "The Spotify campaign employs identical psychological techniques: urgency regarding billing information, official branding to establish trust, and calls-to-action designed to bypass rational thought. Both warn of payment problems, both demand immediate action."
"But if the content appears legitimate”, Lestrade began.
"Content, my dear Inspector, is but one note in a complex symphony. Observe the sender authentication records, SPF, DKIM, and DMARC protocols all reveal discrepancies invisible to your surface-level analysis. High-reputation logos paired with low-reputation sending domains create a pattern my system recognizes as characteristic of brand impersonation fraud."
The demonstration was, as always, flawless. Where the Yard saw legitimacy, Detective Aems perceived deception with crystalline clarity.
But the evening's revelations were far from complete. "Observe these additional specimens," Aems continued, producing two more photographic plates from his extensive files.
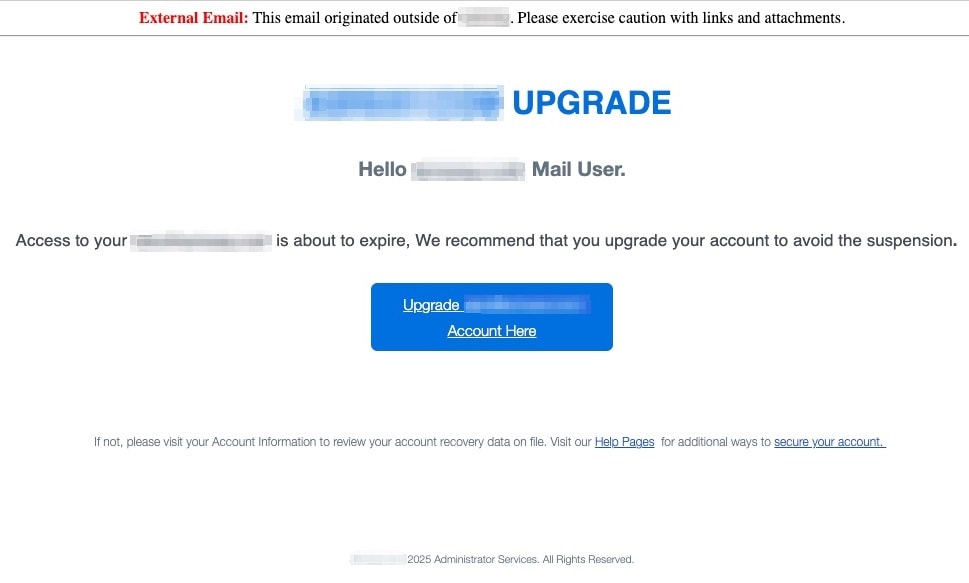
"The Administrator's Gambit—a highly targeted communication claiming account expiration, complete with flawless execution and official signatures. No grammatical errors, perfect corporate styling, yet entirely fraudulent."
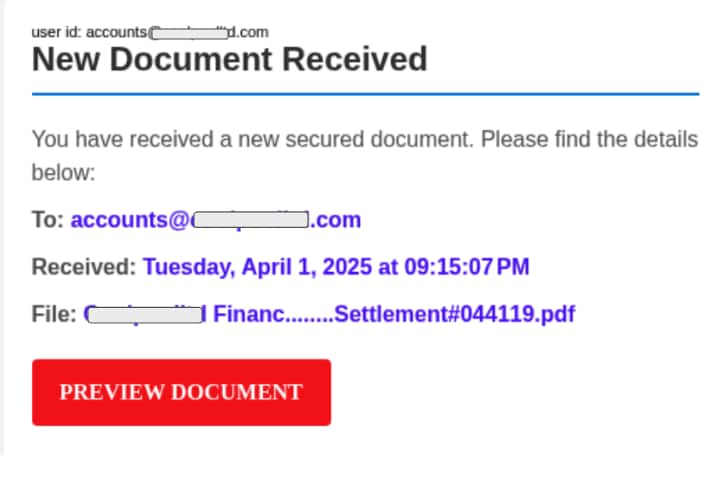
"And here, the Document Deception—personalized correspondence addressing the victim by name and referencing their specific organization. The criminals have invested considerable effort in reconnaissance to achieve such verisimilitude."
"How could we possibly detect such sophisticated impersonations?" Lestrade asked with evident frustration.
"By recognizing that perfection itself can be a warning sign," Aems replied. "When combined with unusual sender authentication and subtle psychological manipulation tactics, these 'perfect' communications reveal their true nature to the trained eye."
The Mystery of the Linguistic Deception
Perhaps no case better illustrated the limitations of conventional methods than the affair I have come to call the Brazilian Invoice Fraud.
"A most elegant deception," Aems mused, producing a photographic plate from his international case files. "With the help of Gen AI, the criminals have localized their approach, observe this masterpiece of cultural deception."
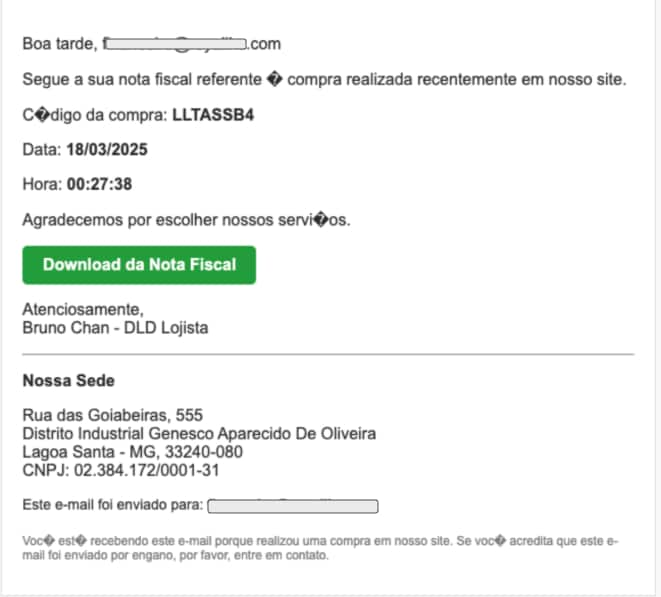
"An invoice written in Portuguese, formatted to mimic the legitimate 'Nota Fiscal Eletrônica' standard used in Brazilian commerce," he explained, pointing to specific elements within the captured correspondence.
"Our URL scanners found nothing suspicious," reported Inspector Bradstreet. "The link pointed to Dropbox, a thoroughly reputable service."
"Your scanners," Aems replied with characteristic precision, "suffer from the same myopia that afflicts all conventional detection. They perceive the destination, Dropbox, and conclude safety." He withdrew a second specimen from his files. "But observe what lies beyond their limited vision."
"They cannot predict that the link will force an automatic download, nor can they distinguish between the promised PDF and the actual executable payload. This CAPTCHA challenge ensures their blindness remains complete."
His advanced linguistic analysis engine, a marvel that could process intent across multiple languages, had identified the true nature of the threat within moments. "The combination of authentication failures, the mismatch between displayed file type and actual delivery mechanism, and the financial fraud patterns embedded in the Portuguese text created an unmistakable signature."
"How could we have known?" Bradstreet asked with evident frustration.
"By abandoning your reliance on surface appearances," Aems replied, "and embracing the scientific method of correlation and deduction."
The Adventure of the Internal Impostor
The final case in this series presented what Aems considered the most insidious form of deception: the impersonation of internal authority.
An electronic message, crafted to appear as an urgent communication from the victim organization's IT department, had successfully bypassed every conventional security measure. Aems withdrew the evidence from his files with particular care.
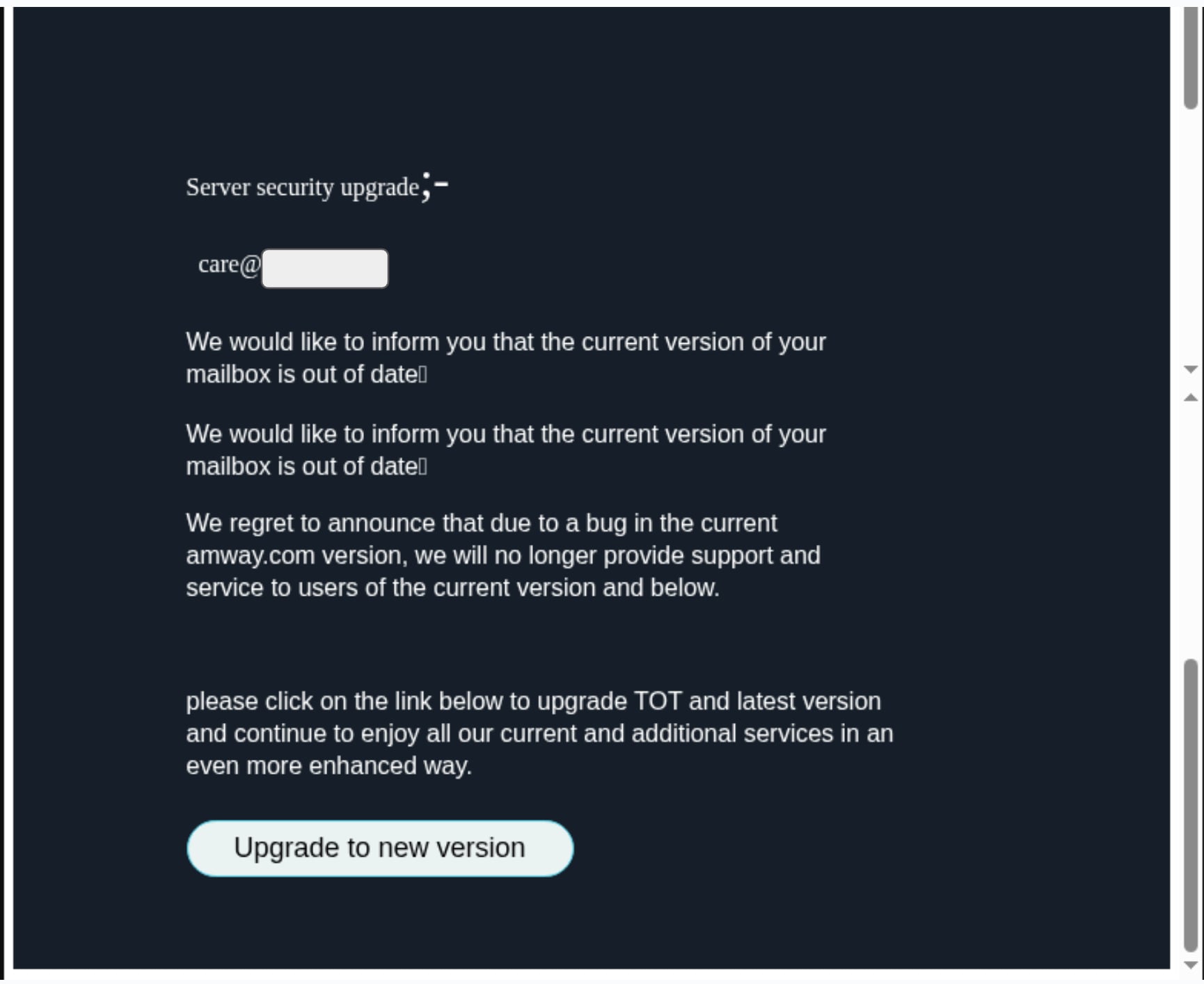
"Most ingenious," admitted Inspector Hopkins, examining the photographic specimen. "Our systems saw an internal communication and applied minimal scrutiny. The corporate branding appears entirely authentic. How were we to suspect external manipulation?"
"By observing what you consistently ignore," Aems replied, pointing to subtle indicators within the captured message. "The sender's external origin, despite internal appearance. The unusual urgency for a routine update. The psychological manipulation designed to bypass careful consideration."
He activated what he termed his 'multi-signal detection protocol', a process that synthesized numerous subtle indicators invisible to conventional analysis. "Individual elements might appear innocuous, but their combination reveals unmistakable criminal intent. It is precisely this holistic approach that separates scientific detection from mere mechanical scanning."
The Science of Digital Deduction
As I conclude this account, I am struck by the consistent pattern revealed across these cases. The methods employed by Scotland Yard’s Cyber Division, their Secure Email Gateways and mechanical filters, are but limited, reactive instruments, unable to perceive the full attack lifecycle. They are blind men groping for a shilling where gold is hidden.
Detective Aems’s revolutionary approach (Advanced Email Security), operating from the Cortex platform, provides a profound remedy. He employs 'unified visibility', a superior form of scientific digital deduction that synthesizes email threat data with crucial telemetry from identity, endpoint activity, and the network.
This correlation permits his analytical engines to achieve three critical and previously unattainable results:
Firstly, to Understand true intent with Gen AI, Aems utilizes formidable Large Language Models (LLMs). These instruments pierce the flawless linguistic disguises, often perfected by the adversary’s own Gen AI, thus revealing the true, malignant purpose of sophisticated phishing and BEC campaigns that static rules cannot register.
Secondly, through this 'Unified Visibility,' Aems correlates all scattered indicators to meticulously chart the entire, obscured multi-stage attack path. Where conventional methods see fragments, Aems constructs the complete, logical sequence.
And lastly, to Provide Automated, Cross-Domain Response, his system enables action with instantaneous finality. This remedy moves far beyond simple message quarantine, instantly neutralizing the entire threat by disabling compromised accounts and isolating affected endpoints, thereby reducing the Mean Time to Respond (MTTR) to the mere blink of an eye.
The criminal enterprises of the Gen AI digital age grow ever more sophisticated, wielding artificial intelligence and psychological manipulation with unprecedented skill. Against such adversaries, the old, mechanical methods prove dangerously obsolete. Only through embracing the scientific principles exemplified by Detective Aems, correlation, contextual analysis, and deductive reasoning, bolstered by the unwavering intelligence of the Cortex platform, can we hope to defeat this evolving digital criminality.
Dr. Watson
Digital Crime Division
Tannery Way Cybersecurity Laboratory
For those seeking to employ these revolutionary methods in their own investigations, detailed technical specifications may be found on our Advanced Email Security page.