-
What Is Cloud Security?
- Why Is Cloud Security Important?
- Essential Elements of a Cloud Security Strategy
- The Three Pillars of Cloud Security
- How Does Cloud Security Work?
- Three Categories of Cloud Service Models
- The Shared Responsibility Model
- Top Cloud Security Risks and Challenges
- Cloud Security Tools
- Cloud Security Best Practices
- Cloud Security FAQs
- How to Assess Risk in the Cloud
- What Is a Cloud Service Provider?
-
Defining Organizational Cloud Security Responsibilities
- What Is Infrastructure as a Service?
- Top 3 Cloud Security Considerations
-
Why You Need Cloud Security
-
Four Ways to Improve Cloud Security and Compliance
- Cloud Security Glossary & FAQs
- Cloud Security Is a Shared Responsibility
-
ASPM Best Practices for Enhancing Your Security Posture
- ASPM Foundations and Strategic Benefits in Cloud Environments
- Establishing Centralized Visibility and Data Organization for Continuous Monitoring
- DevSecOps Culture Integration and Shift-Left Security Practices
- KPI Alignment and Remediation Workflows for Vulnerability Management
- Advanced ASPM Optimization and Proactive Risk Management
- ASPM FAQs
17 Tips to Securely Deploy Cloud Environments
The key to cloud security starts with an understanding of the components of your cloud stack. Its various layers – services, identity, app edge, load balancer, compute and storage – create potential targets and represent areas within the cloud environment you need to secure.
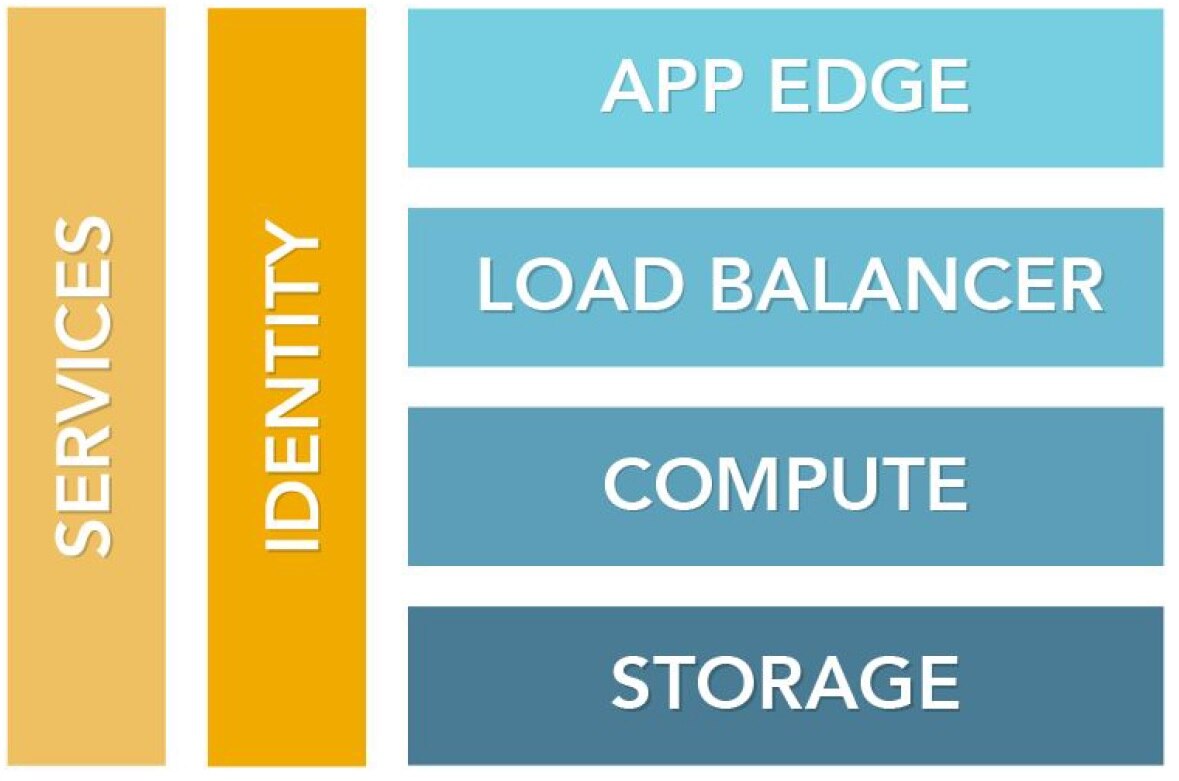
Figure: Layers of a cloud stack
5 Tips to Lock Down Identity Management
Identity and access management determines which parts of the cloud stack users have access to, as well as what they have permission to do when they’re there. If a bad actor can gain access to systems using legitimate credentials, compromise is nearly certain.
To lock down identity management, consider the first five tips that follow.
1. Require Secure Passwords
Use the longest password or passphrase allowed by the system, or use a complex password that includes a mix of letters, numbers and symbols.
2. Implement Multifactor Authentication (MFA) Everywhere
Having a strong password isn’t enough. Organizations need multiple layers of protection. Using a second validation or authentication method provides another layer of protection for user logins.
3. Create Least Privilege Roles
Give users access to the fewest number of accounts and systems that allow them to be productive. This limits the damage that can result from a mistake or if a bad actor gains access to an account.
4. Disable Inactive Accounts
When employees leave an organization, their access to all systems, as well as their access keys, should immediately be disabled. Inactive accounts leave more endpoints vulnerable, and inactive accounts aren’t usually monitored as rigorously as active accounts, which opens the possibility for inactive account activity to go unnoticed for a period.
5. Monitor for Suspicious User Behavior or Compromised Credentials
Use real-time monitoring that leverages machine learning and analytics to identify suspicious activity and compromised account credentials.
Secure the Compute Layer
Organizations should take steps to secure the compute layer to ensure availability of systems and data, and to keep bad actors from using their compute power to spread malware across the business and internet.
Use these next five tips to fortify compute layer security.
6. Harden the Operating System
Remove unnecessary programs that only serve to broaden the attack surface. Make every effort to stay up to date on service packs and patches.
7. Continuously Check for Misconfigurations and Anomalies
Use automated tools to detect changes across the environment as well as anomalous behavior.
8. Enable Secure Login
Issue secure shell (SSH) keys to individuals. SSH keys will keep assets protected when moving across unsecured networks.
9. Implement Inbound and Outbound Firewall Rules
Set definitive rules about what, how much and who can send, receive and access inbound and outbound data.
Many organizations are reluctant to set up outbound rules, but because attackers will attempt to steal (exfiltrate) sensitive data and intellectual property, it’s important to ensure outbound rules are explicitly defined.
Firewall rules need to be created at the application layer rather than the transport or network layer (IP and port information). This practice will prevent attackers from piggybacking off open ports (such as the domain name system [DNS] on port 53).
10. Use Only Trusted Images
Build images from scratch or get them from trusted sources, such as AWS or Microsoft Azure. Don’t use images from Stack Overflow or random message boards and user communities.
Secure Storage
If attackers get access to the storage layer, they can potentially delete or expose entire buckets or blobs of data.
Use the following six cloud security tips to secure your storage.
11. Manage Data Access
Identity and access management (IAM) policies and access control lists (ACLs) help you centralize the control of permissions to storage. Security policies allow organizations to enable or deny permissions by accounts, users or based on certain conditions – such as date, IP address or whether the request was over a Secure Sockets Layer (SSL) encrypted session.
12. Classify Data
Automatically classify data to understand what type of data is stored and where. Data classification policies should match security policies, and any violations should be flagged or automatically remediated.
13. Encrypt, Encrypt, Encrypt!
Encrypt data in transit and at rest. Note that the metadata is often not encrypted, so organizations shouldn’t store sensitive information in cloud storage metadata.
14. Enable Versioning and Logging
Versioning allows organizations to preserve, retrieve and restore data if something goes wrong. With versioning turned on, businesses can restore data from an older version if a threat or application failure causes data loss.
Maintaining access logs provides an audit trail if someone or something gets into your system.
15. Do Not Allow Delete Rights (or Require MFA for Delete)
Organizations should set up roles in their cloud infrastructure that do not allow users to delete data. Many cloud storage solutions enable a feature that requires MFA to delete any version of data stored in the storage layer.
16. Continuously Check for Misconfigurations and Anomalies
Use automated tools to detect misconfigured storage and permissions settings as well as anomalous file access behavior.
Protect Your Cloud Services
After you’ve secured the perimeter and enforced smart policies, you need to focus on security specifically for your services in the cloud.
17. Use Source Control
Use source control to secure versions, access to builds and deployment instances. This practice will reduce the surface area of your code and limit the potential for attacks across your network.