- 1. How does QKD work?
- 2. What are the main types of QKD protocols?
- 3. What are the advantages and disadvantages of QKD?
- 4. How does QKD compare to post-quantum cryptography?
- 5. Where is QKD being used today?
- 6. How are governments and standards bodies shaping QKD adoption?
- 7. What's next for QKD?
- 8. QKD FAQs
What Is Quantum Key Distribution (QKD)? + How It Works
Quantum key distribution (QKD) is a method for creating and sharing secret encryption keys using the principles of quantum mechanics.
It relies on quantum states that change when observed, allowing any interception attempt to be detected. By pairing quantum transmission with classical authentication, QKD enables the secure exchange of keys for protected communication.
How does QKD work?
Quantum key distribution works by sending information using quantum particles—usually photons—to create a shared secret key between two endpoints.
Each photon encodes a bit of data in a quantum state. That state might represent polarization or phase. When the photons travel through a fiber or free-space channel, any attempt to measure them changes their properties. Which means interception can’t happen without being noticed.
In a typical setup, two parties—commonly called Alice and Bob (although below, we’ll refer to them as Leia and Luke)—use a quantum channel to transmit photons and a classical channel to verify results.
The quantum channel carries the raw key material. The classical channel handles coordination and authentication. Both are essential. The quantum exchange ensures security through physics. The classical exchange makes sure both sides are talking to each other, not an attacker.
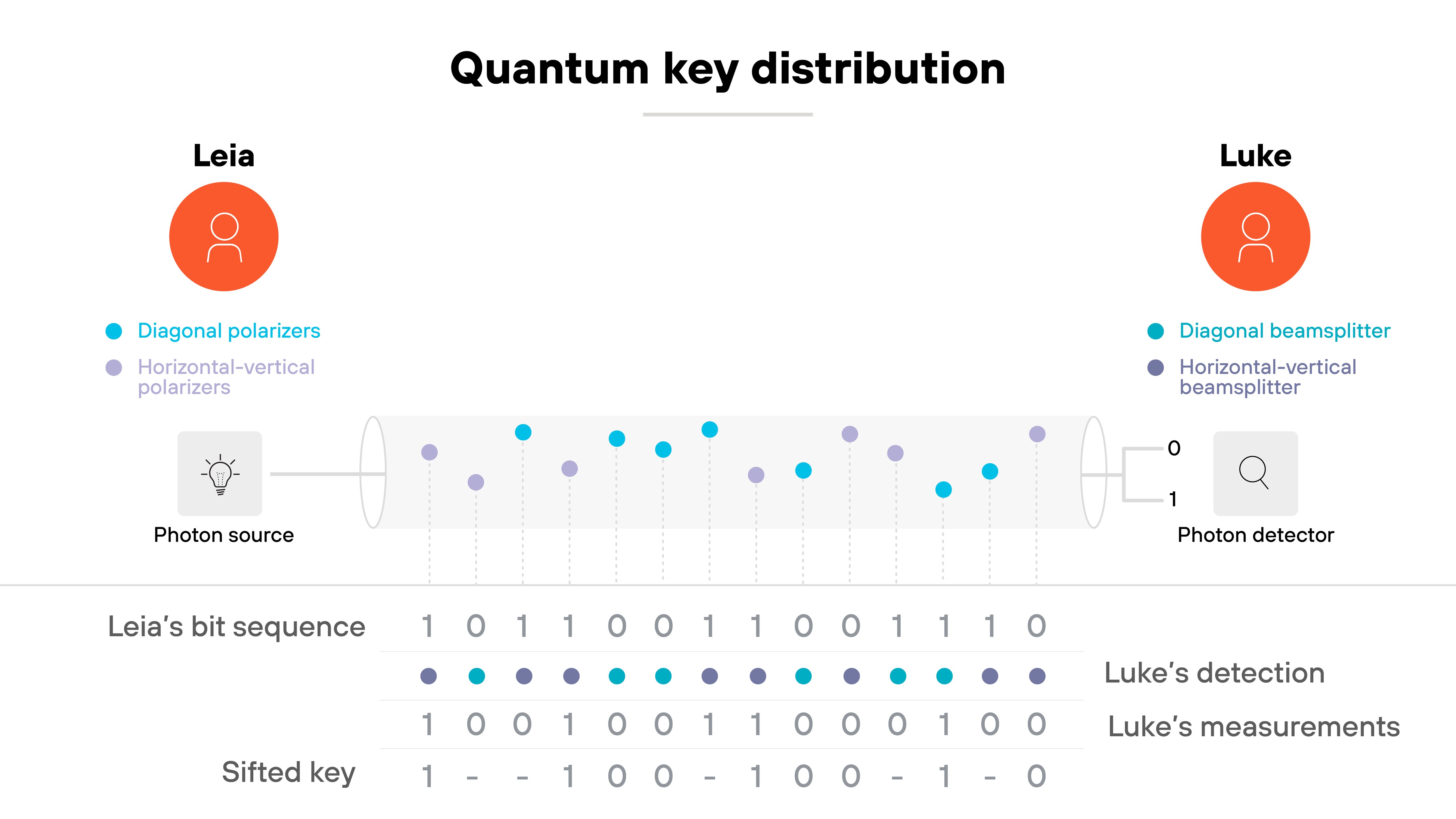
-
After transmission, the participants compare a portion of their measurement results. This step reveals whether an eavesdropper has tampered with the photons. If the detected error rate stays below a defined threshold, they keep the rest of the data as a "sifted key."
-
That key is then refined through two final stages: error correction and privacy amplification. Together, these processes remove mismatched bits and reduce any information an attacker could have learned. The result is a shared, secret key ready for use in encryption.
To simplify it:
QKD turns the laws of quantum mechanics into a method for detecting intrusion and generating encryption keys that can't be copied or read in transit.
What are the main types of QKD protocols?
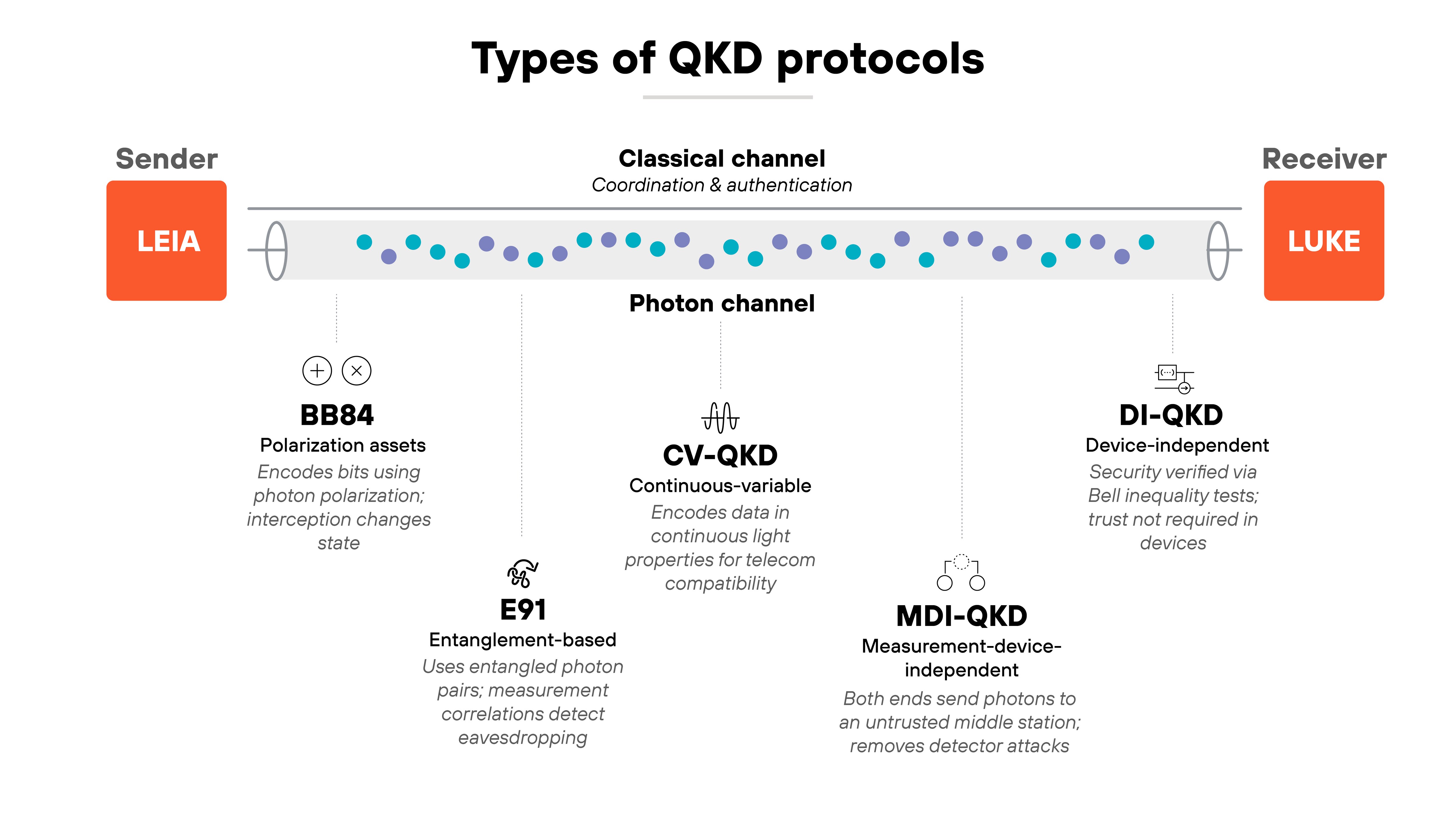
Quantum key distribution protocols all aim to do the same thing: generate a shared secret key between two parties using quantum physics. But the way they achieve it differs.
Each protocol represents a step in the evolution of how QKD has been tested, verified, and hardened against attack.
In other words, the differences show how far the field has come from theory to practical systems.
BB84
The BB84 protocol was the first practical design for QKD.
It uses photons encoded in one of two possible bases to represent bits. When the receiver measures those photons, the results depend on whether their chosen basis matches the sender's.
If an eavesdropper tries to intercept the transmission, it changes the photon states and creates detectable errors. That's why BB84 is still used as a reference model for modern QKD systems. It's simple, proven, and foundational.
E91
The E91 protocol builds on quantum entanglement.
Instead of sending individual photons, it uses entangled photon pairs shared between two parties. Measuring one photon instantly determines the state of the other, no matter the distance. So if an eavesdropper interferes, the correlations change in measurable ways.
E91 provides stronger theoretical security, but it's harder to implement reliably in real-world networks.
CV-QKD
Continuous-variable QKD, or CV-QKD, encodes information in continuous properties of light such as amplitude and phase.
It works with standard telecom components, which makes it easier to integrate into existing fiber networks. However, it requires very precise detection and noise control.
In practice, CV-QKD trades some physical complexity for better compatibility with commercial infrastructure.
MDI-QKD
Measurement-device-independent QKD, or MDI-QKD, solves one of the biggest vulnerabilities in earlier systems: detector attacks. Instead of trusting either party's detectors, it sends signals to a third measurement node that can even be untrusted.
The security comes from quantum correlations rather than the devices themselves. This architecture eliminates a major implementation loophole and has become central to large-scale QKD networks.
DI-QKD
Device-independent QKD, or DI-QKD, pushes this idea further. It removes the need to trust any internal workings of the devices used.
Security is based entirely on the statistical violation of Bell inequalities, which is a quantum property that cannot be faked classically. In theory, it provides the strongest possible assurance of security. In practice, it's still experimental and limited by demanding conditions like high detector efficiency and low signal loss.
Beyond these core protocol families, research is also advancing methods that extend how QKD can be deployed. Twin-field QKD (TF-QKD) increases how far keys can travel by letting both parties send signals to a shared middle point. Trusted nodes and experimental quantum repeaters relay keys across longer distances, supporting wide-area and future intercontinental networks.
In sum:
Each protocol reflects a balance between theory and engineering:
- BB84 and E91 proved QKD was possible. CV-QKD made it practical.
- MDI-QKD made it secure against hardware flaws.
- DI-QKD is shaping what the future of fully trustless quantum communication could look like.
What are the advantages and disadvantages of QKD?
Quantum key distribution offers strong security benefits. But it also faces practical limits. QKD is powerful in theory and controlled environments. It becomes harder to deploy at scale.
Here’s how the benefits work.
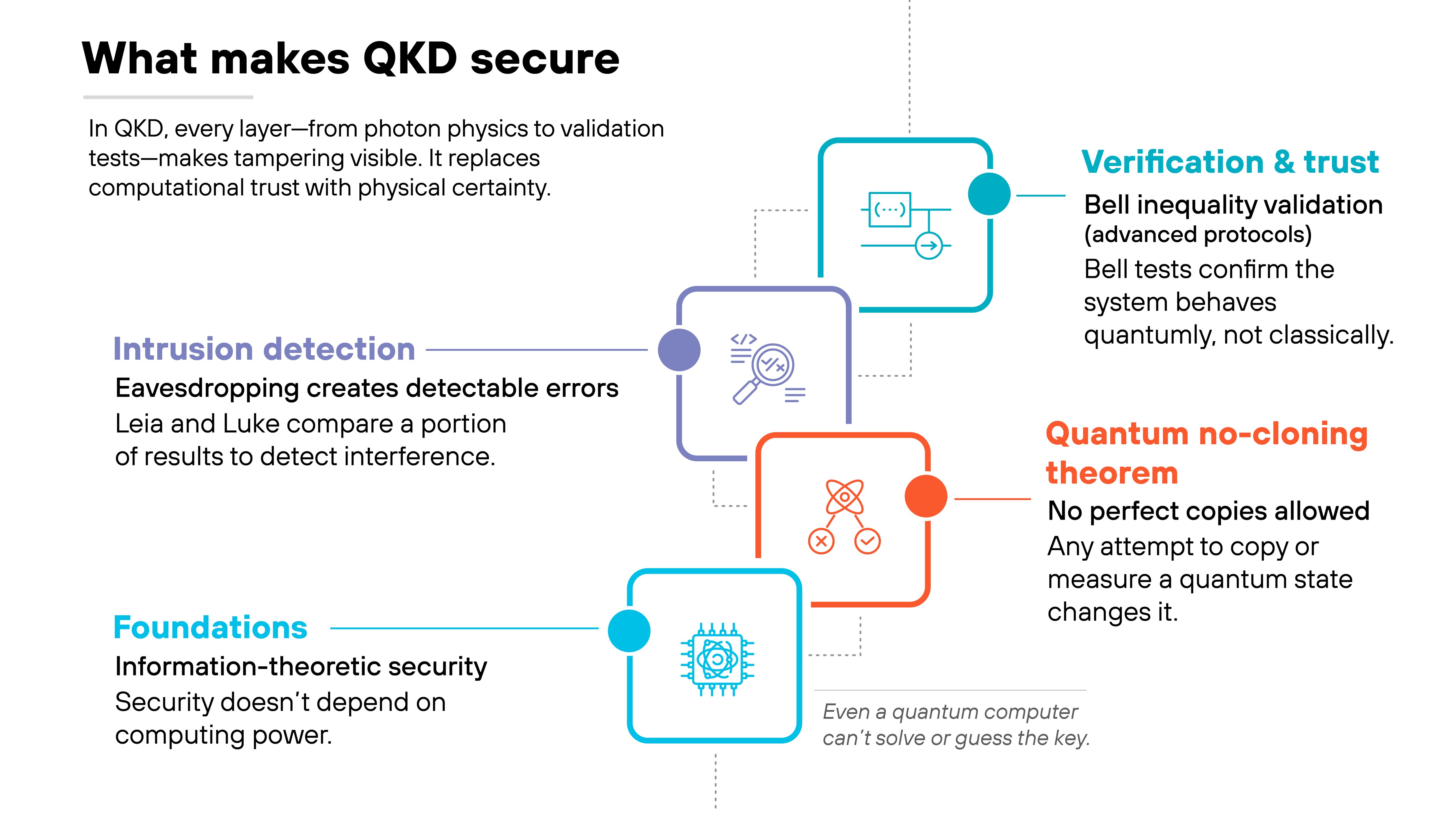
-
QKD provides information-theoretic security.
That means the secrecy of the key does not rely on assumptions about an attacker's computing power. Even a future quantum computer would not be able to break the key itself. The protection comes from how information is encoded into quantum states and how those states behave when observed.
-
Which leads to the quantum no-cloning theorem.
An unknown quantum state cannot be perfectly copied. Any attempt to intercept or duplicate the transmitted photons changes their state. Leia and Luke detect those changes when they compare a portion of their results. If the error rate rises above a threshold, they discard the session.
-
Some protocols add another layer through Bell inequality tests.
These tests check whether the system behaves according to quantum mechanics. If the correlations can't be explained classically, the link is considered secure. That matters for advanced models such as E91 and device-independent QKD.
Now let's walk through the challenges and limitations.
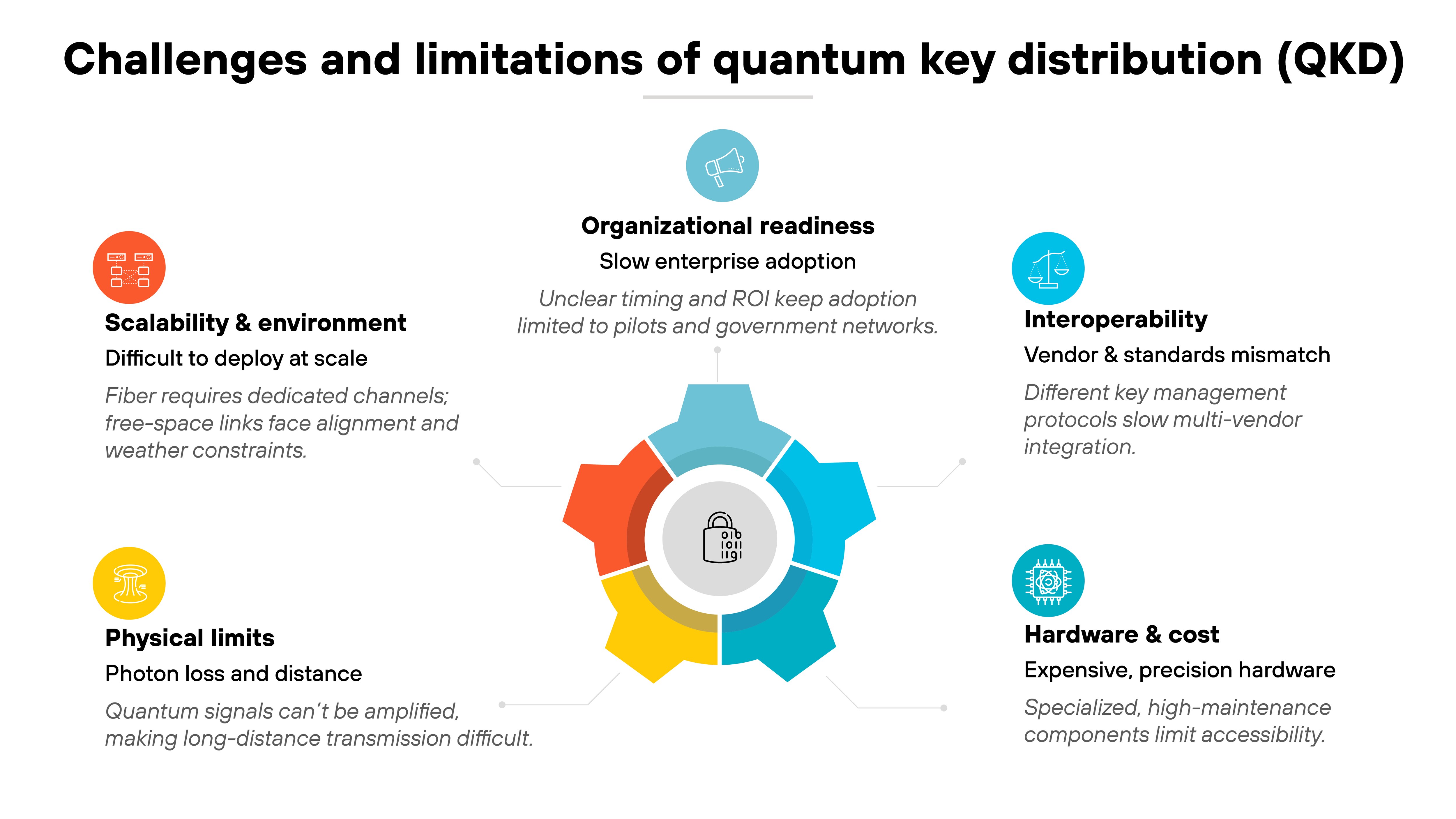
Photon loss increases sharply with distance.
Quantum signals weaken as they move through fiber or free space. They also can't be amplified without breaking coherence. That means long-distance links require trusted nodes or experimental quantum repeaters. Each option adds complexity and risk.
QKD hardware introduces cost.
Systems rely on single-photon sources, detectors, and temperature-controlled optics. Each component needs precise alignment and ongoing monitoring. That limits adoption outside research networks and high-security environments.
Scale is another obstacle.
Fiber-based systems need dedicated optical channels and stable environmental conditions. Free-space and satellite systems help, but they depend on alignment windows and weather conditions. Building continuous coverage takes coordination that few organizations are ready for.
Interoperability is also a challenge.
Vendors use different key-management protocols and interfaces. ETSI and ISO standards are addressing this gap. But integration across legacy equipment remains uneven. That slows multi-vendor deployments.
And there's also the question of readiness.
Many decision-makers understand the theory. But they remain unsure about timing and return on investment. That uncertainty keeps QKD deployments concentrated in governments, defense networks, and telecom pilots.
In practice, QKD's value depends on where it is applied. It offers strong security in controlled or high-assurance environments. It becomes more difficult to use across large, heterogeneous networks. Those tradeoffs shape where QKD fits today and how it will evolve alongside other quantum-safe approaches.
How does QKD compare to post-quantum cryptography?
Quantum key distribution and post-quantum cryptography both aim to protect data from quantum attacks. But they take entirely different paths to get there.
One is based on physics. The other on mathematics. So they're complementary, not competing, approaches.
Post-quantum cryptography, or PQC, is encryption that can resist attacks from both classical and quantum computers.
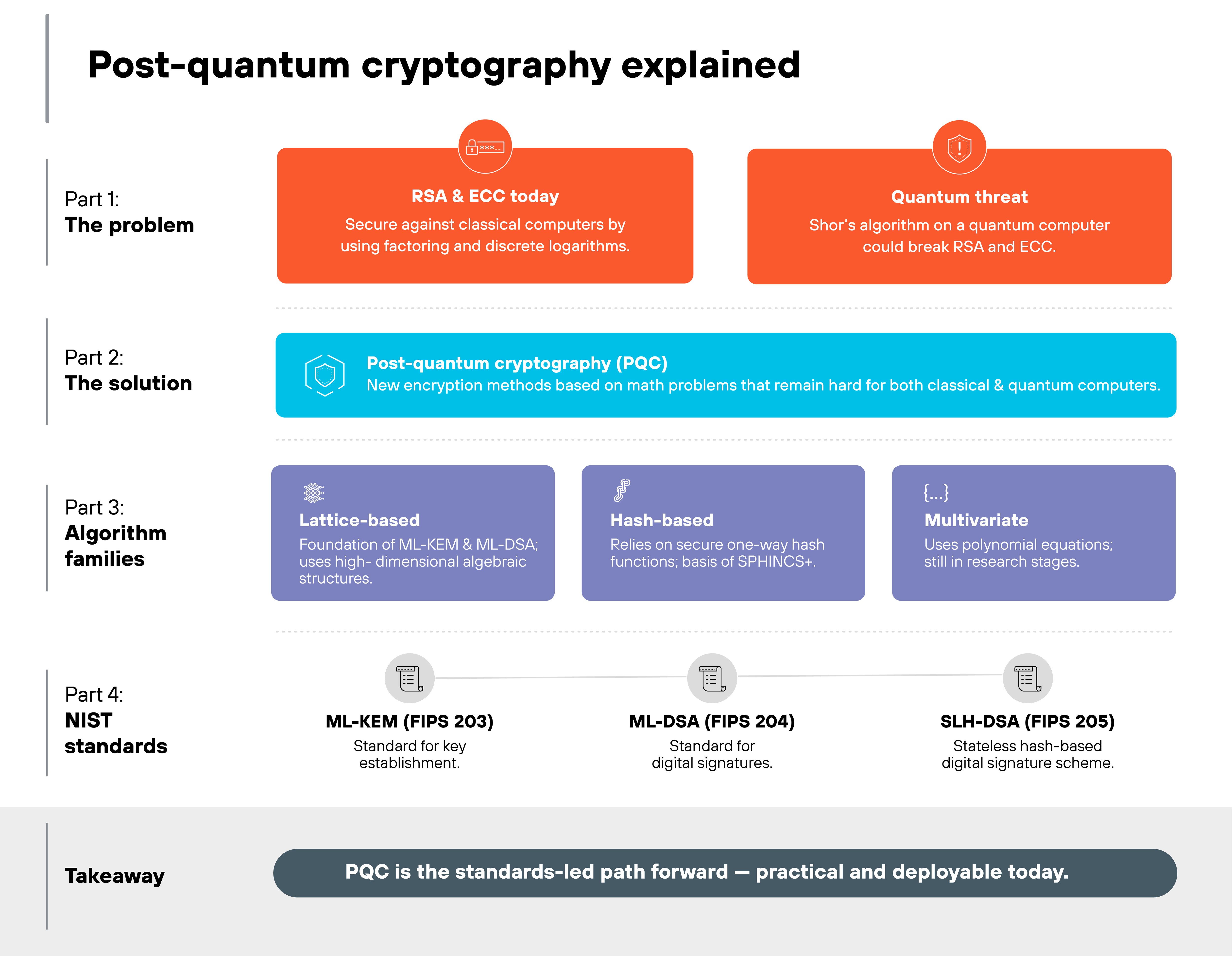
It does this by using new mathematical problems that are hard for any computer to solve efficiently. These algorithms are designed to drop into today's systems without major hardware changes, and they're seen as the way forward for quantum security.
In contrast, QKD secures communication by detecting eavesdropping through quantum mechanics. Its security doesn't depend on computation at all.
| Comparison: QKD vs. PQC at a glance |
|---|
| Aspect | Quantum key distribution (QKD) | Post-quantum cryptography (PQC) |
|---|---|---|
| Security basis | Physics of quantum measurement and no-cloning | Hard mathematical problems (lattice, code, multivariate) |
| Primary defense model | Detects interception in real time | Prevents decryption by quantum algorithms |
| Implementation | Requires quantum hardware and optical links | Software-based; runs on existing infrastructure |
| Scalability | Limited by distance, photon loss, and cost | Highly scalable through classical networks |
| Standardization | Defined under ISO/IEC 23837 and ETSI QKD 014 specifications | NIST FIPS 203, FIPS 204, FIPS 205 |
| Operational maturity | Early-stage deployments; specialized use | Ready for near-term enterprise rollout |
| Integration potential | Works alongside classical encryption | Can combine with QKD for layered defense |
Some national cybersecurity agencies currently recommend prioritizing post-quantum cryptography for most organizations. Guidance from the UK’s NCSC and the U.S. NSA notes that PQC can be deployed widely using existing infrastructure, while QKD requires specialized hardware and is suited to more limited, high-assurance scenarios.
This guidance focuses on near-term practicality rather than dismissing QKD’s security model, which continues to be explored in specialized and long-term confidentiality use cases.
Both are evolving as part of a broader quantum-secure ecosystem.
PQC will safeguard most digital systems through stronger algorithms. QKD will protect the highest-value links where key secrecy must endure for decades.
They're not competing technologies. They're complementary defenses in the post-quantum era.
Where is QKD being used today?
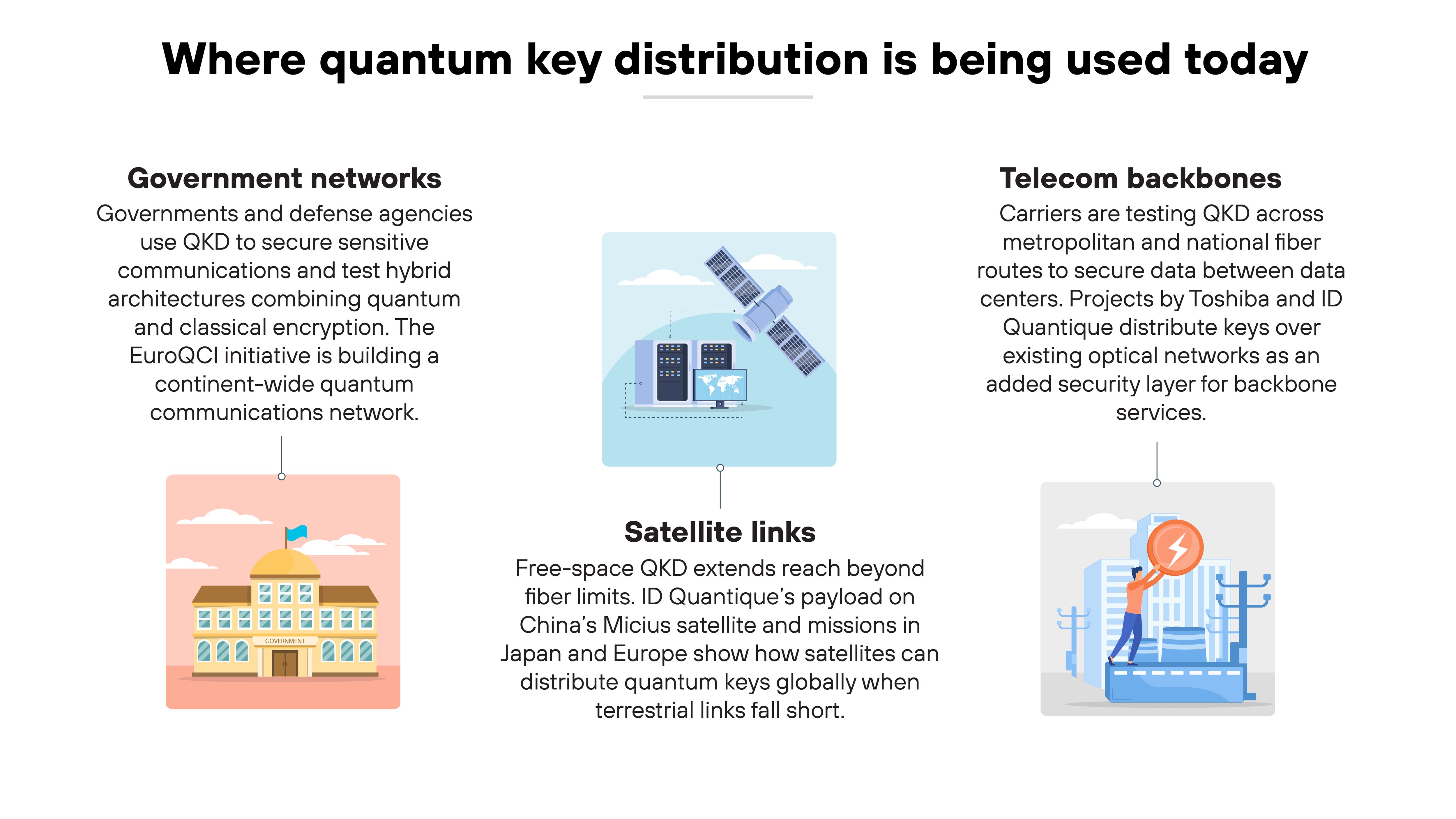
Quantum key distribution has moved beyond the lab. Real-world pilots are showing how it can protect sensitive data across critical networks.
The most active deployments today focus on telecom infrastructure, satellite links, and government communications.
Here's what that looks like in practice.
Telecom backbones
Major carriers are testing QKD across metropolitan and national fiber routes. These pilots focus on securing data moving between data centers and cloud interconnects.
Projects led by Toshiba and ID Quantique use commercial optical fibers to distribute keys alongside regular traffic. The goal is to integrate QKD with existing optical network equipment rather than replace it.
For all practical purposes, QKD is being treated as an added security layer for critical backbone services, not a standalone replacement.
Satellite links
Free-space QKD experiments are extending reach beyond fiber limits. Satellites act as trusted relay nodes, distributing quantum keys between distant ground stations.
European and international programs are expanding this model through coordinated satellite research and pilots.
ID Quantique's payload on the Chinese Micius satellite, along with upcoming missions in Japan and Europe, show that satellite-based QKD can provide global coverage when terrestrial links fall short.
Government networks
Government agencies are among the earliest adopters. National defense, intelligence, and energy sectors use QKD to secure communication between critical command sites.
These deployments often combine QKD with classical encryption and post-quantum algorithms to test hybrid architectures. In Europe, the EuroQCI initiative is coordinating national pilots to create a continent-wide quantum communications infrastructure.
Bottom line:
QKD is no longer theoretical. It's being tested in real optical networks, on orbiting satellites, and within strategic government systems.
The technology still faces scale and cost hurdles, but pilot programs are proving it can work in the field. And that's laying the foundation for quantum-secure networks worldwide.
How are governments and standards bodies shaping QKD adoption?
The next phase of QKD is about more than pilots. It's about coordination across systems so they interoperate, scale, and meet regulatory expectations.
Governments, standards bodies, and research organizations define how QKD should be built, tested, and deployed. That collaborative structure turns isolated experiments into scalable infrastructure.
ISO/IEC established the first international standard for evaluating QKD systems.
ISO/IEC 23837-1 sets security assurance, conformance testing, and interoperability principles. It gives vendors a shared basis to demonstrate that implementations meet agreed criteria. Part 2, now in development, extends this to full system evaluations.
ETSI complements this on the telecommunications side.
ETSI QKD 014 specifies system architectures, interfaces, and key management protocols. These specifications enable secure interoperability across optical networks. ETSI's quantum-safe work also aligns QKD with post-quantum cryptography in hybrid models.
NIST supports the ecosystem through measurement science and cross-program coordination.
Its current work emphasizes practical hybrid models that combine algorithmic and physical-layer security, including authentication and key-lifecycle integration.
CEN-CENELEC leads parallel efforts in Europe.
The Q04 and Q05 reports map use cases, standardization gaps, and readiness levels for quantum communications. They connect pilots to regulatory frameworks and cybersecurity certification, laying groundwork for a pan-European quantum network.
QKD is moving from experimental setups to regulated infrastructure. International efforts are giving it structure so future quantum networks are interoperable, auditable, and compatible with existing cryptographic ecosystems.
What's next for QKD?
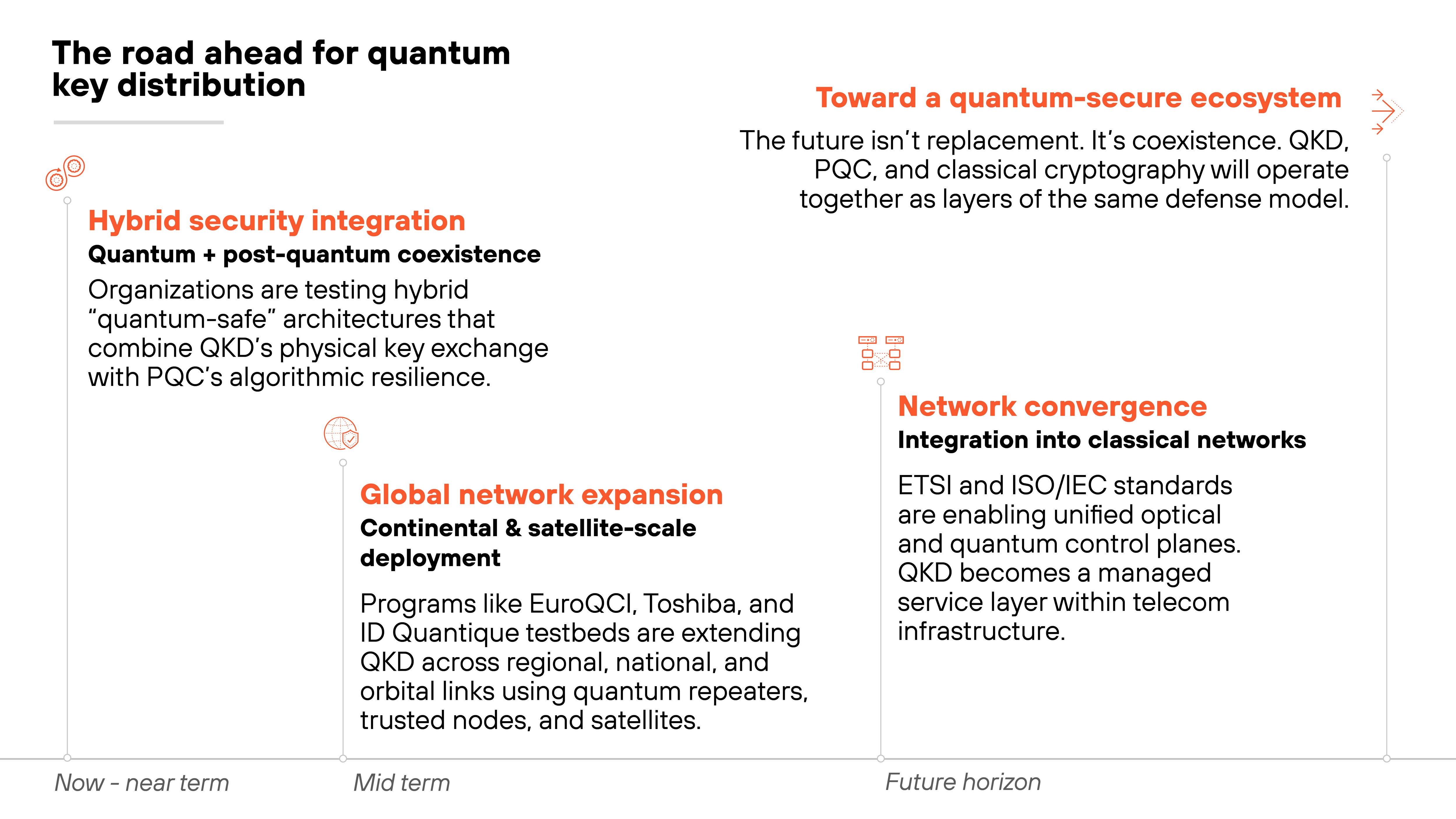
The future of quantum key distribution is about expansion: turning pilot networks into scalable, interoperable systems that work alongside classical and post-quantum cryptography.
Here's where it's headed.
The first frontier is integration with post-quantum cryptography.
Experts see QKD and PQC as complementary layers of defense.
PQC protects data through new algorithms, while QKD provides real-time detection of eavesdropping. Hybrid models that combine both—known as quantum-safe architectures—are already being tested in pilot networks.
So security will come from layered design, not a single technology.
Next is the expansion toward large-scale quantum networks.
New initiatives are extending QKD's reach beyond regional links toward continental and global coverage.
Efforts like the European Quantum Communication Infrastructure (EuroQCI) and global testbeds led by Toshiba and ID Quantique are demonstrating large-scale integration through quantum repeaters, trusted nodes, and satellite relays.
The aim is continuous, end-to-end key distribution across national and international networks.
Finally, QKD is heading toward network convergence.
Rather than operate in isolation, quantum channels will integrate into existing optical networks through standardized interfaces and control planes.
ETSI and ISO/IEC frameworks are defining those mechanisms now. This is what will turn today's pilots into quantum-secure service layers that telecom providers can scale and manage.
Looking ahead, QKD's future lies in coexistence. It won't replace other cryptography. It will reinforce it.
As standards mature and infrastructure evolves, QKD is poised to become part of a broader quantum-secure ecosystem that blends physical, mathematical, and operational assurance into one continuous defense model.
