- 1. What created the need for software firewalls?
- 2. How do software firewalls work?
- 3. Why use software firewalls?
- 4. What are the different types of software firewalls?
- 5. Where are software firewalls deployed?
- 6. What is the difference between a software and hardware firewall?
- 7. How software firewalls help achieve a Zero Trust strategy
- What created the need for software firewalls?
- How do software firewalls work?
- Why use software firewalls?
- What are the different types of software firewalls?
- Where are software firewalls deployed?
- What is the difference between a software and hardware firewall?
- How software firewalls help achieve a Zero Trust strategy
What Is a Software Firewall? [Why It's Needed + How It Works]
- What created the need for software firewalls?
- How do software firewalls work?
- Why use software firewalls?
- What are the different types of software firewalls?
- Where are software firewalls deployed?
- What is the difference between a software and hardware firewall?
- How software firewalls help achieve a Zero Trust strategy
A software firewall is a firewall delivered in a software form factor that runs on general-purpose hardware, virtual machines, or cloud instances. It applies the same inspection and policy enforcement functions as hardware firewalls.
Software firewalls are used to secure applications, workloads, and data where physical appliances can't be placed, like public clouds, containers, and distributed networks.
What created the need for software firewalls?
Firewalls have long enforced traffic policies at network boundaries. Hardware appliances in data centers and offices inspected traffic moving in and out — and still do. They remain essential for anchoring high-performance inspection and policy enforcement wherever physical devices can be deployed.
But environments have changed.
Applications now run in multiple clouds. Workloads are virtualized, containerized, and portable. Development cycles are faster. The result is a network without a fixed boundary.
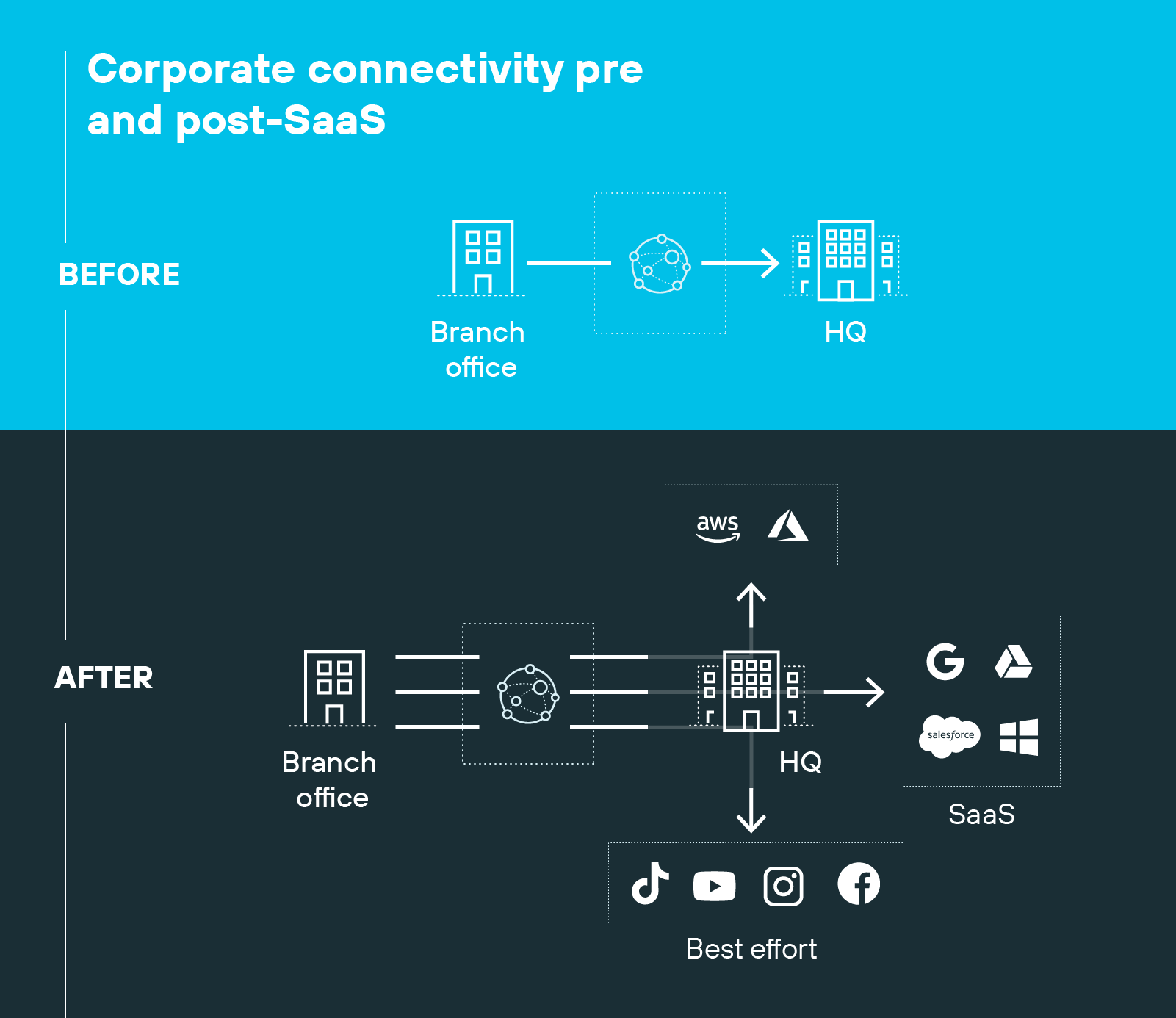
This creates new risks.
Organizations face breaches in cloud environments even with mature security programs. Developers move quickly, often relying on limited native controls. Security teams struggle to enforce consistent policy across diverse platforms. The gap between how fast applications deploy and how slowly traditional appliance rollouts adapt makes the problem worse.
Here's why this matters:
Physical appliances can't be placed inside a cloud provider's infrastructure or attached to workloads that spin up and down on demand. Security needs to extend closer to the workloads themselves, in forms that can scale as dynamically as the environments they protect.
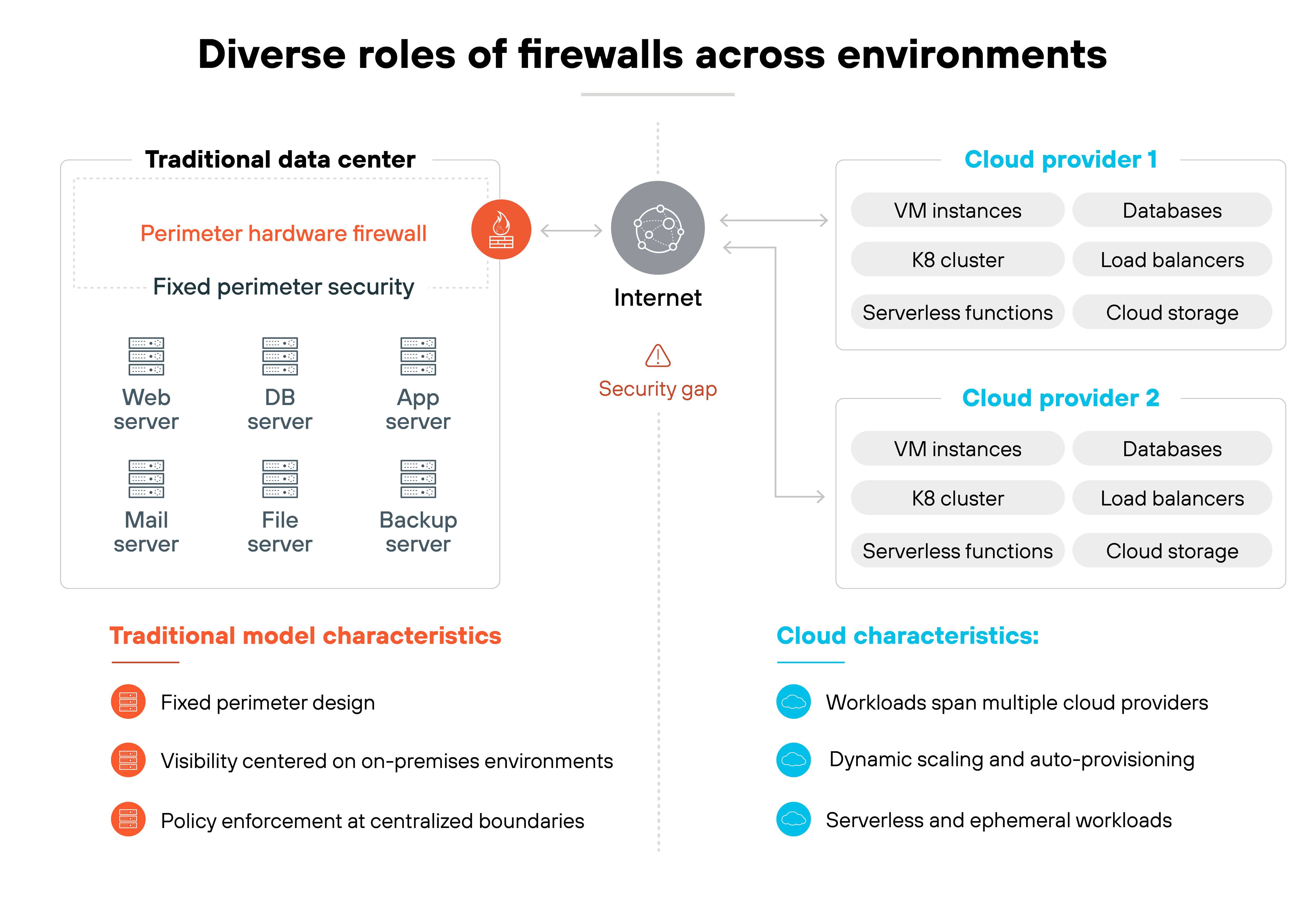
That's where software firewalls come in.
They deliver the same inspection, enforcement, and logging as appliances, but run as software on servers, virtual machines, or containers. They support automation and orchestration, making it possible to scale protection at the speed of modern deployments.
In short: hardware firewalls continue to anchor physical environments. Software firewalls complement them by covering cloud, virtual, and container use cases. Together, they extend firewall protection wherever applications and data reside
How do software firewalls work?
A software firewall inspects traffic between applications, workloads, and networks. It runs as a software process on servers, virtual machines, or cloud instances. And it applies rules to each connection.
Again, the functions are the same as a hardware firewall.
The software evaluates packets. It compares them to policy. It allows or blocks traffic. It can also track session state, enforce application-level rules, and log events for monitoring.
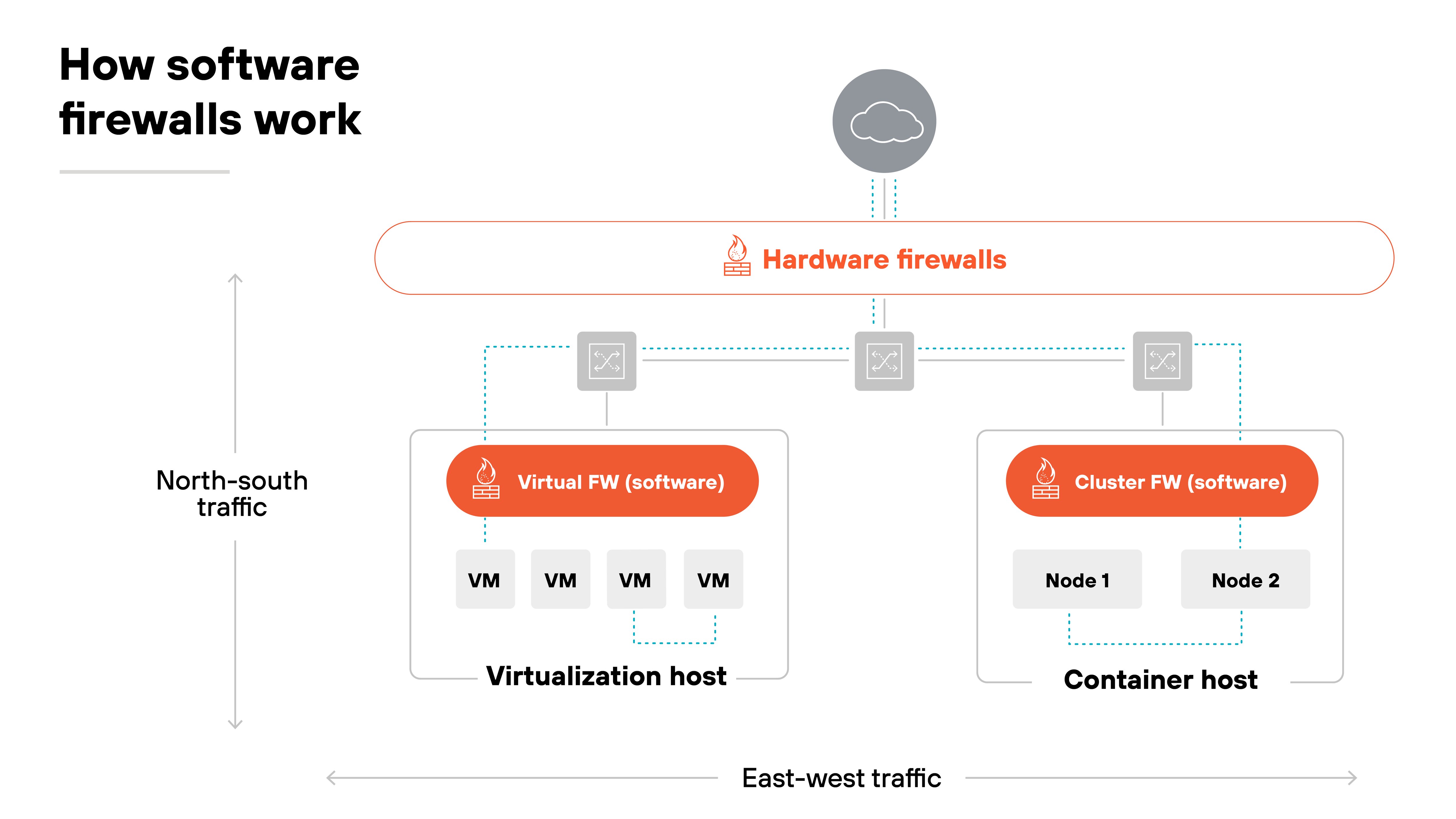
The difference is in placement.
A hardware firewall usually sits at the physical edge of a network. A software firewall runs inside virtual or cloud environments. Which means it can secure east-west traffic between workloads as well as north-south traffic entering or leaving a cloud.
In containerized environments, software firewalls integrate with orchestration platforms like Kubernetes. They enforce segmentation at the service level. And adapt to workloads that are short-lived and change frequently.
In cloud or hybrid deployments, you can spin up software firewalls wherever resources exist. They follow the workload instead of being tied to a single appliance.
Management is centralized. Policies can be defined once and applied across multiple environments. APIs and orchestration tools make it possible to automate deployment and updates. All of this reduces the need for manual configuration.
Why use software firewalls?
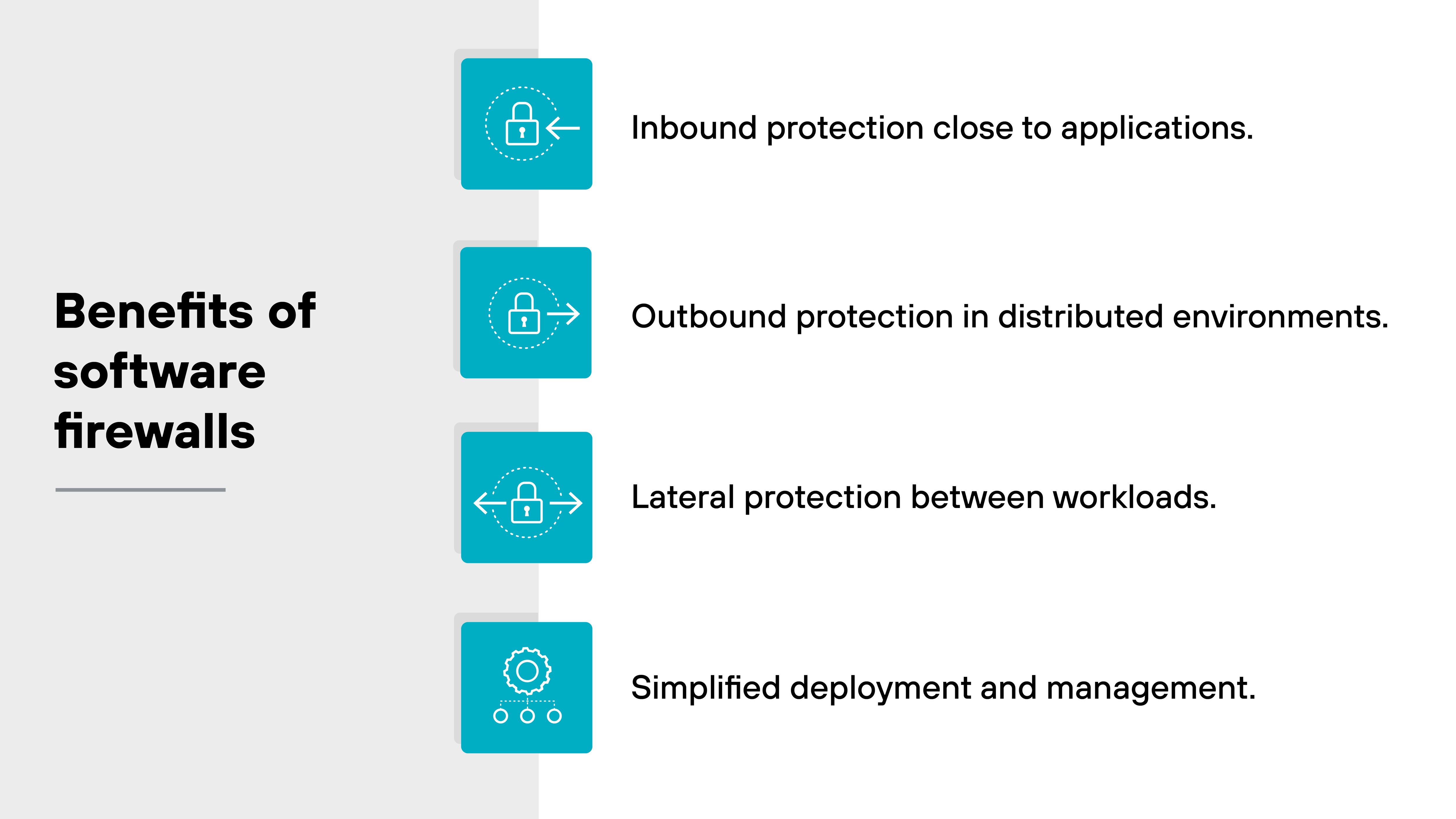
The main reason to use software firewalls is to secure environments where physical appliances aren't practical.
Like hybrid and multi-cloud networks, containerized applications, and distributed workloads. These create traffic flows that perimeter firewalls were never designed to handle. A software form factor makes it possible to place security controls closer to the resources that need them.
Software firewalls bring several advantages in these contexts.
Inbound protection close to applications.
A software firewall can sit directly in front of a database or app tier inside a cloud VPC. That way, only approved connections are allowed, limiting the risk of an attacker reaching workloads from outside.
Outbound protection in distributed environments.
Modern applications often pull code or updates from external repositories. A software firewall can monitor and restrict outbound requests from inside cloud or container platforms, ensuring only approved destinations are reached.
Lateral protection between workloads.
In dynamic environments, applications communicate heavily through APIs and service-to-service calls. Software firewalls can inspect east–west traffic within a data center or cloud, stopping threats from spreading if one workload is compromised.
Simplified deployment and management.
Software firewalls can be provisioned through orchestration tools, scaled up or down as needed, and managed centrally through policies. And that reduces the effort required to keep security consistent across dynamic environments. Whereas you can only manage policies centrally for physical firewalls.
What are the different types of software firewalls?
There are three types of software firewalls:
- Virtual firewalls
- Container firewalls
- Managed service firewalls
Each one uses the same inspection and enforcement principles, but they're applied in different ways.
Virtual firewalls
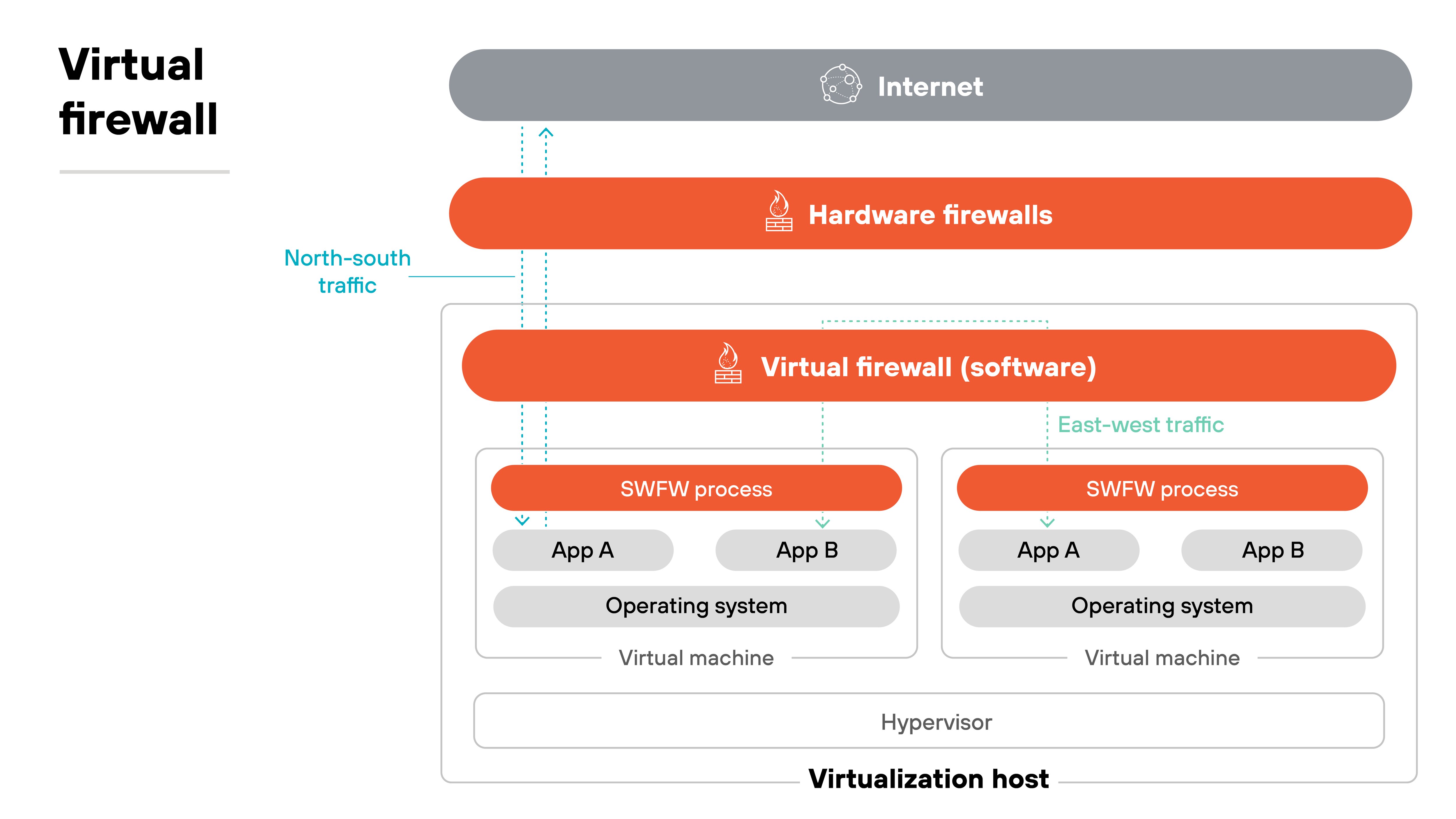
A virtual firewall runs as a software instance on a virtual machine. It's most common in public and private clouds, hybrid networks, and virtualized data centers.
Virtual firewalls can inspect north-south traffic moving in or out of the cloud.
They can also secure east-west traffic between workloads. That means it extends enforcement where cloud provider controls stop.
Plus, virtual firewalls also help segment workloads, apply consistent policy across clouds, and maintain visibility into traffic that spans providers.
- What Is a Virtual Firewall?
- What Is a Public Cloud Firewall?
- What Is Firewall as a Service (FWaaS)? | FWaaS Defined & Explained
Container firewalls
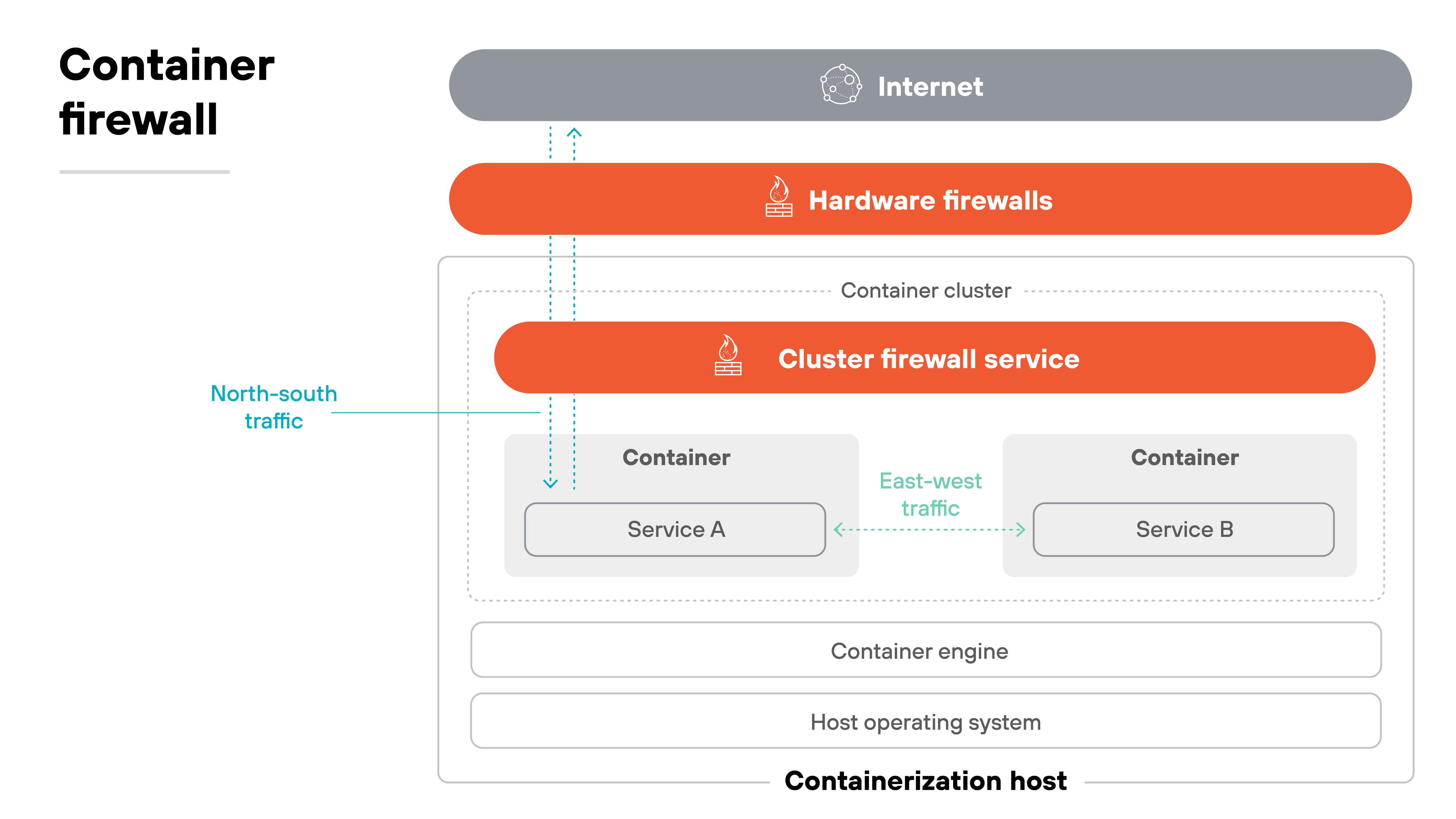
A container firewall is built for orchestration platforms like Kubernetes. Its focus is on microservices.
This is useful because containers are short-lived and highly dynamic. And traditional firewalls aren't designed to watch every service-to-service call.
But a container firewall integrates at the orchestration layer. It enforces segmentation, monitors traffic in real time, and helps secure workloads that change frequently.
Managed service firewalls
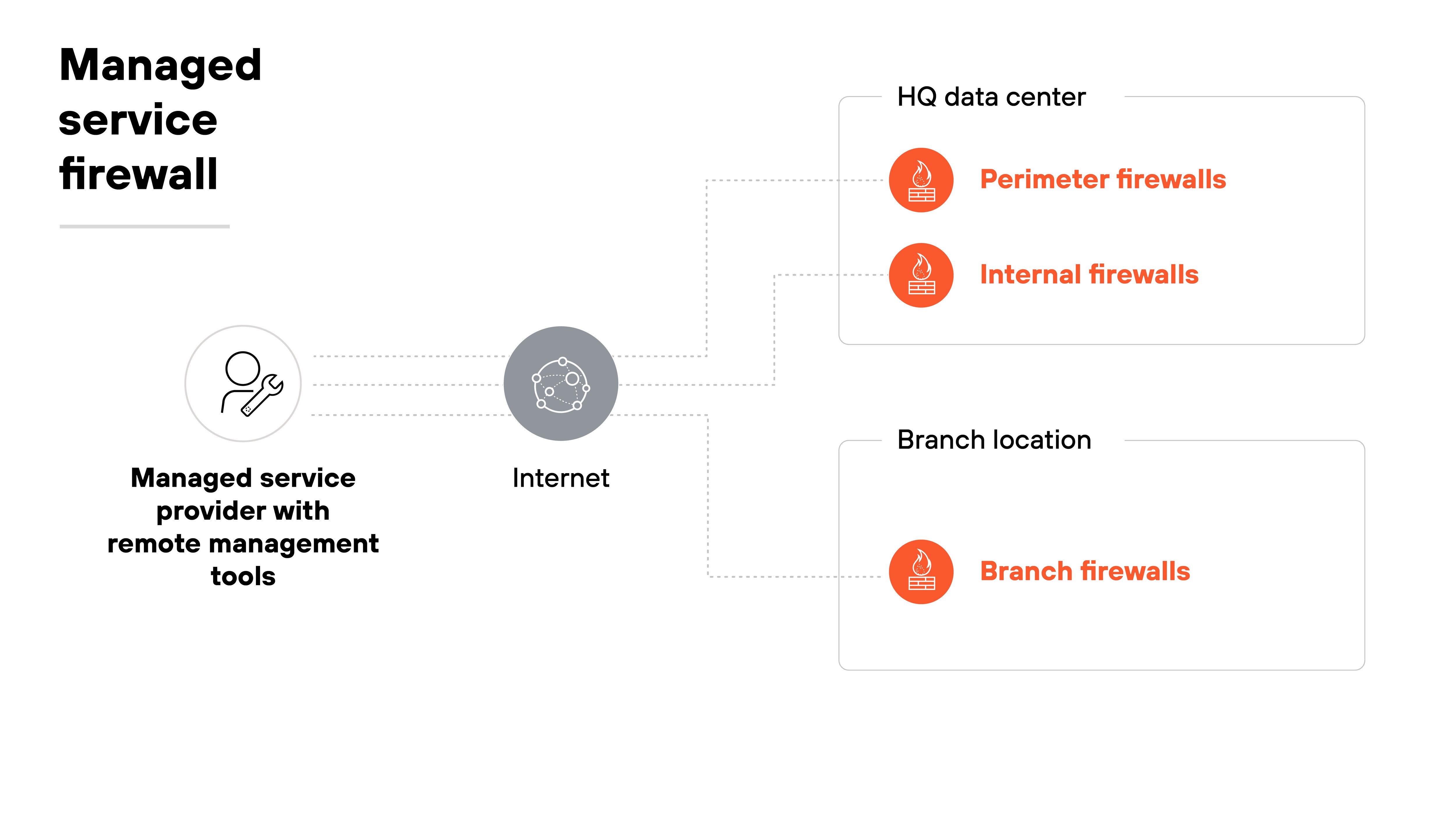
A managed service firewall is a software firewall that's delivered and operated by a third-party provider. The provider hosts the software, maintains it, and handles ongoing updates.
This model reduces operational overhead for the customer. Policies can still be defined and applied centrally, but the provider manages the infrastructure behind them. This way, software firewalls can be scaled up or down on demand and enforced consistently across environments without day-to-day upkeep.
For organizations that want coverage in virtual or cloud environments without direct management, this approach offers a practical alternative.
Where are software firewalls deployed?
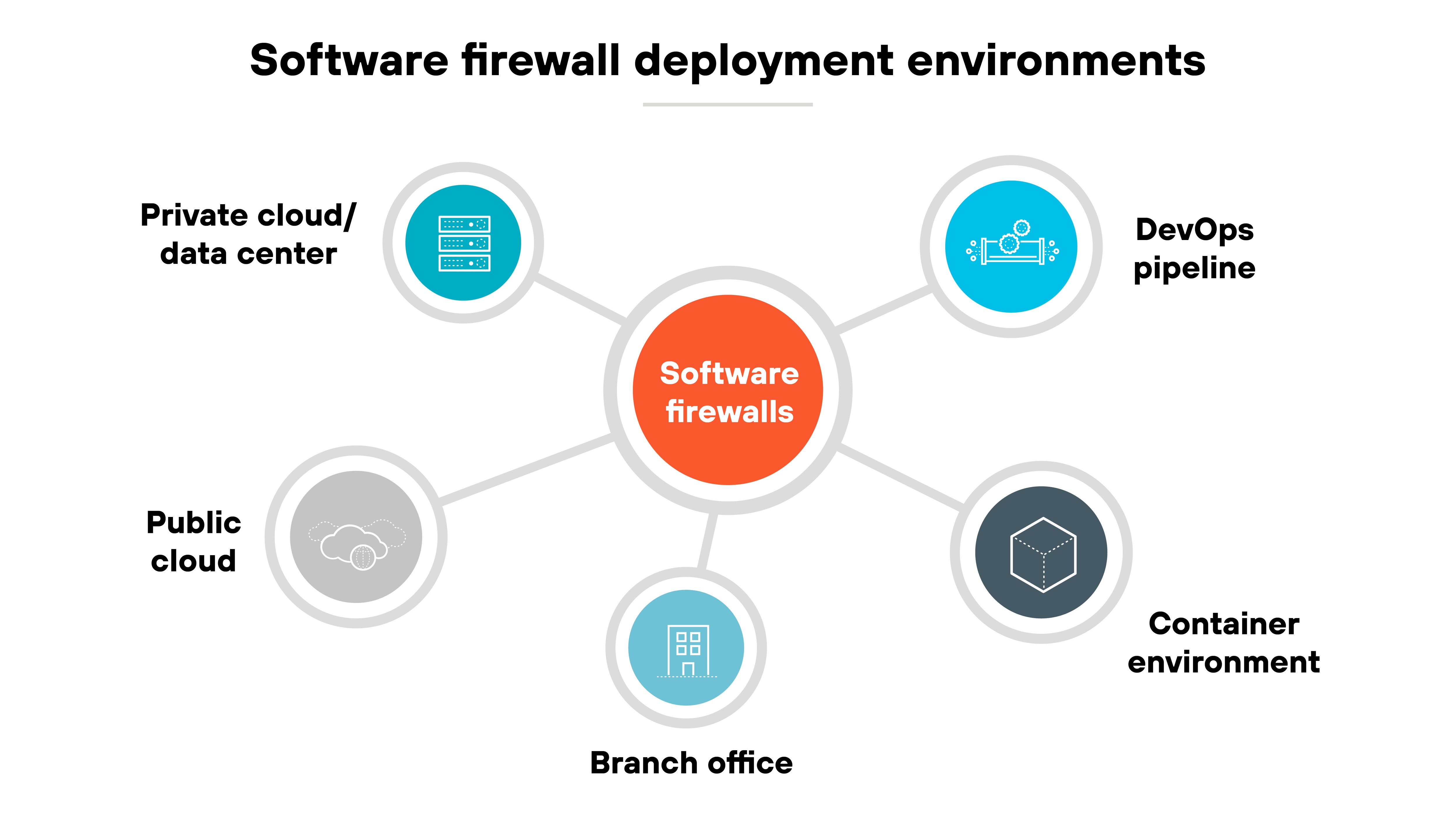
Software firewalls can be placed in several environments, including:
- Public cloud
- Private cloud and data centers
- Branch offices
- Container environments
- DevOps pipelines
Their value comes from extending firewall controls into areas where hardware appliances cannot be installed.
Public cloud
In public clouds, software firewalls run as virtual instances. They monitor north-south traffic moving in and out of cloud workloads.
They also secure east-west traffic between applications inside the cloud. This adds enforcement beyond the native controls offered by providers and helps maintain consistent policy across multi-cloud deployments.
Private cloud and data centers
In private clouds or virtualized data centers, software firewalls protect workloads hosted on shared infrastructure. They can inspect traffic between virtual machines.
They also support microsegmentation, which reduces the attack surface by limiting unnecessary connections within the environment.
Branch offices
Branches often lack the space or resources to host dedicated appliances.
Software firewalls can run on existing servers or white-box hardware. This allows segmentation and threat prevention without deploying a separate physical device at each site.
Container environments
Containerized applications need protection at the orchestration layer. Software firewalls integrate with platforms like Kubernetes.
They enforce policies on communication between services and monitor traffic in highly dynamic, short-lived workloads.
DevOps pipelines
Some deployments use software firewalls that scale on demand.
They integrate into DevOps workflows so policies can be applied without slowing releases. This ensures security keeps pace with rapid deployment cycles.
What is the difference between a software and hardware firewall?
The distinction between software and hardware firewalls comes down to form factor and deployment.
| Software firewalls vs. hardware firewalls |
|---|
| Parameters | Software firewall | Hardware firewall |
|---|---|---|
| Form factors | Software |
Physical device |
| Installation & operation |
|
Installed between network elements and connected devices |
| Deployment options | Cloud, Container, Virtual, NGFW |
NGFW |
| Complexity |
|
|
A hardware firewall is a physical device. It sits between network elements and connected devices. It often anchors the edge of a data center or office network.
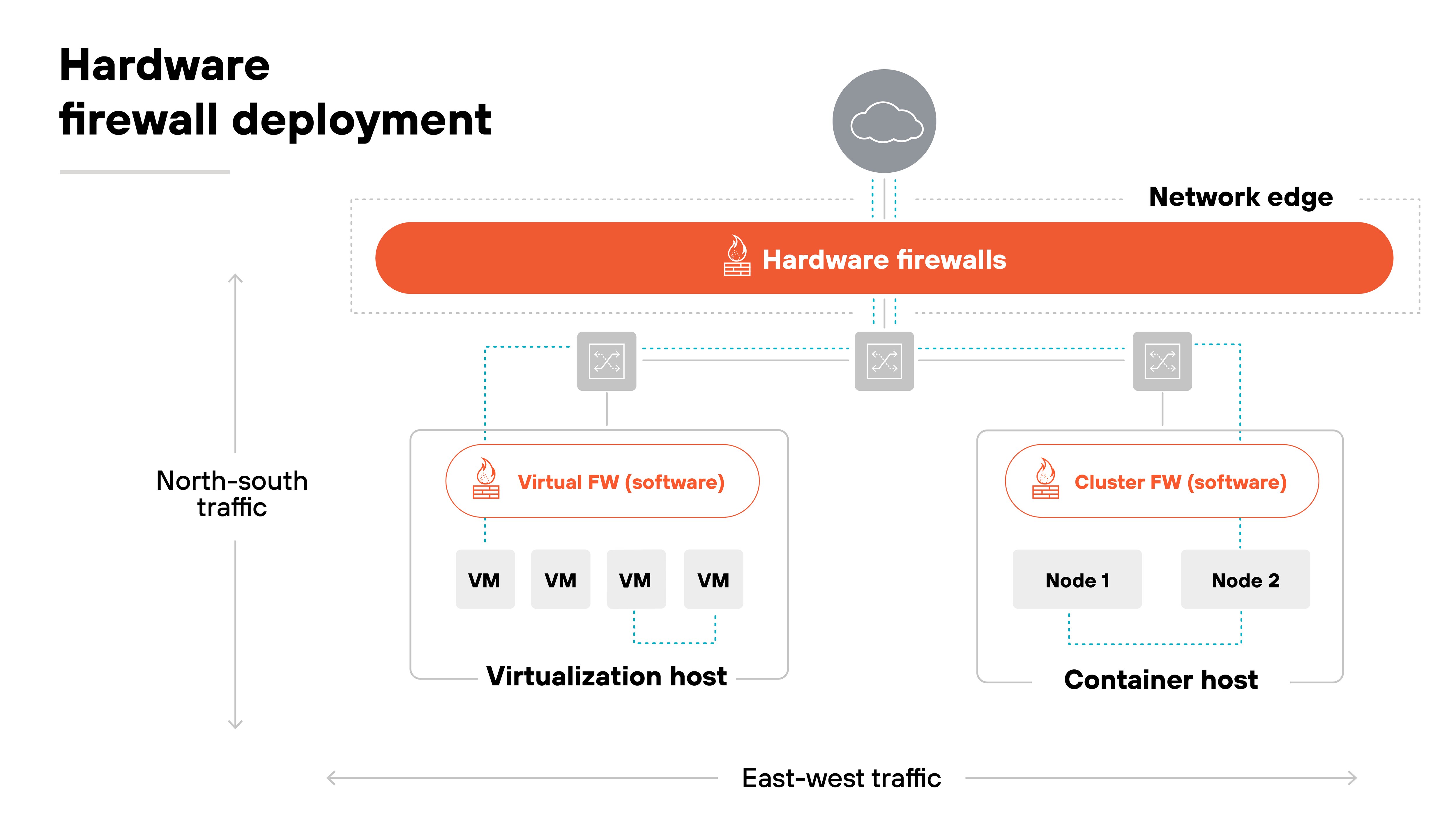
A software firewall is delivered in software form. It runs on a server, virtual machine, or cloud instance.
Deployment is another distinction. Hardware firewalls require physical setup. That means racking equipment, connecting cables, and configuring through dedicated interfaces. Skilled staff are usually needed to install and manage them.
Software firewalls, on the other hand, can be deployed using automation tools. They can scale on demand and be managed centrally through policy. Which makes them practical in hybrid and multi-cloud networks where agility is important. It's worth noting, though, that while they can be deployed faster than hardware appliances, they still require expertise for policy design and orchestration.
Basically: Hardware firewalls secure physical network boundaries. Software firewalls extend the same protections into virtual, cloud, and distributed environments. Both are complementary. Neither replaces the other.
How software firewalls help achieve a Zero Trust strategy
As discussed, traditional firewalls were built to guard the perimeter, but today's environments don't have a single, fixed boundary. Applications and workloads run across clouds, containers, and distributed infrastructure.
Zero Trust emerged as a response to that shift, assuming no user, device, or workload is trusted by default. Every connection must be verified, and access should be limited to only what is required.
Here's where software firewalls come in.
In Zero Trust terms, they provide enforcement points inside environments that hardware cannot reach. They also evaluate requests against defined access rules before allowing traffic to pass. And extend Zero Trust from the edge of the network to the workloads and applications themselves.
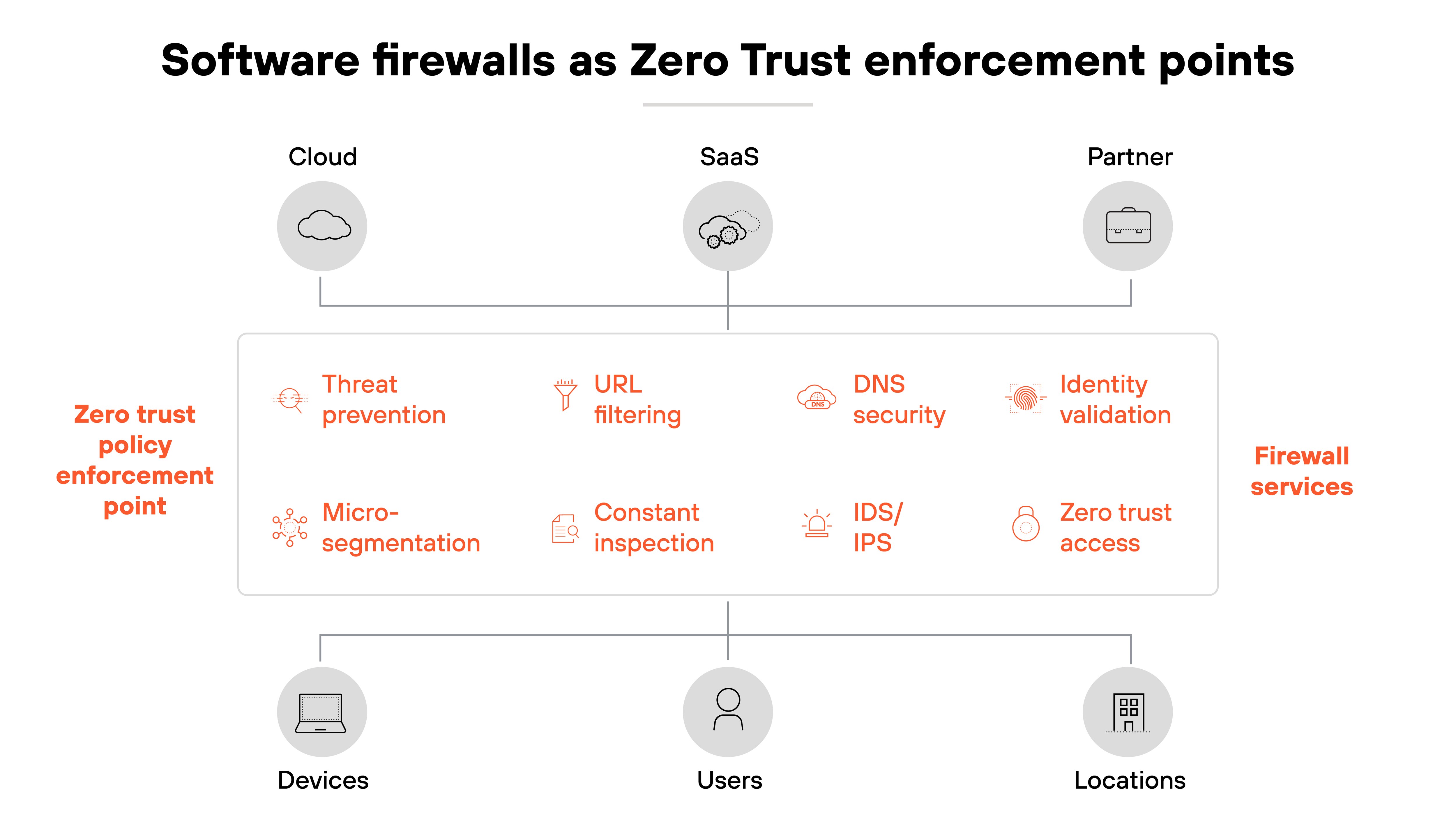
For example: A software firewall can be placed between application tiers in a cloud. It can require explicit policy before one service communicates with another. That reduces the risk of lateral movement if an attacker gains a foothold.
Microsegmentation is a core part of Zero Trust. Software firewalls make it possible to segment workloads at a granular level.
So, a database can be limited to a single application. A containerized service can be isolated from others unless policy allows communication. This supports least-privilege access. Each segment can be restricted based on sensitivity, function, or compliance needs, reducing the blast radius of an attack.
Centralized management also supports Zero Trust. Policies can be defined once and enforced consistently across cloud, virtual, and container environments. That means authentication and access controls remain uniform, even when resources are distributed.
Important: Software firewalls are not a complete Zero Trust solution. They don't replace identity, device, or data controls.
They do, however, give the network layer the enforcement capability Zero Trust requires. And they're a practical enforcement mechanism. They turn Zero Trust principles into real-world controls by verifying every connection and restricting access to the minimum needed.
