- What Is the Difference Between Advanced Endpoint Security and Antivirus (AV)?
-
What is Endpoint Security Awareness Training?
- Understanding Security Awareness Training
- Endpoint Security Awareness Training Explained
- What Does Endpoint Security Awareness Training Cover?
- Why Is Security Awareness Training Important?
- How to Build an Effective Endpoint Security Awareness Training Program
- Industry Awareness Training Case Studies and Success Stories
- The Future of Endpoint Security Awareness Training
- Endpoint Security Awareness Training FAQs
- What Is Endpoint Detection?
-
What Is Endpoint Security Software? How It Stops Cyberattacks
- Endpoint Security Software Explained
- Endpoint Security Software vs. Antivirus
- Core Components of Comprehensive Endpoint Security Software
- How Does Endpoint Security Software Protect a Network?
- What are the Key Features of Endpoint Security Software?
- EPP vs. EDR vs. XDR
- The Role of Threat Hunting in Endpoint Security
- Implementation Strategies for Enterprise Environments
- Defending Against Ransomware: A Use Case
- Endpoint Security Software FAQs
- What Is an Endpoint? Understand Devices, Risks & Security
-
What Is an Endpoint Protection Platform?
- Understanding Endpoint Protection Platforms (EPPs)
- The Importance of Endpoint Protection for Enterprises
- What Cybersecurity Practitioners and CISOs Need to Know About EPPs
- Traditional vs. Cloud Native EPPs
- EPP vs EDR: A Comparative Analysis
- Case Studies: Real-World Applications
- How to Choose the Best EPP
- Endpoint Protection Platform (EPP) FAQs
- What are the Types of Endpoint Security?
- What Is Next-Generation Antivirus (NGAV)
-
What Is Endpoint Security Antivirus?
- Endpoint Security Antivirus Explained
- Understanding Endpoints in Cybersecurity
- Why Endpoint Security Antivirus is Crucial for Modern Cybersecurity
- Endpoint Antivirus vs. Endpoint Security: What Is the Difference?
- Key Components of a Comprehensive Endpoint Security Solution
- How Endpoint Security Antivirus Works
- Implementing and Optimizing Endpoint Security Antivirus
- Choosing the Right Endpoint Security Antivirus Solution
- Challenges and Future Trends in Endpoint Security
- Endpoint Security Antivirus FAQs
What Is Endpoint Security?
Endpoint security is a cybersecurity approach to protecting end-user devices—such as laptops, servers, and mobile devices—from cyberthreats and malicious activity. As remote work and cloud adoption expand the digital attack surface, endpoints have become the primary entry point for threat actors.
A modern Endpoint Protection Platform (EPP) moves beyond traditional antivirus by integrating AI-powered analytics and continuous monitoring to stop attacks before damage occurs. This defense is crucial: Unit 42 data shows that endpoints are the main target in 72% of incidents, often serving as the launchpad for multi-front attacks that exploit both.
Key Points
-
Endpoints are primary targets and entry points for 72% of cyber attacks. -
Modern protection relies on AI and behavioral analytics (NGAV) rather than static signatures. -
A full-spectrum defense combines prevention (EPP), detection/response (EDR), and integrated visibility (XDR). -
Zero Trust is enforced at the endpoint, continuously verifying device posture and limiting lateral movement. -
Unified visibility and management are essential for securing remote workers and hybrid cloud environments.
Key Data: Fronts of Attacks
A single compromised device without comprehensive protection can serve as a launchpad for ransomware, data exfiltration, and privilege escalation. This risk is underscored by the attack front data below, which indicates where threat actors concentrate their operations.
Key Data: Fronts of Attacks
Fronts of Attacks |
Percentage of Cases (Unit 42 2024) |
|---|---|
Endpoints |
72% |
Human |
65% |
Identity |
63% |
Network |
58% |
28% |
|
Cloud |
27% |
Application |
21% |
SecOps |
14% |
Database |
1% |
Why Endpoint Security Is Mandatory
For CISOs and IT leaders, a comprehensive endpoint strategy is a mandatory control that directly manages organizational risk and maintains operational resilience:
- Stops Multi-Front Incidents: Over 70% of incidents tracked by Unit 42 span three or more fronts (endpoints, cloud, identity). Modern Extended Detection and Response (XDR) is required to gain the unified visibility needed to stop these chained attacks.
- Defeats Evolving Threats: Modern protection relies on AI to combat polymorphic, fileless, and zero-day attacks that bypass static, signature-only solutions.
- Ensures Compliance: Strong endpoint controls, especially regarding data access and logging, are foundational for meeting key data protection regulations, including GDPR and HIPAA.
- Guarantees Continuity: By minimizing incident scope, impact, and downtime, high-efficacy endpoint security protects against massive financial losses and reputational damage.
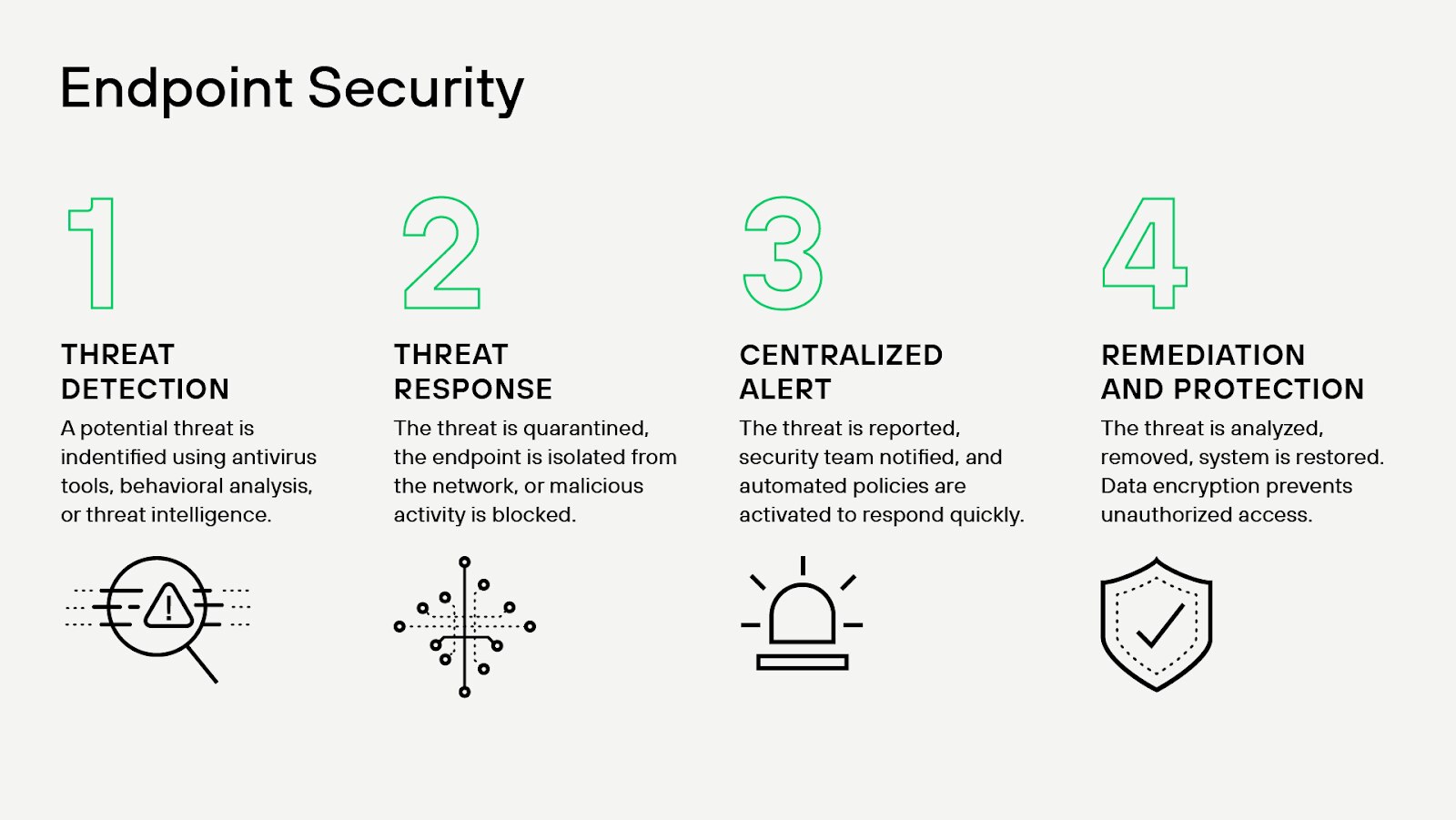
Figure 1: Endpoint Security Lifecycle at a Glance
How Does Endpoint Security Work?
Endpoint security extends protection beyond the network perimeter to every device that connects to the organization’s systems.

Figure 2: A centralized management console is installed on a network server or in the cloud, and client software is installed on each endpoint device.
Unified Platform and Centralized Protection
Modern endpoint security solutions operate on a client–server model designed to streamline management and protection across an organization’s network.
A centralized management console, typically hosted on a network server or in the cloud, serves as the command center. From this console, administrators can monitor, manage, and enforce security policies for every connected endpoint device, including laptops, mobile devices, and servers.
Each endpoint runs a lightweight client agent that communicates with the console, sharing telemetry data and receiving updates or threat intelligence in real time. This centralized approach enables unified visibility, faster response times, and consistent security coverage across the enterprise.
Advanced Detection and Automated Response
Modern endpoint protection platforms integrate advanced detection and automated response capabilities to counter increasingly sophisticated attacks. These systems perform the following functions continuously:
- Monitor endpoint behavior
- Analyze data for anomalies
- Automatically respond to suspicious activity, often before human intervention is needed.
By combining machine learning, behavioral analytics, and threat intelligence, endpoint solutions can detect and neutralize fileless malware, ransomware, and zero-day exploits that might otherwise evade conventional defenses. This proactive, adaptive defense strategy transforms endpoint security from a reactive safeguard into an intelligent, predictive protection layer for the entire organization.
Types of Endpoint Security: A Multi-Layered Approach
A multi-layered endpoint defense relies on several complementary technologies that work together to detect, prevent, and respond to cyberthreats. Below are the most common types of endpoint security used by enterprises today.
Comparison of Endpoint Security Types
Type |
Primary Function |
Detection / Protection Method |
Example Technologies or Tools |
|---|---|---|---|
Endpoint Protection Platform (EPP) |
Baseline defense against common threats like malware and phishing |
Signature-based scanning, firewall, encryption, and policy enforcement |
Palo Alto Networks Cortex XDR |
Endpoint Detection and Response (EDR) |
Continuous monitoring, detection, and response to active threats |
Behavioral analytics, telemetry collection, and real time investigation |
Palo Alto Networks Cortex XDR (EDR capabilities) |
Extended Detection and Response (XDR) |
Correlates and automates responses across multiple security layers |
Unified data from endpoints, network, cloud, and identity systems |
Palo Alto Networks Cortex XDR; XSIAM (AI-Driven SOC Platform) |
Next-Generation Antivirus (NGAV) |
Blocks advanced and unknown malware using AI and behavior analysis |
Machine learning, heuristic analysis, behavioral modeling |
Palo Alto Networks Cortex XDR (NGAV engine) |
Device Control & Data Loss Prevention (DLP) |
Prevents data leaks and unauthorized device use |
Endpoint monitoring, data classification, and policy-based restrictions |
Enterprise DLP integrated with Cortex XDR and Prisma Access |
Patch Management & Vulnerability Assessment |
Reduces exposure by fixing known vulnerabilities |
Automated patch deployment, vulnerability scanning |
Cortex Xpanse (Attack Surface Management)+ Prisma Cloud (Workload Protection) |
Mobile Device Management (MDM) / Unified Endpoint Management (UEM) |
Manages and secures mobile, remote, and BYOD endpoints |
Policy enforcement, remote wipe, app, and identity management |
Palo Alto Networks GlobalProtect (VPN & ZTNA) + Strata Cloud Manager |
Endpoint Protection Platforms (EPPs)
EPP solutions provide a baseline defense against known threats such as malware, phishing, and ransomware.
They typically include antivirus, firewall, and encryption capabilities — all managed through a centralized console. EPP acts as the first line of defense, blocking threats before they can compromise devices.
Core EPP features typically include:
- Next-generation antivirus (NGAV)
- Host-based firewalls and intrusion prevention
- Device and application control
- Disk encryption and data loss prevention (DLP)
- Patch management and vulnerability scanning
- Centralized policy management
Endpoint Detection and Response (EDR)
EDR goes beyond prevention by providing continuous monitoring and threat-hunting capabilities. It records and analyzes endpoint activity to detect anomalies, suspicious behaviors, or lateral movement attempts.
When a threat is detected, EDR enables rapid isolation, investigation, and remediation (automated isolation and containment of infected endpoints) — often in real time. EDR shifts organizations from reactive cleanup to proactive detection and response.
Extended Detection and Response (XDR)
XDR extends the EDR concept by integrating data from multiple security layers — including network, email, cloud, and identity systems. This cross-domain visibility improves threat correlation and enables automated, coordinated responses across the environment. XDR helps security teams reduce alert fatigue and uncover advanced threats that span beyond endpoints.
Next-Generation Antivirus (NGAV)
NGAV uses machine learning and behavioral analytics to identify never-before-seen threats, rather than relying solely on signature-based detection. It can detect zero-day exploits, fileless malware, and polymorphic attacks, making it more effective than legacy antivirus solutions. NGAV serves as a critical layer of prevention in modern endpoint architectures.
Device Control and Data Loss Prevention (DLP)
These technologies protect against insider threats and data exfiltration. Device control regulates the use of removable media and peripheral connections, while DLP monitors and restricts the movement of sensitive data. Together, they help ensure data integrity and compliance across distributed devices.
Patch Management and Vulnerability Assessment
These tools ensure endpoints remain secure by identifying and remediating software vulnerabilities before attackers exploit them. Automated patch deployment helps maintain compliance, reduce manual workload, and close security gaps in real time.
Mobile Device Management (MDM) and Unified Endpoint Management (UEM)
MDM and UEM solutions give administrators control over mobile and hybrid endpoints, enforcing policies and securing devices used in BYOD and remote work environments. UEM unifies control of laptops, smartphones, tablets, and IoT devices within a single platform.
In combination, these technologies create a defense-in-depth model that protects endpoints across all phases of an attack — from initial compromise to post-incident recovery. A layered approach ensures that if one control fails, another is ready to detect, block, or remediate the threat.
Traditional Antivirus vs. Modern Endpoint Security
One of the most common points of confusion in cybersecurity is the distinction between traditional antivirus software and modern endpoint security platforms. While both aim to protect devices from threats, their methods, scope, and sophistication differ significantly.
Traditional antivirus software relies primarily on signature-based detection — it compares files and programs against a database of known malware. While effective at identifying previously cataloged threats, this approach fails to detect new, unknown, or zero-day attacks that lack a signature.
The table below shows the key differences between traditional antivirus and modern endpoint security in scope, capability, and response maturity:
Comparison of Traditional Antivirus vs. Modern Endpoint Security
Feature |
Traditional Antivirus |
Modern Endpoint Security |
Threat Protection |
Detects and removes known malware based on stored signatures. |
Identifies and neutralizes known, unknown, and fileless threats using AI, analytics, and threat intelligence. |
Coverage |
Protects individual devices only. |
Secures the entire network of endpoints, including laptops, servers, and cloud workloads. |
Workflow |
Reactive: Scans for infections and removes them after compromise. |
Proactive: Continuously monitors, detects, and responds to suspicious activity in real time. |
Modern endpoint protection software, on the other hand, uses a multi-layered defense model that combines traditional signature detection with behavioral analytics, machine learning, and integrated threat intelligence. This allows it to recognize suspicious patterns, detect fileless malware, and automatically respond to advanced threats in real time.
Implementing Zero Trust for Endpoint Security
Zero Trust is a foundational security concept that operates on the principle: "never trust, always verify." For endpoints, this means no device, user, or application is inherently trusted, regardless of its location or network segment. Every connection and resource request must be explicitly authorized.

Figure 3: Integrated Security Platform with Zero Trust Endpoint Security
Applying Zero Trust principles to endpoints involves granular access control and continuous verification of device posture, user identity, and application health. This model significantly limits an attacker’s ability to move laterally across the network, even if they compromise a single endpoint. It strengthens the security boundary around every user and device.
Leading from the Front: Palo Alto Networks XDR/ZTNA 2.0 vs. Legacy EDR
Feature |
Legacy EDR/AV |
Palo Alto Networks XDR/ZTNA 2.0 |
|---|---|---|
Scope of Data |
Endpoint Telemetry Only |
Endpoint, Network, Cloud, Identity |
Primary Goal |
Detect and Respond on the Endpoint |
Detect, Respond, and Prevent Across Domains |
Response |
Manual or Semi-Automated |
Automated Cross-Domain Remediation |
Access Model |
Perimeter/VPN-Centric |
ZTNA 2.0 (Zero Trust) |
Intelligence |
Primarily Signature/IOC-Based |
Elite Unit 42 Adversary Intelligence |
Other Key Components
A complete endpoint security strategy combines multiple technologies to prevent, detect, and respond to threats. In addition to EPP, EDR, and XDR, several other essential components reinforce device-level and network-wide protection.
- Firewalls: Firewalls act as a first line of defense by controlling incoming and outgoing network traffic at the device level. They block unauthorized access, enforce security policies, and monitor network activity for suspicious connections.
- Data Loss Prevention (DLP): DLP solutions prevent the unauthorized transfer, sharing, or leakage of sensitive data. They monitor data in motion, at rest, and in use, ensuring compliance with organizational and regulatory data protection standards.
- Application Control: This feature uses whitelisting and blacklisting to manage which applications can execute on an endpoint. By allowing only trusted applications, it helps reduce the attack surface and prevents malicious or unapproved software from running.
- Vulnerability Management: Vulnerability management tools identify, assess, and prioritize software weaknesses that attackers could exploit. Regular scanning and patch deployment ensure endpoints remain secure and compliant with security policies.
- Endpoint Encryption: Encryption protects data at rest by converting it into an unreadable format. If a device is lost or stolen, encryption ensures sensitive information remains inaccessible without proper authentication.
Selecting the Optimal Endpoint Security Solution
Choosing the right endpoint security solution is one of the most critical decisions an organization can make. The ideal platform depends on your organization’s size, industry, risk profile, and available resources.
Because not all solutions offer the same depth of protection or scalability, selecting the right one requires a careful assessment of both current needs and future growth. To simplify this process, organizations can use the following framework when evaluating potential solutions:
Industry & Compliance
Every industry faces unique regulatory and threat landscapes. For example, healthcare organizations must comply with HIPAA, while financial institutions must comply with PCI DSS or SOX. The right endpoint security platform should include built-in compliance reporting, audit-readiness, and policy-enforcement capabilities that align with your sector’s specific standards.
Data Sensitivity
The type and value of the data your organization handles directly impact the level of security required. Highly confidential or regulated data, such as customer PII, intellectual property, or trade secrets, demands solutions with advanced data loss prevention (DLP), encryption, and zero-trust access controls to protect information both in transit and at rest.
Budget & Resources
Endpoint security should deliver strong protection without overextending internal resources. Evaluate the total cost of ownership (TCO), including licensing, deployment, maintenance, and staffing. A cloud-delivered or managed solution can reduce operational overhead and provide enterprise-grade defense without requiring large in-house teams.
Layered Defense
No single technology can protect against every threat. A comprehensive strategy typically combines multiple security layers — for instance, EPP for prevention and EDR for detection and response — to deliver defense-in-depth. The most mature organizations extend this approach through XDR or SIEM integrations, achieving unified visibility and faster incident response across all endpoints and environments.
When these factors are evaluated together, they guide decision-makers toward a solution that balances security efficacy, compliance, cost, and scalability — ensuring the chosen endpoint protection strategy fits the organization’s risk profile and operational capacity.
Strategic Endpoint Security: Challenges and Best Practices
Implementing and managing endpoint security presents significant challenges across both large enterprises and small-to-midsize businesses (SMBs). Security leaders must navigate complexity, operational overhead, and a rapidly expanding attack surface to maintain a strong security posture. A strategic approach is required to overcome these hurdles.
Key Security Challenges for Enterprise and SMBs
- Alert Fatigue and False Positives: Security analysts are constantly overwhelmed by a high volume of low-fidelity alerts, making it easy to miss genuine, critical threats. This leads to burnout and reduced efficiency.
- Asset Sprawl and Shadow IT: The proliferation of personal and company-owned devices, combined with unauthorized software (Shadow IT), creates massive visibility gaps. CISOs cannot protect what they cannot see.
- Talent Gap and Operational Overhead: SMBs often lack the specialized staff required to effectively manage complex EDR/XDR platforms or perform continuous threat hunting. This leaves expensive, advanced tools underutilized.
- BYOD and Remote Workforce Risk: Devices connecting from outside the corporate network are not protected by traditional perimeter defenses. Enforcing consistent security policies on these devices remains a significant hurdle.
Essential Endpoint Security Best Practices Checklist
Security teams can maximize their endpoint protection effectiveness by focusing on these key, actionable strategies:
- Consolidate Tools: Adopt a unified EDR or XDR platform to reduce complexity and improve threat correlation across the environment.
- Enable Automated Response: Configure the security platform to automatically isolate compromised endpoints and terminate malicious processes without requiring manual intervention.
- Prioritize Patch Management: Maintain a rigorous patching schedule for operating systems and third-party applications to eliminate known vulnerabilities before they are exploited.
- Implement Least Privilege: Restrict user and process permissions to the minimum level necessary for their function, significantly limiting the damage an attacker can inflict.
- Conduct Regular Audits: Routinely audit endpoint configurations and security policies to ensure compliance and identify overlooked devices or security holes.
- Integrate Threat Intelligence: Feed up-to-date, relevant threat intelligence into the endpoint security solution to proactively identify and block emerging campaigns.
Endpoint Security FAQs
Key metrics include:
- Detection and response time (MTTD/MTTR)
- Number of blocked or contained incidents
- Patch compliance rate
- Endpoint visibility coverage (% of managed devices)
- Reduction in manual investigation workload
Tracking these metrics through a centralized SOC or XDR console demonstrates whether endpoint controls are actually improving resilience.
