-
What Is Endpoint Detection and Response (EDR)?
- Understanding EDR
- Key Benefits of EDR Solutions
- How EDR Works: A Detailed Breakdown
- Evolution of EDR
- EDR Implementation Process
- Common Challenges and Solutions in EDR Adoption
- Advanced EDR Strategies and Optimization Techniques
- EDR and the Evolving Threat Landscape
- How to Evaluate an EDR Solution
- EDR FAQs
- What Is Endpoint Detection and Response (EDR) Deployment?
- What is EDR-as-a-Service Managed Security?
- What Are Endpoint Detection and Response Tools?
- What is EDR vs. Antivirus?
- How Does EDR Enhance Small Business Cybersecurity?
- How Does EDR Leverage Machine Learning?
- What Is Endpoint Detection and Response (EDR) Compliance?
- What is the Difference Between EDR vs. SIEM?
- What is EDR vs. XDR?
What Is Endpoint Detection and Response (EDR) Management?
EDR management involves overseeing endpoint detection and response solutions, which continuously monitor and analyze endpoint activity to detect, investigate, and respond to advanced threats. This process ensures organizations can effectively protect their digital assets from evolving cyberattacks.
Key aspects of managed EDR include:
- 24/7 Monitoring
- Advanced Threat Detection
- Threat Hunting
- Incident Investigation and Response
- Reduced Alert Fatigue
- Access to Expertise
- Improved Security Posture
Key Points
-
EDR management involves the continuous oversight of endpoint detection and response solutions to ensure optimal threat detection. -
Effective EDR management identifies anomalous activities and automates incident responses, thereby minimizing the impact of breaches. -
Optimizing EDR configurations and policies enhances an organization’s proactive defense against evolving cyber threats. -
EDR management involves integrating threat intelligence and automating workflows to improve the security operations center's efficiency. -
Regular review and tuning of EDR systems ensure they adapt to new attack techniques and maintain robust endpoint security.
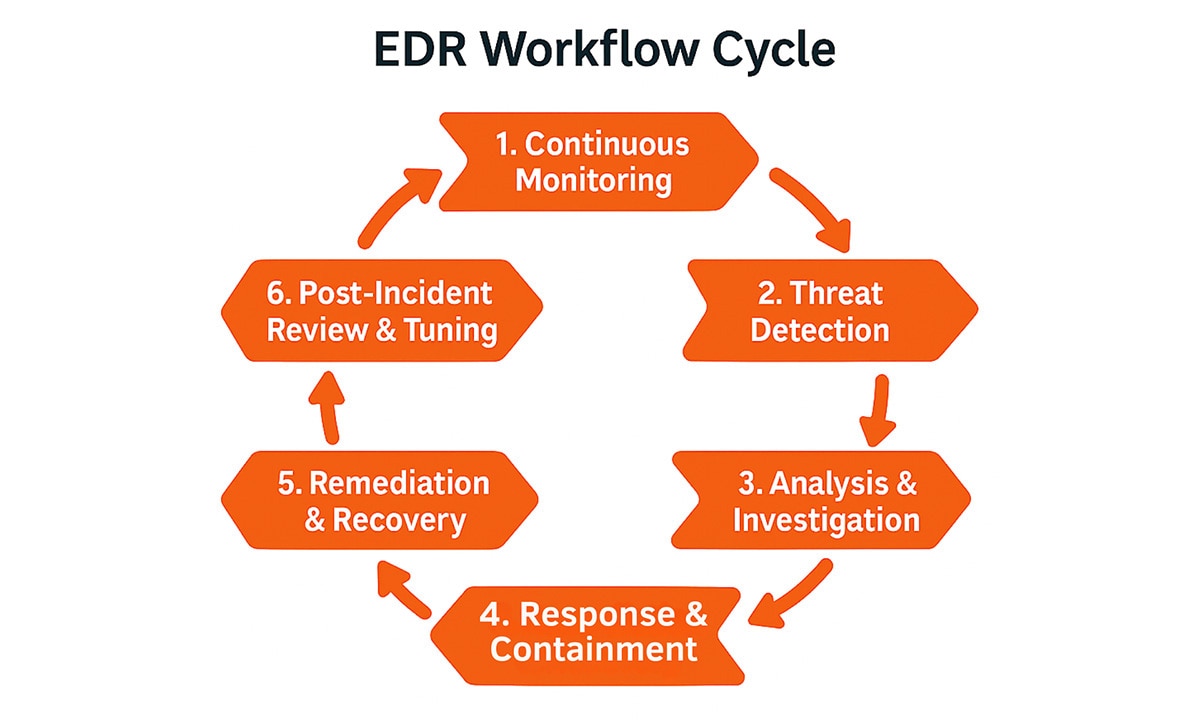
EDR Management Explained
EDR management extends beyond simply deploying an EDR solution; it encompasses the ongoing operational oversight and strategic optimization necessary to enhance an EDR's threat detection and response capabilities.
The cybersecurity landscape has become increasingly alarming, with threat actors escalating both the frequency and sophistication of their attacks. IBM's 2024 Cost of a Data Breach Report reveals that the global average cost of a data breach reached $4.88 million in 2024, representing a 10% increase from the prior year and the most significant yearly jump since the onset of the pandemic.
This surge is primarily driven by business disruption costs and post-breach response activities, with 70% of breached organizations reporting that the breach caused significant or very significant disruption.
Effective EDR management is essential for modern cybersecurity because endpoints—laptops, servers, mobile devices—remain primary targets for sophisticated attacks, ranging from ransomware to advanced persistent threats.
By proactively managing EDR systems, security teams can quickly identify unusual behaviors, comprehend attack paths, and automate or coordinate rapid responses, reducing dwell time and potential damage. This critical practice connects raw security data with actionable cyberthreat intelligence, transforming endpoint telemetry into a comprehensive defensive strategy.
Key Capabilities of EDR Management
Effective EDR management leverages a suite of capabilities to deliver resilient endpoint protection, moving beyond traditional antivirus solutions. These functions collectively enable deep visibility, rapid threat identification, and automated response across an organization's endpoints.
Continuous Endpoint Monitoring and Data Collection
EDR solutions deploy lightweight agents to endpoints, continuously collecting vast amounts of telemetry data, including process execution, file system changes, network connections, and user activities. This granular data provides a comprehensive historical record of endpoint behavior.
Advanced Threat Detection
Sophisticated analytics and machine learning algorithms analyze the collected data in real time, identifying patterns and behaviors indicative of both known and unknown threats. This includes behavioral analysis, anomaly detection, and correlation of events across multiple endpoints.
Incident Investigation and Forensics
EDR tools provide security teams with rich contextual information and forensic capabilities, enabling them to investigate detected incidents thoroughly. This includes visualizing attack paths, understanding root causes, and performing retrospective analysis to uncover hidden threats.
Automated Response and Remediation
Upon detection of a threat, EDR systems can automatically initiate predefined response actions, such as isolating affected endpoints, terminating malicious processes, or quarantining suspicious files. This rapid automation significantly reduces dwell time and limits the spread of an attack.
Threat Hunting
EDR empowers security analysts to search for threats that may have evaded automated defenses proactively. By providing access to comprehensive endpoint data and powerful querying tools, threat hunters can uncover stealthy attacks and emerging threats before they cause significant damage.
The Crucial Role of EDR Management in Modern Cybersecurity
EDR management is no longer optional in today's threat landscape; it's a fundamental pillar of a resilient cybersecurity strategy. Its importance stems from the evolving nature of cyber attacks and the limitations of traditional security measures.
Adapting to Evolving Threat Landscapes
Traditional signature-based antivirus solutions often fall short against polymorphic malware, fileless attacks, and zero-day exploits. Managed EDR, with its behavioral analysis and machine learning capabilities, offers a dynamic defense that can detect novel attack techniques.
Bridging Gaps in Security Posture
Many organizations face blind spots, especially with the proliferation of remote work and diverse endpoint devices. EDR management offers comprehensive visibility across all endpoints, illuminating previously unseen activities and vulnerabilities.
Enhancing Incident Response Efficiency
Manual incident response is time-consuming and prone to human error. EDR management streamlines the entire threat intelligence lifecycle—from detection and investigation to containment and remediation—by automating key tasks and providing actionable insights.
Reducing Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR)
By providing real-time alerts and automated responses, EDR management drastically reduces the time it takes to identify and neutralize threats. Faster response times directly translate to reduced financial losses and reputational damage from breaches.
EDR Management Challenges and Solutions
Despite its benefits, implementing and managing an EDR solution effectively presents several challenges. Addressing these proactively is essential for maximizing the return on investment and maintaining a strong security posture.
Alert Fatigue and False Positives
Many EDR systems generate a high volume of alerts, leading to alert fatigue for security teams and the risk of legitimate threats being overlooked.
- Solution: Continuously refine detection rules and machine learning models, implement strong alert prioritization, and integrate EDR with Security Orchestration, Automation, and Response (SOAR) platforms to automate initial triage.
Integration with Existing Security Infrastructure
Integrating EDR with Security Information and Event Management (SIEM), firewalls, and other security tools can be a complex process.
- Solution: Select EDR solutions that offer open APIs and strong integration capabilities. Develop clear integration strategies and leverage security frameworks, such as MITRE ATT&CK, for consistent data mapping and correlation.
Resource Requirements and Skill Gaps
Effective EDR management demands skilled security analysts for threat hunting, investigation, and policy tuning. Many organizations grapple with shortages in cybersecurity talent. More organizations faced significant staffing shortages compared to the previous year, reflecting a 26% increase.
They reported an average of $1.76 million in higher breach costs than those with low-level or no security staffing issues, according to the IBM Report: Escalating Data Breach Disruption Pushes Costs to New Highs. This shortage is particularly severe in specialized areas such as threat hunting, incident response, and advanced persistent threat (APT) analysis—core competencies essential for effective EDR management.
- Solution: Invest in training for existing staff, consider managed EDR (MDR) services from reputable providers, and leverage EDR solutions with intuitive interfaces and guided investigation workflows.
Performance Impact on Endpoints
EDR agents continuously monitor system activity, which can sometimes lead to performance degradation on endpoint devices.
- Solution: Select EDR solutions designed with lightweight agents and optimized resource consumption. Implement phased rollouts and rigorous testing to identify and mitigate performance issues before widespread deployment.
Continuous Tuning and Optimization
Threat actors continually evolve their tactics, techniques, and procedures (TTPs), necessitating the continuous update of EDR configurations and policies.
- Solution: Establish a regular review cycle for EDR policies, subscribe to reliable threat intelligence feeds, and leverage vendor updates and best practices to stay informed. Conduct periodic purple team exercises to test and fine-tune EDR effectiveness.
Best Practices for Effective EDR Management
Optimizing EDR management involves a combination of strategic planning, continuous improvement, and leveraging the full capabilities of the chosen solution.
Establish Clear Baselines and Policies
Define what constitutes "normal" behavior across your endpoints. Develop clear, granular policies for detection, alerting, and automated response based on your organization's risk tolerance and compliance requirements.
Leverage Threat Intelligence Feeds
Integrate reputable threat intelligence feeds with your EDR solution. This enriches your EDR's detection capabilities with real-time information on emerging threats, indicators of compromise (IOCs), and indicators of attack (IOAs).
Prioritize Alerts Based on Risk Context
Implement a system to prioritize EDR alerts by factoring in asset criticality, user privileges, and the severity of the detected activity. This helps security teams focus on the most impactful threats first.
Automate Repetitive Tasks
Utilize EDR's automation capabilities for tasks like initial containment, forensic data collection, and basic remediation. Integrate with SOAR platforms to orchestrate more complex response workflows.
Regular Threat Hunting
Go beyond automated alerts by conducting proactive threat hunting. Utilize the EDR's data and search capabilities to proactively identify subtle signs of compromise that might otherwise go undetected.
Conduct Regular Drills and Simulations
Conduct incident response drills and tabletop exercises that incorporate your EDR capabilities. This helps refine playbooks, identify gaps, and ensure your team is proficient in using the EDR solution during an actual incident.
Continuous Training for Security Teams
Ensure your security team receives ongoing training on the EDR solution, including its advanced features, threat hunting techniques, and forensic analysis capabilities. Stay current with new features and threat landscape shifts.
EDR vs. EPP: A Complementary Relationship
Understanding the distinction between EDR and EPP (Endpoint Protection Platform) is crucial, as they serve different, yet complementary, roles in a holistic endpoint security strategy. EDR management often involves the interplay between these two components.
Endpoint Protection Platform (EPP)
EPP focuses primarily on preventing known threats from reaching endpoints. It typically includes antivirus, anti-malware, firewall, and intrusion prevention system (IPS) functionalities. EPP uses signature-based detection and heuristic analysis to block threats before they can execute.
Endpoint Detection and Response (EDR)
EDR, on the other hand, focuses on detecting and responding to advanced and unknown threats that may bypass EPP defenses. It continuously monitors endpoint activity, collects telemetry data, and uses advanced analytics, machine learning, and behavioral analysis to identify suspicious activities post-execution.
The Synergy
An effective cybersecurity posture often involves deploying both EPP and EDR solutions. EPP acts as the first line of defense, preventing a vast majority of known threats. EDR then provides the deeper visibility and response capabilities necessary to catch sophisticated attacks that evade initial prevention, ensuring a more resilient defense-in-depth strategy. EDR management, in this context, involves optimizing the interaction and sharing of intelligence between these two layers.
Integrating EDR Management with a Broader Security Ecosystem
For maximum effectiveness, EDR management should not operate in a silo. Integrating EDR with other security tools creates a unified security posture, enhancing threat visibility and enabling faster response times.
EDR and SIEM Integration
Integrating EDR data with a SIEM system provides a centralized view of security events across the entire IT environment. EDR feeds rich endpoint telemetry to the SIEM, which can then correlate this data with logs from other sources—like firewalls, network devices, and applications—to identify complex attack chains. This correlation provides a broader context for security incidents, enhancing overall threat detection.
EDR and SOAR Integration
SOAR platforms automate and orchestrate security workflows. Integrating EDR with SOAR allows for automated responses to EDR-detected threats, such as automatically isolating an infected host, triggering playbooks for incident enrichment, or creating trouble tickets in a security ticketing system. This significantly reduces manual effort and speeds up response times.
EDR and Threat Intelligence Platforms
Directly integrating EDR with threat intelligence platforms (TIPs) enriches EDR's detection capabilities. EDR can ingest real time threat indicators (IOCs, IOAs) from TIPs, improving its ability to identify emerging threats and understand attacker TTPs. Conversely, EDR can provide valuable endpoint telemetry back to the TIP, contributing to the organization's unique threat intelligence.
EDR and Network Security
While EDR focuses on endpoints, integrating its insights with network security devices, such as next-generation firewalls (NGFWs), can provide a more comprehensive picture of an attack. For example, EDR might detect suspicious internal network activity, and the NGFW can then block related command-and-control traffic or isolate the compromised endpoint at the network level.
Case Study of a Successful EDR Implementation
Multiterminais is among the largest marine terminal and dry port operators in Brazil and a leader in integrated logistics. Millions of tons of freight—some vessels carry up to 24,000 containers—need to be loaded and unloaded around the clock. An operation of this size must be protected by a resilient, flexible, and cost-effective cybersecurity platform.
The Challenges
- Multiterminais’ port and logistics services need to operate threat-free 24/7/365 to ensure the smooth flow of goods and services into and out of South America.
- The company's existing siloed endpoint security system was draining performance and requiring regular intervention. A malware incident originating in one of the endpoints also resulted in a multiday system outage.
The Solution
The Results
By utilizing the Palo Alto Networks platform to secure data, people, and processes, Multiterminais ensures the continuous flow of container operations and trade across Brazil and worldwide.
The security operations center (SOC) now faces 80% fewer alerts, freeing the team to focus on strategic security issues. The mean time to detect (MTTD) has been reduced by 93% and the mean time to respond (MTTR) by 90%. The innovative Cortex XDR cybersecurity platform is transforming Multiterminais’ service reliability and agility with the following benefits:
- Uninterrupted shipping operations: By securing its data, people, and processes, Multiterminais ensures the continuous flow of container operations and trade across Brazil and worldwide.
- Reduced costs: 100% availability ensures 100% shipping operations, avoiding the cost of an outage (the team estimates that system downtime could cost the company “six figures per day”).
- Reduced volume of alerts: Using Cortex XDR, Multiterminais has reduced the volume of alerts by 80%. This frees the SOC team from repetitive, manual security operations to focus on strategic, added-value tasks.
- Increased security agility: Using the unified Palo Alto Networks platform, Multiterminais reduced their Mean Time To Detection (MTTD) from an average of 8 hours to 30 minutes (a 93% reduction). The MTTR dropped by 90%.
- Improved SOC productivity: The CIO explains, “Reducing the SOC workload in identifying and circumventing threats enables the team to work more on prevention. When an event is detected, more attention is given to resolving the event.”
