What is OT security?
OT security is the process of securing the practices and technologies deployed to monitor, detect, and control changes to operational technology infrastructure, people, and data.
What Is Operational Technology (OT)?
Operational technology (OT) refers to hardware and software systems that execute monitoring and/or control over industrial equipment and processes.
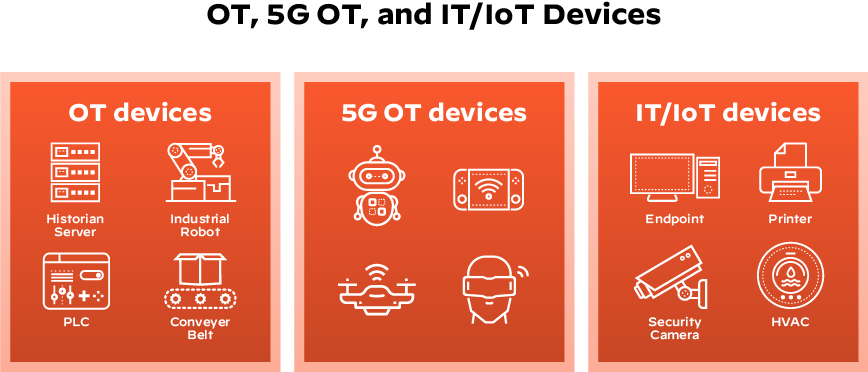
Such industrial processes and equipment include:
- Critical infrastructure
- Utilities
- Electric grids
- Manufacturing plants
- Traffic control systems
The umbrella term “operational technology” encompasses many specialized frameworks, such as:
- Process control domains
- Programmable logic controllers
- Physical access controls
- Distributed control systems
- Safety instrumented systems
- Transportation systems
- Supervisory control and data acquisition (SCADA) systems
- Building management/automation systems (often collectively referred to as Industrial Control Systems, or ICS)
IT vs. OT Security
While operational technology and information technology security share some similarities, OT has characteristics that distinguish it from traditional information processing systems.
OT’s direct impact on the physical world
Perhaps the most marked difference between IT and OT security is OT’s direct connection to the outside world. In other words, OT has the potential to impact the physical elements of society. Some of these potential impacts include:
- Disruption of production
- Public health and safety risks
- Environmental damage
- Financial problems
- Production losses
- Negative impacts to a nation’s economy
- Compromised proprietary information
Unique performance and reliability requirements
OT environments rely on applications and operating systems which could be unconventional to typical IT professionals.
Conflicting safety and efficiency vs. security goals
When it comes to the design and operation of OT systems, safety, and efficiency sometimes conflict with security.
The following table compares IT and OT systems requirements for connectivity and security:
| Connectivity Mechanisms | Via Telco, Wi-Fi | Via Telco, Radio, Satellite, Powerline Carrier, Wi-Fi |
| Security Priority | Data security with high confidentiality | Operational uptime with high availability, safety, and integrity |
| Security Standards | ISO-17799, 27001, NIST SP 800-53 | ISA99, NERC CIP 002-009, NIST SP 800-53, NIST SP 800-82 |
| Security Patching | Frequent | Slow to impossible |
| Cyber Forensics | Available | Limited, if any |
| Overall Impact from Security Breaches | Business impacts | Business impacts, process fluctuations, equipment damage, environmental release, personnel safety |
Convergence of IT and OT
Historically, IT and OT were managed by separate groups in an organization. IT and OT did not share interdependencies. However, in recent years, the paradigm has shifted.
Today, it’s common for OT systems to be provisioned with networking and computational technologies. The worlds of IT and OT are converging, which is laying the groundwork for the Industrial internet of things (IIoT).
Modern OT environments must facilitate the exchange of data between machines and applications. At the same time, OT environments need to be able to scale processes across physical and virtual systems. This is why OT systems are starting to resemble IT systems.
IIoT is set to play a key role in the fourth Industrial Revolution. Converged IT/OT ecosystems will serve as conduits that will deploy IIoT into the 4IR ecosystem
The integration promises numerous benefits:
- Improved flow of information
- Process automation
- Advances in the management of distributed operations
- Better adherence to regulatory compliance
Why Is OT Security Important?
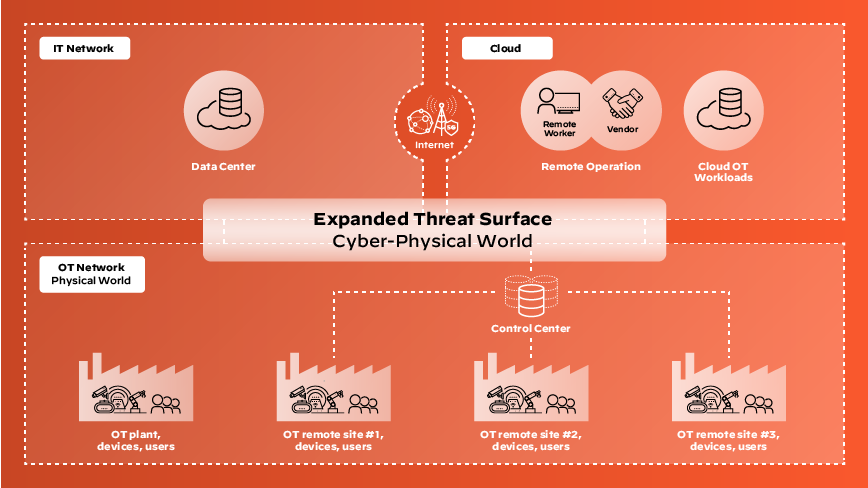
As the lines of distinction between IT and OT fade, the attack surface of interconnected IT/OT systems widens. The most common attack vector for hackers to infiltrate is via the internet.
ICS sensors, instruments, and OT devices accessible over an OT network are susceptible to weaponization. Botnets can be used to launch targeted attacks on critical infrastructure.
Usually, human-machine interfaces (HMIs) that connect human operators to industrial control systems are also networked to IT infrastructures. The accessibility to HMIs from internet-facing business networks poses a grave risk to ICS security. Consequently, HMIs are susceptible to IP-based vulnerabilities, including:
- Authentication bypass
- Weak session management
- Unsecured ICS communication protocoling
- Insufficient control traffic encryption
Attackers typically infiltrate ICS systems with malware. It could be generic, or it could be malware designed to attack critical infrastructure. These infiltrations often result in denial of service (DoS) attacks that paralyze or halt industrial networks and operations.
ICS and IIoT devices are also high-value targets for hackers. Whether malicious actors are looking to collect ransoms or sabotage rival nations by accessing confidential data, this is a target area.
OT Security Risks and Challenges
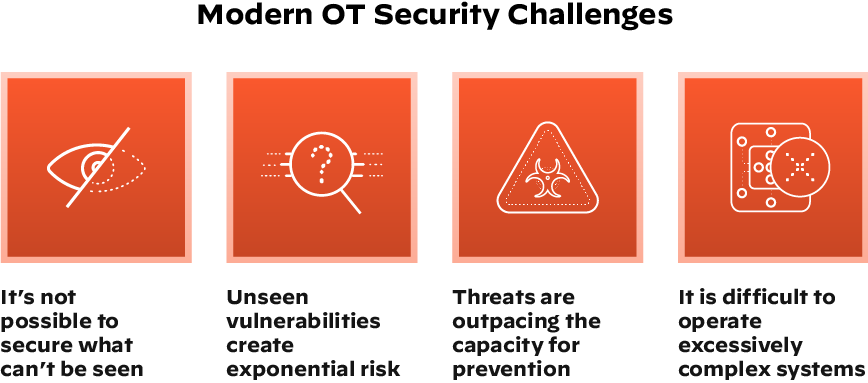
Digital transformation and connectivity in OT environments bring great promise, as well as significant risk. A flood of connected devices will increase opportunities for attack. This is especially true in OT environments because OT devices are vulnerable and exposed.
- 1K+ common vulnerabilities and exposures in industrial control systems
- 80+ vulnerabilities in top 4 OT vendor devices
- 29% of OT devices exposed due to internet connectivity
The dangerous aftereffects of security breaches on ICS differ greatly from typical cyber attacks. Consider the impacts of possible incidents an OT system may face:
- Interference with safety systems operations
- Interference with equipment protection systems (which protect costly equipment that is not easily replaced)
- Malicious changes to alarm thresholds, commands, or instructions
- Malware infected OT software or improperly modified OT configuration or software settings
- Jammed or delayed flow of data through OT networks, which could disrupt OT operation
- Erroneous data sent to system operators (designed to disguise unauthorized changes or cause operators to take inappropriate actions)
Top OT Security Best Practices
According to NIST, there are nine OT security recommendations for forming, implementing, maintaining, and continually improving an OT security program. In implementing and maintaining these best practices, organizations can establish an OT security roadmap for risk management:
- Establish OT security governance.
- Build and train a cross-functional team to implement OT security program.
- Define OT security strategy.
- Define OT-specific policies and procedures.
- Establish security awareness training program for OT organization.
- Implement a risk management framework for OT.
- Develop maintenance tracking capability.
- Develop incident response capability.
- Develop recovery and restoration capability.
Establishing a complete and effective OT security program is a complex undertaking differing from typical cybersecurity strategies. Ultimately, the end goal is to maximize operational uptime by reducing security breaches. Whether environments are partially air gapped or cloud connected, this can be accomplished with a Zero Trust OT security approach. A Zero Trust OT security approach consists of:
1. Least- privileged access control
- Microsegment
- Grant minimum access
2. Continuous trust verification
- Assess OT device security posture and behavior
- Assess app and user behavior
3. Continuous security verification
- Inspect all traffic, even for allowed connections
- Prevent all threats, including zero-day threats
Suggested FAQs
- OT and IT serve different purposes and operate in different environments. Therefore, they deal with different threat profiles and security tools.
- OT is focused on equipment and process safety and availability. IT is focused more on data security and confidentiality.
- OT is less exposed to the internet and faces attacks at a lower frequency; however, when attacks do arise, they can result in catastrophe. IT is more exposed to the internet and faces attacks at a greater frequency.
- OT security patching doesn’t usually happen frequently in comparison to typical weekly patches within IT environments.
- Interference with safety systems operations
- Interference with equipment protection systems (which protect costly equipment that is not easily replaced)
- Malicious changes to alarm thresholds, commands, or instructions
- Malware infected OT software or improperly modified OT configuration or software settings
- Jammed or delayed flow of data through OT networks, which could disrupt OT operation
- Erroneous data sent to system operators (designed to disguise unauthorized changes or cause operators to take inappropriate actions)
