What Does It Mean to Be “5G-Ready”?
This post is also available in: 简体中文 (Chinese (Simplified)) 繁體中文 (Chinese (Traditional)) Français (French) Deutsch (German) 日本語 (Japanese) 한국어 (Korean) Nederlands (Dutch) Türkçe (Turkish) Español (Spanish) Italiano (Italian)
With regard to security, it’s critical.
We keep hearing about products and technologies that are “5G-ready.” But what does that mean? Mobile Service Providers will undoubtedly require 5G equipment that is scalable in terms of capacity and throughput, but does that alone mean the networks will be 5G-ready?
In late February at Mobile World Congress 2019, we can certainly expect to see demos of 5G core networks, network slicing, New Radios (5G-NR), and other 5G-ready network components. But what about security? Mobile networks will not be 5G-ready unless the necessary security capabilities are baked into these networks by design.
Tom Wheeler, former chairman of the Federal Communications Commission, accurately points out in a recent NY Times op-ed: “Leadership in 5G technology is not just about building a network, but also about whether that network will be secure enough for the innovations it promises.” Wheeler goes on to state, “The simple fact is that our wireless networks are not as secure as they could be because they weren’t designed to withstand the kinds of cyberattacks that are now common. This isn’t the fault of the companies that built the networks, but a reflection that when the standards for the current fourth-generation (4G) technology were set years ago, cyberattacks were not a front-and-center concern.”
A New Approach for Security Is Needed
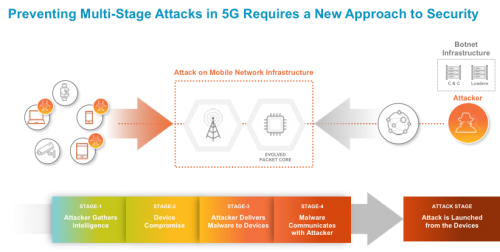
With 5G, everything changes. Critical applications like remote healthcare, remote monitoring and control over our power grids, and self-driving automobiles will all rely on 5G technologies. The networks will become more distributed, and many critical applications will be hosted at the edge of 5G networks and across edge clouds. Opportunities for threat actors will emerge if they are allowed to go unchecked, as they will use automation to wage multi-stage attacks and find the least secure portions of the 5G networks to exploit. For mobile networks to be 5G-ready, a new approach for security is required.
Even though standards and network architectures are still being defined, mobile operators not only have the opportunity to build the right set of security capabilities into these network evolutions by design, they have no choice but to do it. Today’s cyberattacks are already capable of evading mobile networks, and their continued evolution is indeed a front-and-center concern.
To truly be 5G-ready, mobile operators need to adopt a robust and comprehensive end-to-end security strategy with:
- Complete visibility, inspection, and controls that are applied across all layers of the network – application, signaling, and data planes.
- Cloud-based threat analytics – powered by machine learning (ML) – that are leveraged across the different mobile network locations and environments.
- A cloud-ready platform that ensures consistent security enforcement across all network locations.
With these necessary security capabilities in place, mobile networks will be able to evolve as 5G-ready with a data-driven threat prevention posture that provides contextual security outcomes. Mobile operators will be able to automate processes to proactively identify infected devices and prevent device-initiated attacks. They will be able to capture advanced multi-stage attacks that will naturally look to leverage different signaling and control layers across the 5G networks. They will be able to automatically identify advanced threats, correlate these with specific devices/users, and isolate/remove infected devices from their networks. They will also be able to differentiate themselves as “secure business enablers.”
These 5G networks are set to become the backbone of transformational services that will positively alter our lives for generations to come. Whether it’s autonomous vehicles, remote surgery, smart utilities, or the multitude of other technological advancements that will enable us to benefit from 5G, as Wheeler states: “Innovators, investors and users need confidence in the network’s cybersecurity if its much-heralded promise is to be realized.”
Meet with us at Mobile World Congress for an exclusive, executive 5G security briefing
Email us at: mwc@paloaltonetworks.com
References:
Palo Alto Networks: A New Approach for 5G Security
Lee Klarich Interview on 5G Cyber Security
Webinar: 5G Security: A New Approach is Needed
Related Blogs
Subscribe to the Newsletter!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.