Every year, the cloud is becoming more distributed, automated and tightly wired into the business. Every day, adversaries compress the timeline between compromise and data exfiltration. What once took them 44 days now takes minutes. For the fifth year in a row, Palo Alto Networks State of Cloud Security Report 2025 captures the changes both big and small that security leaders are navigating in the market today. Our report reveals that the rapid adoption of enterprise AI is fueling an unprecedented surge in cloud security risks, driving a massive expansion of the attack surface. We found that 99% of organizations experienced at least one attack on their AI systems within the past year, and the acceleration of GenAI-assisted coding is outstripping security teams' capacity to keep pace. What’s missing isn't just visibility, it’s alignment.
Our research, drawing on insights from more than 2,800 security leaders, surfaces the critical cost of misalignment across teams, tools and workflows. This report provides key benchmarks to help inform the decisions that shape your cloud strategy as we track where teams gain ground, where they struggle, and how the threat landscape, now accelerated by AI, is evolving.
The Cloud Attack Surface Is Expanding with AI
The biggest shift in the cloud landscape is the acceleration of risk driven by AI adoption. As cloud infrastructure expands to host the growing number of AI workloads, it has become a critical target. The introduction of GenAI into development pipelines is also compounding the problem by increasing the volume of insecure code going into production.
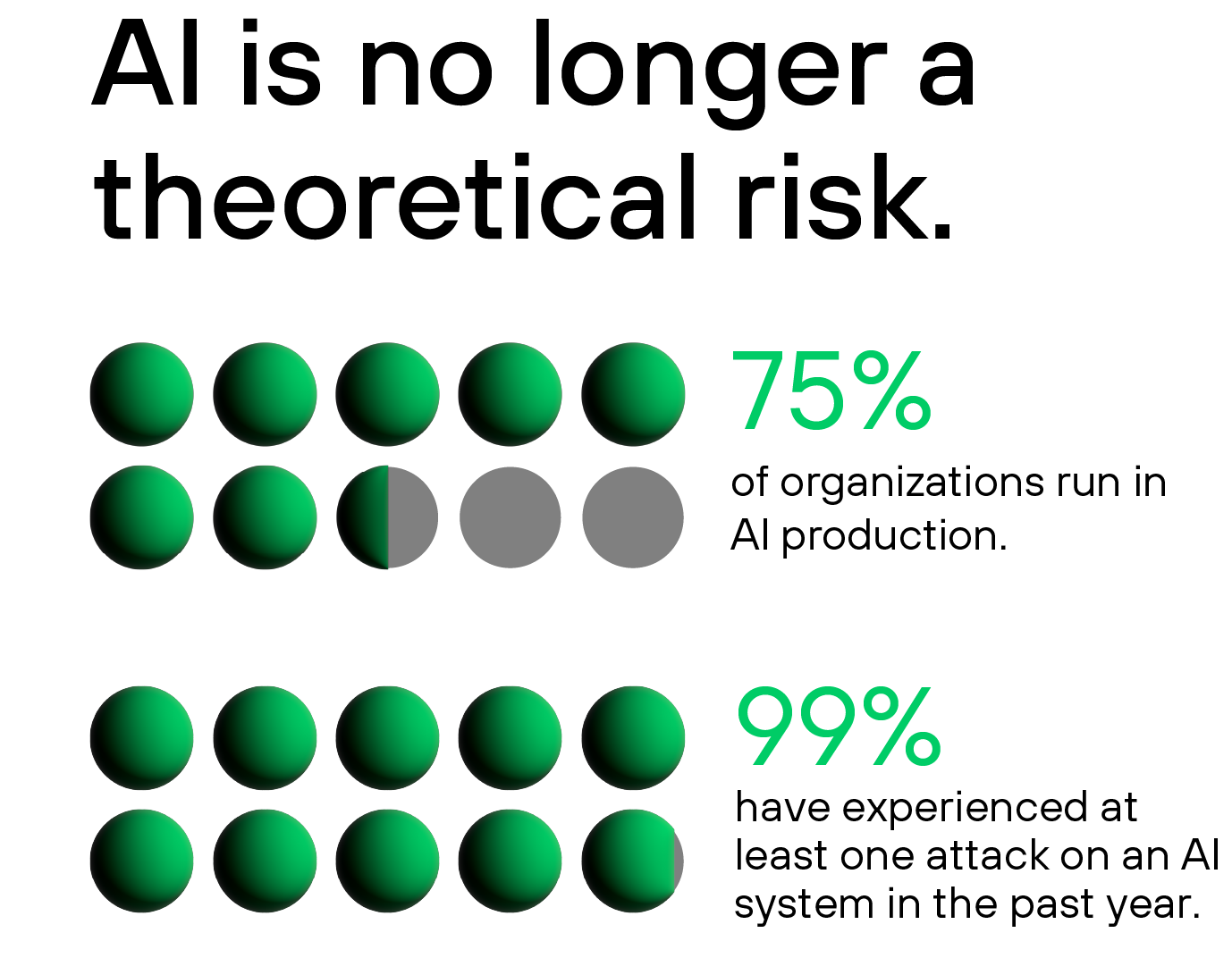
Of those surveyed in the 2025 report, 75% of organizations stated that they are running AI in their production environments today. That level is significant, as it points to the growing adoption and use of AI as businesses are locked in what looks like a modern arms race to bring the latest capabilities and benefits to their organizations and customers. In addition, as stated earlier, our findings confirm that 99% of organizations reported at least one attack on their AI systems within the past year. This number proves that AI needs human guardrails, as well as to be secured to contain the risk of critical data exposure by adversaries.
The AppSec Pipeline Is Not Secure Enough Yet
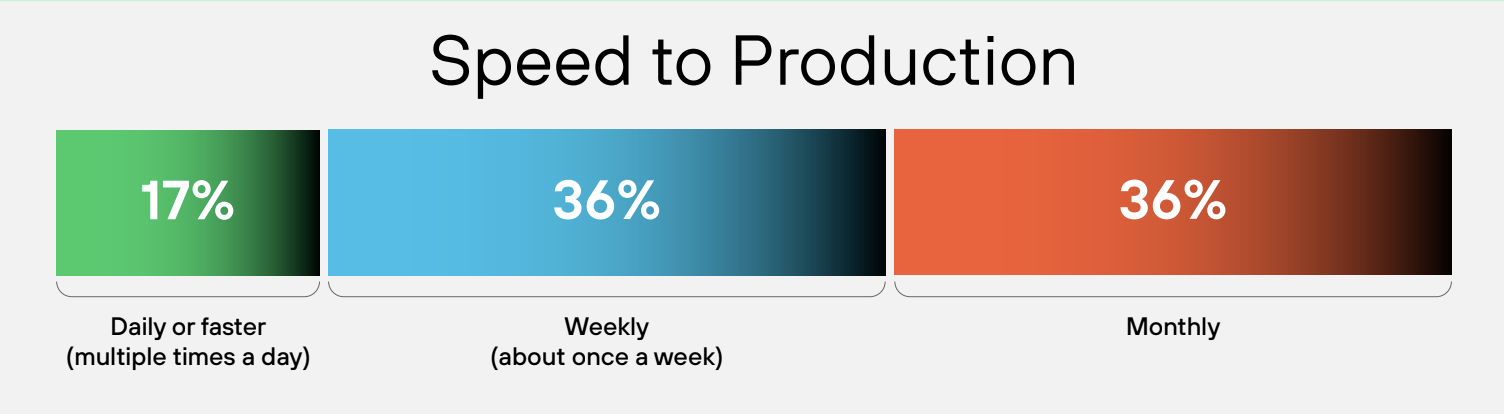
As AI expands the cloud attack surface and has been proven to be a significant target, we can see that code development pipelines are also being stressed by the same forces. An important trend from the 2025 report is the rise of GenAI-assisted coding (vibe coding), used by 99% of respondents. The use of vibe coding is generating insecure code faster than security teams can review it. The acceleration creates a massive risk gap: 52% of teams are shipping code weekly, but only 18% are able to fix vulnerabilities at that same pace. This confirms that traditional, human-led approaches to application security are inadequate, leaving security teams to fight threats with fragmented tools and slow, manual fix cycles.
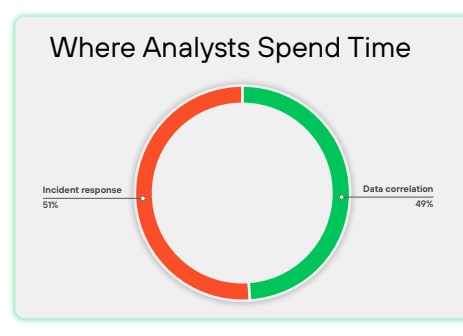
As the pace of development increases, the disconnect between security assessment and remediation is becoming more apparent too. While teams are making progress by shifting away from outdated vulnerability prioritization methods, they still struggle to integrate security effectively into the development workflow. This introduces a large number of vulnerabilities into production, where 20% of organizations report that an average of 37% of their high or critical issues reach their production environments. Once in production those vulnerabilities linger, as 82% of organizations report it taking longer than a week to deploy code fixes. What is slowing teams down?
The traditional refrain toward implementing prevention that blocks risks from reaching production during rapid code development is still true today. The barriers are clear: 31% cite poor CI/CD integration and another 31% worry about slowing down development. On the positive note, only 17% rely on CVSS scores to prioritize their fixes as teams are now moving more toward context-rich decisions based on exploitability-based triage (32%) and business impact (33%).
The New Frontiers of Cloud Risk
Attackers are rapidly pivoting to exploit the foundational layers of the cloud, with a clear focus on ungoverned interfaces and overprivileged access. The volume and autonomy introduced by AI agents further accelerates this exploitation, turning minor gaps into major incidents.
Attacks on APIs Jump for 41%
APIs are the new primary entry point. Attacks on APIs increased for 41% of organizations in the last year, marking the sharpest rise of any threat category measured. As agentic AI relies heavily on APIs to operate, this explosion in usage has greatly expanded the attack surface. Furthermore, nearly every AI-related threat, including model supply chain tampering, token theft and prompt injection, involves an API boundary. This reinforces the role of ungoverned interfaces in scalable AI compromise, with 47% of AI system breaches involving data exfiltration through assistants or plugins.
Identity Still Remains the Weakest Link
Insufficient access controls remain a leading vector for credential theft and data exfiltration. 53% of organizations cite lenient identity and access management (IAM) practices as a top data security challenge. This problem is compounded by complexity. The number climbs to 57% among organizations running more than six AppSec tools, proving that the discipline required to maintain least privilege is failing to scale with tool sprawl. Data leaves through both legitimate business systems and breach events, making it fundamentally an identity problem.
The top three exfiltration vectors confirm this focus:
- SaaS sync or export misuse: 63%
- Overpermissive external sharing: 59%
- Compromised credentials or tokens: 58%
Lateral Movement Risks Persist
Once an attacker gains a foothold, they can move freely. Twenty-eight percent point to unrestricted network access between cloud workloads as a growing threat, allowing attackers to pivot across environments and turn minor compromises into major incidents.
The Growing Imperative of Cloud & SOC Must Merge
The gap between detection and resolution is where breaches succeed. Today the cloud and SOC divide is proving too slow in the face of machine-speed threats. Structural fragmentation is clearly visible in response times, while 74% of organizations detect threats within 24 hours, 30% take more than a full day to resolve them. A delay like this is caused by disjointed workflows and isolated data sources between cloud and SOC teams, which stall incident response (IR) for 50% of organizations.
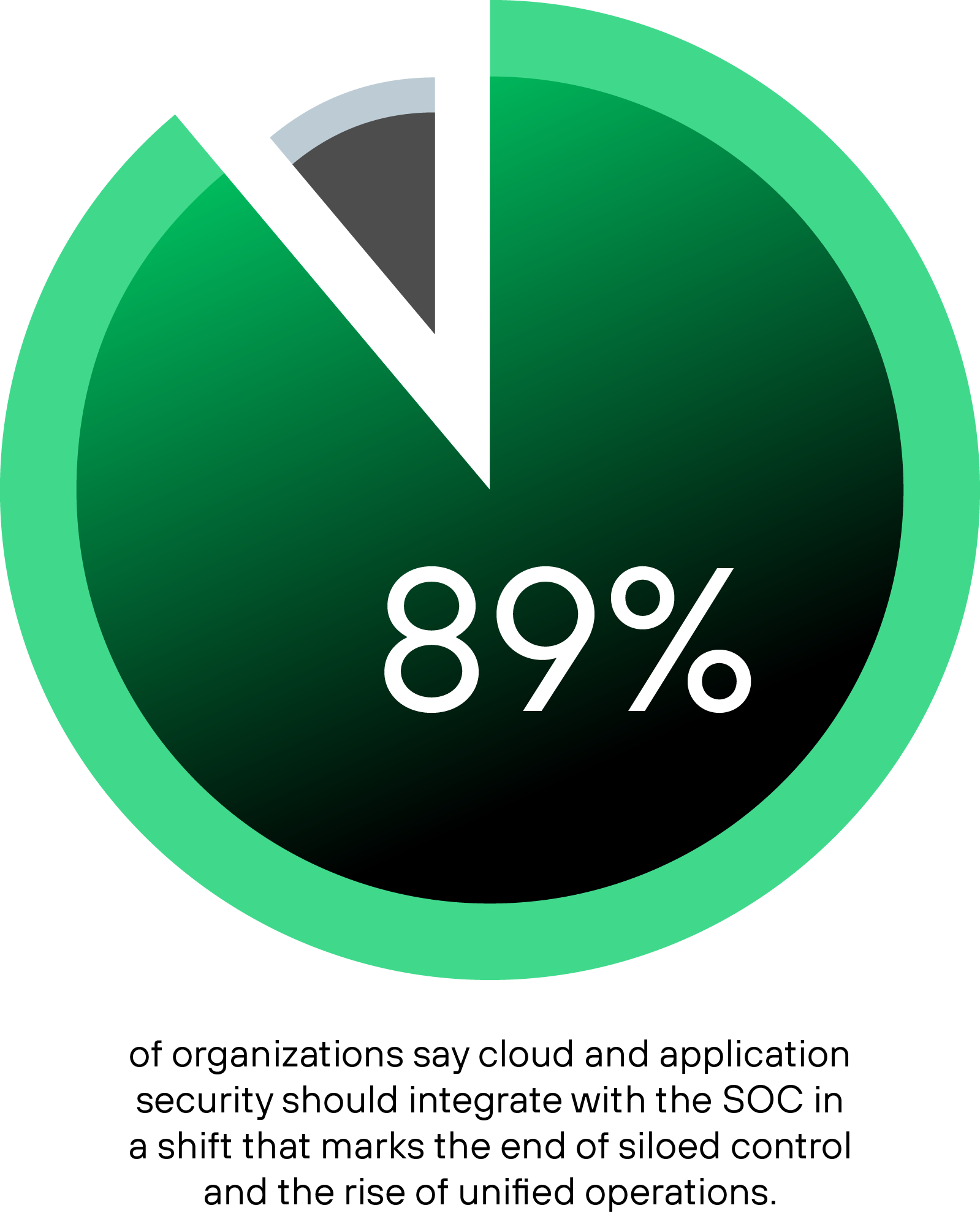
The demand for consolidation shows up across the board:
- 89% of organizations believe cloud security and security operations must fully merge, not just integrate.
- Organizations currently manage an average of 17 tools from five vendors, creating fragmented data and context gaps.
- Consequently, 97% of respondents prioritized consolidating their security footprint to address the chaos of tool sprawl.
The model that worked for lift-and-shift can't contain threats that move at machine speed. Organizations are ready to collapse the distance between teams and tools.
About the Report
The State of Cloud Security Report 2025 draws from over 2,800 security leaders and practitioners across 10 countries and includes breakouts by region, industry and cloud maturity, along with the full incident data and strategic insights we’ve touched on here.
Learn More and Transform to an Agentic-First Platform
To stay ahead of adversaries who use AI to launch attacks at machine speed, human-led defense is no longer sufficient. The report emphasizes that organizations must counter with an equivalent evolution: Agentic security, leveraging autonomous agents to deliver cloud security from code to cloud to SOC.
Download the full State of Cloud Security report to see how today’s leaders are closing the gap and what we recommend.