Advanced Terraform security is a hot topic as you scale in the cloud. Because infrastructure as code (IaC) allows you to quickly spin up cloud resources at scale, leveraging an IaC framework like Hashicorp Terraform is key to helping your team move fast in the cloud. But as you adopt Terraform and start to leverage more advanced Terraform use cases, securing those new use cases can be challenging.
As you adopt increasingly-advanced Terraform use cases, you’ll need equally advanced IaC security. To address this need and support teams as they modernize their applications and operationalize cloud-native workflows, Palo Alto Networks partners closely with Hashicorp (and was, in fact, named their partner of the year).
In addition to securing your infrastructure deployments with support for Terraform Cloud Run Tasks, you can leverage Prisma Cloud for advanced Terraform security use cases — such as dynamic blocks, Terraform Pre-Plan Run Stage scanning, nested modules, multihop variable rendering and more. With Prisma Cloud’s developer-friendly approach to advanced Terraform security, you’ll be able to ship code that’s secure by default.
Dynamic Blocks and for_each Arguments
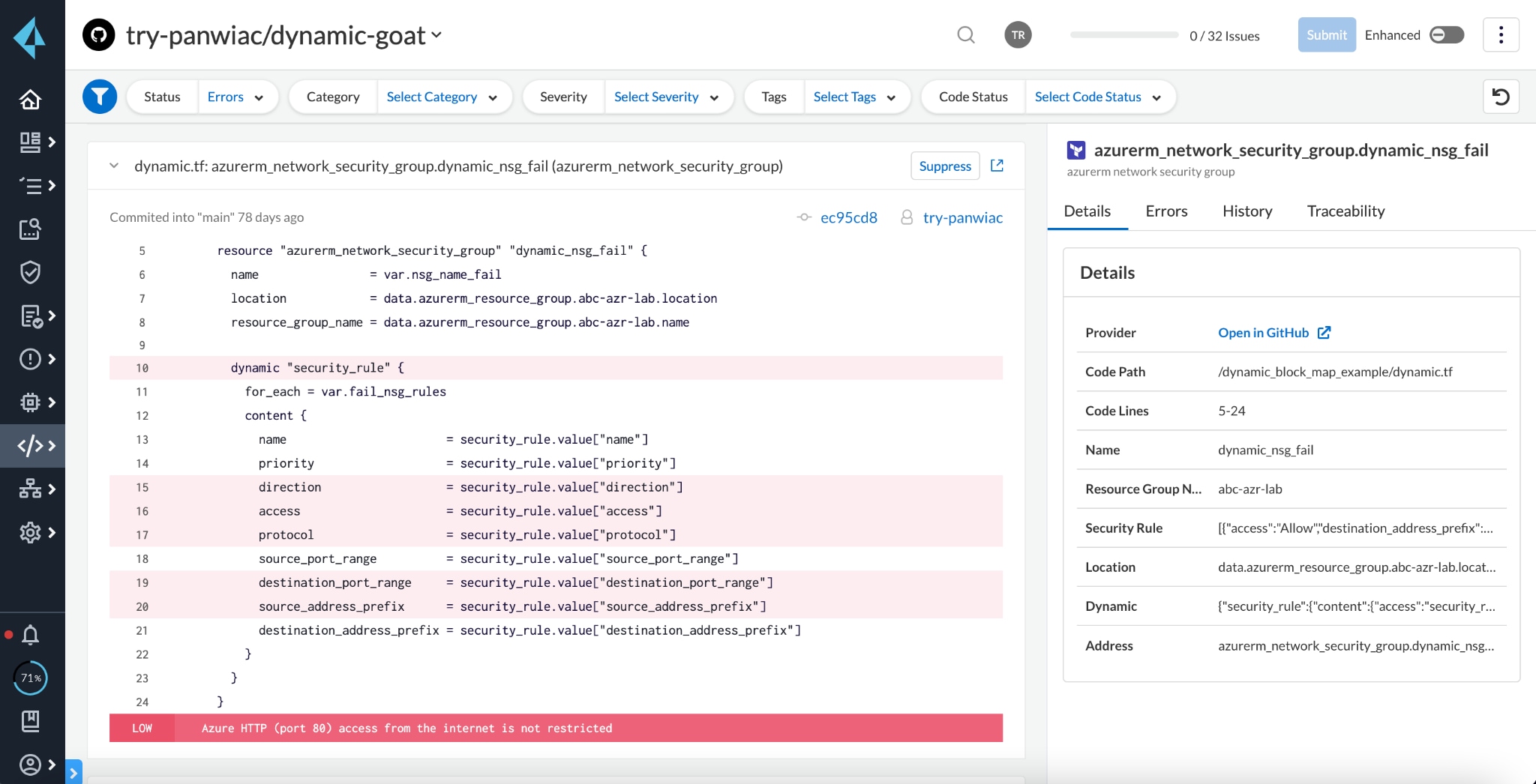
Dynamic blocks and for_each arguments offer developers a simple way to templatize cloud resources and generate multiple correct configurations consistently. If you have a golden configuration for an S3 bucket, you just need to define one statement with for_each arguments and then repeat however many you need. And if you have repetitive configurations inside of a resource, such as opening multiple ports in a security group, then you can leverage dynamic blocks to simplify replicating those configurations.
However, dynamic blocks and for_each arguments introduce risk. If your golden S3 bucket configuration contains a security issue, that issue gets multiplied by the number of resources created by the for_each argument. Prisma Cloud now resolves these arguments to identify security issues in the HCL to make it easier to fix before production.
Terraform Pre-Plan Run Stage Support
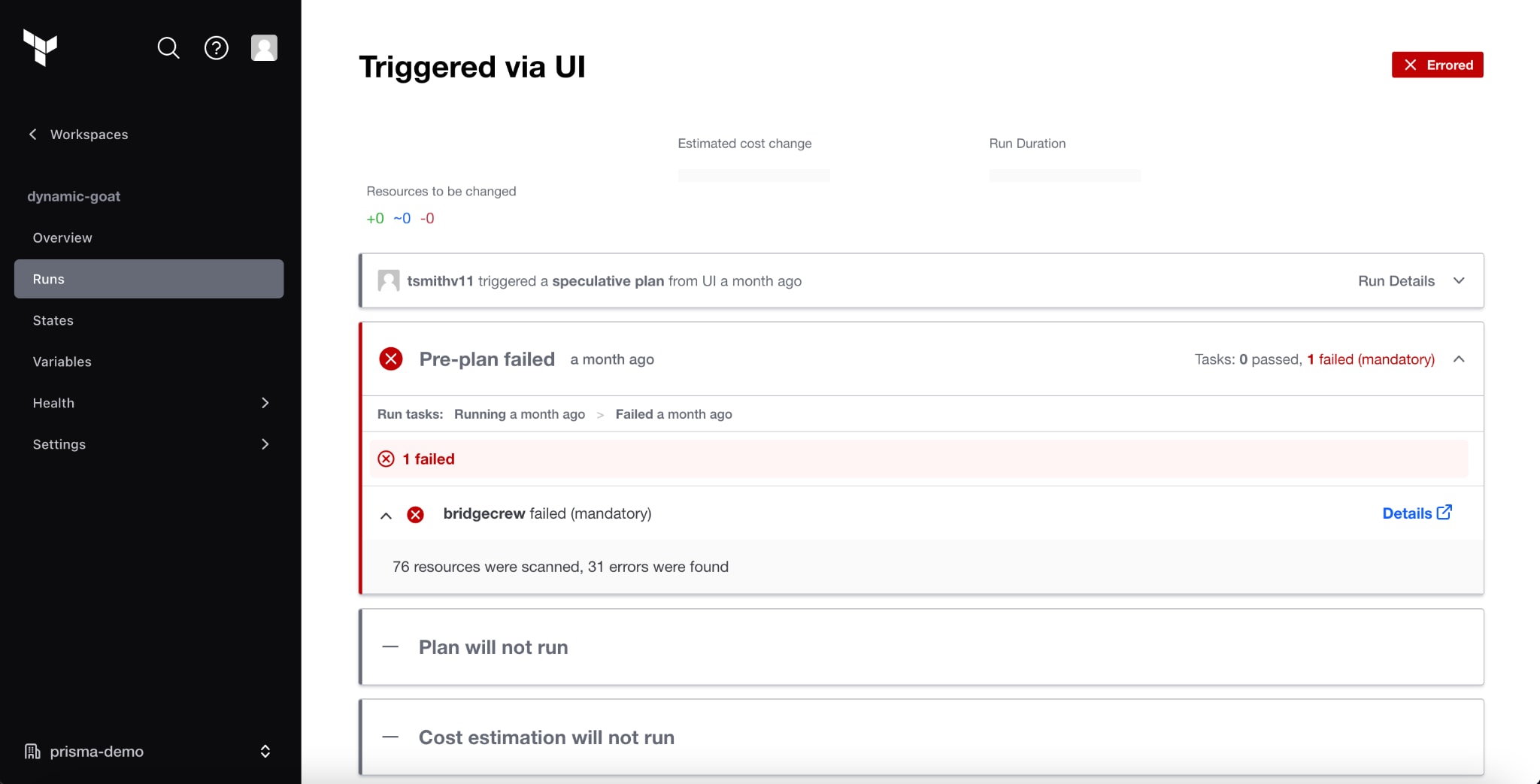
While our support for Terraform Run Tasks allows you to scan plan files after they’ve been generated and before they’re deployed, Pre-Plan support enables you to scan the code before the plan files are even generated. This feature streamlines and accelerates development because you no longer have to wait to scan the plan file to identify security issues.
Historically, security issues identified in the plan file were difficult to get visibility into and slowed development, since it was challenging to tie the security issue to the specific line of code that generated the issue. Now, you can scan the actual code and see the specific lines of code that need fixing, so you can easily remediate issues and ship secure code fast.
And if you have complex code like dynamic blocks and for_each arguments, Prisma Cloud will highlight the violating code block to further streamline the remediation process so you don’t have to wait for the plan file to start identifying and fixing issues.
Nested Modules and Multihop Variable Rendering
Terraform doesn’t just include simple modules or single variables. Oftentimes, modules are built in a tree-like structure with one module referencing other sub-modules. This module structure, called nested modules, requires a more advanced approach to security. Simple module and variable rendering can catch security issues in simple code, but this process will cause false positives and false negatives in advanced Terraform security use cases.
Prisma Cloud renders nested modules and spans across variable hops to provide accurate insights on the code as it will be applied to the cloud. Instead of tying plan files back to the issue, Prisma Cloud can render nested modules into the final resource so that the platform can scan for misconfigurations and drift.
With Prisma Cloud, you can get advanced Terraform security that’s embedded into your existing workflows so that you can ship secure code fast. To see advanced Terraform security in action, watch a Code Security demo or request a free trial.