On Mar. 3rd, Linux publicly disclosed DirtyPipe, a critical kernel vulnerability introduced in Linux 5.8 and tracked as CVE-2022-0847. Unprivileged local attackers can exploit DirtyPipe to take over a vulnerable machine by injecting code into root processes, or by overwriting read-only, immutable, or root-owned files. The vulnerability is relatively easy to exploit and enables significant attacks against container environments.
Malicious containers can exploit DirtyPipe to overwrite their image on the underlying host. This may allow them to compromise both current and future ones neighboring containers, given they share the same image, base image, or file layers. Prisma Cloud researchers analyzed the vulnerability and discovered that DirtyPipe can also be weaponized to create a malicious container image that breaks out upon execution. Given the severity of the issue, we cannot rule out that existing containers may escape as well.
Environments running untrusted or publicly exposed containers are especially at risk, as they are most likely to host malicious containers. Unfortunately, there are no mitigations at the moment. Hardening containers with user namespaces or by running them as a non-root doesn't prevent an attack. Users are encouraged to update to a fixed version kernel as soon as possible: v5.16.11, v5.15.25, and v5.10.102. There is a silver lining though: hosts running a Linux version older than v5.8 aren't affected. If you're running a non-vulnerable version, be careful not to upgrade to a vulnerable one.
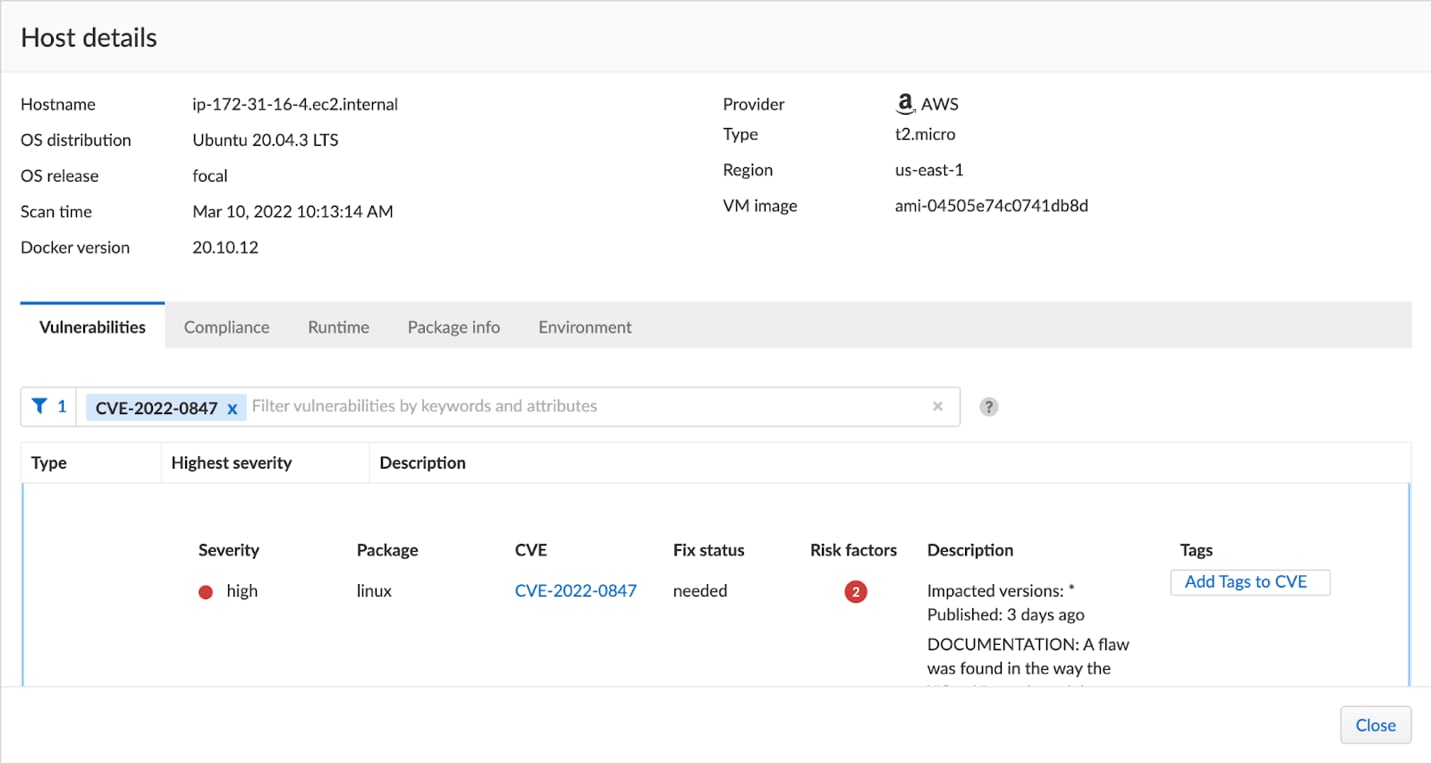
Prisma Cloud identifies and alerts on hosts running a vulnerable Kernel version. Users are encouraged to head over to 'Compute/Monitor/Vulnerabilities' to identify vulnerable hosts.
Root Cause Analysis
DirtyPipe stems from missing variable initialization in the kernel's implementation of pipes. The Kernel may mistakenly reuse flags that dictate whether a pipe can write to a memory page. As a result, an attacker can trick the Kernel into marking read-only memory pages exposed to the attacker's pipe as writable. We recommend reading the excellent advisory from Max Kellermann, the one who found the issue, for the full details.
There are some minor exploitation constraints. An attacker cannot:
- Overwrite files that it cannot read.
- Enlarge a file.
- Write to offsets that are multiples of the system's page size, including 0.
Unfortunately, these limitations are unlikely to stop the vast majority of exploits.
DirtyPipe Attacks on Container Environments
DirtyPipe enables severe attacks on container environments, as highlighted by the screenshots below.
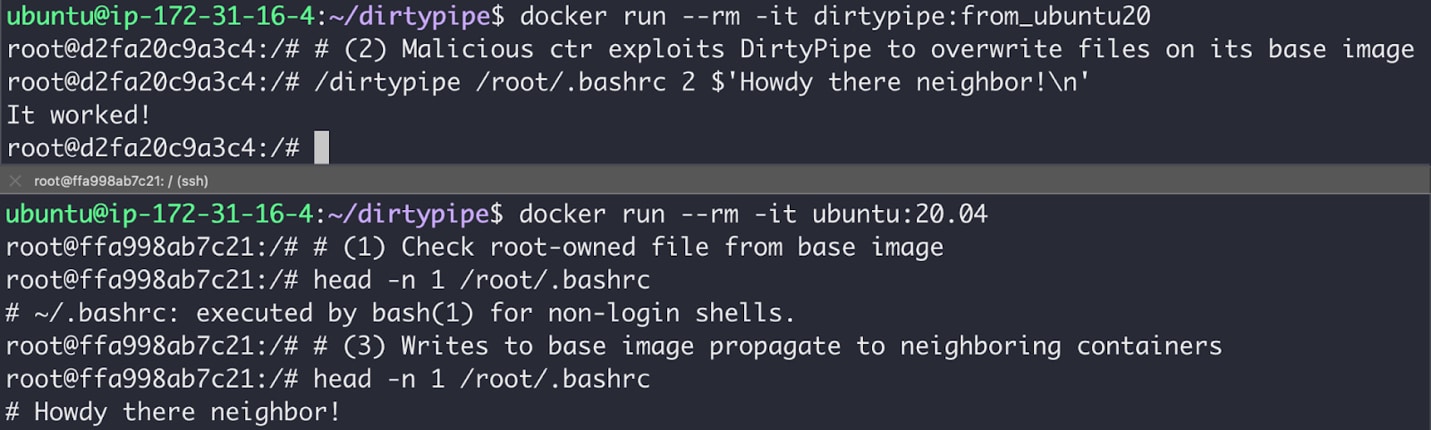
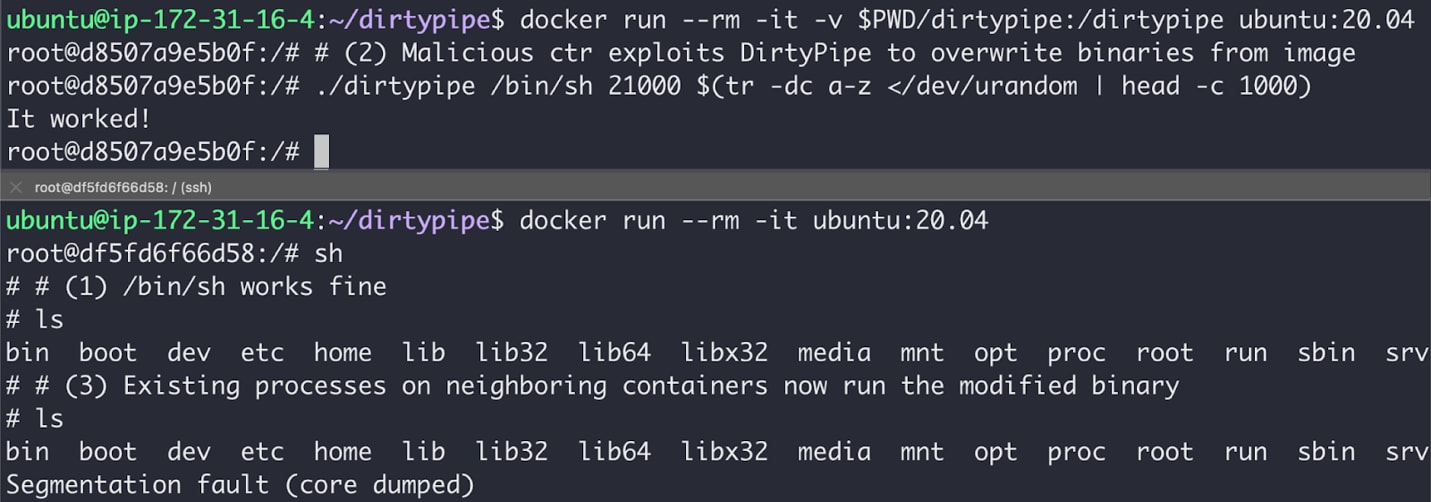
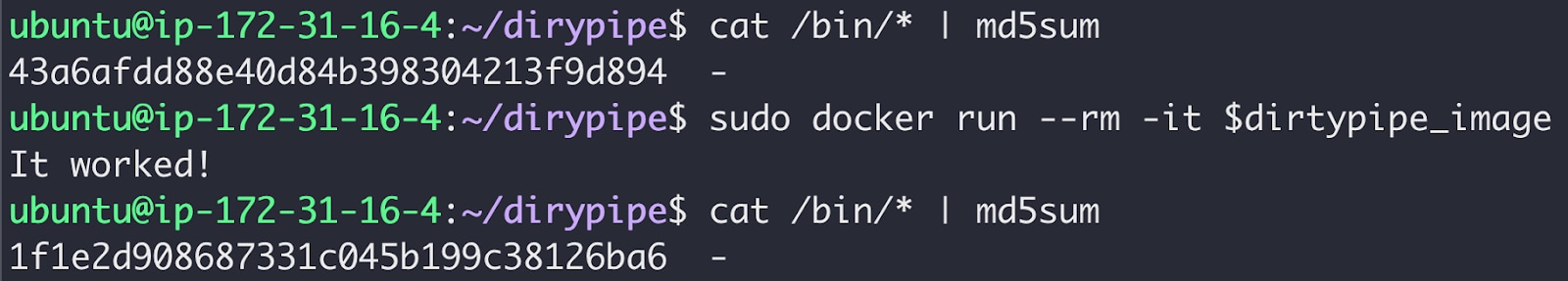
At the moment, we're not sharing the details of our container escape exploit to prevent malicious parties from weaponizing it.
While we haven't identified a way for an already running container to escape, others might. There're definitely indirect methods, for example by compromising a neighboring privileged container that has access to the underlying host.
Conclusion
DirtyPipe is a critical vulnerability in the Linux kernel with significant impact on container environments. Both container escapes and cross-container attacks are possible. Environments running untrusted or publicly exposed containers are especially at risk. Users are encouraged to update to a fixed Kernel version as soon as possible. Note that Linux versions older than 5.8 aren't affected.
Get Started with Prisma Cloud
Prisma Cloud customers are encouraged to head over to 'Compute/Monitor/Vulnerabilities' to identify vulnerable hosts. New customers can see Prisma Cloud’s Compute capabilities in action, by requesting a free trial here.
Learn More
Whether you’re new to containers or a cloud-native veteran, The 2024 Definitive Guide to Container Security is your essential resource for understanding, implementing and mastering security in a containerized environment. This book-length guide lays out in-depth insights and practical advice to empower developers, DevOps, cloud teams and security professionals to effectively protect their cloud-native applications.