At Prisma Cloud, we work hard to maintain pace with the latest industry advances in cloud workload technology to ensure we can support customers as they adopt them. One technology in particular where we have seen rising adoption rates has been with AWS Fargate.
Recognizing the current importance and potential future needs for this service, Prisma Cloud now provides an easy-to-deploy option for Defenders to protect Fargate tasks via a task definition. Users can also automate deployments with API call scripts instead of performing the task within Prisma Cloud, to better facilitate deployments at scale.
What Makes AWS Fargate Different?
We could discuss the relative benefits of Fargate for an entire blog, but to keep it short, it brings in a mix of advantages from both serverless functions and containers. As AWS states, it's “serverless compute for containers.”
With Lambda functions, developers can focus on application code without worrying about the underlying infrastructure. However, Lambda has some limitations in terms of CPU and execution time. And because serverless is a new operating paradigm for many customers, migration can be difficult.
Fargate addresses these issues by operating containers "as-a-service." It still abstracts away the operational overhead of managing underlying hosts but brings in the flexibility of a containerized deployment.
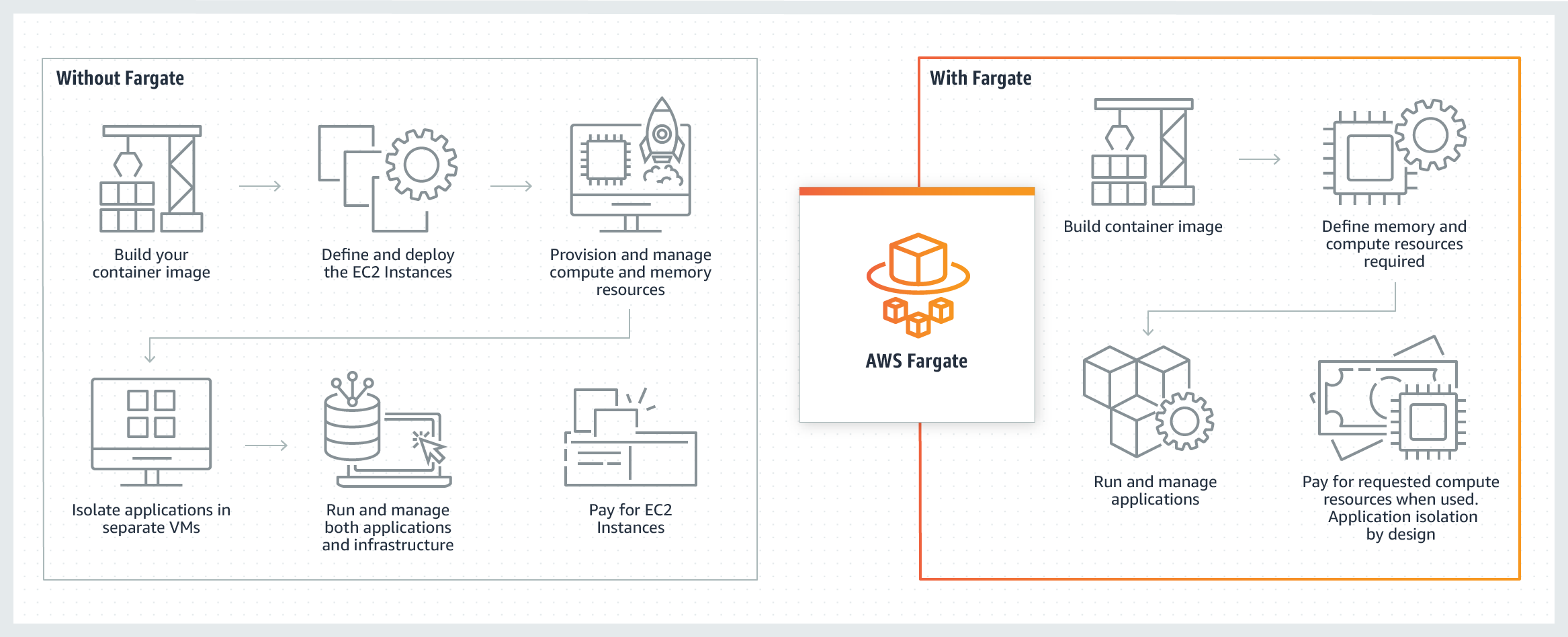
Securing Fargate with Prisma Cloud
Understanding these architectural differences, here are different ways in which we protect Fargate tasks – all with a single agent and no other integrations needed.
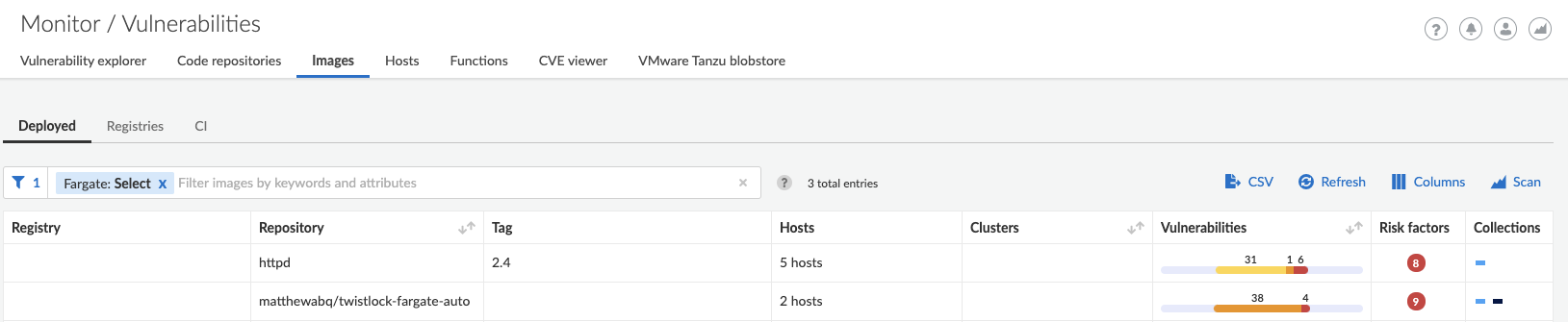
Vulnerability Scanning for Images in Tasks
Prisma Cloud Defenders can automatically perform vulnerability scans on images running in Fargate, just like regular container deployments – and will perform default scans across your Fargate deployments. You can also trigger policies specifically for images in tasks, filter images by task name, easily differentiate between images running in tasks versus deployed container hosts and much more.
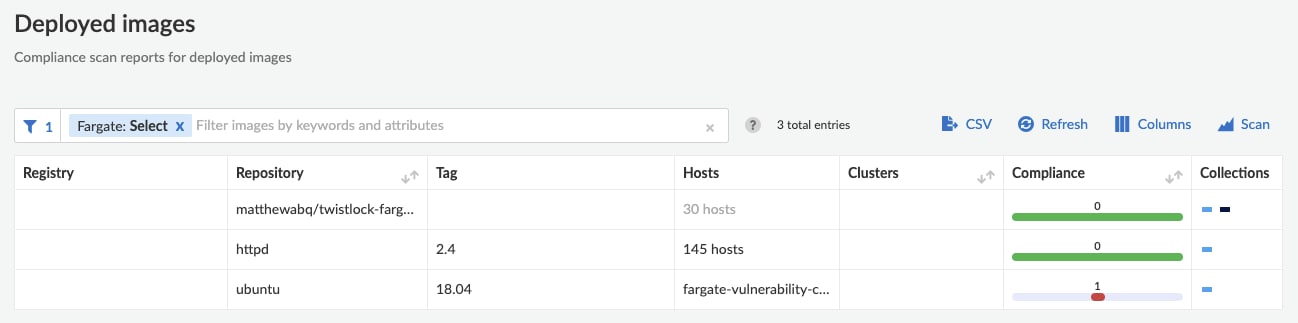
Compliance Scanning for Images in Tasks
Our research team reviewed all of our out-of-the-box container image compliance checks in order to curate a specific list for those that are applicable to Fargate, which helps reduce the "noise to signal" ratio in alerts. In addition, customers still maintain the ability to apply custom compliance checks for images running in Fargate tasks.
Runtime Protection for Fargate Tasks
Defenders for Fargate run as sidecar containers that monitor tasks to ensure they execute as defined, and alert on any violations of runtime policies. These controls can detect the launch of suspicious processes in your tasks, and outbound network connections to denied lists.
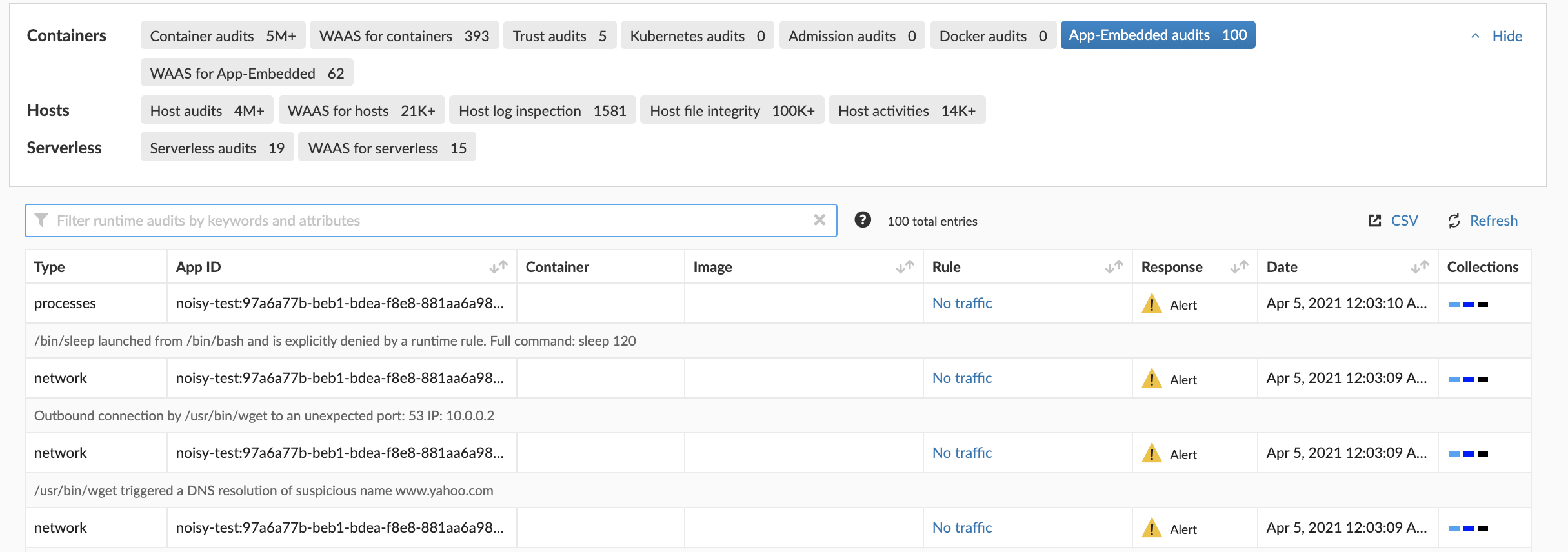
Violations of runtime policies by a Fargate task
WAAS for Fargate
Prisma Cloud also provides Web Application and API Security (WAAS) for Fargate tasks. Defenders for Fargate run as a reverse proxy to all other containers in the task. Depending on policies enforced, WAAS filters traffic that reaches your application port, and when a violation is observed, it alerts on or prevents the traffic, depending on your settings for that policy.
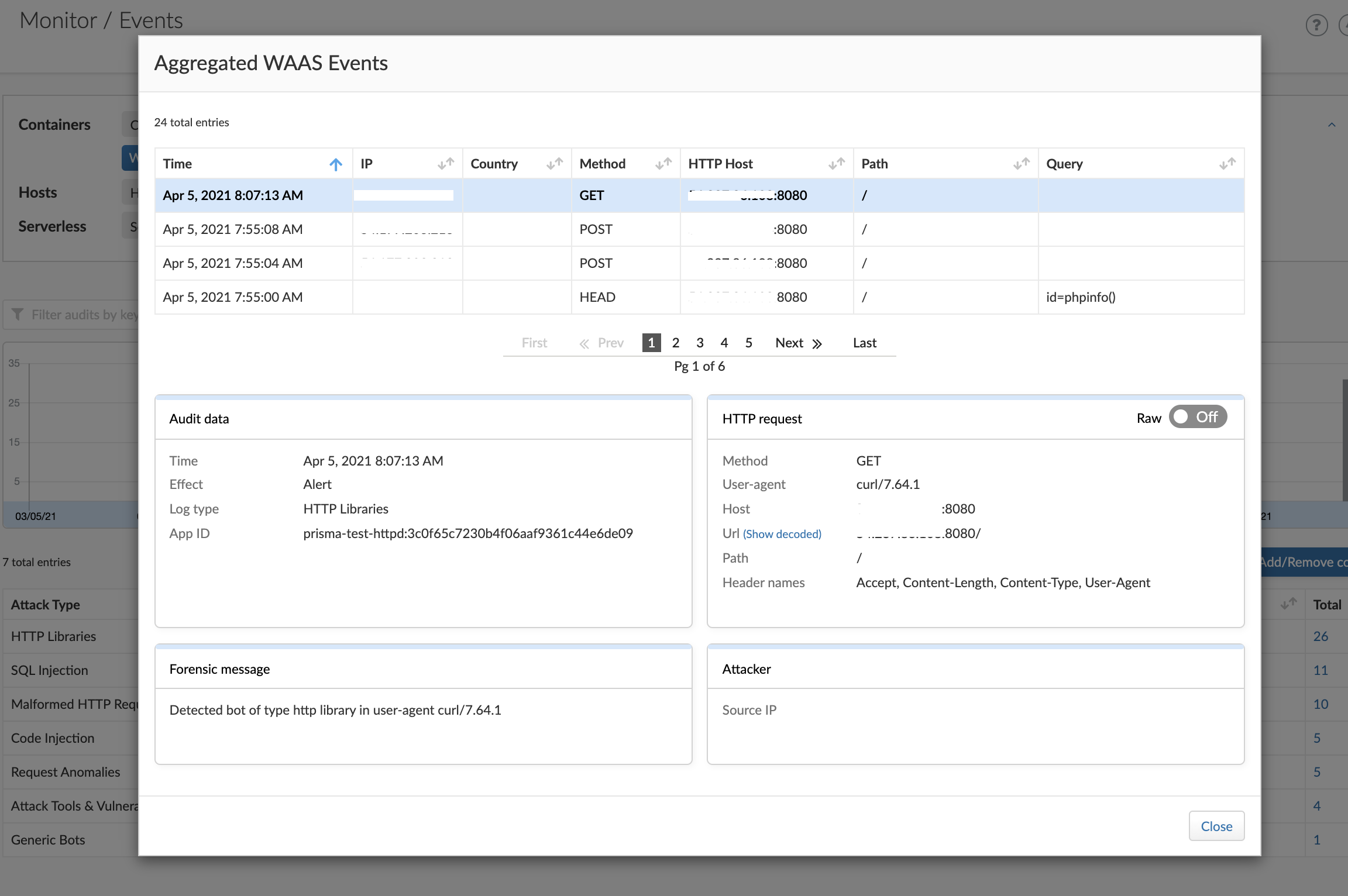
Learn More About Securing AWS Fargate with Prisma Cloud
From alerting on vulnerable components, compliance violations and web attacks, we provide not just one aspect of security, but make sure that your Fargate tasks are protected. Learn more about the type of attacks that Prisma Cloud detects and prevents in the technical documentation for Prisma Cloud WAAS and Defenders for AWS Fargate.
You can also learn more about securing diverse architectures into runtime with our latest ebook, Why and How to Add Runtime Defense to Your Cloud Security Strategy.