Cloud Workload Protection Delivers on the Promise of Zero Trust for Virtual Machines, Containers, and Serverless Architectures Across the Application Lifecycle
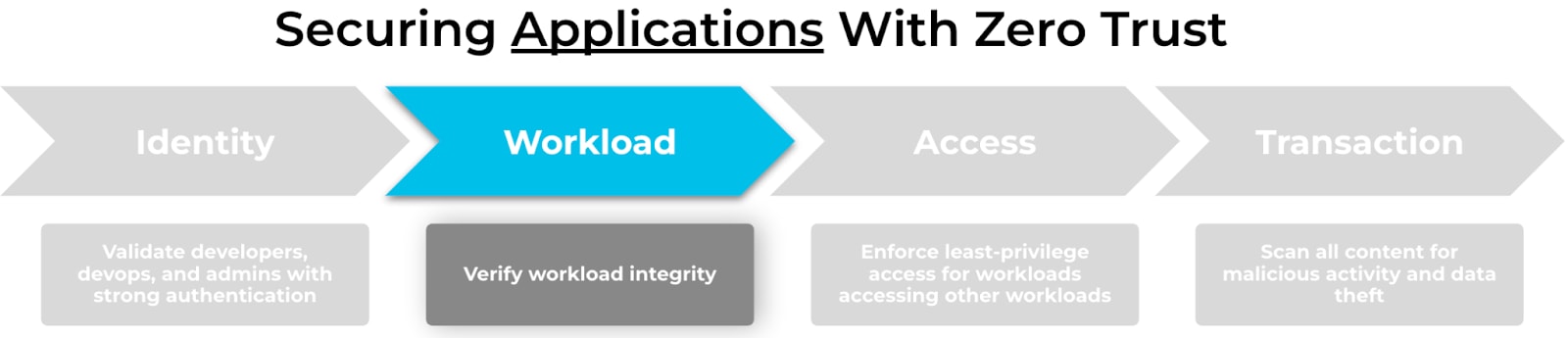
The principles of Zero Trust mindset is about rethinking how we secure identities, workloads, access, and data transactions. Cloud workload protection requirements are at the intersection of DevOps, cloud native architectures and Zero Trust architectures. The role of DevOps coupled with security is growing as vulnerabilities and breaches redefine the fundamental relationship between security and development.
The State of Cloud Workloads
Today’s enterprises continue to move to the cloud and take advantage of emerging cloud native architectures. The Palo Alto Networks 2022 State of Cloud Native Security Report found that:
- Organizations expect to host 68% of their workloads in the cloud within two years.
- 99% of organizations use virtual machines (VMs)
- 93% of respondents use containers
- 79% of respondents use CaaS
- 99% of respondents use PaaS/serverless.
A Cloud Native Computing Foundation (CNCF) survey revealed containers in production are the norm today with complexity and security as 2 out of top 3 challenges shared by respondents. With the proliferation of the cloud native architectures, security, infrastructure, and DevOps teams need a centralized solution to provide visibility and protection across the continuum of cloud native architectures to address vulnerabilities, manage compliance, and enable runtime protection.
With a vulnerability like Log4Shell, security teams would quickly want to identify vulnerable applications while also protecting their applications from threats and attacks. Ransomware attacks, for example, are increasing and becoming more costly to targeted organizations. According to Unit 42 threat research, the average ransom paid by organizations in the US, Canada, and Europe increased from US $115,123 in 2019 to $312,493 in 2020—a 171% year-over-year increase.
What Do You Need to Protect Workloads with Zero Trust?
Cloud native architectures bring clear benefits of improved scalability, availability, and shorter deployment time. The shift to a Zero Trust model is driven by runtime protection to enforce application control, prevent attacks, and capture forensic data. DevOps teams require comprehensive policy creation and enforcement. Including a flexibility of alerting and blocking execution of code if policy is violated by continuously monitoring and responding to indicators of compromise. Application-related security risks are on the rise. And with security becoming a top priority, there is more push to integrate security into early stages of the application lifecycle. Today’s DevOps teams are using continuous integration and continuous delivery (CI/CD) workflow, and they require tools and automation to secure cloud infrastructure and applications early in development.
With the perimeter changed from traditional apps, servers and users to hybrid-cloud, remote access and mobility, it is clear that Zero Trust model is not static - as the applications mature, so does the vulnerability and attack landscape; it is only a matter of time when the external attackers will attack an exposed application.
How We Can Help
Palo Alto Networks offers a portfolio designed to deliver on the promise of Zero Trust for cloud workloads. More specifically, the Cloud Workload Protection Platform (CWPP) capabilities from Prisma Cloud combined with Cortex Extended Detection & Response (XDR) provide complete controls to secure cloud workloads across the software development lifecycle.
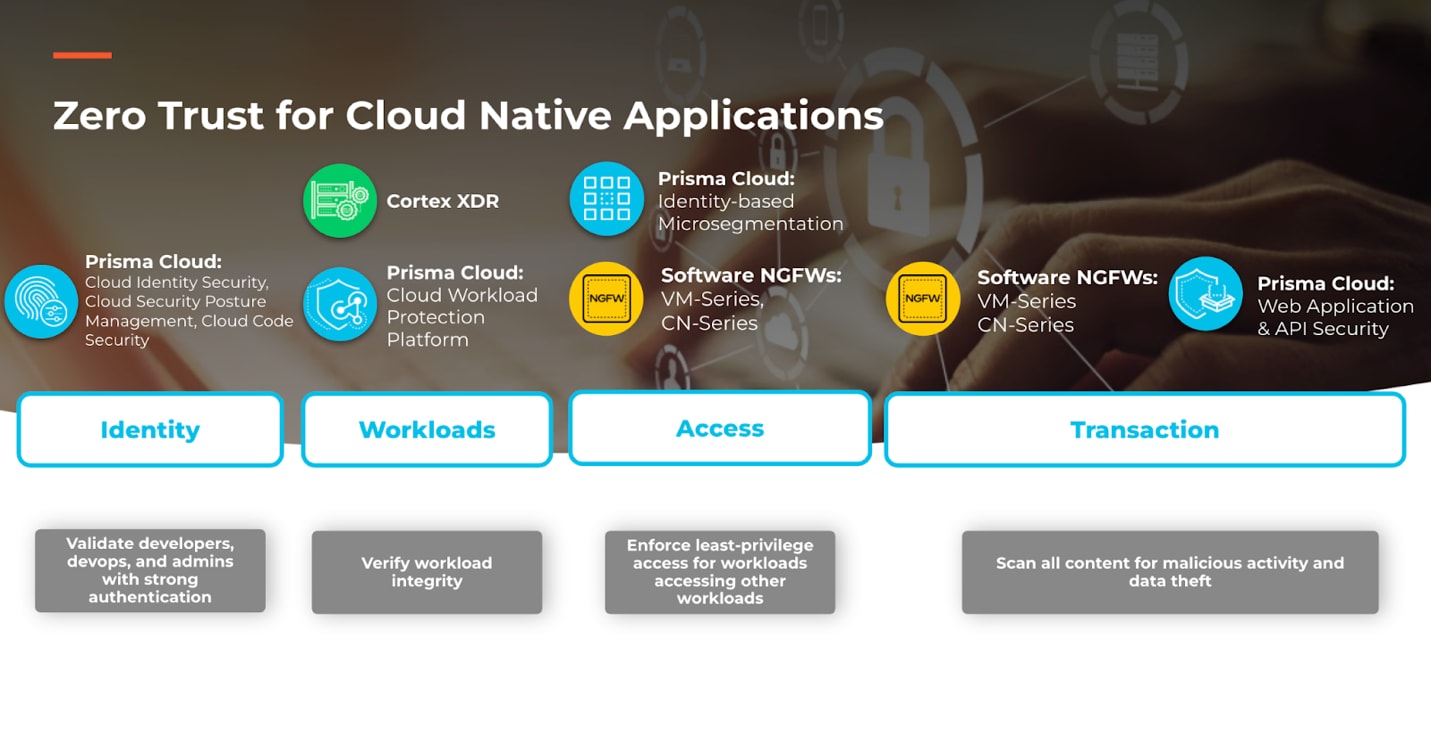
Prisma Cloud
Prisma Cloud delivers Cloud Workload Protection to secure hosts, Kubernetes, containers and serverless workloads across the full application lifecycle. Through the Cloud Workload Protection platform, Prisma Cloud delivers leading vulnerability management capabilities for the software development lifecycle (SLDC). Cloud Workload Protection provides application visibility into what is running and what is critical, thus driving reduced resolution time from hours to minutes. By identifying workloads and enforcing pre-defined policies, it restricts access to workloads based on risk, contextual policy and verified business need. This is done with a comprehensive policy enforcement with alerting or blocking threats at runtime. Additional key Prisma Cloud capabilities for Cloud Workload Protection include:
- Monitor and enforce security policies and compliance settings across your environments and assess privileges used by infrastructure
- Policy declaration defining which registries, repositories, and images to trust, along with responses to untrusted entities
- Fail/interrupt a build if an image contains vulnerabilities that meet severity criteria
- Identify changes to containers at runtime and prevent unknown behavior, including processes and unknown file system calls
- Runtime protection to ensure that processes that run in your environment meet the parameters of the learned models and the rules defined in the console
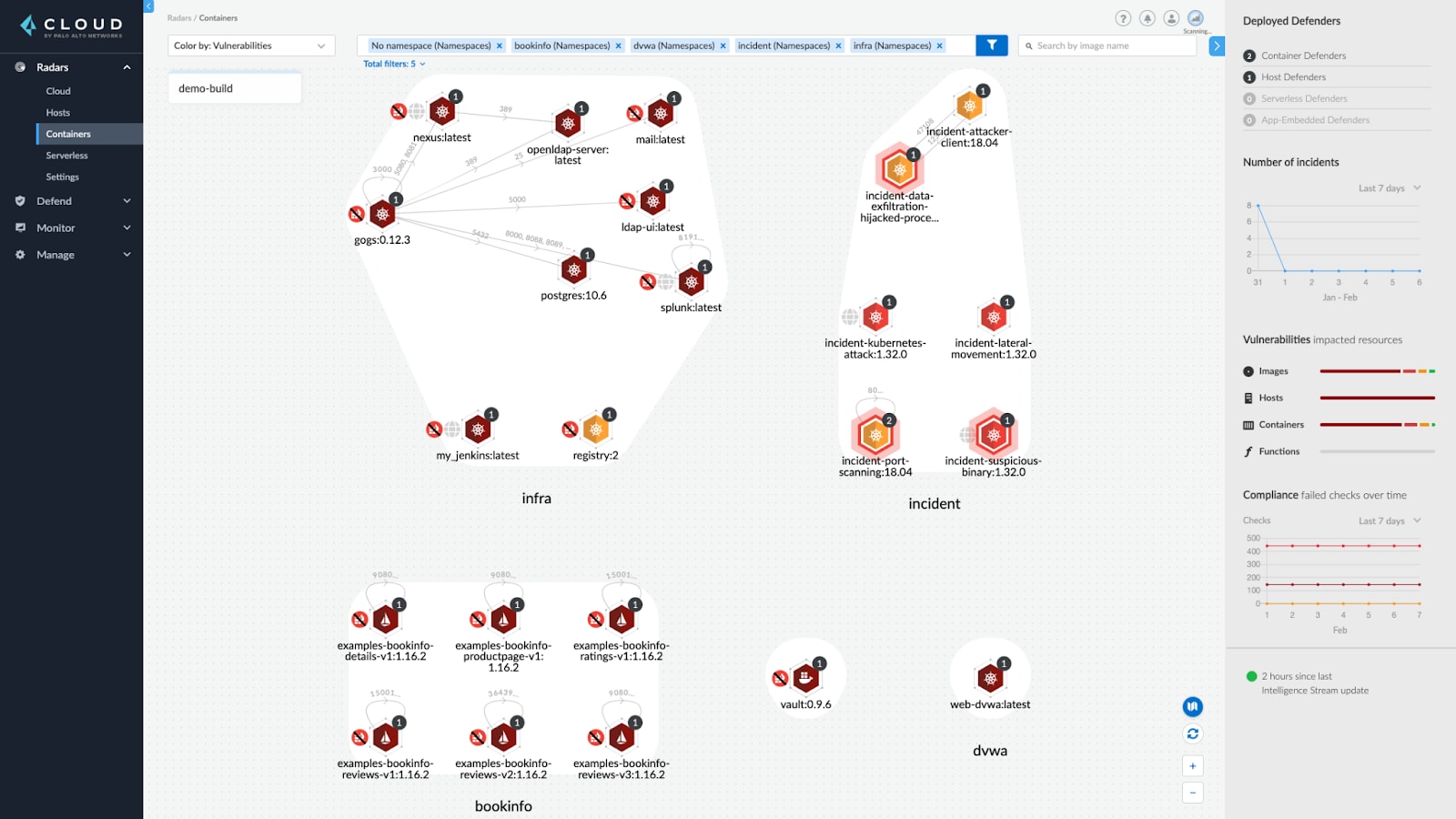
Cortex XDR
To achieve Zero Trust, organizations must verify the integrity of cloud workloads and secure the workloads from sophisticated attacks. Cortex XDR delivers tested and proven threat prevention, detection and response capabilities to proactively secure your cloud workloads against exploits, malware and post-intrusion activity. The Cortex XDR agent offers robust protection against Linux VM and container attacks, including ransomware and cryptocurrency mining malware. It also prevents exploits, including Log4Shell, with technique-based exploit prevention.
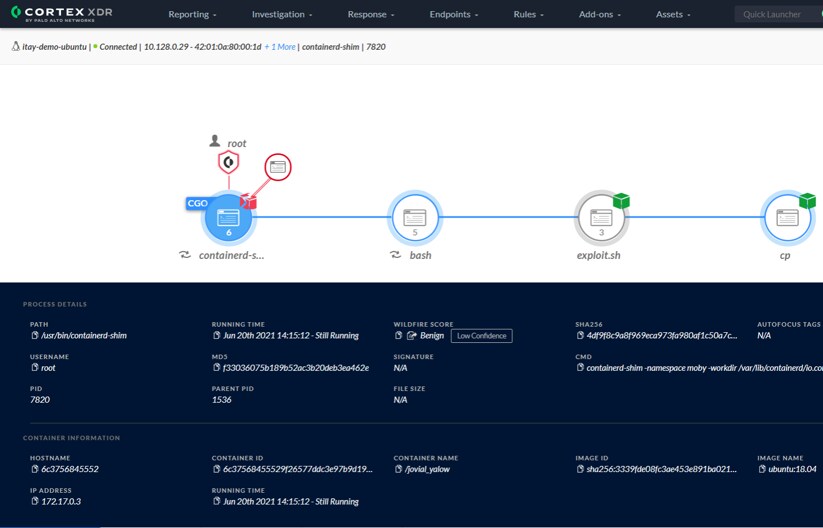
In addition to protecting cloud workloads from attacks, Cortex XDR can detect and respond to advanced threats, such as adversary tactics and techniques, with AI-driven behavioral analytics. Cortex XDR can collect cloud data from the Cortex XDR agent, from cloud audit and flow logs, and from Prisma Cloud, to uncover hidden threats. Thanks to the integration between Prisma Cloud and Cortex XDR, incident data from Prisma Cloud can be stitched within Cortex XDR for further analysis such as deep forensics and incident response.
Learn More
Palo Alto Networks can help secure cloud workloads and applications with Zero Trust principles from build to run. If you want to learn more about how to secure the fastest moving cloud native environments with Zero Trust, then check out our latest LinkedIn Live event. If you’re ready to get valuable hands-on experience with Prisma Cloud, then sign up for an interactive cloud native security camp.