What Does a Firewall Do? | How Firewalls Work
Firewalls act as a gatekeeper for network communications examining and filtering network traffic to ensure only authorized and safe traffic passes through.
This process protects the network from unauthorized attempts to gain access, cyber attacks, and malicious code.
How Does a Firewall Work?
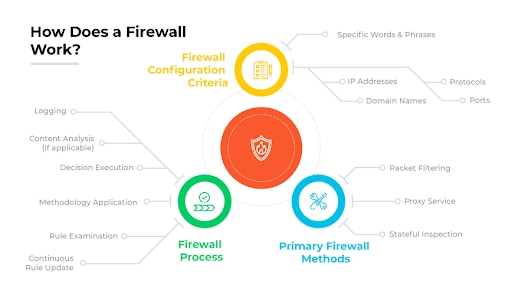
Primary Firewall Methods
Firewalls, whether hardware or software, operate utilizing three primary methods:
Packet Filtering:
Packet filtering is an access control mechanism that screens small data units (packets) against a predetermined rule set. Packets adhering to the rule set progress to their destined system, while the system rejects the rest. Packet filtering firewalls allow the filtering traffic mechanism to be based on elements like source and destination IP addresses, or even the type of service.Proxy Service:
Here, the proxy firewall acts as an intermediary. Instead of permitting direct communication of data packets between the user and the internet, the proxy fetches the data for the user and then relays it, preventing direct system access.Stateful Inspection:
Stateful inspection firewalls track outgoing packets and compare incoming responses to their database of active sessions. They approve only those that match a valid corresponding outbound packet.
Firewall Configuration Criteria
Configuration involves defining rules set based on specific parameters to control internal and external data exchanges. Configuration criteria includes:
IP Addresses:
Every device connected to the internet has a unique identifier called the IP address. These 32-bit number addresses typically appear as a series of four decimal numbers. If the firewall recognizes an external IP address as a potential threat or if it appears to access excessive data, it can block all communications from that address.Domain Names:
Protocols define the rules of communication between two devices or applications. Commonly used protocols that include IP, TCP, HTTP, FTP, UDP, ICMP, SMTP, SNMP, and Telnet. Organizations might decide to allow only specific protocols to be accessible on their network.Ports:
Servers provide services through port numbers. For example, HTTP, the protocol web browsers use, typically operates through port 80. Organizations can block or allow traffic based on these port numbers, ensuring tighter control over accessible services.Specific Words and Phrases:
Advanced solutions can scan packets for certain keywords, blocking any packet containing flagged terms.
Firewall Process
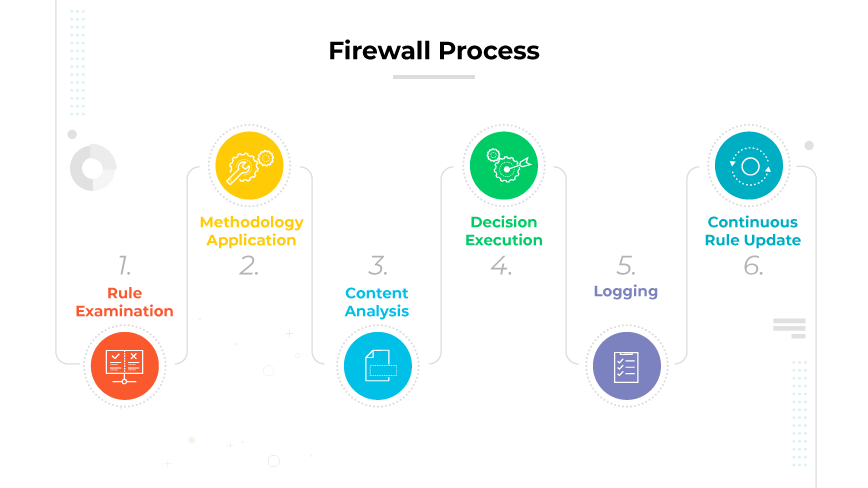
The structured process a firewall employs when a data packet attempts to traverse it occurs in the following manner:
Rule Examination:
Every data packet's journey starts with an evaluation against the established rules. Each rule outlines a specific criterion, and if the packet doesn't comply, it's immediately discarded.Methodology Application:
The solution type determines which primary methodology (Packet Filtering, Proxy Service, or Stateful Inspection) processes the packet.Content Analysis (if applicable):
Some firewalls can scrutinize the content of data packets. They search for specific words or phrases and block the packet if any of those terms appear.Decision Execution:
After the relevant evaluations, the firewall either allows the packet through if it meets all checks or discards it if it fails any.Logging:
The firewall typically maintains a log of its actions. This includes details of accepted and rejected packets, providing administrators with insights into traffic patterns and potential threats.Continuous Rule Update:
Firewalls don't operate on static rules. Based on emerging threats and changing network requirements, administrators regularly update and refine these rules to maintain optimal network security.
The use of firewalls has expanded in recent years with the rise in cyber threats. There are multiple types of firewalls available, including software firewalls, which integrate into different operating systems.
Modern solutions such as NGFWs often work hand in hand with advanced features such as intrusion prevention, antivirus software, deep packet inspection, and more to offer a multi-layered defense strategy.
Firewall Benefits FAQs
Solutions can work at various points within a network depending on their type and the security need:
- Perimeter: Often situated at the edge of a network, this is the main point where data enters or exits the network. It's the primary line of defense against external threats.
- Internal: To further segment and protect different parts of an organization's internal network, firewalls can be placed between different network segments, often in larger or more complex organizational structures.
- Host-based: Installed directly on individual devices (e.g., servers, computers), these control incoming and outgoing traffic specific to that device.
- Cloud-based: For organizations leveraging cloud services, software firewall solutions protect data moving in and out of the cloud environment.
- Serving as gatekeepers that filter network traffic based on defined security rules.
- Analyzing details within data packets, such as origin and content, to determine their safety.
- Employing techniques like stateful packet inspection for thorough traffic analysis.
- Preventing data leakage by monitoring outgoing traffic.
- Supporting network segmentation to enhance security layers.
- Integrating with threat intelligence services to receive updates on current threats.