What Is a Proxy Firewall? | Proxy Firewall Defined & Explained
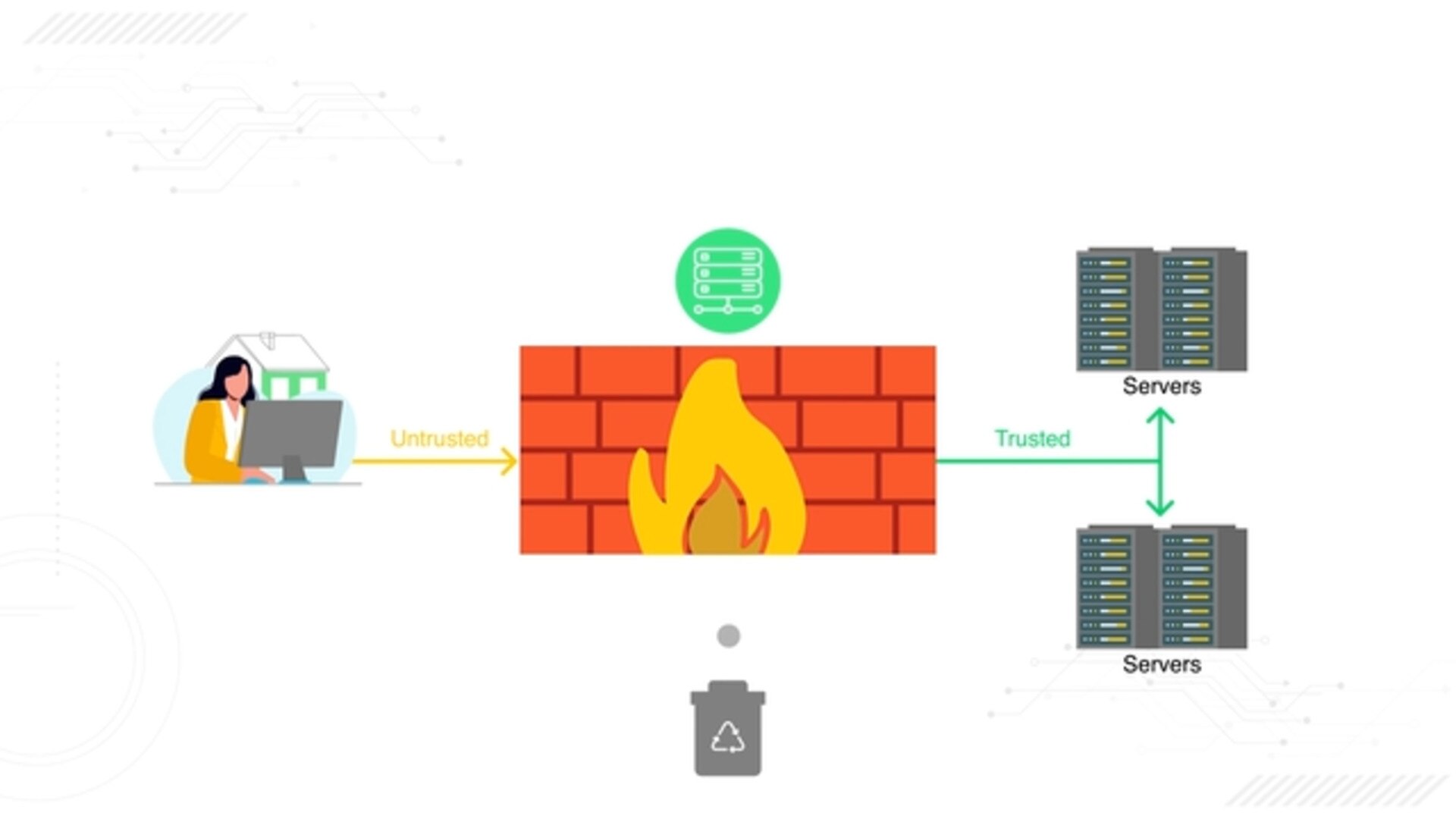
A proxy firewall is a network security device that serves as an intermediary between user requests and the resources they access, filtering messages and data exchange at the application layer.
By evaluating and transferring data packets on behalf of users, a proxy firewall ensures direct connections with external servers are never established, which increases security by concealing internal network addresses. This type of firewall also applies strict rules to control which applications are permitted to transmit data, preventing malicious content from entering the network.
How Do Proxy Firewalls Work?
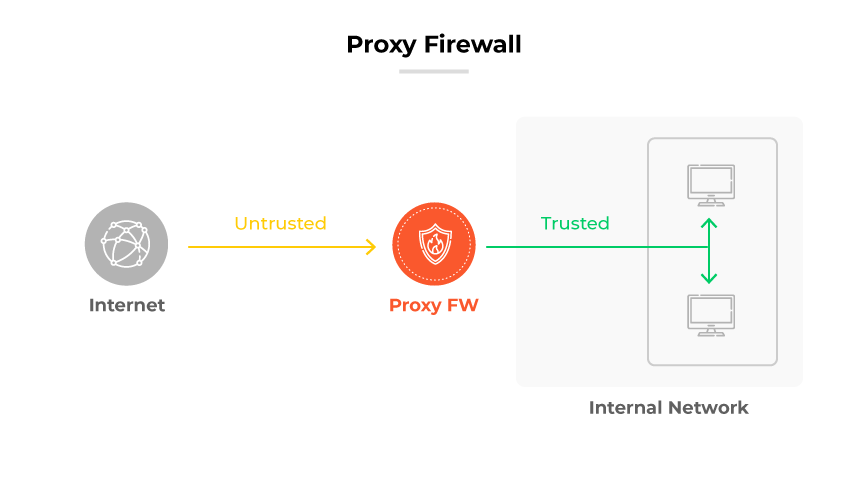
A proxy firewall works by acting as a gatekeeper between an organization's internal network and external services like the public internet. It processes requests by establishing a connection to the requested service on behalf of the user, scrutinizing the traffic for security threats, and ensuring compliance with network policies.
Deep Packet Inspection (DPI) thoroughly examines the contents of incoming data packets to identify and block unauthorized access, enhancing the network's defense against intrusions.
The proxy firewall intercepts internet requests from within the network, evaluates them against the organization's security rules, and if approved, communicates with the target service. The firewall then relays the response back to the original requester, obscuring the internal network's details from the external world.
By preventing direct connections between internal users and external services, the proxy firewall secures the network against unauthorized access and provides a level of anonymity, safeguarding internal internet protocol (IP) addresses. This additional security layer is critical when users access web based services, ensuring only safe, authorized content is relayed back to the internal network.
The proxy firewall's ability to inspect and manage data at the application layer provides defense against sophisticated cyber threats, like malware and phishing attacks. For this reason, it is sometimes referred to as an application firewall. They can also serve as a firewall for servers. Its role is central to enforcing a comprehensive network security system, especially in complex enterprise environments where control over data exchange is paramount.
Proxy firewalls serve additional functions such as caching content to improve load times, compressing data to optimize bandwidth, and even blocking access to specific sites.
Proxy Firewall Features
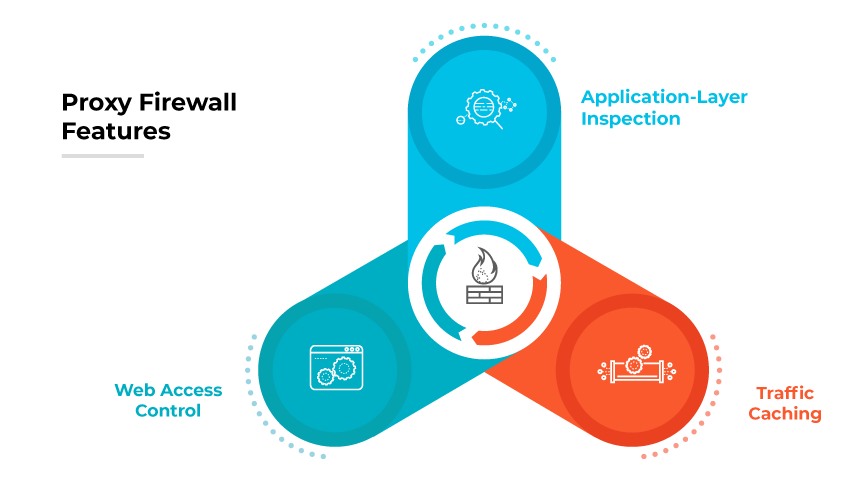
Traffic Caching
Proxy firewalls enhance performance by caching web content, which allows for quicker retrieval of frequently accessed web resources. Caching reduces bandwidth usage and speeds up response time for user requests, resulting in an efficient web browsing experience.
Web Access Control
Proxy firewalls enforce security policies by controlling access to websites. They can block or allow traffic based on URLs or content categories, which helps prevent users from accessing malicious or inappropriate sites and protects the network from web based threats.
Application-Layer Inspection
A proxy firewall examines traffic at the application layer for signs of malicious activity. By inspecting the data being transmitted to and from applications, it ensures only safe and compliant information is allowed through, safeguarding the network against application-layer attacks.
Proxy Firewall Benefits
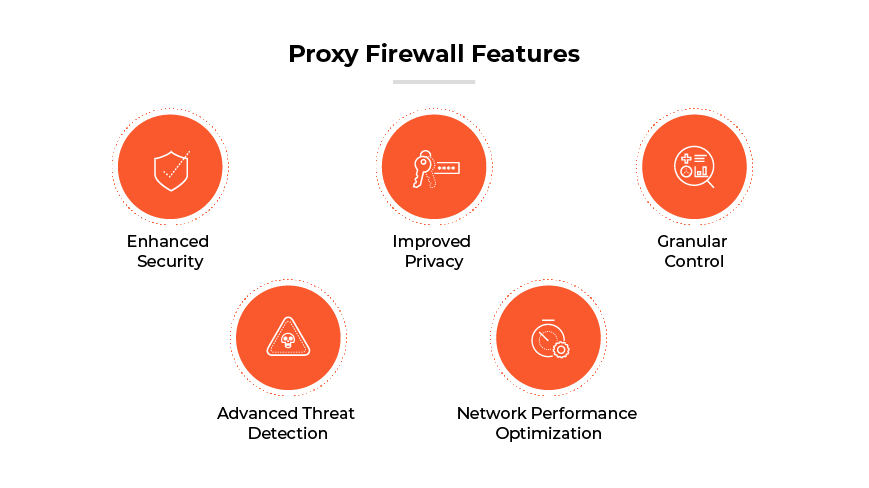
Enhanced Security
A proxy firewall serves as a robust line of defense, screening application data to protect network resources. By mediating data transfer and denying direct external access, it helps prevent security breaches.
Improved Privacy
Proxy firewalls mask internal network details from the outside internet, providing anonymity to user activities and safeguarding against external threats attempting to gather sensitive company information.
Advanced Threat Detection
By evaluating the content of network traffic, proxy firewalls can detect and mitigate sophisticated cyber threats, offering a high level of protection against complex attack vectors.
Granular Control
Proxy firewalls provide detailed control over user access and activities, allowing administrators to enforce security policies at the user level and maintain comprehensive logs for auditing and reporting purposes.
Network Performance Optimization
Proxy firewalls can cache frequently accessed content, optimizing the performance of network resources and streamlining user access to critical applications and data.
Proxy Firewall Challenges
Managing Network Performance
While proxy firewalls are highly secure, they can introduce a bottleneck effect, as each connection is funneled through the proxy, potentially leading to slower traffic flow and network performance issues.
Protocol Limitations
Proxy firewalls may not support every network protocol, which can restrict the range of applications that can be utilized securely within an enterprise network, impacting flexibility in operations.
System Complexity
The intricacies of setting up and managing proxy firewalls can pose challenges, requiring specialized knowledge and sometimes leading to configurations that may inadvertently expose vulnerabilities if not handled correctly.
Possible Single Point of Failure
Due to their centralized nature, if a proxy firewall fails, it can become a single point of failure for network security, underscoring the need for robust failover and redundancy strategies.
Encryption and Privacy Concerns
Proxy servers cache data, which could expose sensitive information if not properly secured. Ensuring end-to-end encryption and the integrity of the data becomes paramount to prevent such risks.
Types of Proxy Firewalls
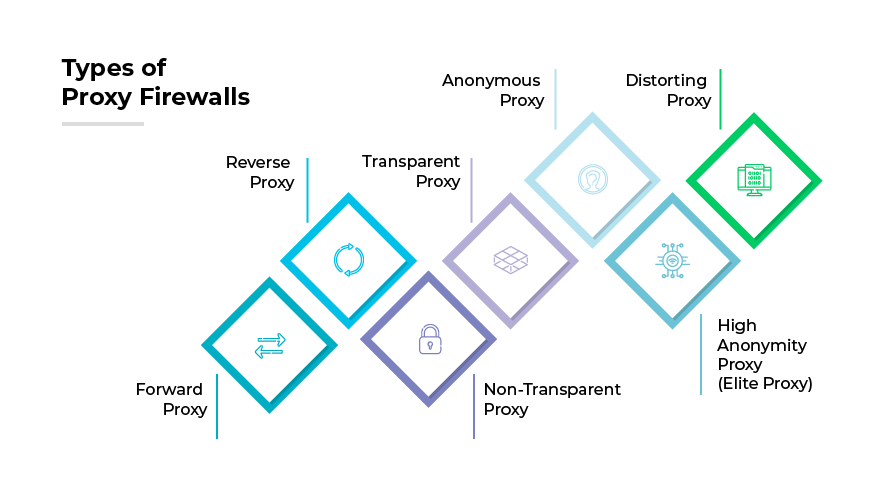
Forward Proxy
Sits between the user's computer and the internet. It is primarily used to facilitate requests from within an internal network to the internet, often providing caching functions and content filtering.
Reverse Proxy
Positioned in front of one or more web servers, intercepting requests from the internet. It's typically used for load balancing, web acceleration, and as an additional security layer.
Transparent Proxy
Also known as an intercepting proxy, inline proxy, or forced proxy, it intercepts normal communication at the network layer without requiring any special client configuration. Users do not need to be aware of the proxy's existence.
Non-Transparent Proxy
Requires configuration on the user's machine (such as browser settings). The proxy is visible to the user and may perform tasks like IP masking and content filtering.
Anonymous Proxy
Hides the user's IP address from the web services being used, making the user's browsing activities untraceable.
High Anonymity Proxy (Elite Proxy)
Unlike an anonymous proxy, which can be detected, a high anonymity proxy does not send the X-Forwarded-For HTTP header, making it difficult or impossible for the destination server to detect the use of a proxy.
Distorting Proxy
Provides an incorrect IP address to the web service, as opposed to hiding or masking it, which can be used for privacy or security reasons.
Types of Firewalls Defined and Explained
Proxy Firewall vs. Other Firewall Types
Proxy Firewall vs. Traditional Firewall
Unlike traditional firewalls, which act as a simple filter between the internal network and the outside world, a proxy firewall evaluates and relays requests. This can provide deeper content inspection and the ability to mask internal IP addresses, offering enhanced privacy and security.
Traditional firewalls typically operate at the network or transport layer, making decisions based on IP addresses and ports. They are designed to block or permit traffic based on a set of defined rules but do not generally inspect the content within the data packets as thoroughly as proxy firewalls do at the application layer. Traditional firewalls provide a fundamental barrier but lack the ability to perform complex content analysis or offer the same level of user specific controls.
Proxy firewalls can offer caching capabilities. Traditional firewalls, focused on access control, do not provide such performance benefits. However, the detailed inspection and processing requirements of proxy firewalls can introduce latency, which may impact network performance, a challenge less commonly associated with traditional firewalls.
Proxy Firewall vs. Packet Filtering Firewall
In depth examination of data packets allows a proxy firewall to identify and block potentially harmful content, offering granular control over network traffic. The distinct advantage is its ability to obscure internal network structures and enhance security protocols by preventing direct communication between internal clients and external servers.
Conversely, a packet filtering firewall functions at a more fundamental level, examining data packets at the network layer based on IP addresses, port numbers, and protocols. This method is less resource intensive and allows for rapid data processing. At the same time, it lacks the capability to perform an in depth analysis of packet content. This can leave a network exposed to sophisticated cyber threats that pass through based on trusted source addresses.
Proxy Firewall vs. Stateful Inspection Firewall
By vetting every data packet at the application level, application proxy firewalls maintain strict control over network traffic, efficiently preventing malicious content from breaching the network.
A stateful inspection firewall adds context to the data packets it filters. By maintaining a dynamic state table of all active connections, this type of firewall can track each session, inspect packet headers, and the continuity and state of the traffic. Since stateful firewalls monitor continuously, they can detect and block packets that may be part of an unauthorized or suspicious data flow, even if the individual packets themselves appear legitimate.
While proxy firewalls excel in their ability to provide deep data inspection and heightened security, stateful inspection firewalls stand out for their ability to understand and remember the state of network connections over time. This fundamental difference in operation means that proxy firewalls are particularly adept at protecting against application-level exploits. On the other hand, because stateful inspection firewalls monitor the state of network traffic, they offer a balance between performance and security.
Proxy vs. Next-Generation Firewall (NGFW)
A proxy firewall ensures no direct contact is made with external servers, which effectively hides the network's internal architecture from external threats.
Next-Generation Firewalls (NGFWs), however, incorporate traditional firewall functions like stateful inspection with advanced features such as integrated intrusion prevention systems, application awareness, and control. NGFWs are equipped to block sophisticated threats through their ability to inspect the payload of packets, use threat intelligence, and adapt to new security challenges. They are designed to enforce policies and understand and adapt to the flow of applications.
While proxy firewalls provide a strong security layer, NGFWs offer a broader, more adaptive approach to network security.
Comparing Proxy Firewalls with Other Security Technologies
Proxy Firewalls vs. Proxy Servers
Proxy firewalls and proxy servers both act as intermediaries in the flow of internet traffic, but they serve different purposes within a network.
A proxy firewall filters traffic at the application layer. Its primary function is to prevent direct connections to the internal network, enhancing security by controlling and auditing the data that enters and leaves.
Conversely, a proxy server primarily acts as an intermediary for requests from clients seeking resources from other servers. It facilitates various functionalities such as web request handling, data caching to speed up frequent requests, and IP address masking for privacy. It can provide a basic level of security by hiding the internal network's IP address from the external network. However, its main role is not to enforce security policies but to streamline and manage web traffic.
Proxy Firewalls vs. Application-Level Gateways
An Application-Level Gateway can be a form of a forward proxy firewall, but it specifically operates at the application layer of the OSI model. It filters incoming and outgoing traffic to a network, providing security, filtering, and content translation at the application protocol level.
A forward proxy typically acts as an intermediary for clients within an internal network when they make requests to external servers on the Internet, managing outbound traffic. An Application-Level Gateway has this capability but also inspects traffic more deeply at the application protocol level, enforcing security policies and potentially modifying traffic as it passes through.
All Application-Level Gateways can function as forward proxies, but not all forward proxies provide the same level of deep inspection and protocol-specific functionalities that an Application-Level Gateway does.