-
- MITRE ATT&CK Framework Explained
- Structuring Adversary Behavior by Tactic
- MITRE ATT&CK Tactics and Their Role in Security Intelligence
- MITRE ATT&CK Techniques
- MITRE ATT&CK Use Cases
- Using the MITRE ATT&CK Framework during a Live Attack
- Comparing MITRE ATT&CK and the Cyber Kill Chain
- Advancing Organizational Maturity with ATT&CK
- Toward a Behavioral Framework for Securing AI
- MITRE ATT&CK Framework FAQs
Table of Contents
- How Do I Implement MITRE ATT&CK Techniques?
-
What is the MITRE ATT&CK Matrix?
- MITRE ATT&CK Matrix Explained
- Key Components of MITRE ATT&CK: Tactics, Techniques, and Procedures
- Diverse MITRE ATT&CK Matrices: Adapting to Specific Environments
- How Organizations Operationalize MITRE ATT&CK
- Implementing and Maintaining a MITRE ATT&CK Program
- Benefits of Leveraging the MITRE ATT&CK Framework
- Common Challenges and Solutions
- MITRE ATT&CK and the Cybersecurity Landscape
- MITRE ATT&CK Matrix FAQs
-
What Are MITRE ATT&CK Techniques?
- MITRE ATT&CK Techniques Explained
- The Anatomy of a MITRE ATT&CK Technique
- Understanding Common and Emerging ATT&CK Techniques
- Detecting and Mitigating MITRE ATT&CK Techniques
- Leveraging ATT&CK Techniques for Enhanced Security Operations
- The Future Evolution of ATT&CK Techniques
- MITRE ATT&CK Techniques FAQs
-
How Has MITRE ATT&CK Evolved?
- Evolution of MITRE ATT&CK Explained
- The Historical Trajectory of MITRE ATT&CK
- Why TTPs Matter: Shifting the Cybersecurity Paradigm
- Key Milestones in ATT&CK's Expansion and Refinement
- Core Components and Their Evolving Definition
- Why the Evolution Matters: Benefits for Cybersecurity Professionals
- Addressing the Evolving Threat Landscape with ATT&CK
- Operationalizing the Framework: Practical Applications and Challenges
- The Future of MITRE ATT&CK
- Evolution of MITRE ATT&CK FAQs
- What Are MITRE ATT&CK Use Cases?
- A CISO's Guide to MITRE ATT&CK
- How Does MITRE ATT&CK Apply to Different Technologies?
-
What is the Difference Between MITRE ATT&CK Sub-Techniques and Procedures?
- Understanding the MITRE ATT&CK Framework
- Exploring Sub-Techniques in the ATT&CK Framework
- Exploring Procedures in the ATT&CK Framework
- The Role of Sub-Techniques in Cybersecurity Strategies
- Procedures as a Tool for Detailed Threat Analysis
- Continuous Evolution: Staying Updated with ATT&CK Framework
- MITRE ATT&CK Sub-Techniques vs. Procedures FAQs
What Is MITRE ATT&CK Framework?
6 min. read
Table of Contents
The MITRE ATT&CK framework is a knowledge base of adversary tactics and techniques, derived from real-world observations, used to map, detect, and mitigate post-compromise behavior across enterprise, cloud, mobile, and industrial control system environments.
MITRE ATT&CK Framework Explained
The MITRE ATT&CK framework is a globally accessible knowledge base of adversary behavior, maintained by MITRE Corporation and grounded in real-world observations. It organizes cyber attack techniques by tactics — each representing a stage in an adversary’s objective, such as Initial Access, Privilege Escalation, or Exfiltration. Each technique is mapped to procedures, detection opportunities, and mitigations.
ATT&CK allows defenders to model threats based on how adversaries operate p]ost-compromise rather than focusing solely on signatures or indicators. The framework supports cyber threat intelligence analysis, red teaming, defensive gap assessments, and control validation across enterprise, cloud, mobile, and ICS environments.
What sets MITRE ATT&CK apart is its emphasis on behavior versus tooling. It tracks what attackers do, as well as how they do it. By aligning defenses with the tactics and techniques defined in ATT&CK, organizations can build detection strategies with resilience to evolving tools and emerging threat actors.
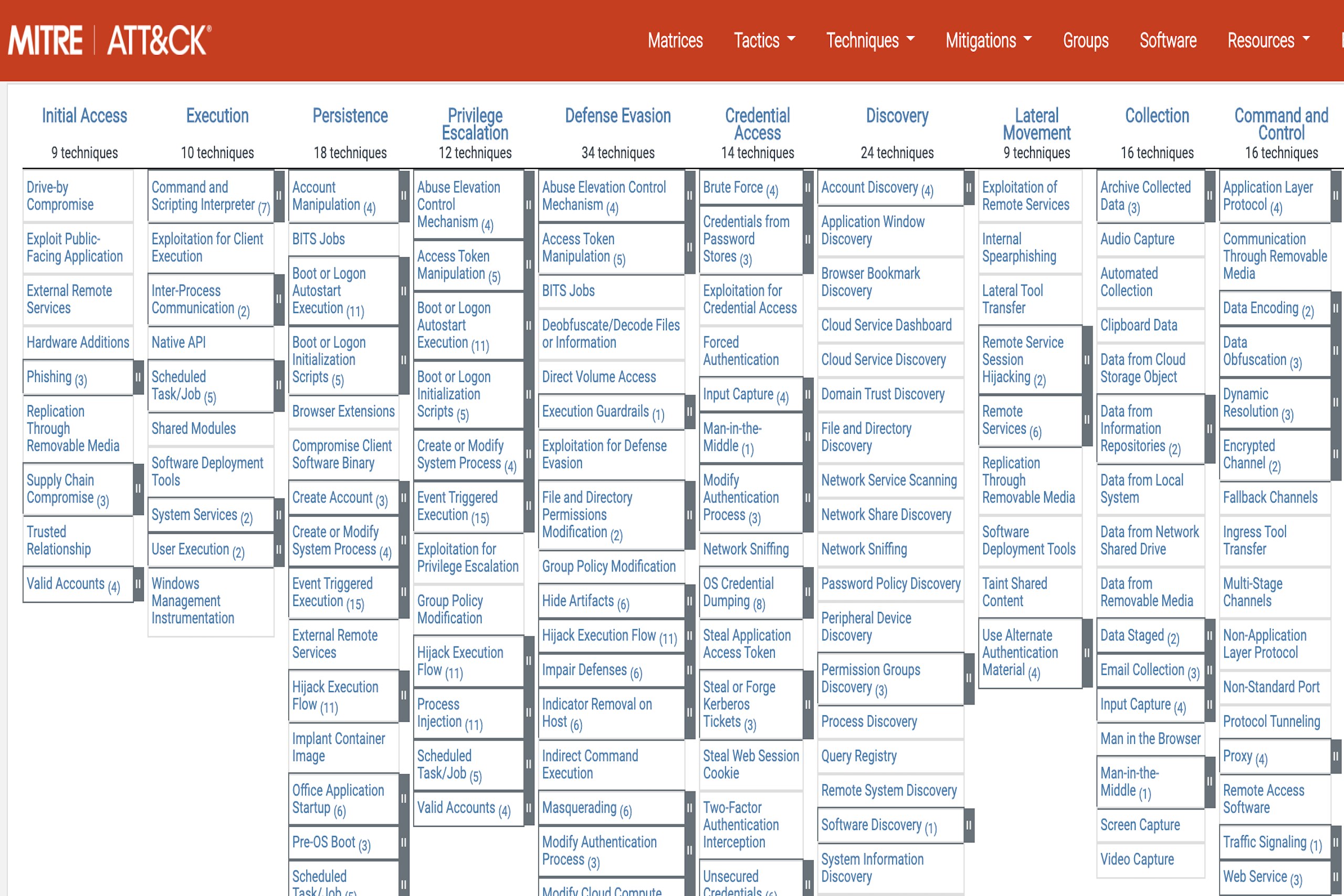
Structuring Adversary Behavior by Tactic
Each MITRE ATT&CK Matrix organizes adversary behavior into a visual structure based on tactics and techniques. Tactics are the columns, which represent an attacker’s objective at each phase of an intrusion. MITRE techniques are the cells beneath them, specific actions used to achieve the objective. Some techniques also include subtechniques, which offer more granular detail on variations of a given behavior.
The matrices are dynamic, updated regularly by MITRE ATT&CK to reflect newly observed adversary tradecraft across platforms and industries. Each matrix is tailored to a domain: Enterprise, Mobile, Cloud, Containers, or ICS.
Enterprise Matrix
The Enterprise matrix covers behaviors across Windows, macOS, Linux, Azure AD, SaaS, and other platforms. It spans 14 core tactics, from Initial Access to Impact. Each tactic contains multiple techniques. For example, Execution includes T1059: Command and Scripting Interpreter, a commonly used method for running malicious code on endpoints.
Enterprise is the most widely adopted matrix, forming the foundation for detection engineering, threat modeling, and red/blue team exercises across security programs.
Cloud Matrix
The Cloud matrix extends ATT&CK to cloud-native environments. It includes tactics tailored to identity federation, API abuse, and tenant manipulation. Techniques like T1078.004: Valid Accounts – Cloud Accounts and T1562.008: Impair Defenses – Disable or Modify Cloud Logging reflect how attackers exploit SaaS misconfigurations and cloud control plane weaknesses.
Many organizations integrate the Cloud matrix into detection rules for platforms like AWS CloudTrail, Azure Monitor, and Google Cloud Audit Logs.
Mobile Matrix
The Mobile matrix focuses on iOS and Android-specific attack vectors. Tactics here include Initial Access, Collection, and Exfiltration, adapted to reflect mobile OS design. Techniques include mobile-specific behaviors such as T1406: Credential Access via Keylogging and T1450: Application Layer Protocol.
Mobile threats remain under-monitored in many organizations, making this matrix critical for visibility into employee-owned and BYOD environments.
ICS Matrix
Designed for industrial control systems (ICS), the ICS matrix includes tactics like Inhibit Response Function, Manipulation of Control, and Impair Process Control. These reflect the physical outcomes attackers pursue in environments such as energy, manufacturing, and water treatment.
The ICS matrix draws from unique adversary behavior, including techniques observed in campaigns like Triton and Industroyer, where attackers sought to disrupt or destroy physical processes.
Tactic |
Enterprise |
Cloud |
Mobile |
ICS |
Reconnaissance |
X |
|
|
|
Resource Development |
X |
|
|
|
Initial Access |
X |
X |
X |
X |
Execution |
X |
X |
X |
X |
Persistence |
X |
X |
X |
X |
Privilege Escalation |
X |
X |
X |
X |
Defense Evasion |
X |
X |
X |
|
Credential Access |
X |
X |
X |
|
Discovery |
X |
X |
X |
X |
Lateral Movement |
X |
X |
X |
X |
Collection |
X |
X |
X |
X |
Command and Control |
X |
X |
X |
X |
Exfiltration |
X |
X |
X |
|
Inhibit Response Function |
|
|
|
X |
Impair Process Control |
|
|
|
X |
Impact |
X |
X |
|
X |
Evasion |
|
|
|
X |
Table 1: MITRE ATT&CK tactic coverage by matrix
How Matrices Drive Threat-Informed Defense
Matrices serve as structured maps of known behavior. They inform detection coverage audits, highlight control gaps, and enable SOCs to prioritize alerts by adversary intent. Security teams use matrices to build detection logic, design simulation exercises, and communicate threats in a standardized language aligned with adversary behavior.
MITRE ATT&CK sharpens detection tools, giving every alert a tactical context, which then turns data into decisions.
MITRE ATT&CK Tactics and Their Role in Security Intelligence
In the MITRE ATT&CK framework, tactics represent the why behind adversary actions — their tactical goals within the kill chain. Each tactic defines a discrete phase of an attack, such as gaining initial access, escalating privileges, or exfiltrating data. There are 14 tactics in the Enterprise matrix, beginning with Reconnaissance and ending with Impact.
Tactics provide structure to raw telemetry. When mapped to adversary behavior, they contextualize what a detected action is trying to achieve. That allows defenders to assess not only what occurred, but where they’re in the adversary lifecycle and what comes next.
From Raw Signals to Tactical Awareness
Security operations teams often drown in alerts that lack hierarchy or intent. By aligning detections to ATT&CK tactics, analysts can group telemetry into functional stages of an intrusion.
For example, failed login attempts from an unusual source may map to Initial Access, while the creation of a new admin account aligns with Privilege Escalation. If followed by a file transfer to an external domain, it may indicate Exfiltration. Each mapping tells a story — and each story points to how close the attacker is to achieving their goal.
Tactic-based detection doesn't just enrich alerts. It strengthens response prioritization. An alert mapped to Command and Control deserves more scrutiny than one stuck in Reconnaissance. Context allows teams to focus where adversary progress is most dangerous.
Operational Benefits Across the Security Stack
- Threat hunting becomes more structured when tactics guide hypotheses. Hunters can focus on verifying if specific objectives have been attempted, like lateral movement across departments.
- Detection engineering becomes more resilient when mapped to tactics instead of signatures. If a new tool is used for data staging, but it behaves similarly to known techniques, the tactic-based detection still applies.
- Red teaming becomes more impactful when emulated activity aligns with known tactics used by real threat actors, allowing defenders to evaluate detection and response per objective, not per tool.
- Threat intelligence becomes more actionable when indicators are enriched with tactic tags. Knowing a hash belongs to a tool used during Persistence changes how it's triaged and blocked.
Tactics turn data into decisions. They give every behavior a role and every signal a purpose.
Building Intelligence Around the Adversary's Objectives
Tactical awareness transforms security from event-driven to adversary-driven. Instead of reacting to symptoms, teams operate with insight into attacker intent. Insider knowledge informs everything from SIEM rule tuning to tabletop exercises and executive reporting.
When organizations track their detection coverage by tactic, they understand their exposure by adversary objective.
MITRE ATT&CK Techniques
In the MITRE ATT&CK framework, techniques describe how adversaries achieve tactical objectives. Each technique represents a specific method used to carry out a phase of the attack. Techniques are nested under the tactics they serve. For example, under the Execution tactic, Command and Scripting Interpreter (T1059) represents an adversary’s use of scripting environments to run payloads on a system.
Every technique is documented with examples, detection guidance, and potential mitigations. Many techniques also include sub-techniques, which provide more granular insight into variations on the method. Sub-techniques help organizations tune defenses precisely and build detections that account for diverse implementations of the same adversarial intent.
Operationalizing Technique-Level Intelligence
Techniques are the building blocks of behavior-based detection. By mapping alerts or observed activity to techniques, defenders can shift from indicator-driven analysis to adversary-informed investigation.
A single technique may manifest in many ways. Valid Accounts (T1078), used under multiple tactics like Initial Access or Persistence, can appear as a successful login from an unusual geography, a token refresh from a known user agent, or a new session for a service account. Mapping all these back to the same technique enables broader detection coverage without relying on static IoCs.
Technique Prioritization Based on Threat Landscape
Not all techniques carry equal weight. Prioritization depends on factors like industry threat profile, existing visibility gaps, and adversary alignment.
Organizations often use:
- Historical incident data to map which techniques were used in past compromises
- Threat intelligence reports that attribute techniques to known threat actors
- Control coverage assessments that highlight where detection or prevention is weak
- MITRE’s own D3FEND and CAPEC models to connect techniques to countermeasures and exploit patterns
Mapping internal telemetry against high-priority techniques gives teams a focused, threat-informed view of their exposure.
Linking Techniques to Real Threat Actor Behavior
Each technique page in ATT&CK includes references to groups that have used the method, such as APT29’s use of Spearphishing Attachment (T1566.001) or FIN7’s use of Scheduled Task/Job (T1053). The connection between tactics, techniques, and actors allows defenders to build threat models based on real campaigns rather than hypothetical attack chains.
When organizations map incidents to techniques and correlate them with actor profiles, they gain the ability to predict what actions are likely next in an attack and to prioritize defenses accordingly.
MITRE ATT&CK techniques turn logs into narratives. They enable defenders to understand not just that something happened, but why it happened, how it was done, and what’s likely to follow. That behavioral clarity is what makes the framework operationally valuable at every layer of the security stack.
MITRE ATT&CK Use Cases
Detection Engineering
The MITRE ATT&CK framework enables security teams to design detections around behavior, not tools. By mapping detections to specific techniques, analysts can write rules that detect adversarial activity regardless of the toolset. Taking this approach future-proofs detection logic, allowing SOCs to catch unknown variants of known behaviors.
Techniques also guide coverage assessments. Teams can identify which techniques are already detected and which lack visibility, helping them prioritize sensor deployment, log enrichment, or new detection rules based on tactical risk.
Threat Hunting
Hunting teams use MITRE ATT&CK to focus hypotheses. Instead of relying on broad anomaly detection, hunters align their queries to high-priority techniques observed in relevant campaigns. A team may explore variations of Lateral Tool Transfer (T1570) or Remote System Discovery (T1018) to find activity suggesting an adversary is moving laterally.
Because each technique includes example procedures, data sources, and detection recommendations, ATT&CK provides a starting point for crafting hunts with operational focus.
Threat Intelligence Mapping
ATT&CK creates a shared language for expressing adversary behavior. Cyber threat intelligence teams enrich reports by tagging tactics and techniques used by threat groups. Instead of vague references to “malicious PowerShell,” intelligence products specify T1059.001, tying observed behavior directly to MITRE ATT&CK’s standardized taxonomy.
This structure allows faster triage. When a new report mentions a technique your organization already detects, you can validate coverage immediately. When it surfaces a gap, you can respond with targeted action.
Red Teaming and Purple Teaming
ATT&CK helps red teams emulate adversaries more accurately. Rather than relying on generic scripts, they build campaigns aligned to known actors using the same techniques, mapped across tactics. A red team simulating APT29, for example, might execute Spearphishing Attachment (T1566.001) for access and Scheduled Task/Job (T1053) for persistence.
Purple teams use the same mapping to validate controls. They track detection efficacy by technique and identify which alerts were blocked, missed, or misclassified. MITRE ATT&CK becomes the blueprint for adversary simulation and response validation.
Security Gap Assessment
Organizations use the MITRE ATT&CK framework to conduct defensive coverage audits. By mapping existing detections and telemetry to ATT&CK techniques, they can visualize which behaviors are detected, which are monitored passively, and which are blind spots. These assessments often drive decisions around logging scope, EDR coverage, SIEM correlation, and budget allocation.
Tools like MITRE ATT&CK Navigator allow organizations to visualize these gaps and overlay them with threat actor profiles, helping prioritize based on both capability and likelihood.
Executive Reporting and Risk Communication
Because MITRE ATT&CK abstracts behaviors into tactics and techniques, it offers a language that connects technical detail to executive-level risk. Security leaders can report on how their organization detects Credential Access or Exfiltration rather than listing raw event counts.
This alignment helps CISOs communicate detection maturity, justify investment, and benchmark capability over time. ATT&CK provides the structure to translate detection engineering into operational and strategic insight.
When ATT&CK is embedded across detection, response, intelligence, and reporting, it becomes more than a framework. It becomes the shared operating system for threat-informed defense.
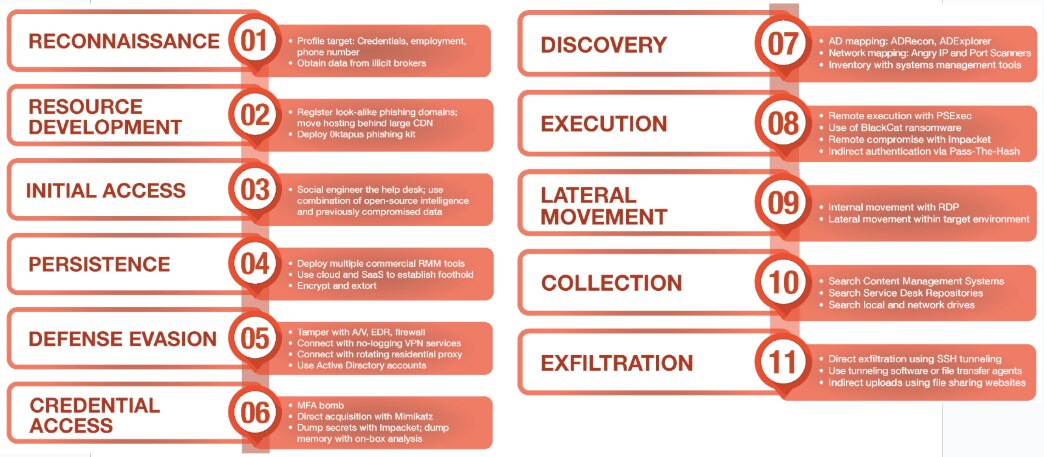
Using the MITRE ATT&CK Framework during a Live Attack
Behavior Over Time: Mapping an Intrusion to ATT&CK
The real value of the MITRE ATT&CK framework emerges during an active intrusion. Security teams are equipped to interpret adversary behavior in sequence and map each move to a tactic and technique. Mapping of course turns fragmented telemetry into a structured timeline of intent, progress, and exposure.
The example below walks through a simplified but realistic attack scenario, showing how ATT&CK techniques surface across the intrusion lifecycle. Each step illustrates how defenders use the framework to identify, contextualize, and counter specific adversary actions.
ATT&CK in Action: Step-by-Step Intrusion Mapping
Initial Access
A phishing email arrives with a malicious Excel file containing embedded macros.
Mapped to: T1566.001: Spearphishing Attachment
Execution
Once opened, the file executes an obfuscated PowerShell payload.
Mapped to: T1059.001: PowerShell
Persistence
The payload establishes long-term access by registering a scheduled task.
Mapped to: T1053.005: Scheduled Task
Privilege Escalation
The attacker impersonates a local admin token to bypass user restrictions.
Mapped to: T1134.001: Token Impersonation/Theft
Defense Evasion
Windows event logs are cleared, and tamper protection on the EDR agent is disabled.
Mapped to: T1070.001: Clear Windows Event Logs
Mapped to: T1562.001: Disable or Modify Tools
Credential Access
Memory scraping tools target the LSASS process to harvest credentials.
Mapped to: T1003.001: LSASS Memory
Lateral Movement
The attacker uses RDP and stolen credentials to move to a finance department workstation.
Mapped to: T1021.001: Remote Desktop Protocol
Collection
Documents tagged “invoice,” “ACH,” and “wire” are aggregated and zipped.
Mapped to: T1560.001: Archive Collected Data: Local Archiving
Exfiltration
Files are transferred over an HTTPS session to attacker-controlled infrastructure.
Mapped to: T1048.002: Exfiltration Over Asymmetric Encrypted Non-C2 Protocol
Impact
Ransomware is deployed as a final-stage distraction and coercion mechanism.
Mapped to: T1486: Data Encrypted for Impact
Team-Specific Engagement Across the Framework
While the attack unfolds, different teams engage with MITRE ATT&CK through different lenses:
- SOC analysts triage alerts by tactic, accelerating escalation when alerts transition from Execution to Lateral Movement.
- Detection engineers correlate behaviors across users and hosts, improving coverage of linked techniques like Credential Dumping and Remote System Discovery.
- Threat hunters develop hypotheses based on common technique chains seen in similar actor profiles.
- Incident responders reconstruct the intrusion path by mapping observed telemetry to tactics and sub-techniques.
- Executives receive incident briefings anchored in standardized, adversary-centric language, reducing guesswork and elevating clarity.
The MITRE ATT&CK framework isn’t just a postmortem taxonomy. It’s a live system for understanding where an adversary is in their campaign, how they’re operating, and where your defenses must adapt next. It moves teams from event collection to adversary alignment. In a live incident, that shift is the difference between chasing alerts and stopping attacks.
Comparing MITRE ATT&CK and the Cyber Kill Chain
The Cyber Kill Chain and MITRE ATT&CK both model adversary behavior, but they serve different functions and reflect different levels of operational granularity. The Kill Chain, developed by Lockheed Martin, offers a high-level view of attacker progression from initial reconnaissance to execution of objectives. MITRE ATT&CK operates at a much deeper layer, mapping the specific techniques adversaries use within and across those stages.
The Cyber Kill Chain’s seven stages — Reconnaissance, Weaponization, Delivery, Exploitation, Installation, Command and Control, and Actions on Objectives — are linear. It’s a useful narrative structure, especially for early-stage incident response and high-level education. MITRE ATT&CK, in contrast, isn’t linear. It’s tactic-driven and maps techniques across overlapping or repeating objectives like Persistence, Credential Access, or Exfiltration. Its inherent flexibility better reflects real-world intrusion complexity.
Granularity and Operational Value
Where the Kill Chain describes what phase an attacker is in, ATT&CK describes how that activity is being executed. For example, Kill Chain might identify the Installation phase. ATT&CK would detail whether the adversary used T1053: Scheduled Task or T1547.001: Registry Run Keys to persist.
MITRE ATT&CK also tracks sub-techniques, allowing defenders to tune detections for specific procedures within a broader tactic. Utilizing the level of detail enables more precise detection logic, more effective threat hunting, and more accurate simulation during red and purple team operations.
Kill Chain is more static. It doesn’t adapt as easily to multicloud, hybrid, or identity-centric attacks, where lateral movement and privilege escalation don’t follow predictable paths. ATT&CK’s matrix structure, by contrast, accommodates dynamic attacker behavior across systems and platforms.
Use Case Alignment
The Kill Chain is ideal for communicating high-level attack flow in executive briefings or early-stage planning. It helps organizations establish a general understanding of adversary progression and supports the design of layered defenses that block attacks at each stage.
ATT&CK is tactical and technical. It’s used by SOC teams, threat hunters, and detection engineers to build and evaluate defenses around specific behaviors. It supports control validation, logging strategy, threat modeling, and response prioritization.
Many mature organizations use both. They use Kill Chain to explain and frame, and ATT&CK to operationalize and act. Together, they offer strategic alignment and technical precision. When precision matters, though, MITRE ATT&CK carries the weight.
Advancing Organizational Maturity with ATT&CK
Most security programs encounter the MITRE ATT&CK framework early, often during detection tuning or threat intelligence tagging. Its value, however, emerges when ATT&CK moves from reference to backbone. Mature organizations treat it as more than a matrix of adversary behavior. They use it to align detection strategy, measure defensive performance, and drive coordinated response across teams.
ATT&CK adoption often begins with coverage analysis and detection engineering. From there, it progresses to threat-informed defense, simulation planning, and metrics-driven decision-making. Organizations that mature their use of ATT&CK develop a continuous feedback loop between adversary behavior, control visibility, and operational readiness.
Tailoring ATT&CK to the Environment
No two environments have the same threat surface. MITRE ATT&CK offers flexibility across platforms — Windows, Linux, macOS, cloud, SaaS, containers, mobile, and ICS — but operationalizing that coverage requires mapping it to your architecture and telemetry.
Identity infrastructure, for example, is rich with ATT&CK-relevant techniques but often under-monitored. Techniques like T1078.004: Valid Accounts – Cloud Accounts or T1556.006: Modify Authentication Process – Cloud IAM demand cloud-native detection coverage that traditional tools miss.
Organizations using SaaS platforms like Microsoft 365 or Google Workspace often overlook tactics such as Persistence and Collection, assuming those environments are inherently secure. ATT&CK exposes gaps by anchoring detection efforts in adversary behaviors rather than vendor guarantees.
Visibility across the matrix should be platform-aware. A mature program understands which tactics are relevant to each domain and prioritizes accordingly.
Scaling ATT&CK Use Across Teams
Security teams gain the most from MITRE ATT&CK when it becomes a shared operating model across functions. That means:
- Detection engineers using technique IDs to standardize and version-control rules
- Threat intel analysts tagging actor behavior to ATT&CK to support prioritization
- Incident responders tracing intrusions across tactics to reconstruct kill chains
- Red teams building scenarios aligned to real adversary tradecraft
- Blue teams measuring response times against high-risk techniques
The convergence builds institutional memory. ATT&CK creates a common vocabulary that connects detection logic with strategic threat models and live operational decisions.
Benchmarking and Metrics for ATT&CK Adoption
Mature organizations measure with ATT&CK. Coverage heat maps become part of board reporting. Simulation outcomes are tied to specific techniques. Detection logic is tested not just for alert generation but for adversary interruption at each tactical stage.
Key maturity indicators include:
- Percent of high-priority techniques mapped to active detections
- Detection-to-response time per tactic
- Frequency of ATT&CK-aligned red and purple team exercises
- Breadth of MITRE ATT&CK technique references in IR case retrospectives
By tying operational metrics to adversary behavior, organizations can calibrate investment, reduce alert noise, and focus on the techniques that actually matter in their threat landscape.
Toward a Behavioral Framework for Securing AI
As adversaries adopt artificial intelligence and target machine learning systems, the need for a structured, behavioral understanding of AI-specific threats becomes urgent. MITRE’s Sensible Regulatory Framework for AI Security represents a forward-looking counterpart to the ATT&CK Framework, grounded in the same philosophy: that effective defense begins with clearly defined, observable threat behaviors.
While ATT&CK maps how human adversaries act post-compromise, the AI framework anticipates how threat actors may exploit the unique properties of learning systems. Both frameworks aim to give defenders a shared vocabulary and a strategic lens. In time, as AI becomes more deeply integrated into enterprise infrastructure and attacker playbooks, the principles underpinning MITRE ATT&CK will likely shape how organizations detect, mitigate, and govern AI threats at scale.
MITRE ATT&CK Framework FAQs
MITRE D3FEND is a complementary knowledge base to ATT&CK, focused on defensive techniques. While ATT&CK catalogs how adversaries operate, D3FEND maps countermeasures, such as hardening, detection, and deception techniques, to specific MITRE ATT&CK techniques. It helps defenders evaluate whether their controls mitigate or detect known adversary behaviors, creating a more structured link between offensive behaviors and defensive architecture.
A sub-technique is a more detailed, specific implementation of a broader ATT&CK technique. For example, T1059: Command and Scripting Interpreter includes sub-techniques like PowerShell (T1059.001) and Bash (T1059.004). Sub-techniques allow defenders to tailor detections and mitigations to the exact procedure used, enabling finer-grained analytics and a deeper understanding of adversary tradecraft.
ATT&CK Navigator is a web-based tool developed by MITRE that allows security teams to visually explore and annotate the ATT&CK matrices. It enables users to map detections, threat actor techniques, and coverage across tactics. Teams often use Navigator to track control coverage, plan red teaming exercises, and prioritize gaps based on adversary behavior.
An ATT&CK technique ID is a unique identifier assigned to every technique and sub-technique in the framework. These IDs, such as T1021 or T1059.003, ensure consistency in detection engineering, intelligence reporting, and red team planning. Referencing IDs standardizes communication across tools, teams, and reports.
MITRE Engage is a framework focused on adversary engagement and cyber deception. Unlike ATT&CK, which documents adversary behavior, Engage provides structured guidance for using deception — such as honeypots, misdirection, and adversary interaction — to disrupt and observe intrusions. It aligns closely with ATT&CK tactics to guide proactive defense beyond detection and response.
MITRE ATT&CK catalogs adversary behavior post-compromise, focusing on tactics and techniques. CVE (Common Vulnerabilities and Exposures), also maintained by MITRE, is a standardized list of known software vulnerabilities. CVE is about exploitable flaws in code. ATT&CK is about what an attacker does once they have access. Together, they describe both how attackers get in and how they operate once inside.
PRE-ATT&CK was a matrix designed to capture adversary behavior before gaining initial access — such as reconnaissance and target selection. In 2020, MITRE deprecated PRE-ATT&CK and merged relevant behaviors into the Enterprise matrix to better reflect continuous, multiphase intrusions. Many of its concepts now appear under tactics like Reconnaissance and Resource Development.
