Having pivoted away from traditional monolithic application models, today’s DevOps teams routinely leverage technologies like containers and serverless architectures to build microservices-based applications distributed across vast ecosystems.
Following up on our recent blog post where we touched on code-to-cloud remediation as part of new features in the Prisma Cloud Darwin release, we'd like to delve deeper into remediation. First, let's look at the challenges of risk remediation in cloud security.
Challenges in Modern Security
The evolution of the app, with its many gains, remains a double-edged sword. Widespread use of open-source libraries and the proliferation of application components has broadened the attack surface. Security teams race to keep pace with swift deployments while DevOps teams, in their drive for rapid deployment, often view security and InfoSec as obstacles. Compounding these challenges, the tools designed to safeguard modern architectures often fall short.
The Industry's Incomplete Response
Security vendors have responded with purpose-built solutions that address only parts of the security problem. While many tools, for instance, provide insights based on risk factors from CVE, CVSS, and NVD, they lack the context of an organization’s specific environment. Key questions remain unanswered:
- Are there misconfigurations in the cloud that could amplify exploitation risks?
- Is the vulnerability exposed to the internet through the network?
- What permissions do vulnerable machines or containers have?
The market is flooded with tools, each addressing only a subset of use cases. Traditional tools might focus on hosts or virtual machines running inside clouds, while others scan for vulnerabilities in open-source software within code repositories. This fragmented approach lacks cohesion. If a critical vulnerability spreads across thousands of instances, these tools falter, unable to trace the issue back to its origin in the developer environments.
These limitations pose significant challenges for security teams, who require about 145 hours to resolve a security alert1 — in stark contrast to adversaries who need only 15 minutes to exploit a new vulnerability.2
The industry’s solution to the security problem has been to shift left. But the industry has fallen short in offering solutions that teams find challenging to operationalize due to blind spots and interoperability issues. Purpose-built tools don't cater to the needs of either the DevOps or the security teams and, in fact, deepen the divide between them.
Video: Learn how to remediate misconfigurations, first in code and then in the cloud.
Facilitating DevSecOps
DevSecOps, as we know, offers an optimal scenario for security and DevOps teams. In this framework, security teams gain complete visibility into all applications and their components throughout the code, build, deploy, and run phases.
In its platform approach to secure cloud-native applications, Prisma Cloud leads the way in enabling enterprises to integrate security throughout the application lifecycle. The Prisma Cloud platform equips DevOps teams with the tools to take responsibility for security before deploying code. By facilitating DevSecOps, Prisma Cloud bridges the gap, helping both teams to meet their goals.
Unveiling Prisma Cloud
Prisma Cloud offers a uniquely comprehensive CNAPP that fosters DevSecOps by giving teams a clear view of application components, from the code phase — including libraries, packages, dependencies, and IaC templates — right through to the runtime phase, encompassing running hosts, containers, and services.
Surfacing critical security weaknesses, the platform then correlates findings back to the flaws in development code, enabling teams to easily fix issues at the source, preventing future insecure deployments.
Seamless Integration with Developer Tools
The shift left principle comes into play by identifying security issues early in the code, build, and deploy phases. Prisma Cloud stands out by offering seamless, out-of-the-box integrations with popular tools developers rely on, such as IDEs, code repositories, container registries, and CI/CD pipelines.
By embedding security checks into familiar developer tools like VSCode, GitRepos, and container and serverless registries, DevOps teams can spot and address security concerns right from their familiar environments, even before deploying applications. The capacity to identify and rectify issues during runtime has become a proven weapon in the DevSecOps arsenal, ensuring the deployment of secure applications and preventing potential breaches.
Key Features of Prisma Cloud
Prisma Cloud ensures that security isn't an afterthought but an integral part of enterprise processes. Among standout features introduced in the Darwin release is the code-to-cloud traceback capability, which offers users a visual map of all application artifacts from code to cloud. With code-to-cloud traceback, users can precisely identify and address artifacts throughout the application lifecycle.
Another notable feature, drift detection identifies local changes that deviate from the intended final state — whether these changes were made during the code, build, deploy, or run phases. As teams know, early drift detection ensures timely remediation.
Additionally, the platform empowers teams to fix alerts, incidents, and findings in the code or in the cloud. This dual capability ensures you can both prevent issues in the code phase and address the repercussions of these issues during the run phase.
Operationalizing Security with Prisma Cloud
Prisma Cloud empowers DevSecOps teams to collaborate, ensuring security is integrated throughout the code, build, deploy, and run phase.
Runtime Phase
In the runtime phase, teams should deploy agents to safeguard applications and their associated microservices. By doing so, they can achieve a holistic view of all compliance violations and vulnerabilities at the application level via the Prisma Cloud. This visibility is crucial for identifying risks and exposures, especially those associated with Kubernetes and application configurations.
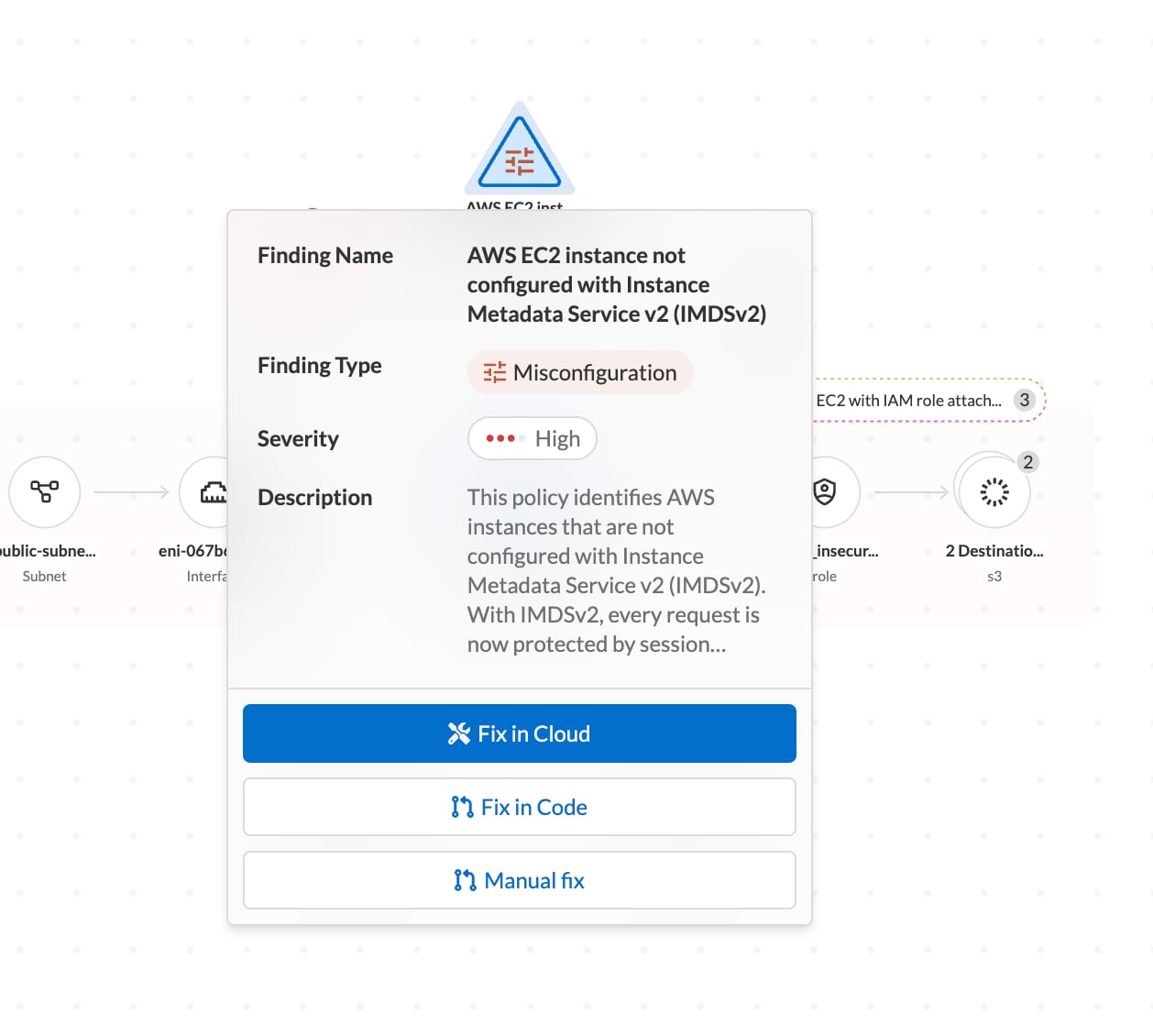
Deploy Phase
During the deploy phase, it's essential to scan for code-related issues, such as misconfigurations and vulnerabilities in application artifacts. Recognizing weaknesses in the CI/CD pipeline and infrastructure is equally vital. The platform aids in detecting exposed secrets and credentials in the pipeline, especially those originating from IaC templates. Establishing and implementing least privilege access during this phase ensures that only authorized individuals can make critical changes.
Build Phase
In the build phase, the platform's capabilities shine by scanning IaC templates for compliance violations and misconfigurations. It's also adept at detecting exposed secrets and credentials, ensuring that sensitive information remains protected.
Code Phase
The code phase emphasizes the importance of software composition analysis to identify vulnerabilities in open-source packages — a growing concern in today's tech landscape. Prisma Cloud integrates with popular IDEs like VSCode, allowing developers to identify library and package dependencies in code for various programming languages.
The Power of Code-to-Cloud Intelligence
Prisma Cloud is uniquely designed with Code-to-Cloud Intelligence, connecting risk insights in production back to the source in development environments to protect applications. Security teams can trace risk across each stage of the app lifecycle — code, build, deploy and run — to reduce risk and prevent breaches.
Our users tell us they choose Prisma Cloud for the platform's strong remediation capabilities — and for its ability to bridge DevOps and security teams, helping them to meet their collective goals.
Learn More
Tune in to our on-demand webinar, CNAPP Supercharged: A Radically New Approach to Cloud Security, to learn about Prisma Cloud's latest innovations and how to streamline app lifecycle protection. And don’t miss an opportunity to test drive best-in-class code-to-cloud security with a 30-day Prisma Cloud trial.
References
1. Apr 18, and 2023. n.d. “Unit 42 Cloud Threat Report, Volume 7: Navigating the Expanding Attack Surface.” Palo Alto Networks. Accessed October 4, 2023. https://www.paloaltonetworks.com/resources/research/unit-42-cloud-threat-report-volume-7.
2. “2023 Unit 42 Attack Surface Threat Report.” n.d. Palo Alto Networks. https://www.paloaltonetworks.com/resources/research/2023-unit-42-attack-surface-threat-report.