Preventing Unplanned Outages Due to Faulty Certificates Using Cortex Xpanse
On September 30, 2020, one of the largest certificate providers, “Let’s Encrypt'' saw their root certificate expire which required all their customers to upgrade their devices or face outages.
Digital certificates are issued to organizations by trusted authorities like Let’s Encrypt to keep user data secure, verify ownership of the website, prevent attackers from creating a fake version of the site, and avoid misleading unsuspecting customers.
The problem with these certificates is that like most cybersecurity assets, they are procured and deployed with abandon. Most organizations still track their assets through a series of emails, spreadsheets, or outdated inventory/configuration management databases.
While Let's Encrypt repeatedly advised its customers to make the necessary upgrades, one could safely assume that many were unable to as they did not have a granular view of all the certificates they owned.
In a recent MIT Technology Review Insights1 survey of over 700+ cybersecurity executives, over 50% of organizations faced a cybersecurity incident from an unknown or unmanaged digital asset. Another 20% mentioned that while they hadn’t yet had an incident on an unknown/unmanaged asset, they fully expected to see some in the near future.
Several prominent organizations faced disruptions and outages as a consequence of not having visibility into certificates deployed on their attack surface. Organizations like Cisco Umbrella, Catcpoint, Monday.com, Auth0, Shopify, cPanel, and many others faced disruptions on account of their respective certificates expiring as fallout from the Let's Encrypt incident.
Gartner estimates that business losses on account of unforeseen downtimes can be anywhere from $140,000 per hour to $300,0002 or more on average.
How does your asset management team monitor the lifecycle of your certificates to prevent unplanned downtime? Do your teams know when their certificates are about to expire or have other misconfigurations?
With Cortex Xpanse, organizations can prevent unplanned disruptions to their businesses stemming from known and unknown misconfigured certificates. Cortex Xpanse is a global internet collection and attribution platform that empowers CISOs to continuously discover, evaluate, and mitigate their external attack surface. Today, Xpanse customers collectively represent 12% of the overall IPv4 internet and include leading Fortune 500 companies as well as both US government organizations and military branches.
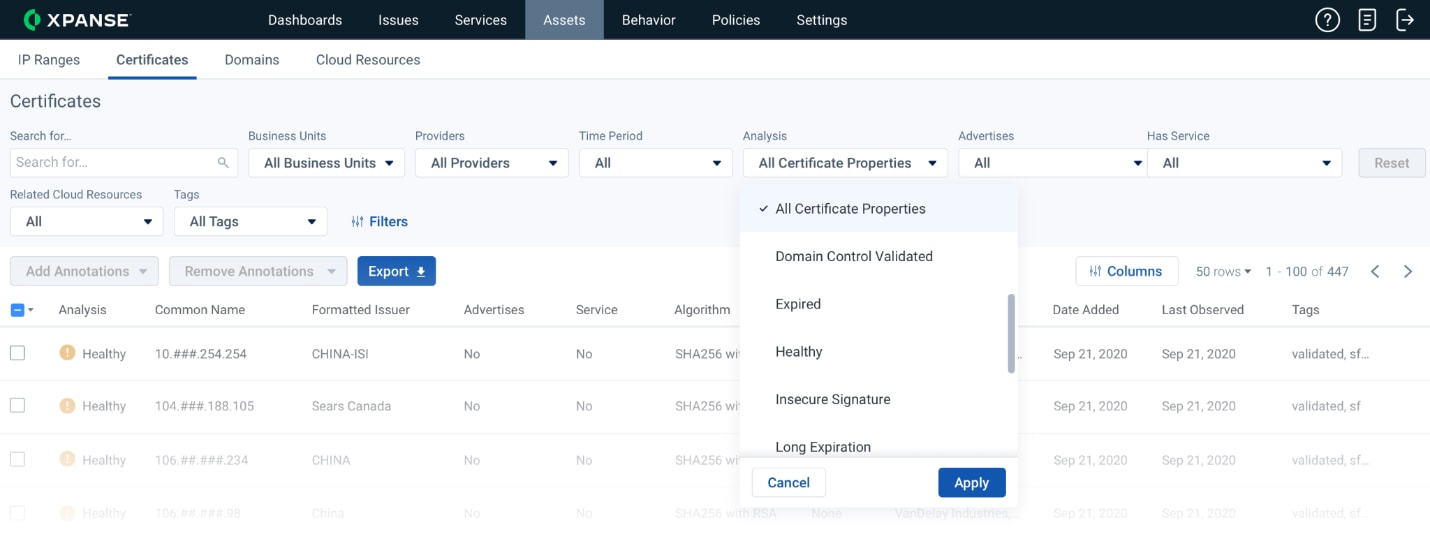
Fig 1: Screenshot of Certificate Management inside Expander
Certificates are one of the several assets which Xpanse helps organizations track and remediate. Cortex Xpanse automatically discovers an organization’s known and unknown certificates. Xpanse applies policies on this discovered inventory of certificates to automatically identify certificate misconfigurations, including expiring and expired certificates. Xpanse also identifies self-signed certificates, certificates with a short public key, long expiration, wildcard, and domain-control validated certificates so that organizations can remediate them.
Xpanse maintains a large repository of collected certificates, enriched with many of the fields referenced in RFC 5280, Internet X.509 Public Key Infrastructure Certificate and Certificate Revocation List (CRL) Profile. Having access to this wealth of data, allows us to enumerate information like self-signed attribution, and other misconfigurations identified in this article.
With Xpanse, organizations can secure their attack surface to improve operational efficiency by reducing mean time to discovery (MTTD) and mean time to remediation (MTTR). Xpanse also helps organizations reduce operational costs by being the single source of truth for your organization’s public-facing assets and replacing inaccurate, incomplete, and manual processes.
To learn more about Cortex Xpanse, visit here.
1 MIT Technology Review Insights, A game-changer in IT security, 2020
2 https://blogs.gartner.com/andrew-lerner/2014/07/16/the-cost-of-downtime/
Related Blogs
Subscribe to Security Operations Blogs!
By submitting this form, you agree to our Terms of Use and acknowledge our Privacy Statement. Please look for a confirmation email from us. If you don't receive it in the next 10 minutes, please check your spam folder.