-
What Is a Cyber Attack?
- Threat Overview: Cyber Attacks
- Cyber Attack Types at a Glance
- Global Cyber Attack Trends
- Cyber Attack Taxonomy
- Threat-Actor Landscape
- Attack Lifecycle and Methodologies
- Technical Deep Dives
- Cyber Attack Case Studies
- Tools, Platforms, and Infrastructure
- The Effect of Cyber Attacks
- Detection, Response, and Intelligence
- Emerging Cyber Attack Trends
- Testing and Validation
- Metrics and Continuous Improvement
- Cyber Attack FAQs
- Dark Web Leak Sites: Key Insights for Security Decision Makers
-
What Is a Zero-Day Attack? Risks, Examples, and Prevention
- Zero-Day Attacks Explained
- Zero-Day Vulnerability vs. Zero-Day Attack vs. CVE
- How Zero-Day Exploits Work
- Common Zero-Day Attack Vectors
- Why Zero-Day Attacks Are So Effective and Their Consequences
- How to Prevent and Mitigate Zero-Day Attacks
- The Role of AI in Zero-Day Defense
- Real-World Examples of Zero-Day Attacks
- Zero-Day Attacks FAQs
-
What Is Lateral Movement?
- Why Attackers Use Lateral Movement
- How Do Lateral Movement Attacks Work?
- Stages of a Lateral Movement Attack
- Techniques Used in Lateral Movement
- Detection Strategies for Lateral Movement
- Tools to Prevent Lateral Movement
- Best Practices for Defense
- Recent Trends in Lateral Movement Attacks
- Industry-Specific Challenges
- Compliance and Regulatory Requirements
- Financial Impact and ROI Considerations
- Common Mistakes to Avoid
- Lateral Movement FAQs
-
What is a Botnet?
- How Botnets Work
- Why are Botnets Created?
- What are Botnets Used For?
- Types of Botnets
- Signs Your Device May Be in a Botnet
- How to Protect Against Botnets
- Why Botnets Lead to Long-Term Intrusions
- How To Disable a Botnet
- Tools and Techniques for Botnet Defense
- Real-World Examples of Botnets
- Botnet FAQs
- What is a Payload-Based Signature?
-
What is Spyware?
- Cybercrime: The Underground Economy
-
What Is Cross-Site Scripting (XSS)?
- XSS Explained
- Evolution in Attack Complexity
- Anatomy of a Cross-Site Scripting Attack
- Integration in the Attack Lifecycle
- Widespread Exposure in the Wild
- Cross-Site Scripting Detection and Indicators
- Prevention and Mitigation
- Response and Recovery Post XSS Attack
- Strategic Cross-Site Scripting Risk Perspective
- Cross-Site Scripting FAQs
- What Is a Dictionary Attack?
- What Is a Credential-Based Attack?
-
What Is a Denial of Service (DoS) Attack?
- How Denial-of-Service Attacks Work
- Denial-of-Service in Adversary Campaigns
- Real-World Denial-of-Service Attacks
- Detection and Indicators of Denial-of-Service Attacks
- Prevention and Mitigation of Denial-of-Service Attacks
- Response and Recovery from Denial-of-Service Attacks
- Operationalizing Denial-of-Service Defense
- DoS Attack FAQs
- What Is Hacktivism?
- What Is a DDoS Attack?
-
What Is CSRF (Cross-Site Request Forgery)?
- CSRF Explained
- How Cross-Site Request Forgery Works
- Where CSRF Fits in the Broader Attack Lifecycle
- CSRF in Real-World Exploits
- Detecting CSRF Through Behavioral and Telemetry Signals
- Defending Against Cross-Site Request Forgery
- Responding to a CSRF Incident
- CSRF as a Strategic Business Risk
- Key Priorities for CSRF Defense and Resilience
- Cross-Site Request Forgery FAQs
- What Is Spear Phishing?
-
What Is Brute Force?
- How Brute Force Functions as a Threat
- How Brute Force Works in Practice
- Brute Force in Multistage Attack Campaigns
- Real-World Brute Force Campaigns and Outcomes
- Detection Patterns in Brute Force Attacks
- Practical Defense Against Brute Force Attacks
- Response and Recovery After a Brute Force Incident
- Brute Force Attack FAQs
- What is a Command and Control Attack?
- What Is an Advanced Persistent Threat?
- What is an Exploit Kit?
- What Is Credential Stuffing?
- What Is Smishing?
-
What is Social Engineering?
- The Role of Human Psychology in Social Engineering
- How Has Social Engineering Evolved?
- How Does Social Engineering Work?
- Phishing vs Social Engineering
- What is BEC (Business Email Compromise)?
- Notable Social Engineering Incidents
- Social Engineering Prevention
- Consequences of Social Engineering
- Social Engineering FAQs
-
What Is a Honeypot?
- Threat Overview: Honeypot
- Honeypot Exploitation and Manipulation Techniques
- Positioning Honeypots in the Adversary Kill Chain
- Honeypots in Practice: Breaches, Deception, and Blowback
- Detecting Honeypot Manipulation and Adversary Tactics
- Safeguards Against Honeypot Abuse and Exposure
- Responding to Honeypot Exploitation or Compromise
- Honeypot FAQs
- How to Break the Cyber Attack Lifecycle
-
What Is Phishing?
- Phishing Explained
- The Evolution of Phishing
- The Anatomy of a Phishing Attack
- Why Phishing Is Difficult to Detect
- Types of Phishing
- Phishing Adversaries and Motives
- The Psychology of Exploitation
- Lessons from Phishing Incidents
- Building a Modern Security Stack Against Phishing
- Building Organizational Immunity
- Phishing FAQ
- What Is a Rootkit?
- Browser Cryptocurrency Mining
- What Is Pretexting?
- What Is Cryptojacking?
What Is Password Spraying?
Password spraying is a low-and-slow authentication attack where adversaries attempt a small set of common passwords, like Winter2024! or Password1 — across many usernames. Unlike brute-force attacks, spraying avoids lockouts by rotating targets, making it an effective way to discover weak credentials at scale without triggering typical rate-based defenses.
Password Spraying Explained
In the MITRE ATT&CK framework, password spraying is a brute-force authentication technique classified under MITRE ATT&CK technique ID T1110.003: Brute Force – Password Spraying. It's not a vulnerability but a tactic used to exploit weak credential hygiene at scale while evading lockout mechanisms. Attackers target a large number of accounts using a limited set of commonly used passwords, spacing attempts to avoid detection.
Tactic Vs. Vulnerability
Unlike dictionary or credential stuffing attacks, which rely on password reuse across services, password spraying doesn't require breached credentials. It's opportunistic by design, exploiting weak passwords combined with poor monitoring or poorly enforced password policies. Most often, it's a means of initial access or privilege escalation, not an exploit in the traditional sense.
Alternate Terminology
You'll see password spraying referred to in threat reports as “low-and-slow brute forcing,” “spray attacks,” or “horizontal password attacks.” The core strategy remains consistent — avoid triggering account lockouts by distributing login attempts across users rather than concentrating on one account.
Evolution and Usage Trends
Password spraying has evolved in parallel with enterprise adoption of cloud authentication, particularly SSO portals and remote access platforms. Attackers have adapted tooling to automate rotation across services like Microsoft 365, Okta, and VPN gateways. In some cases, they now integrate CAPTCHA solvers and proxy infrastructure to bypass geofencing or rate-limiting.
In 2024, threat actors increasingly paired spraying with MFA fatigue and session token theft, chaining multiple techniques for stealthier access. Enterprise detection remained challenging due to low volume, IP diversity, and the appearance of legitimate login behavior.
How Password Spraying Works
Password spraying is engineered to evade traditional lockout protections and evade detection thresholds by reversing the brute-force model. Instead of targeting one account with many passwords, it targets many accounts using just a few common passwords in a distributed, time-separated manner.
Attack Flow
The attacker typically begins with a list of valid usernames. These may come from open-source intelligence (OSINT), breached credential databases, misconfigured directory services, or tools like Kerbrute or GetADUsers.py for internal networks. Once a list is compiled, the attacker rotates through a handful of common or default passwords — such as "Spring2024!", "Welcome1", or "Password123" — applying each one to the entire user list before moving to the next.
The attack often proceeds in waves, timed to avoid triggering account lockouts or threshold-based anomaly detection. A single login attempt per account per password variant can span hours or days.
Common Tools and Infrastructure
Attackers rely on frameworks that support slow and distributed credential testing. Commonly used tools include:
- Spray (by Dominic White): A Python-based tool for authenticated access testing via NTLM/LDAP.
- MSOLSpray: A lightweight Azure AD password spray tool designed to avoid lockouts.
- Go365spray: Written in Go, focused on Microsoft 365 login portals.
- Kerbrute: For enumerating and brute-forcing Kerberos logins over internal Active Directory networks.
They often run these tools through TOR exit nodes, rotating residential proxies, or cloud VMs to diversify origin IPs and evade geofencing or rate-limiting filters. Credential sprays against SaaS and federated identity providers (e.g., Okta, Azure AD, Duo) have grown due to their centralized access and minimal user friction.
Targeted Protocols and Surfaces
Password spraying works best against externally exposed login surfaces that don’t implement strict rate-limiting or MFA. Common targets include:
- Microsoft 365 login portals: Especially Exchange Online, SharePoint, and Teams.
- VPN gateways: Pulse Secure, Fortinet, and Cisco ASA have all been frequent targets.
- SSO and identity providers: Okta, Duo, Ping Identity, and custom SAML or OIDC implementations.
- Webmail: Particularly older or custom-hosted OWA and Zimbra instances.
Exploited Weaknesses
The core susceptibility to password spraying involves the oversight of two key security measures — the reliance on weak, guessable passwords and poorly tuned lockout policies or passive MFA configurations. Single sign-on and legacy authentication protocols like IMAP or POP3 can create indirect password-based access channels even when modern auth is enforced elsewhere.
Variant: Low-and-Slow Spray with MFA Enumeration
A growing trend combines password spraying with MFA prompt analysis or enumeration. Attackers identify which users have MFA enabled by observing authentication response codes and then focus spraying on users without enforced MFA or with fallback SMS-based mechanisms that are easier to bypass.
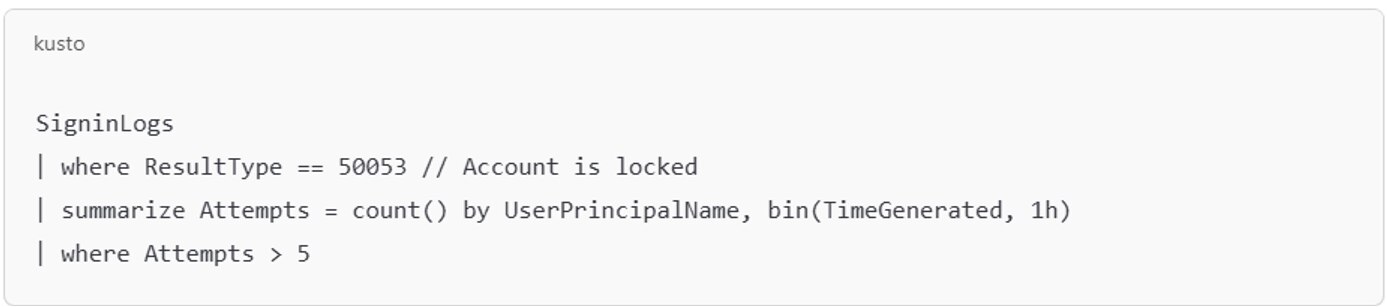
Figure 1: Detection query example (for Microsoft 365/Azure)
The query in figure 1 identifies accounts with multiple failed login attempts leading to lockouts, a common side effect of failed spray attempts when incorrectly timed or improperly throttled. More advanced correlation involves comparing failed logins across disparate IPs with consistent user-agent strings.
Password spraying succeeds not through sophistication but by exploiting security fatigue — users choosing predictable passwords and administrators relying too heavily on legacy detection logic.
Password Spraying in the Broader Attack Lifecycle
Password spraying plays a pivotal role in early-stage access operations. It's a credential-based attack method frequently used during the initial access or reconnaissance phase of a cyber attack, often serving as a precursor to deeper network compromise, privilege escalation, and eventual data exfiltration or ransomware deployment.
Initial Access: Distributed Probing at Scale
Attackers typically begin by harvesting usernames through OSINT, credential dumps, or enumeration against publicly exposed identity providers. Password spraying follows, using common passwords to avoid lockouts. Because the method targets authentication portals directly — Microsoft 365, Okta, VPNs, webmail — it bypasses many traditional perimeter defenses and probes the identity layer directly.
Spraying is especially effective in hybrid or cloud-first environments where federated identity enables access to multiple systems through a single compromised account. Attackers frequently pair this with session replay or token theft to move laterally post-compromise.
Credential Access and Privilege Escalation
If spraying succeeds, attackers prioritize high-privilege accounts — administrators, service accounts, or executives — to gain broader control. Even low-privilege credentials can be leveraged to enumerate internal services or pivot toward misconfigured SaaS integrations or API tokens. Password spraying often transitions into more targeted credential dumping, Kerberoasting, or golden ticket attacks in on-premises Active Directory environments.
Persistence Through Federated SSO
Once attackers access the target environment, they often establish persistence by abusing trusted identity providers. In Microsoft environments, attackers may register their own devices via Intune, create OAuth tokens using hijacked credentials, or persist access through service principals with delegated privileges. The entire chain relies on the foothold created by a successful spray.
Post-Compromise Lateral Movement and Data Exfiltration
From a foothold gained via password spraying, attackers can escalate privileges, map internal architecture, and exploit poorly segmented environments. In several data breaches, password spraying led directly to lateral movement via compromised VPN or RDP services. SaaS environments lacking behavioral monitoring are particularly vulnerable to exfiltration of email archives, file shares, or contact databases.
Attack Chain Example
- Attacker collects usernames from LinkedIn and public email aliases.
- Launches a spray across hundreds of M365 accounts using "Winter2024!" as the password.
- Gains access to two non-MFA accounts, one belonging to a contractor.
- Uses the credentials to access SharePoint and harvest files containing internal IP schema.
- Registers a rogue device and establishes persistent session tokens.
- Exploits internal service misconfiguration to move laterally and access customer PII.
Password spraying is rarely an isolated tactic. It acts as the ignition point for sophisticated, multistage intrusion chains that exploit both identity weaknesses and architectural oversights. Its low technical barrier and high success rate make it a favorite tool for both opportunistic cybercriminals and advanced persistent threat (APT) actors.
Real-World Examples of Password Spraying Attacks
Password spraying remains one of the most commonly reported external attack techniques. Its low resource requirements, high success rate, and difficulty to detect at scale make it a persistent threat across sectors, from finance to education to critical infrastructure.
Microsoft Exchange Password Spraying Campaign (2023)
In early 2023, Microsoft identified a coordinated password spraying campaign targeting Exchange Online users. The threat actors, attributed to a nation-state group, focused on diplomatic and defense organizations. They bypassed MFA in some cases by exploiting legacy protocols like IMAP and POP3, which didn’t enforce strong authentication. Once access was obtained, the attackers searched inboxes for sensitive diplomatic correspondence and credential resets. Microsoft recommended disabling legacy auth and tightening conditional access policies.
Cisco Duo Compromise via Contractor Account
A compromised contractor account, accessed via password spraying, enabled threat actors to enroll a new MFA device and gain access to Cisco’s internal systems. In the 2022 incident, the attacker harvested employee credentials through previous breaches and tested them against Duo's portal. After gaining entry, they exfiltrated internal documents and source code repositories. The cyberattack highlighted the risk of incomplete offboarding and unmonitored contractor credentials.
US Federal Agency Compromise (CISA Alert AA22-137A)
CISA released an alert detailing how a federal agency’s external remote access services were breached through a password spray campaign. The attacker used an open-source tool to target Outlook Web Access and VPN login portals with a list of commonly used passwords. Once inside, the attacker implanted a web shell and maintained persistence through scheduled tasks. CISA emphasized the need for robust account lockout policies and federated identity hardening.
APT28 (Fancy Bear) Targeting Microsoft 365 Tenants
In 2023, APT28 conducted extensive password spraying against Microsoft 365 tenants of military and governmental institutions across Europe and North America. The campaign avoided triggering lockouts by rotating IP addresses and spreading attempts over weeks. Successful account compromises enabled surveillance of defense-related communications. Microsoft identified the attacker’s infrastructure and issued technical guidance for detecting residual activity, including sign-ins from TOR exit nodes and anomalous token usage.
Detection and Indicators
Password spraying attacks are designed to evade traditional defenses by blending into normal authentication traffic. They don’t trip account lockouts because they target many accounts with a few common passwords, rather than brute-forcing one account with multiple guesses. Identifying these attacks requires careful correlation of authentication patterns, source behavior, and access context.
Common Indicators of Compromise (IOCs)
- Source IP anomalies: Look for repeated authentication attempts across multiple accounts from a single external IP address. IPs may rotate, but persistent subnets or TOR exit nodes often repeat.
- Time-distributed login attempts: Spraying campaigns may span hours or days. Even low-frequency attempts (e.g., one password per hour per account) can succeed. Aggregate attempts over longer windows.
- Consistent user agent strings: Attack scripts and automation tools like Spray365 or FireProx often reuse headers or user-agent strings across sessions. Flag uniform values with high request volumes.
- Authentication method: Password spraying frequently targets basic auth endpoints (e.g., legacy Exchange, VPN, RDP, or webmail portals). Monitor OAUTH token abuse and failed SAML assertions.
Behavioral Patterns in Logs
- Failed logins against dormant or unused accounts: Attackers test broad username lists, including former employees or service accounts. Watch for failed attempts on accounts not recently accessed.
- Uniform password usage across accounts: Look for failed login attempts where the same password is used repeatedly across different usernames within a small time window.
- Geo-velocity mismatches: Logins or attempts from unusual geographies, especially if they deviate from a user’s historical behavior, may point to automated credential abuse.
SIEM and XDR Monitoring Recommendations
SIEMs should implement correlation rules that flag:
- Multiple failed authentications across unique usernames from the same IP
- Excessive login attempts against a small group of user accounts
- Authentication attempts to high-value portals (e.g., VPN, Exchange, M365) with no follow-up activity
XDR tools should baseline normal authentication activity per user and per endpoint. Deviation from these baselines — such as logins attempted at unusual hours, across many accounts, or from headless browsers — should trigger review.
Enrich detections with threat intel on spray infrastructure, including TOR IPs, known bad ASNs, or domains linked to password spraying kits. Where possible, enrich logs with identity metadata to prioritize alerts for admin accounts or those with sensitive resource access.
Preventing and Mitigating Password Spraying Attacks
Password spraying thrives on weak credentials and insufficient login protections. Effective defense demands layered controls that limit exposure, throttle misuse, and detect abnormal authentication patterns in real time.
Block Access to Insecure Protocols and Legacy Endpoints
Disable or restrict use of authentication mechanisms that don’t support modern defenses like MFA or account lockouts. Common high-risk targets include:
- Exchange Web Services (EWS)
- IMAP/POP3 endpoints
- RDP without network-level authentication
- VPN portals using static credentials only
Segment these services behind zero trust access brokers or decommission them entirely if not in active use.
Enforce MFA Everywhere It’s Supported
Multifactor authentication significantly limits the value of a compromised password. Enforce MFA across all user accounts, especially for:
- Admin and privileged roles
- Remote access services
- SaaS portals with federated identity
- Third-party contractor accounts
Avoid fallback mechanisms that allow password-only access under certain conditions (e.g., “trusted device” exemptions).
Implement Account Lockout and Throttling Mechanisms
Account lockouts after a defined number of failed logins — ideally paired with exponential backoff or progressive delays — can halt most spraying attempts. To reduce impact on legitimate users:
- Lock only for verified usernames.
- Use CAPTCHA after repeated failures.
- Apply lockout logic at both application and identity provider layers.
Monitor Authentication at Scale
Rate-limit failed login attempts by IP address and user ID. Monitor aggregate login failures across time windows to detect slow, distributed password spraying campaigns. Use behavioral analytics to identify suspicious but low-frequency anomalies.
Harden Credential Hygiene
- Require long, complex passwords, and rotate any default or shared credentials.
- Block common and leaked passwords using tools like NIST’s banned list or Azure AD’s Smart Lockout.
- Decommission unused accounts and enforce expiration for guest or service accounts.
Train Employees Without Overreliance on Awareness
While user training won’t prevent spraying directly, educating staff about account security (e.g., avoiding password reuse, reporting MFA prompts they didn’t initiate) can reduce attacker success post-compromise.
What Doesn’t Work
Relying solely on signature-based threat detection or assuming VPNs protect against brute force is a false sense of security. Spraying often exploits what defenders forget to monitor — password-only endpoints, legacy ports, and unmonitored identity federation paths.
Preventing password spraying means closing systemic gaps. Defense must cover the identity surface area with precision, context awareness, and ongoing visibility.
Responding to Password Spraying
Because password spraying often precedes deeper compromise, incident response efforts must combine immediate containment with long-term architectural improvements that harden identity infrastructure and remove blind spots from authentication telemetry.
Contain and Confirm the Scope of Exposure
When a password spraying attack is detected — either through behavioral alerts, identity provider logs, or third-party telemetry — immediate containment depends on confirming which accounts were successfully accessed. Begin by correlating failed login attempts with successful logins from the same IP, device fingerprint, or geography. Flag anomalous access patterns, especially outside normal business hours or from untrusted networks.
Lock potentially compromised accounts and force credential resets. Disable affected sessions in identity providers (e.g., Okta, Azure AD) to prevent lateral movement or token replay. Prioritize accounts with elevated privileges or third-party integrations.
Eradication and Root Cause Validation
Once the scope is mapped, investigate the root cause:
- Was MFA misconfigured?
- Did legacy protocols expose an endpoint to spraying?
- Did logging gaps delay detection?
Audit federation configurations, authentication flows, and SIEM/XDR signal paths to ensure complete visibility into all authentication telemetry — especially from mobile clients, legacy apps, or non-browser-based traffic. Disable basic auth protocols where possible.
If the attack involved widespread credential testing across your environment, verify no other cyberattack modules (e.g., phishing or MFA fatigue) were chained in parallel.
Communication and Executive Briefing
Brief leadership on what occurred using plain, quantifiable language: number of attempted logins, number of confirmed compromises, and any systems accessed. Emphasize operational impact and dwell time, not just technical containment.
Notify internal stakeholders responsible for IAM, endpoint security, and cloud access. If third-party contractors or federated identities were targeted, alert partner organizations. For high-profile or regulated industries, coordinate with legal and compliance for breach notification if thresholds were exceeded.
Post-Mortem and Hardening Actions
- Password policy audit: Evaluate enforcement of unique passwords, banned password lists, and credential reuse tracking.
- MFA coverage validation: Extend MFA requirements to any services, endpoints, or applications previously excluded due to technical debt or exception handling.
- Log pipeline assessment: Ensure all login attempts — successful and failed — are captured, enriched, and correlated in SIEM or XDR. Include user-agent strings, IPs, and device fingerprints.
- Behavioral analytics tuning: Calibrate detection rules to better catch low-and-slow spraying. Incorporate velocity rules, impossible travel detection, and identity enrichment to spot cross-account spray patterns.
- User education refresh: Educate users on password reuse risk, especially across SaaS accounts. Include awareness around phishing that might follow spraying attacks to gain secondary access.